Integrate Anything.
Automate Everything.
If it talks, Torq Hyperautomation can connect to it.
Integrate, Instantly.
You Build It
Elevate non-technical users with developer like powers with no-code tools while providing full-code support for power users.
We Build It
Create integrations in record time by partnering with Torq’s experienced customer success team.
Always Up-To-Date Integrations
Stay connected even if your third-party API or data format changes with real-time API monitoring and updates for uninterrupted automation.
Top Categories
Abnormal Security
Orchestrate and automate response to email security events, analyzing emails and their attachments and automatically performing remediation actions.
Adaptive Shield
Automatically drive SaaS Security findings and alerts to resolution, while accessing security checks, audit logs and user data.
AlientVault OTX
Automatically enrich security alerts and findings with accurate Threat Intelligence data, driving to risk-score-driven decisions.
Anomali ThreatStream
Automatically enrich security alerts and findings with accurate Threat Intelligence data, driving to risk-score-driven decisions. Manage sandbox analysis pipeline for suspicious files.
Anvilogic
Detect, hunt, and investigate threats across multiple data platforms then quickly execute interactive remediation workflows.
Apiiro
Orchestrate resolution of Software Supply Chain findings and alerts in fully automated or human-in-the-loop fashion.
Aqua
Manage CSPM alerts, scans, cloud accounts, audit logs, and tests.
Armis
Turn asset management and attack surface findings into actionable remediation while enriching with context on users and devices.
Asana
Execute automated workflows for Project Management tasks and update results / enrich information in the project plan.
Atlassian Jira
Attach automation workflows to activities in Jira / ServiceDesk tickets, enriching the tickets with information and driving to resolution.
Atlassian
Orchestrate and automate incident response workflows by leveraging paging and user interaction, driving incidents to resolution.
Atmosec
Automatically drive SaaS Security findings and alerts to resolution, while accessing security checks, audit logs and user data.
AWS
Automate just-in-time access, resolve security issues performing enrichment / containment / remediation actions on your infrastructure.
AWS Security Lake
Query and update information stored in the data lake for Detection Engineering, Threat Hunting and other security processes.
Axonius
Turn asset management and attack surface findings into actionable remediation while enriching with context on users and devices.
BambooHR
Orchestrate employee lifecycle based on HRIS events, automate employee and contractor on-boarding and off-boarding.
BigID
Orchestrate and automate Data Security, Privacy, Compliance and Governance operations with automated workflows performing fully automated or human-in-the-loop enforcement and remediation.
Box
Orchestrate and automate documents sharing lifecycle, introduce human-in-the-loop approvals for external sharing and automatically review document access activity.
Britive
Automate Zero Trust workflows for Privileged Access to your cloud infrastructure.
Check Point Cloudguard
Automate Network Security policy management lifecycle, as well as remediation of Network / Cloud Security findings.
Cisco Umbrella
Automate SASE operations, including block/allow-lists management, just-in-time access and service provisioning.
Cisco WebEx
Create interactive chatbots, democratizing security events lifecycle with human-in-the-loop capabilities and provide delightful self-service experiences to information employees.
CloudFlare
Automate SASE operations, including block/allow-lists management, just-in-time access and service provisioning.
Coralogix
Query historical logs, enriching security signals with important context information.
CrowdStrike
Orchestrate EDR / XDR operations, attaching automated enrichment, containment and response workflows to identified threats and additional events.
Cybereason
Orchestrate EDR / XDR operations, attaching automated enrichment, containment and response workflows to identified threats and additional events.
Cybersixgill
Automatically enrich security alerts and findings with accurate Threat Intelligence data, driving to risk-score-driven decisions. Orchestrate lifecycle of actionable threat information.
CyCognito
Automate external attack surface management findings, driving them to resolution while enriching with asset context.
Datadog
Orchestrate resolution of security and observability alerts, enriching each event with dynamically queried historical data. Automate detection engineering and Threat Hunting processes.
Devo
Orchestrate SIEM / UEBA operations, attaching automated enrichment, containment and response workflows to identified threats and additional events.
Discord
Create interactive chatbots, democratizing security events lifecycle with human-in-the-loop capabilities and provide delightful self-service experiences to information employees.
DomainTools
Enrich security events with up-to-date information, submit specific domains for review and more.
Drata
Automate lifecycle of evidence collection for compliance controls, ensuring consistent and accurate assets for the audit cycle.
