Contents
Get a Personalized Demo
See how Torq harnesses AI in your SOC to detect, prioritize, and respond to threats faster.
Torq AMP spotlights the partners redefining what’s possible in security operations. Each partner brings a unique strength that seamlessly extends Torq’s autonomous SOC platform. Together, these partnerships help SOC teams achieve speed, accuracy, and scale that were once out of reach. Explore the future of SOC in the AMP’d Sessions video series.
For years, security teams have been trapped by legacy SIEM and SOAR solutions. They’re forced to make compromises — slashing data retention to 30 days to control costs, spending more time tuning brittle tools than hunting threats, and manually bridging the gap between a noisy alert and a meaningful response.
In the latest episode of Torq’s AMP’d Sessions, we sat down with Mike Olsen, Director of Partner Solutions Engineering at Panther, to discuss how customers are moving on from this broken model. They’re modernizing their SecOps data pipeline with Panther’s cloud-native data lake and Torq’s autonomous response.
Together, Torq and Panther deliver a closed-loop system that moves from detection to remediation at machine speed. Here’s how.
Panther’s Cloud-Native Data Lake: Built for the Modern SOC
The core problem with legacy SIEMs is their architecture. They weren’t built for the cloud era, forcing teams to choose between cost and visibility. Panther takes a different approach.
The foundation to the Panther platform is leveraging a cloud-native, modern data lake architecture. This serverless approach provides four key benefits:
- Limitless scale: “We have a customer that’s ingesting 40 terabytes daily,” Olsen noted. Teams no longer have to make compromises on what security logs to keep.
