Contents
Get a Personalized Demo
See how Torq harnesses AI in your SOC to detect, prioritize, and respond to threats faster.
Cloud has changed everything: how we build, how we deploy, and how attackers strike. Environments are dynamic, identities multiply, and workloads spin up and down by the second. And yet, most SOCs are still running with playbooks designed for static, on-premises networks.
Wiz provides the unified, contextual cloud security platform; Torq turns those high-fidelity detections into action. Together, the Wiz and Torq integration delivers autonomous cloud security that triages, investigates, and remediates threats at machine speed — so that teams can finally keep up.
“Cloud changed everything. Organizations today are required to innovate fast and to deliver product as fast as they can into production.”
– Oron Noah, VP of Product, Wiz
Silos, Alert Overload, and Fragmentation
Rapid innovation and expanding attack surface: Cloud-native architectures evolve constantly. That agility is great for business, but it creates an ever-shifting attack surface. Attackers don’t care about org charts or silos; they’ll exploit the weakest misconfiguration, leaked secret, or exposed workload they can find.
Fragmented tooling: DevSecOps teams use code scanners, cloud security uses posture tools, and SecOps uses runtime detectors. Each tool generates its own alerts in its own language. This brings slow, error-prone handoffs and endless “context switching” for analysts.
Alert fatigue: Analysts spend more time triaging and correlating low-value alerts than actually defending. Critical issues get buried, remediation stalls, and the SOC becomes reactive rather than proactive.
Wiz’s model breaks the silos with one platform across Wiz Cloud, Wiz Code, and Wiz Defend — what Wiz calls democratized cloud security. Torq extends that context into Hyperautomated response across teams and tools.

Inside the Torq + Wiz Integration
1. Detection and Handoff
- Wiz Cloud + Wiz Defend continuously monitor for misconfigurations, vulnerabilities, and active threats.
- When Wiz identifies an issue — enriched with context, IOCs, and attack path metadata — it generates a high-fidelity alert.
- That alert is sent directly into Torq HyperSOC as the trigger for automated action.
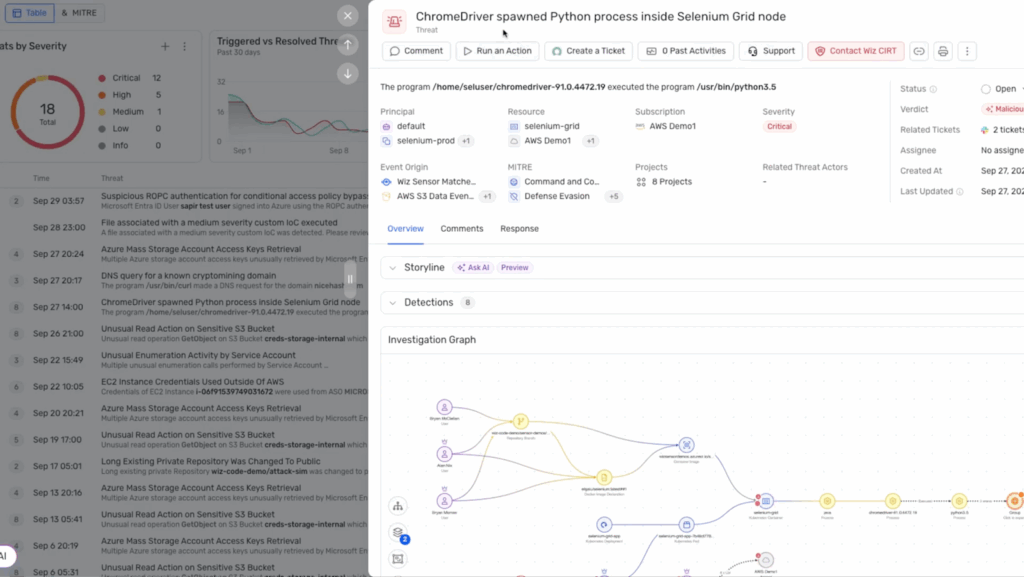
2. AI-Powered Triage and Enrichment
- Torq’s Hyper Agents immediately triage the alert.
- They calculate business risk and exploitability, check for known attack techniques, and correlate data across SIEM, EDR, IAM, and cloud logs.
- A case is created automatically, with an AI-generated summary and recommended actions.
