Contents
Get a Personalized Demo
See how Torq harnesses AI in your SOC to detect, prioritize, and respond to threats faster.
The SANS 2025 SOC Survey is a reality check: despite years of investment in shiny new tools and all the talk of AI and automation, most security teams are stuck in firefighting mode, drowning in unstructured data, and burning out talent.
The tools may be new, but under the hood, most SOCs still struggle with the same structural issues they were five years ago: reactive workflows, manual processes, and underwhelming AI adoption. This isn’t a technology shortage — it’s an execution failure.
Without strategic change, your SOC’s maturity progress will stay stalled. So what’s the fix?
The 5 Critical SOC Failures in 2025
1. Reactive, Alert-Triggered Response
According to the SANS 2025 SOC Survey, 85% of SOCs primarily trigger incident response from endpoint alerts, rather than proactive detection. The report notes that even what’s labeled “threat hunting” is often just retroactive analysis, not true, hypothesis-driven investigation. While most SOCs have plentiful threat intelligence available, it’s often left on the shelf or used unevenly. The result: teams stay trapped in reactive mode, moving only after the alarm sounds — when the attacker already has a head start.
2. Data Dumping Without a Plan
42% of SOCs shove all incoming data into a SIEM, with no plan to retrieve or analyze it. This “visibility strategy that risks collapsing under its own weight” creates a major challenge for analysis and response. Investigations slow down, visibility drops, and SIEM costs explode — all while real threats hide in the noise. Not to mention that SOCs are paying to hoard all of that unused clutter.
3. Underperforming AI Adoption
42% of SOCs are rolling out AI/ML tools “out of the box” with zero customization — and AI/ML tools ranked at the bottom of the satisfaction list. Without tuning and integration, it’s just another underutilized expense. This unmanaged adoption means that a significant portion of AI is used without being part of defined security operations, turning a promising technology into a source of frustration, wasted budget, and added risk.
4. Manual, Time-Consuming Reporting
69% of SOCs still report SOC metrics manually — and nearly half say it’s too time-consuming. Analysts spend hours compiling data for reports instead of chasing threats. Leadership gets stale data, and optimization efforts stall.
5. A Retention Crisis
Although talent shortages remain a top challenge for SOCs, a staggering 62% of SOC pros say their organization isn’t doing enough to keep top personnel. The most common tenure for SOC staff is only 3-5 years. That’s your most valuable skilled asset walking out the door because they’re burned out, bored, or both. Without providing clear career paths and meaningful work, you’re just training people for their next job somewhere else, which creates a constant cycle of recruitment and loss of institutional knowledge.
How Torq HyperSOC Solves the SOC Nightmare
The SANS SOC Survey data doesn’t just show where SOCs are stuck; it points to what’s missing: strategic automation and integrated AI that actually executes. With an agentic AI-driven AI SOC Analyst and Hyperautomated case management, Torq HyperSOC™ turns SOCs from reactive to autonomous, freeing security teams from mundane, repetitive tasks for more strategic work.

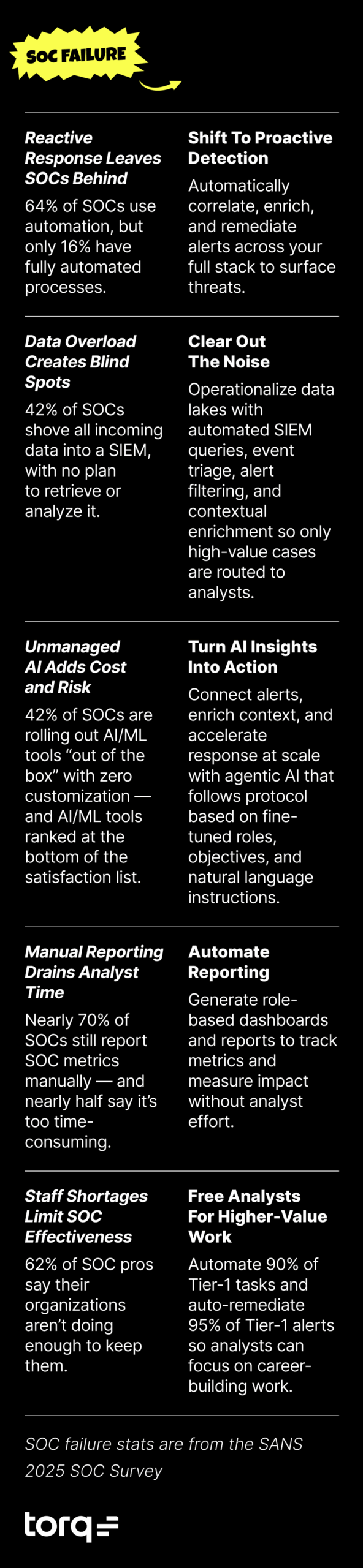
1. Proactive Detection, Faster Response
Thanks to full-stack integrations, Torq HyperSOC collects and analyzes data from XDR, SIEM, EDR, and other security platforms, automatically correlating alerts and enriching them with internal and external threat intelligence. Automated workflows can escalate, contain, and remediate threats immediately, including sandboxing suspicious files or URLs when deeper analysis is needed.
