3,000+ alerts a day. One missed click away from disaster.
A SOC analyst descends into an endless abyss of alerts riddled with false positives, spawning faster than they can be closed — and buried somewhere in all that noise, something dangerous is lurking.
A neverending nightmare dwells in the fluorescent glow of enterprise SOC screens: 3,000 alerts per day across 28+ tools — 40% of which vanish into darkness, never to be investigated.1 Each messy shift handoff, each hour of the grind, each growing backlog feeds the creeping fear: the one alert you missed is the one that will take the business down.
BURIED ALIVE
Alert fatigue and data dumping
Enterprises are battling over 3,000 alerts per day, across 28+ tools.1Software Analyst Cyber Research’s 2025 AI SOC Industry Report by Francis Odum and Rafal Kitab
42% of SOCs shove all incoming data into a SIEM, with no plan to retrieve or analyze it.2SANS 2025 SOC Survey
THE SILENT SCREAM
Overwhelm leads to missed threats
61% of teams have ignored alerts that turned out to be critical.1Software Analyst Cyber Research’s 2025 AI SOC Industry Report by Francis Odum and Rafal Kitab
CODE RED
Reactive firefighting
85% of SOCs primarily trigger incident response from endpoint alerts, rather than proactive detection.2SANS 2025 SOC Survey
THE EMPTY CHAIR
Burnout and turnover
62% of SOC pros say their organization isn’t doing enough to keep top personnel.2SANS 2025 SOC Survey
The most common tenure for SOC staff is only 3-5 years.2SANS 2025 SOC Survey

Sleep Peacefully.
We’ll Leave the Torq On.

Sleep Peacefully.
We’ll Leave the Torq On.
CLEAR OUT THE NOISE
Intelligent Case Management
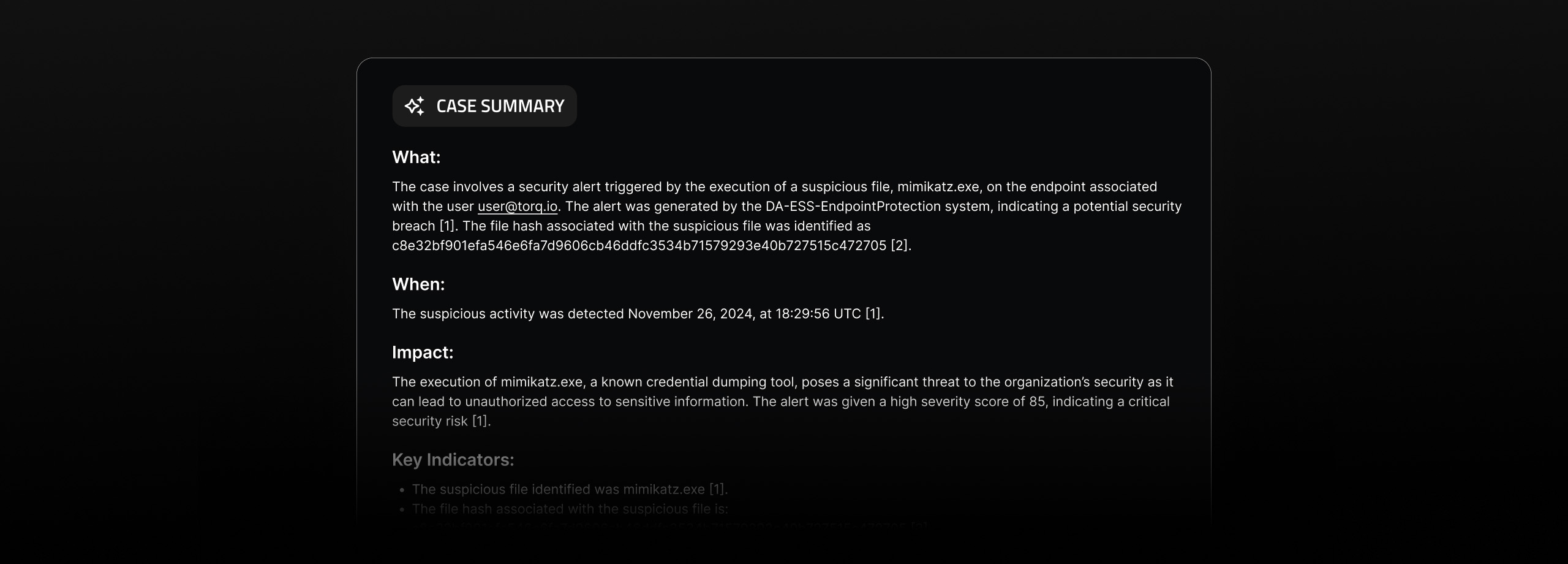
Torq’s AI-driven case management system transforms how SOC teams handle alerts by automating triage, enrichment, and prioritization so analysts focus only on what matters. Every case is dynamically scored by severity, correlated with contextual telemetry and threat intel, and either routed to the right responder or resolved autonomously with predefined playbooks.