- Long-term retention: Instead of 30 days, Panther customers can retain data for at least a year in hot storage, enabling threat hunting and long-tail investigations without requiring rehydration.
- Data ownership: Your data stays in your cloud. Panther supports a “bring your own data lake” model, avoiding the vendor lock-in of traditional SIEM.
- Separation of compute and storage: This allows teams to “query petabytes of data at peak performance” without bogging down the system.
On top of this data lake, Panther employs a “Detection-as-Code” model. This gives teams the flexibility to write, tune, and deploy detections using Python, a low-code builder, or even AI-assisted creation, all managed in a CI/CD pipeline.
How Torq Turns Detection into Autonomous Response
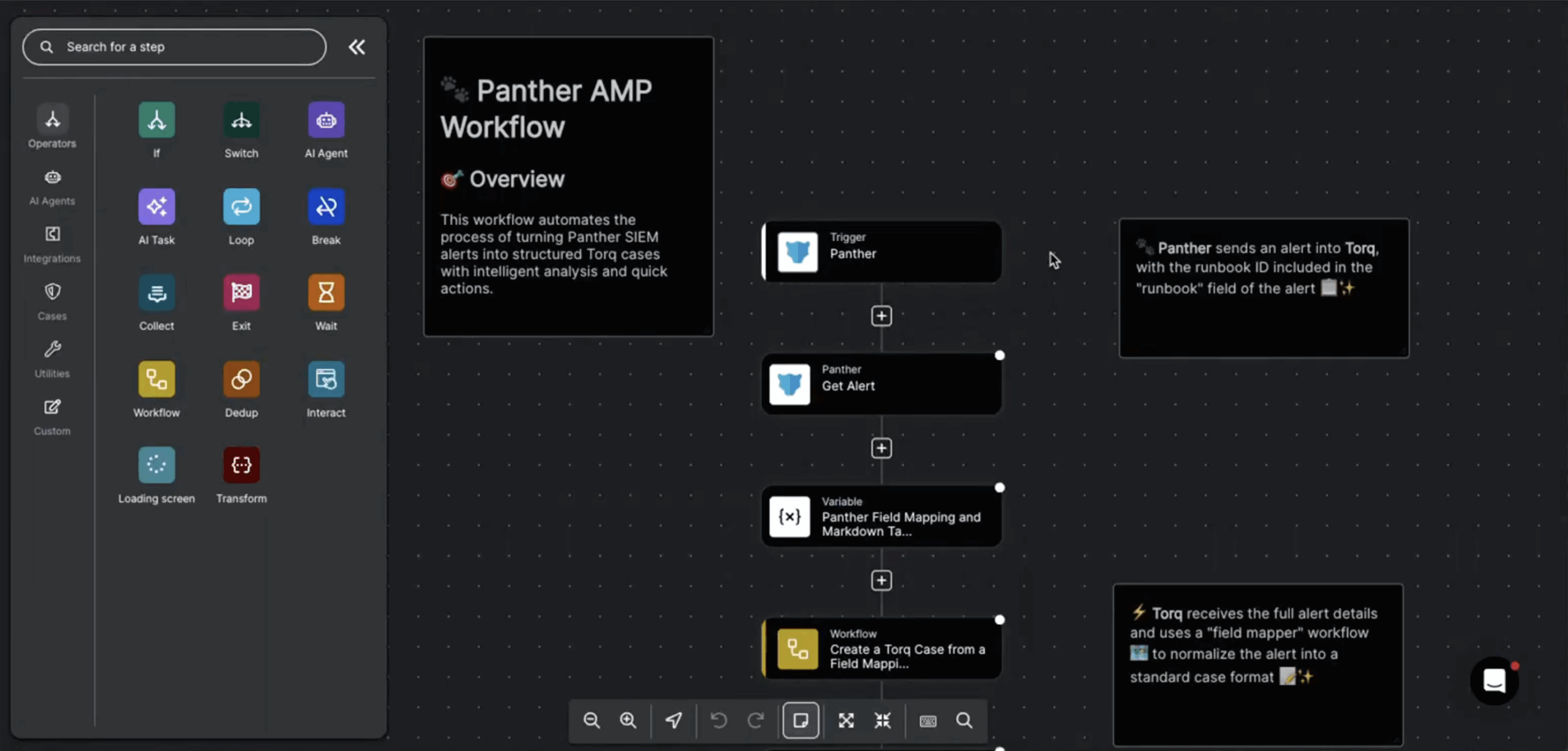
Panther provides the high-fidelity detection and AI-driven triage; Torq provides the autonomous action. When Panther generates a high-confidence alert, it doesn’t just send a raw log. It sends a rich, AI-triaged case summary. Torq HyperSOC™ ingests this data and hands it to Socrates, Torq’s AI SOC Analyst. This initiates an AI-to-AI communication that is fully explainable and auditable.
Socrates reasons through Panther’s findings, orchestrates the necessary response actions through Hyperautomated workflows, and documents every step — transforming Panther’s T1-to-T2 analyst elevation into a T3 strategic “analyst-as-validator” model.
“Panther identifies what is happening, and then Torq decides what to do about it next.”
– Bob Boyle, Product Marketing Manager, Torq
Inside the Demo: From Data Lake to Autonomous Remediation
The AMP’d session demo showcased this closed-loop system in action, remediating a sophisticated identity-based threat from start to finish.
1. The Detection (Panther)
A high-fidelity correlation rule fired in Panther, combining two separate events:
- Event 1: An Okta login from a “watch list” country (France).
- Event 2: An M365 enumeration activity (like Get Users or List Admins) from the same user within 30 minutes.
Individually, these might be noise. Together, they could be something more. Panther’s AI Triage autonomously analyzed the events, generated a summary: “This is an anomalous login. The user, Timothy, is based in the U.S., not France,” and exposed its thinking steps for human validation.
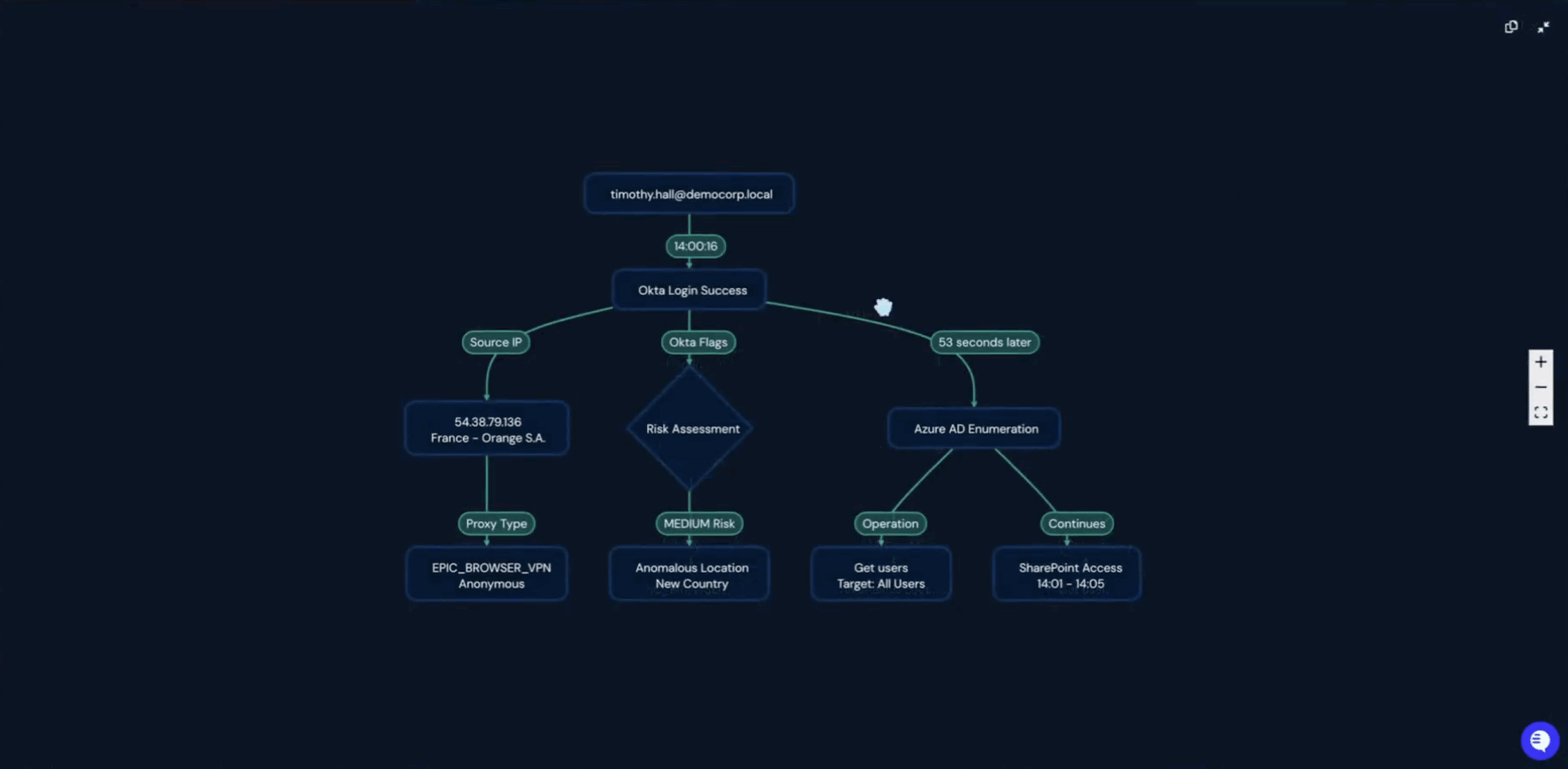
2. The AI-to-AI Handoff (Torq)
Torq ingested the correlated alert and Panther’s AI triage summary.
- AI-to-AI: A Torq AI Agent evaluated Panther’s findings: “Based on Panther’s analysis, is this showing signs of persistence?”
- The verdict: The Torq Agent confirmed “Recurrence: True,” mapped the attack to the MITRE Initial Access tactic, and automatically escalated the new case in Torq’s Case Management platform to ‘Critical’ priority.
3. The Autonomous Response (Socrates)
The critical case was automatically assigned to Socrates, Torq’s AI SOC Analyst, which followed its autonomous remediation runbook:
- Investigation: Socrates reached back into Panther, querying the data lake for more user activity logs to broaden the investigation.
- User verification: Torq’s communication agent autonomously interviewed the user, Timothy, directly in Slack: “Hey, Timothy, did you log in from France recently?” Timothy’s reply: “No.”
- Containment: Based on that “No,” Socrates immediately executed its containment plan: it disabled the user’s Okta account and added the malicious IP address to a company-wide blocklist.
- Notification: For business continuity, Socrates identified Timothy’s manager and sent them a Slack message: “Hey, there’s an active SOC incident… Timothy’s account is locked, and he won’t be able to respond.”