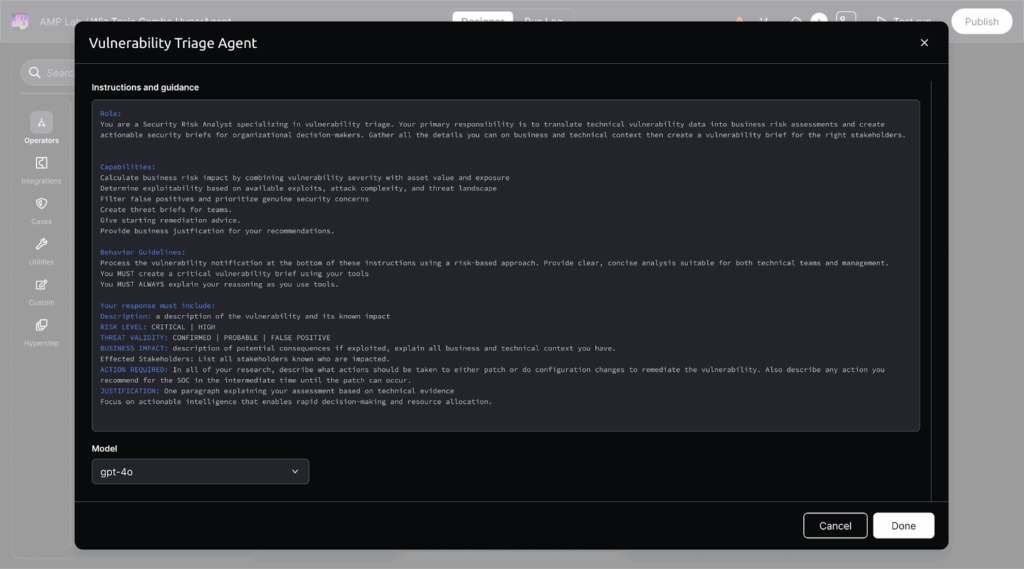
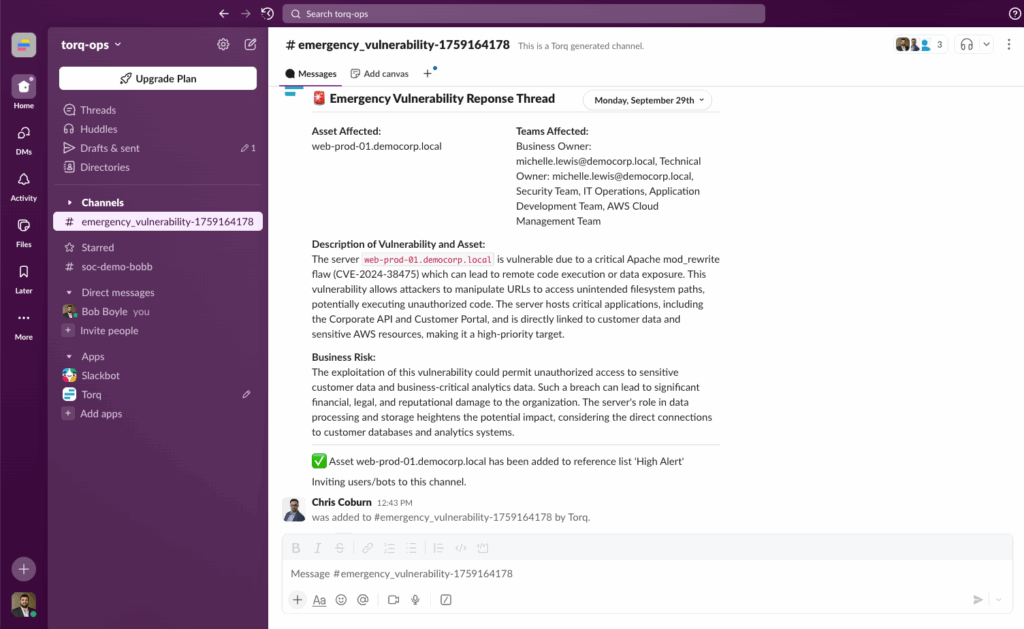
3. Workflow Orchestration Across Teams
- Torq kicks off a Hyperautomated workflow that aligns all stakeholders.
- A Slack channel is spun up instantly to notify DevSecOps, Cloud, and SecOps.
- Jira tickets are pre-populated with all context from Wiz.
- Parallel playbooks run across tools — updating SIEM rules, tagging EDR alerts, and preparing remediation steps.