DropBox
Orchestrate and automate documents sharing lifecycle, introduce human-in-the-loop approvals for external sharing and automatically review document access activity.
Elastic Security
Automate Threat Detection, Investigation and Response following actionable alerts on Elastic data and leveraging flexible data retrieval capabilities. Automate detection engineering and Threat Hunting processes.

Flashpoint
Combine data, insights, and automation to identify risks and stop threats.
Fortinet
Automate Network Security policy management lifecycle, as well as remediation of Network / Cloud Security findings.
Google Chat
Create interactive chatbots, democratizing security events lifecycle with human-in-the-loop capabilities and provide delightful self-service experiences to information employees.
Google Cloud
Generate a token to authenticate Google apps and to run Gcloud CLI commands.
Google Workspace Mail (Gmail)
Orchestrate email security lifecycle, analyzing emails and attachments, as well as introducing quarantine and other remediation measures.
GreyNoise
Automatically enrich security alerts and findings with accurate Threat Intelligence data, driving to risk-score-driven decisions.
HashiCorp
Strengthen your automated workflows with short-lived or just-in-time-accessed entitlements and credentials managed by HashiCorp Vault; automate Terraform lifecycle.
Hibob
Orchestrate employee lifecycle based on HRIS events, automate employee and contractor on-boarding and off-boarding.
Hunters
Orchestrate and automate resolution of SOC alerts, enriching with data from 3rd parties and involving human-in-the-loop decisions.
IBM qRadar
Orchestrate SIEM operations, attaching automated enrichment, containment and response workflows to identified threats and additional events.
Ironscales
Orchestrate email security issues resolution in a fully-automated or human-in-the-loop fashion.
Jamf
Automate device management lifecycle, including user/group policies, device onboarding and offboarding, OS/application upgrades and security events.
JumpCloud
Automate user and device management lifecycle, from on-boarding to off-boarding, including compliance, just-in-time and privileged access policies.
JupiterOne
Turn asset management and attack surface findings into actionable remediation while enriching with context on users and devices.
Kandji
Automate device management lifecycle, including user/group policies, device onboarding and offboarding, OS/application upgrades and security events.
Lacework
Automate CNAPP issues remediation lifecycle, in either a fully-automated or human-in-the-loop fashion, involving Security, DevOps and Engineering role-players.
Legit Security
Orchestrate resolution of Software Supply Chain findings and alerts in fully automated or human-in-the-loop fashion.
LimaCharlie
Automate remediation of LimaCharle XDR alerts, enriching with information from 3rd-party systems and drive to resolution.
Microsoft 365
Orchestrate email security lifecycle, access and update data in Word, Excel, PowerPoint documents.
Microsoft Active Directory
Automate managing user and device lifecycle, from on-boarding to off-boarding, implement just-in-time access procedures and orchestrate response to security events.
Microsoft Azure
Automate just-in-time access, resolve security issues performing enrichment / containment / remediation actions on your infrastructure.
Microsoft Azure Cognitive Services
Extend automated workflows with conversational experience and Generative AI for data analytics, decision support and more, enabling AI-driven autonomous security operations.
Microsoft Defender
Orchestrate EDR operations, attaching automated enrichment, containment and response workflows to identified threats and additional events.
Microsoft Entra
Automate managing user and device lifecycle, from on-boarding to off-boarding, implement just-in-time access procedures and orchestrate response to security events.
Microsoft Power BI
Retrieve and update information, allowing in-depth analytics on up-to-date rich information about security events.
Microsoft Sentinel
Orchestrate SIEM / XDR operations, attaching automated enrichment, containment and response workflows to identified threats and additional events.
Microsoft Teams
Create interactive chatbots, democratizing security events lifecycle with human-in-the-loop capabilities and provide delightful self-service experiences to information employees.
monday.com
Execute automated workflows for Project Management tasks and update results / enrich information in the project plan.
NextDLP
Orchestrate and automate Data Loss Prevention and Insider Risk Management operations by attaching rich workflows to handle security events in fully-automated or human-in-the-loop fashion.
Notion
Automate knowledge management and data security operations, accessing and responding to events, as well as querying and updating information stored in Notion pages and tables.
Okta
Automate managing user and device lifecycle, from on-boarding to off-boarding, implement just-in-time access procedures and orchestrate response to security events.
OneLogin
Automate managing user lifecycle, from on-boarding to off-boarding, implement just-in-time access procedures and orchestrate response to security events.