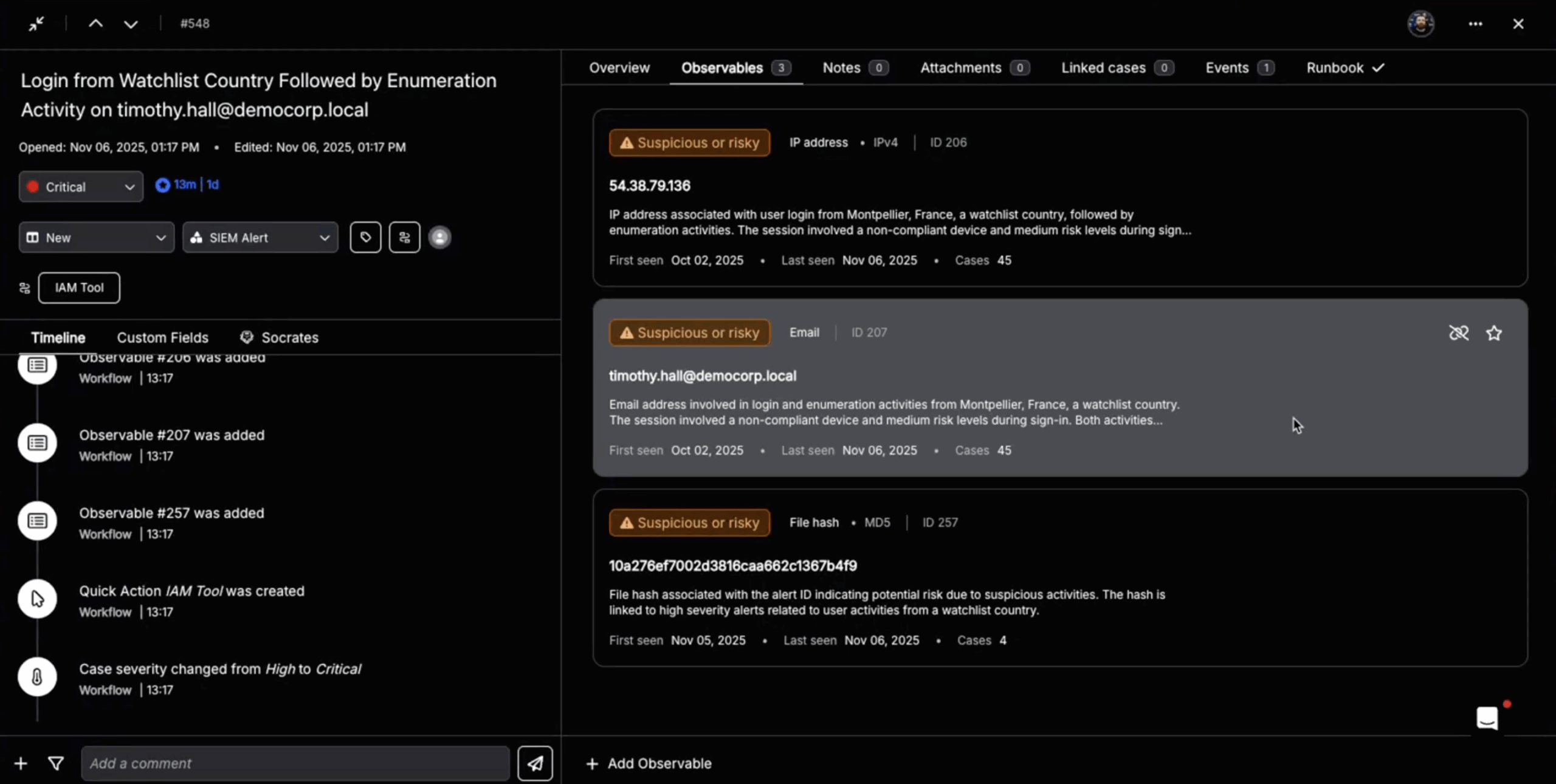
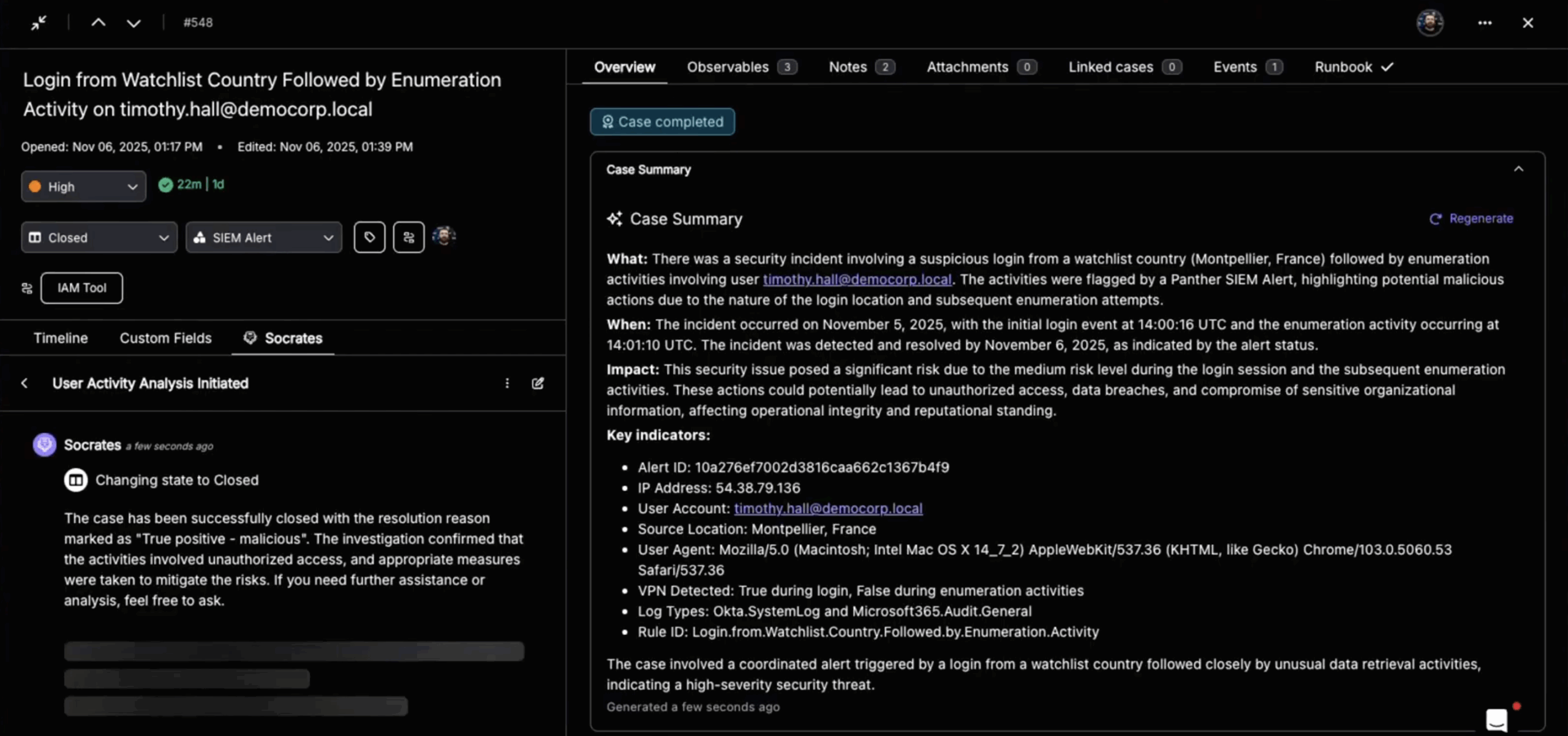
4. The Closed-Loop SecOps Pipeline
The entire cybersecurity lifecycle — from initial detection to full containment — happened in seconds. Every AI thought process, query, and action was logged in an immutable audit trail. The case was then escalated to a human analyst, not to work the alert, but to simply validate the autonomous actions already taken and close the case.
This partnership fundamentally changes the SecOps paradigm. It’s no longer a linear, manual handoff from a legacy SIEM to a brittle SOAR. It’s a single, intelligent, and closed-loop system, or what we like to call an autonomous SOC.
“What I’m most amped about is the combination of Panther’s AI-driven context from detection, and then combining that with Torq’s Hyperautomation for response. It’s really closing that loop and eliminating the manual gap between detection and action.”
– Mike Olsen, Director of Partner Solutions Engineering, Panther
Better Together: Torq + Panther
For security teams, the Torq and Panther partnership means:
- Limitless scale: Ingest and retain all your security data in Panther’s data lake.
- AI-triaged detections: Eliminate noise with Panther’s high-fidelity, AI-analyzed alerts.
- AI-to-AI communication: Let Panther’s detection agents talk directly to Torq’s response agents for autonomous escalation.
- Autonomous remediation: Go beyond simple automation to fully remediate threats — from investigation to containment and user verification — without human intervention.
- End-to-end auditability: Maintain full, explainable audit logs of every AI decision and action, from detection to response.
Watch this workflow unfold in real time in the Torq + Panther AMP’d Session.