Analysts spend less time manually digging through logs and more time on high-value investigations, while observables, relationship tracking, and automated case management help shrink mean time to detect (MTTD) and mean time to respond (MTTR) and scale expert-level threat hunting across the enterprise.
2. Clear Out the Noise
Torq ingests, analyzes, and organizes data, intel, and alerts from across your entire security stack. Leveraging Hyperautomated workflows and agentic AI, Torq enables security teams to operationalize data regardless of where it is being stored. Automated workflows parse through endless SIEM logs, bubbling up only the most important events, while AI Agents autonomously triage, enrich, and create high-value, fully contextualized cases.
This gives organizations the freedom to reduce SIEM costs by offloading mass data dumps into more cost-efficient next-gen data lakes, while Torq acts as the glue in the middle — normalizing and correlating data from multiple sources, without impacting existing processes or sacrificing security data gaps for cost-savings.
3. Deeply Embedded Agentic AI That Works for You
Standalone AI tools lack the visibility to connect alerts, enrich context, and provide meaningful insights. Torq’s agentic AI is deeply embedded in our platform, which acts as the connective tissue across your security stack, correlating data, surfacing insights, and accelerating response actions at scale. Much like onboarding a new human analyst to the security team, each AI Agent is given clear roles, objectives, access to a specific set of tools necessary to complete their task, and is instructed to use historical context to better understand how various use cases are typically handled within the organization.
Torq gives security leaders the flexibility to tailor agentic AI to fit seamlessly into the organization as a finely tuned force-multiplier, a fatigue-resistent expert analyst, or simply an extra set of helping hands.
4. Instant, Automated Reporting
Torq dashboards give security leaders a real-time view of key metrics like incident resolution times, case closures, productivity gains, and cost savings, so teams can measure the impact of their security operations and automation efforts.
With an intuitive and completely customizable drag-and-drop interface, dashboards are easy to create, track trends, and export for deeper analysis, all without manual configuration or coding. Role-based reports can instantly generate executive-ready dashboards — no analyst effort required.
5. A Better SOC Day-to-Day
The autonomous SOC doesn’t replace analysts; it empowers them. By automatically triaging, contextualizing, and investigating alerts, Torq HyperSOC removes the constant reactive grind and frees security teams to focus on meaningful, strategic, and creative work they joined the field to do, like threat hunting, detection engineering, and deep analysis.
This not only makes analysts more engaged and more likely to stay — reducing turnover — but also boosts efficiency by eliminating wasted time on grunt work and rote tasks.
Torq HyperSOC is the first solution we’ve seen that effectively enables SOC professionals to mitigate issues including alert fatigue, false positives, staff burnout, and attrition. We are also impressed by how its AI augmentation capabilities empower these staff members to be much more proactive about fortifying the security perimeter.”
– Chris Kissel, Vice President, Security & Trust Products, IDC Research
Shift Your SOC into High Gear
The SANS 2025 SOC Survey makes it clear that progress in most SOCs isn’t stalled because they lack tools — it’s stalled because those tools aren’t integrated, automated, or built for action.
Torq HyperSOC replaces fragmented workflows, disconnected data, and manual bottlenecks with integrated, end-to-end, AI-driven Hyperautomation across the SOC. It’s how you stop chasing alerts, start hunting threats, and defend at scale. In other words: the SOCs that break free from react-mode will be the ones that automate the busywork and apply their human talent where it matters most.
Don’t die. Learn how HyperSOC saves security teams, transforms strategy, and proves business impact.