OpenAI
Extend automated workflows with conversational experience and Generative AI for data analytics, decision support and more, enabling AI-driven autonomous security operations.
Orca Security
Automate and orchestrate response to Cloud Security findings and alerts, enriching the data from multiple sources and driving issues to resolution.
OX Security
Orchestrate resolution of Software Supply Chain findings and alerts in fully automated or human-in-the-loop fashion.
PagerDuty
Orchestrate and automate incident response workflows by leveraging paging and user interaction, driving incidents to resolution.
Palo Alto Networks
Automate Network Security policy management lifecycle, as well as remediation of Network / Cloud Security findings.
Palo Alto Networks Cortex XDR
Automate Network Security policy management lifecycle, as well as remediation of Network / Cloud Security findings.
Panther
Orchestrate and automate resolution of SOC alerts, enriching with data from 3rd parties and involving human-in-the-loop decisions.

PingIdentity
Automate managing user lifecycle, from on-boarding to off-boarding, implement just-in-time access procedures and orchestrate response to security events.
Prisma Cloud
Automate and orchestrate response to Cloud Security findings and alerts, enriching the data from multiple sources and driving issues to resolution.
Proofpoint
Orchestrate and automate response to email security events, analyzing emails and their attachments and automatically performing remediation actions.
Qualys
Orchestrate and automate Continuous Vulnerability Management, Application Security and Cloud Security pipelines in fully-automated, as well as human-in-the-loop fashion.
Rapid7 VM
Orchestrate and automate Continuous Vulnerability Management and Application Security pipelines in fully-automated, as well as human-in-the-loop fashion.
Recorded Future
Automatically enrich security alerts and findings with accurate Threat Intelligence data, driving to risk-score-driven decisions. Orchestrate lifecycle of actionable threat information.
SafeBreach
Orchestrate Breach and Attack Simulation drill follow-up, dynamically provision entitlements based on drill results and handle interactive communications.
SentinelOne
Orchestrate EDR / XDR operations, attaching automated enrichment, containment and response workflows to identified threats and additional events.
ServiceNow
Attach automation workflows with flexible business rules to SeviceNow ITSM / SOAR tickets, enriching them with information and driving to resolution.

Shodan
Enrich security events orchestration with rich information about internet-connected services using flexible queries.
Slack
Create interactive chatbots, democratizing security events lifecycle with human-in-the-loop capabilities and provide delightful self-service experiences to information employees.
Snowflake
Query and update information stored in the data lake for Detection Engineering, Threat Hunting and other security processes.
Snyk
Orchestrate resolution of Cloud Native and Application Security findings via fully-automated or human-in-the-loop workflows.
Sophos
Orchestrate Endpoint Security and EDR operations, attaching automated enrichment, containment and response workflows to identified threats and additional events.
Splunk
Orchestrate SIEM operations, attaching automated enrichment, containment and response workflows to identified threats and additional events. Automate detection engineering and Threat Hunting processes.
Splunk On Call
Orchestrate and automate incident response workflows by leveraging paging and user interaction, driving incidents to resolution.
SumoLogic
Orchestrate SIEM operations, attaching automated enrichment, containment and response workflows to identified threats and additional events. Automate detection engineering and Threat Hunting processes.
Tanium
Orchestrate XEM operations, automating device lifecycle and enriching data with up-to-date endpoint information to drive open issues to resolution.
Tenable Cloud Security
Orchestrate and automate remediation of security findings of AWS, Microsoft Azure and Google Cloud.

Tenable Vulnerability Management
Orchestrate and automate Continuous Vulnerability Management and Application Security pipelines in fully-automated, as well as human-in-the-loop fashion.
ThreatQ
Automatically enrich security alerts and findings with accurate Threat Intelligence data, driving to risk-score-driven decisions. Orchestrate lifecycle of actionable threat information.
Twilio
Store your credentials and use them in steps that communicate with Twilio without storing sensitive information in the workflow.
Uptycs
Automate and orchestrate response to CNAPP and XDR findings and alerts, enriching the data from multiple sources and driving issues to resolution.
urlScan
Automatically enrich security alerts and findings with accurate Threat Intelligence data, driving to risk-score-driven decisions.
VirusTotal
Automatically enrich security alerts and findings with accurate Threat Intelligence data, driving to risk-score-driven decisions.

VMware Carbon Black
Orchestrate EDR / XDR operations, attaching automated enrichment, containment and response workflows to identified threats and additional events.
