Cybersecurity is a landscape forever in motion, an arena where threats evolve at an alarming pace. The tools we employ to counter threats should match this pace and anticipate the unforeseeable. Still, a chasm exists where tools are not keeping up with the changes, particularly regarding case management.
I’m Dor Morgenstern, lead PM for Case Management at Torq. With a background rooted in cybersecurity, I’ve seen firsthand the evolving challenges that security operations face. In this blog, I aim to shed light on the transformational power of workflow-centric case management and how it addresses these challenges head-on.
The Sunset of Legacy SOAR Solutions
From their start, case management and SOAR solutions carried the promise of transforming cybersecurity operations. They introduced playbooks, welcoming an era that promised seamless automation and rapid response to threats. On paper, they’re the perfect solution.
But the reality has been disappointing. Instead of simplifying the security process, these platforms layer automation onto existing ticketing or case management solutions. Like placing a new engine in an old car chassis–it might run faster, but it still can’t navigate the modern digital highway efficiently.
Legacy SOAR gives people clunky configuration panels resembling aircraft cockpits. Analysts and SOC architects are forced to mentally sift through a mess of switches, knobs, and redundant options. Instead of enabling rapid response, the tools become a stumbling block. More often than not, critical response actions get delayed by the sheer complexity of the tool meant to streamline them. SOAR is not alone in this complexity problem, of course, as Ross Haleliuk pointed out in a recent blog:
“…every product today has hundreds of configurations, options, and knobs that security practitioners need to turn a certain way to achieve a particular outcome.”
That’s where workflows come into play.
The Intuitive Power of Workflows