NEVER MISS A REAL THREAT
Automated Investigation & Remediation
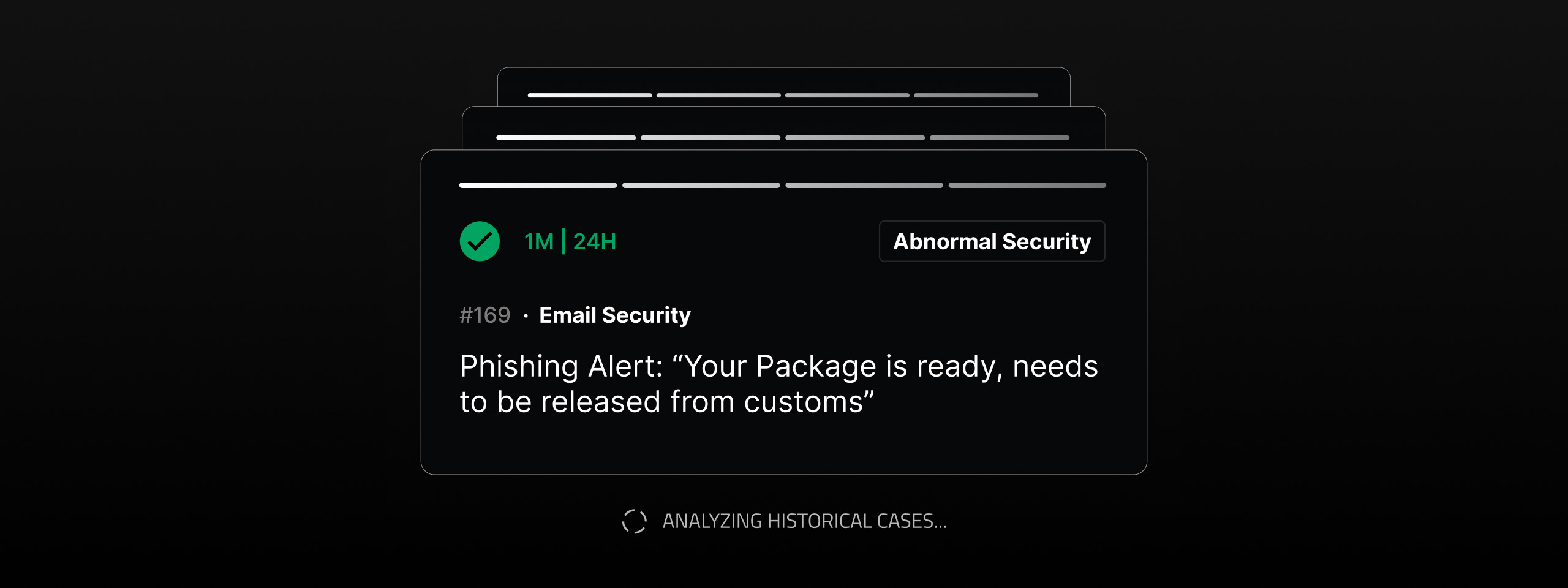
Automated investigation in Torq HyperSOC™ connects the dots faster than any human could. It uncovers hidden attack patterns across EDR, SIEM, cloud, and identity tools, surfacing the full scope of a threat in seconds. And Torq HyperSOC™ doesn’t just detect threats, it acts on them too. It executes containment, remediation, and recovery actions across your entire security stack autonomously, or intelligently escalates critical cases for human-in-the-loop intervention, drastically reducing MTTR.
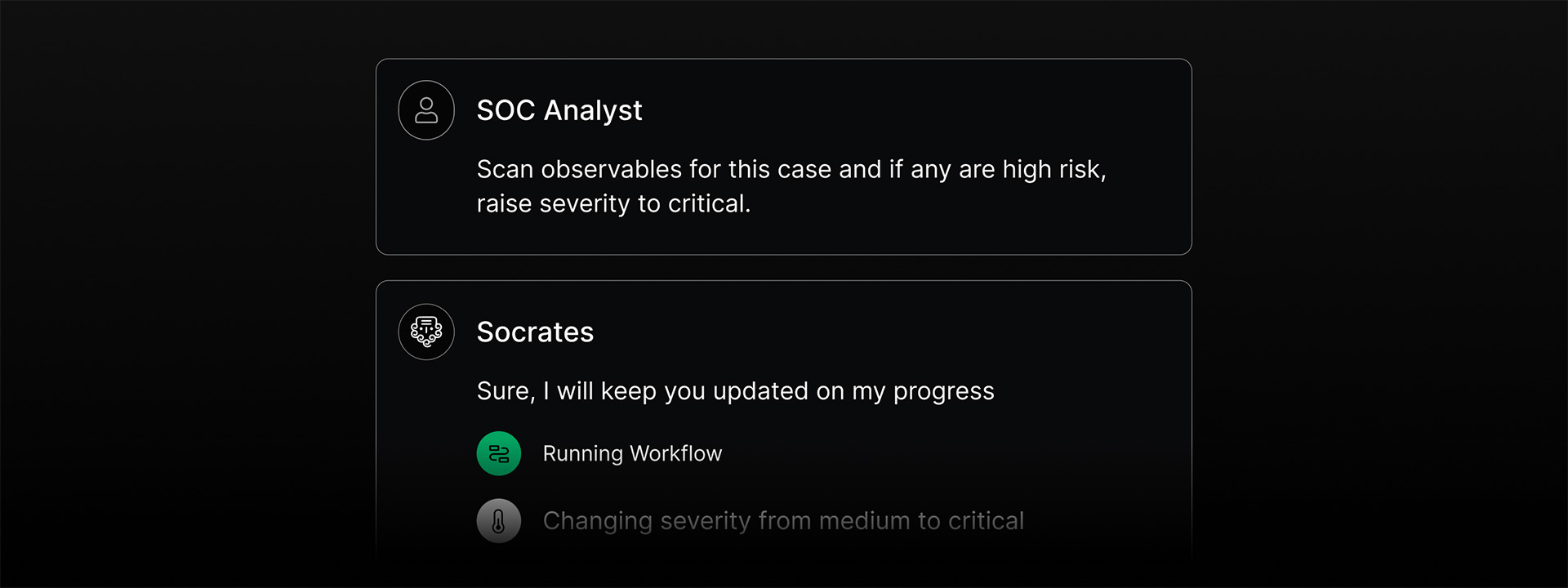
SHIFT TO A PROACTIVE POSTURE
AI Planning & Execution