Always Up-to-Date Integrations.
Dedicated engineers and tools monitor for third-party API changes in real-time to ensure maximum connectivity and compatibility.
Security automations to run continuously and uninterrupted around the clock.
Third-party security vendors are added frequently for the most seamless out-of-the-box integrations.
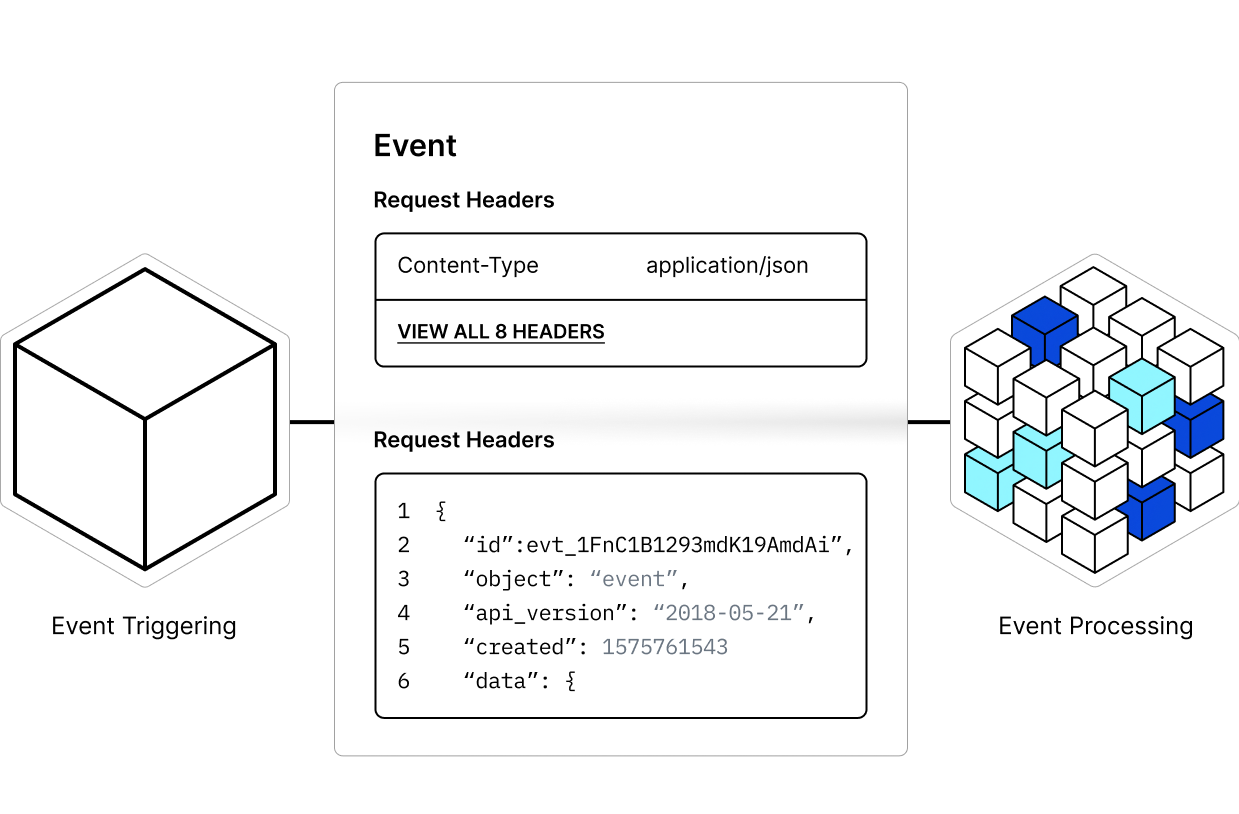
Event-Driven, Real-Time Updates.
Trigger automated workflows or actions based on specific events for timely and precise responses.
Webhooks facilitate instant connectivity for real-time notifications, enhancing responsiveness for the most pressing issues.
Facilitate efficient communications between disparate systems or services, promoting cohesion across security tooling and infrastructure.
Connect to Any Command Line Interface.
Go beyond APIs, supporting any CLI, platform, and programming or scripting language for maximum integration flexibility.
Extends capabilities beyond what APIs and webhooks can offer, especially in environments with complex or non-standard configurations.
Connect older systems that do not support modern API or webhook integrations.
Request a Demo
Ditch legacy SOAR and switch to enterprise-grade, AI-driven hyperautomation.
See it in action. Get a demo.