At the heart of this new paradigm shift in cybersecurity lies the idea of dynamic workflows. Instead of getting bogged down in static configurations and limited predefined settings, why not design a system that evolves and adapts on the fly?
Workflows act like dynamic decision trees, charting a course through the complexity of security incidents. They are inherently flexible, allowing for real-time adaptation based on the unique characteristics of each security event. Teams are no longer forced to stick to a rigid script; instead, they can navigate the ever-changing terrain of cybersecurity threats.
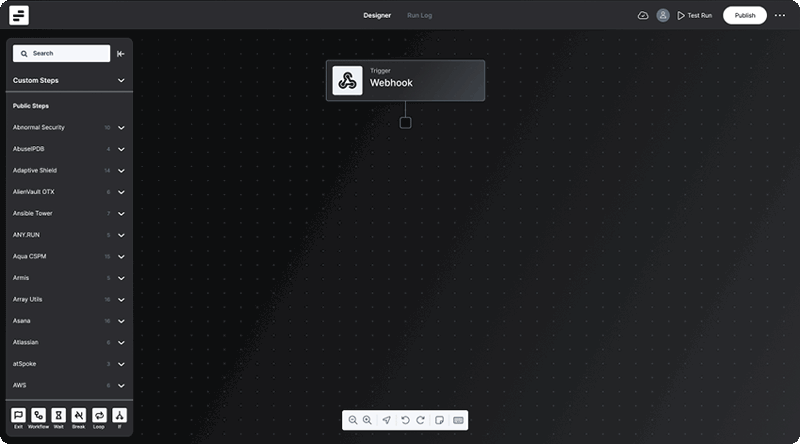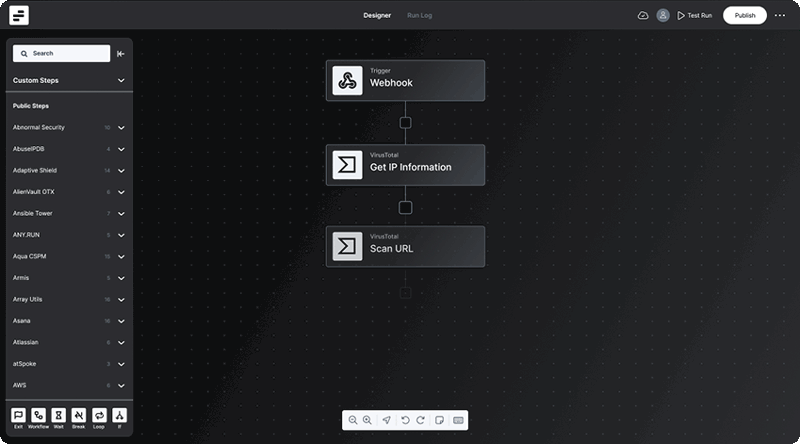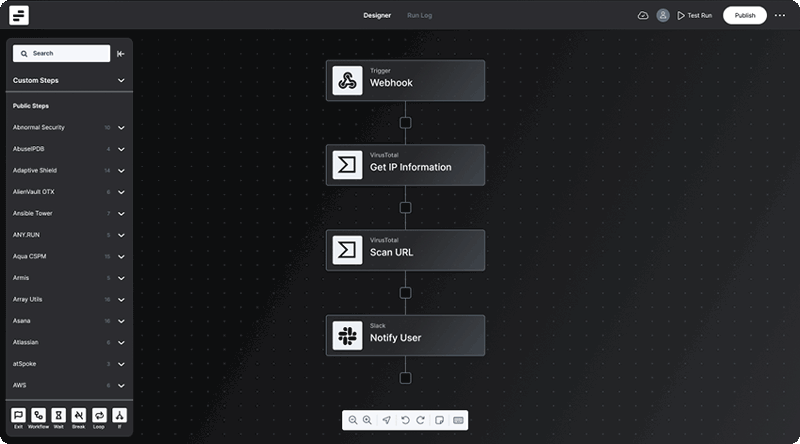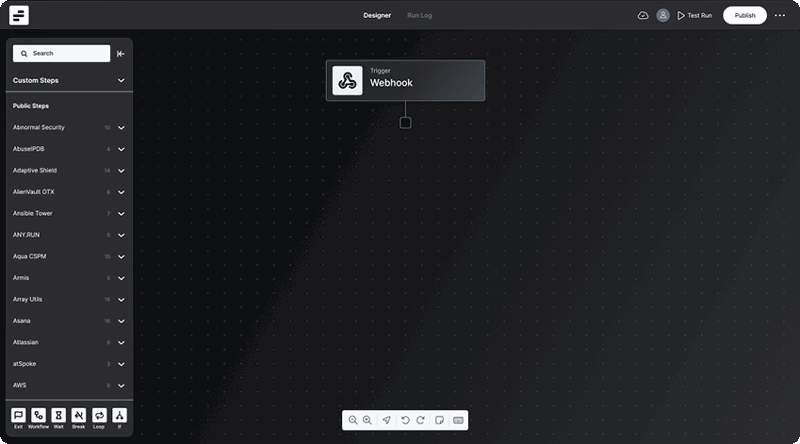
The distinction between legacy configuration panels and workflows is clear– where configuration panels are static, workflows are dynamic. Where panels force users into a one-size-fits-all mold, workflows adapt and mold themselves around the unique life cycle of each case. Workflows breathe life into the cybersecurity process, transforming it from a static chore into a dynamic dance of defense.
Torq’s Hyperautomation: A New Dawn in Cybersecurity
Our approach at Torq is a game-changer in case management. Instead of bolting automation onto dated case management systems, we’ve designed our case management system as an integral part of a powerful no-code automation foundation, ditching the messy bolt-on experience most SOC teams struggle with for an organically embedded case management process. What does this mean in practical terms? Let’s break it down with some clear examples:
1. Dynamic Case Tailoring: Consider a scenario where suspicious activity is detected from a list of IP addresses. With traditional systems, you might be constrained by pre-defined case layouts and parameters. With Torq, the case can be dynamically modified on the fly using workflows (i.e., surfacing relevant information or even remediation workflows as quick buttons to the case), adapting to intel as it comes in.