Torq HyperSOC™ uses agentic AI to plan and execute deeply customized investigations and responses. It learns from past incidents, recognizes familiar threat patterns, and dynamically adapts to new attack vectors, creating precision response plans that evolve with your environment. Human analysts can spend more time on proactive, high-value investigations so your team stays ahead.
FREE YOUR TEAM UP FOR THE “COOL STUFF”
AI SOC Analyst
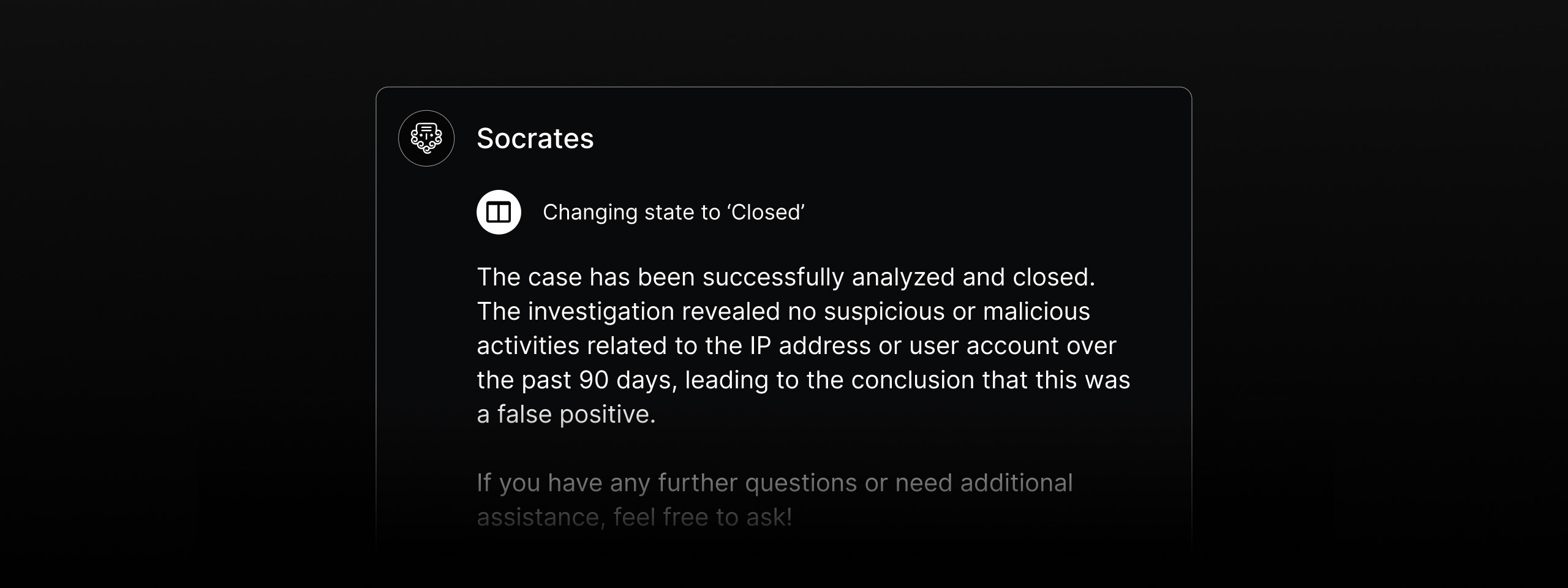
Meet Socrates — the AI SOC Analyst that plans, investigates, and remediates threats autonomously. It orchestrates a Multi-Agent System (MAS) of specialized AI agents to handle nearly all Tier-1 tasks so you can focus the valuable, limited resource of human expertise on creative, rewarding, and strategic work.
1 Software Analyst Cyber Research’s 2025 AI SOC Industry Report by Francis Odum and Rafal Kitab
2 SANS 2025 SOC Survey