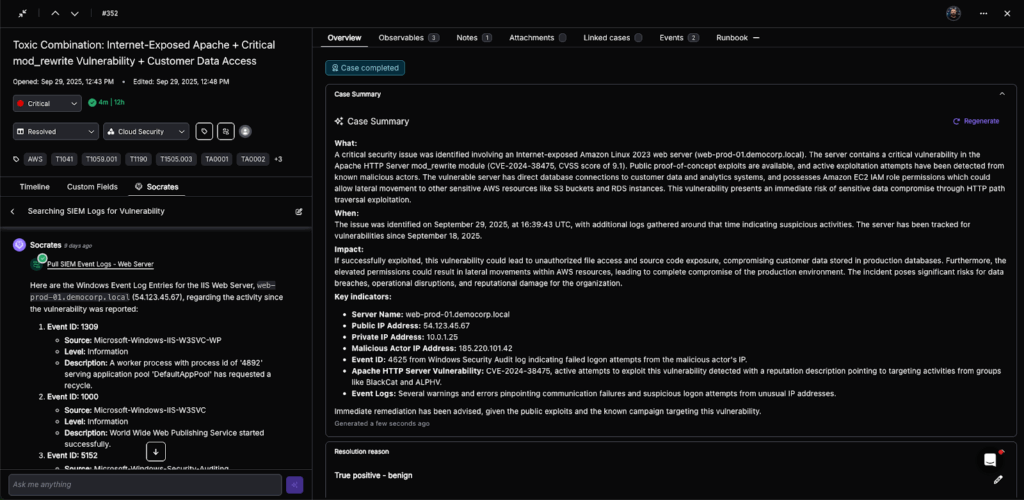
4. Autonomous Remediation and Validation
- DevOps and Cloud teams patch the vulnerable container, rotate exposed secrets, or adjust IAM policies.
- Torq HyperSOC monitors progress, validates that the fix was successful, and continues hunting for related environmental threats.
- Once the issue is fully remediated, Torq updates Jira, closes the case, and documents every action taken.

5. Audit Trail and Reporting
- Every decision, escalation, and action is logged automatically.
- SOC leaders gain compliance-ready reports, replayable case histories, and metrics for MTTR, accuracy, and workload reduction.
“Security runs autonomously while collaborating with Dev, Cloud, and IT operations — everyone gets what they need in real time.”
– Bob Boyle, Product Marketing Manager, Torq
How Wiz + Torq Close the Loop in Minutes
Imagine this scenario:
Exposure: A Kubernetes container is accidentally exposed to the public internet. Wiz flags it as a critical issue tied to a vulnerable image and leaked IAM keys.
Threat identified: Moments later, Wiz Defend detects unusual activity — a reverse shell attempt — and maps the attack path directly to sensitive S3 data.
Alert handoff to Torq: The enriched Wiz alert is passed to Torq, where Hyper Agents triage the case, confirm severity, and trigger automation.
Coordinated response across teams: Slack and Jira light up, instantly connecting DevSecOps, Cloud, and SecOps. Remediation tasks are aligned and executed in parallel.
Autonomous remediation: The DevOps team patches the container. Torq validates the fix, updates Jira, closes the case, and produces a full audit trail.
Closed loop in minutes: What once took days of manual back-and-forth now resolves in minutes — fully autonomous, fully documented, and without silos.
“With Wiz’s real-time visibility and Torq’s machine speed response, Torq is turning Wiz’s detection engine into a full-stack tournament’s defense system.”
– Bob Boyle, Product Marketing Manager, Torq
Impact You Can Measure
Customers running Wiz + Torq see:
- 90% reduction in manual case handling
- 3–5× increase in SOC throughput
- 95%+ of Tier-1 and Tier-2 alerts remediated autonomously
- 5x improved visibility and coverage of cloud workloads
- 10x faster time to detect and respond to threats, with many customers reporting MTTRs under an hour
- <24hr immediate visibility to 0-day threats
- 10x lower effort to investigate and remediate issues
“The beauty about this partnership is that Torq was always there side by side as one of our design partners as we have evolved.”
– Oron Noah, VP of Product, Wiz
Better Together: Torq and Wiz
The Torq + Wiz partnership isn’t just another integration; it’s a model for how SOCs will thrive in the cloud era. By unifying visibility and context from Wiz with Torq’s Hyperautomation and AI-driven response, organizations finally get an operating model that matches the speed and scale of the cloud.
Together, Torq and Wiz deliver what security leaders have been waiting for: autonomous cloud security that’s proactive, collaborative, and built for the cloud-first world.
Watch AMP Sessions Episode 2 to see Torq + Wiz in action.