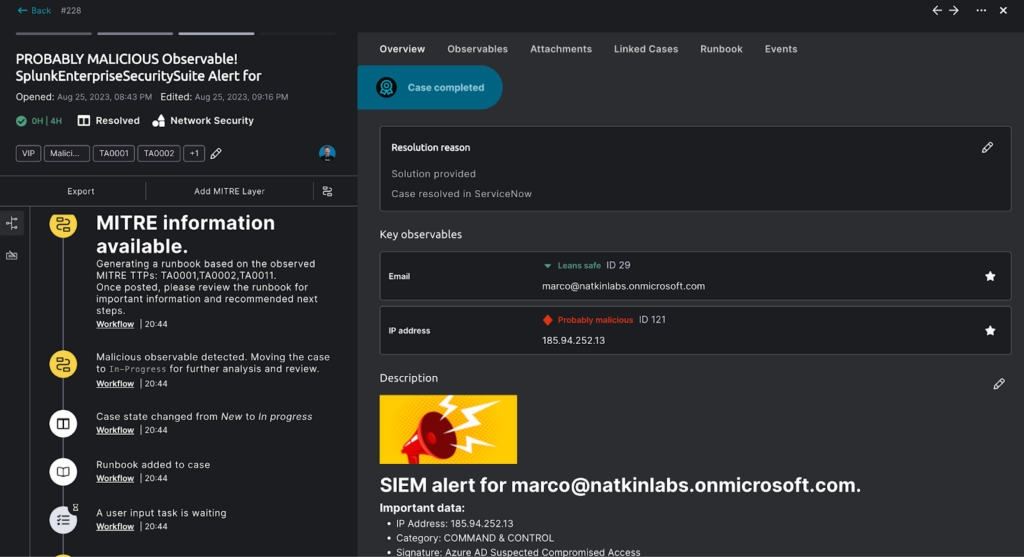
2. Intuitive Workflows Over Configuration Panels: Torq liberates SOC architects from sifting through overwhelming configuration panels. Want to add a new data enrichment step? Simply tweak the workflow. It’s as straightforward as connecting a new step in a visual editor, without a single line of code.

3. Automated Remediation Built-In: Remediation isn’t an afterthought; it’s part of the process. If the case’s workflow identifies a malicious email, it can automatically initiate remediation steps, like isolating affected systems or revoking email access, all within the same case environment.
4. Intelligence at Your Fingertips: Traditional SOAR systems separate threat intelligence from case data, requiring teams to hop between different platforms. With Torq, observables and indicators of compromise (IOCs) like IP addresses and file hashes are first-class citizens, easily accessible and actionable within the case.
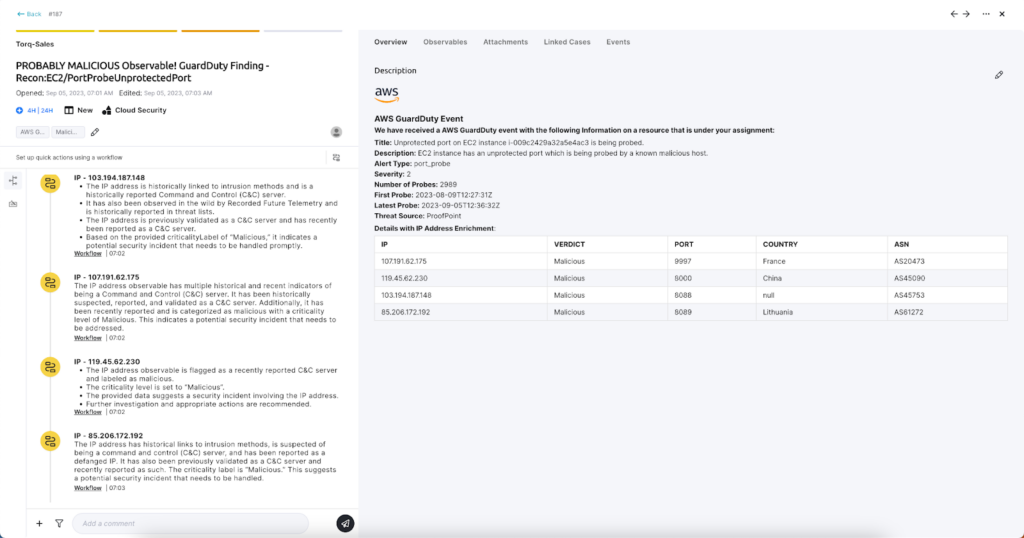
5. Lifecycle Triggers for Contextual Actions: The dynamic nature of Torq empowers SOC architects to set up triggers based on case milestones. For instance, when a case moves to the investigation stage, a workflow could automatically pull in additional forensic data, notify team leads, or modify the case’s layout as it evolves.
