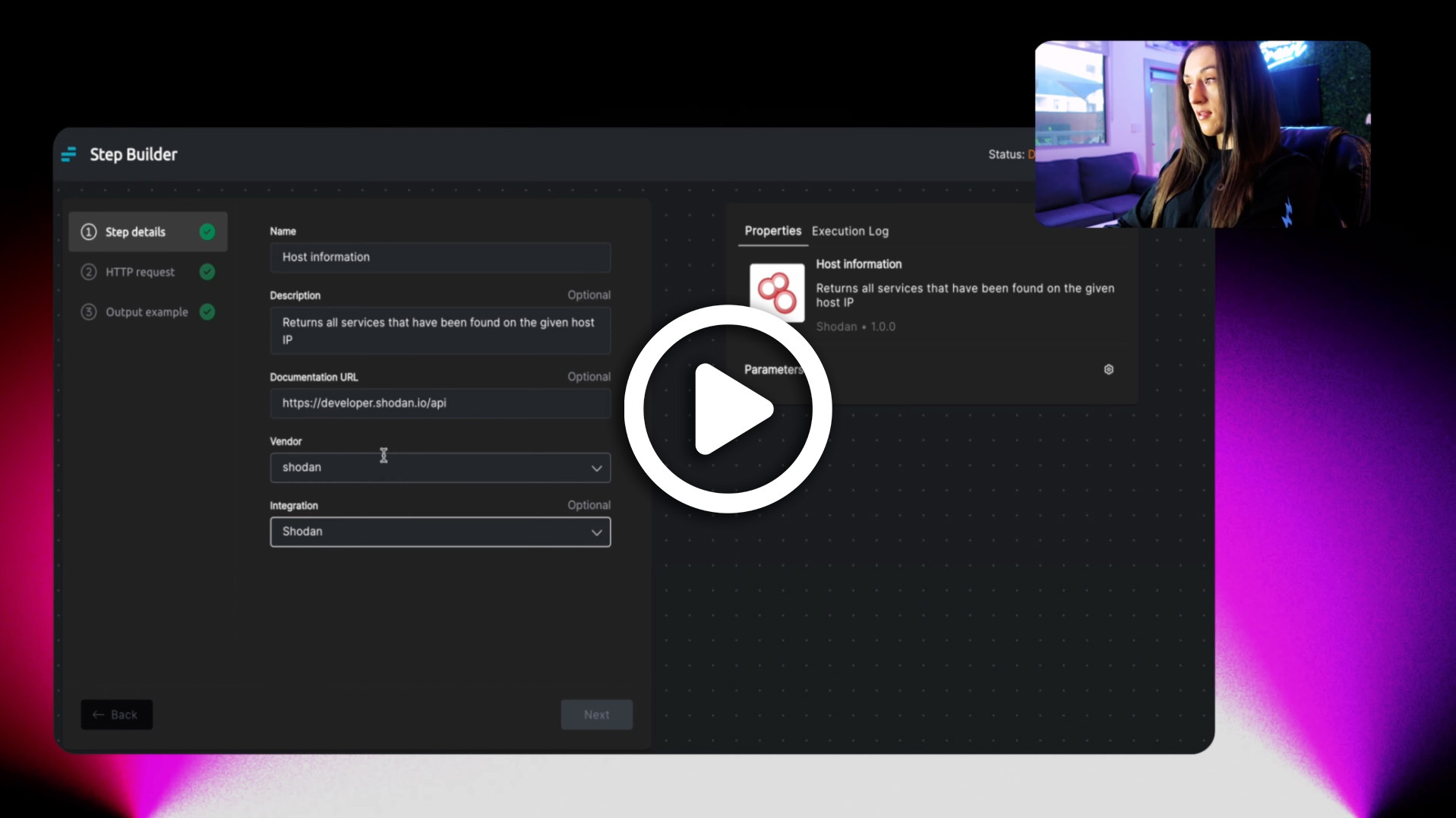
Hyperautomation
How to Save Your SOC Analysts From Alert Fatigue
SecOps teams face an unyielding barrage of security signals raised by various systems and tools....
Read More