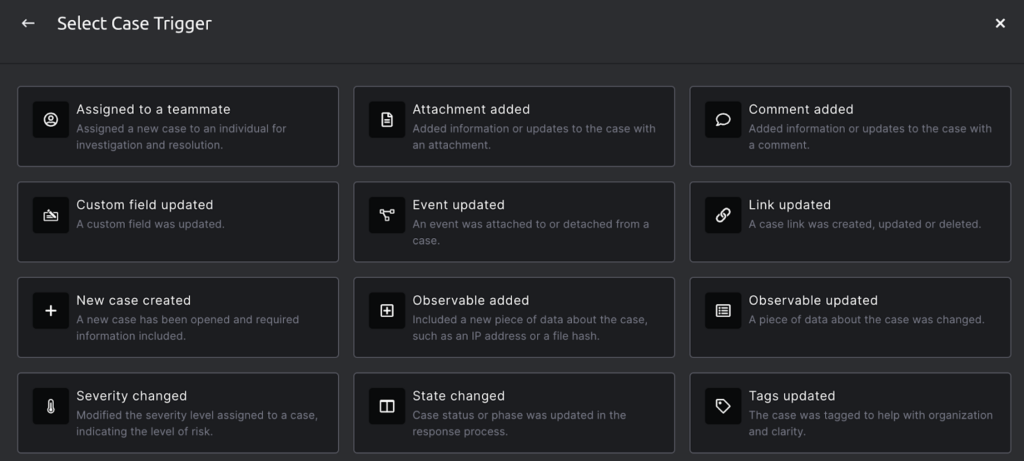
The power of automation is harnessed when it’s organically embedded into the case management process, not slapped on as an afterthought. This provides a more cohesive and efficient system for handling security events.
Our emphasis is not on rigid configuration panels that can stifle response flexibility. Instead, Torq’s system is designed to harness the full potential of dynamic workflows. We empower analysts and architects to craft unique response strategies tailored to specific threats and organizational needs. Security professionals are not restrained by the limitations of their tools. With Torq, they are free to innovate, adapt, and respond with unparalleled precision.
The Torq Difference: Dynamic Control Across the Lifecycle
Another thing that sets Torq apart is the degree of control we’ve built-in throughout the case’s lifecycle. In traditional SOAR platforms, playbooks–though groundbreaking for their time– are often employed merely as remediation tools. Torq’s approach is more holistic. Every stage, from detection to analysis and finally to remediation, can be steered by dynamic workflows. This ensures that the system is always in tune with what’s occuring in a case, leading to spot-on accuracy and timely responses.
Furthermore, Torq’s platform eliminates the need for redundant back-and-forth between separate systems. Integrating no-code automation into the fabric of case management means that every action, automated or manual, is executed within a unified environment. It’s a symphony orchestra where every instrument, no matter how disparate, plays in perfect harmony.
The Future of Hyperautomation is Here
We’re at a turning point in cybersecurity. On the one hand, threats are multiplying and evolving at a pace that’s hard to keep up with. Conversely, the tools and systems at our disposal are often found wanting. But with Torq’s innovative approach to case management, the tide is turning.
By placing powerful hyperautomation at the heart of our platform, we’ve ushered in a new era in cybersecurity operations that prioritizes agility, precision, and efficiency. Legacy SOAR platforms had their moment in the sun. As the landscape changes, so must our tools. Torq is lighting the way to a safer, more secure digital future in this fast-changing arena.
Want to learn more about how Torq can dramatically enhance your security workflows so you can stay ahead of emerging threats? Test drive Torq Hyperautomation, here: https://torq.io/demo/




