Contents
Get a Personalized Demo
See how Torq harnesses AI in your SOC to detect, prioritize, and respond to threats faster.
When a cyberattack occurs, every second counts. Metrics like Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR) are critical benchmarks in cybersecurity, helping organizations evaluate the effectiveness of their Security Operations Centers (SOCs). But what’s the difference between MTTD vs MTTR, and why do they matter?
Understanding and improving these metrics through strategic investments in security automation can significantly elevate your security posture, minimize damage, and keep your organization safe from threats.
MTTD vs. MTTR in Cybersecurity
Mean Time to Detect and Mean Time to Respond are both fundamental KPIs in cybersecurity, but each measures something distinct.
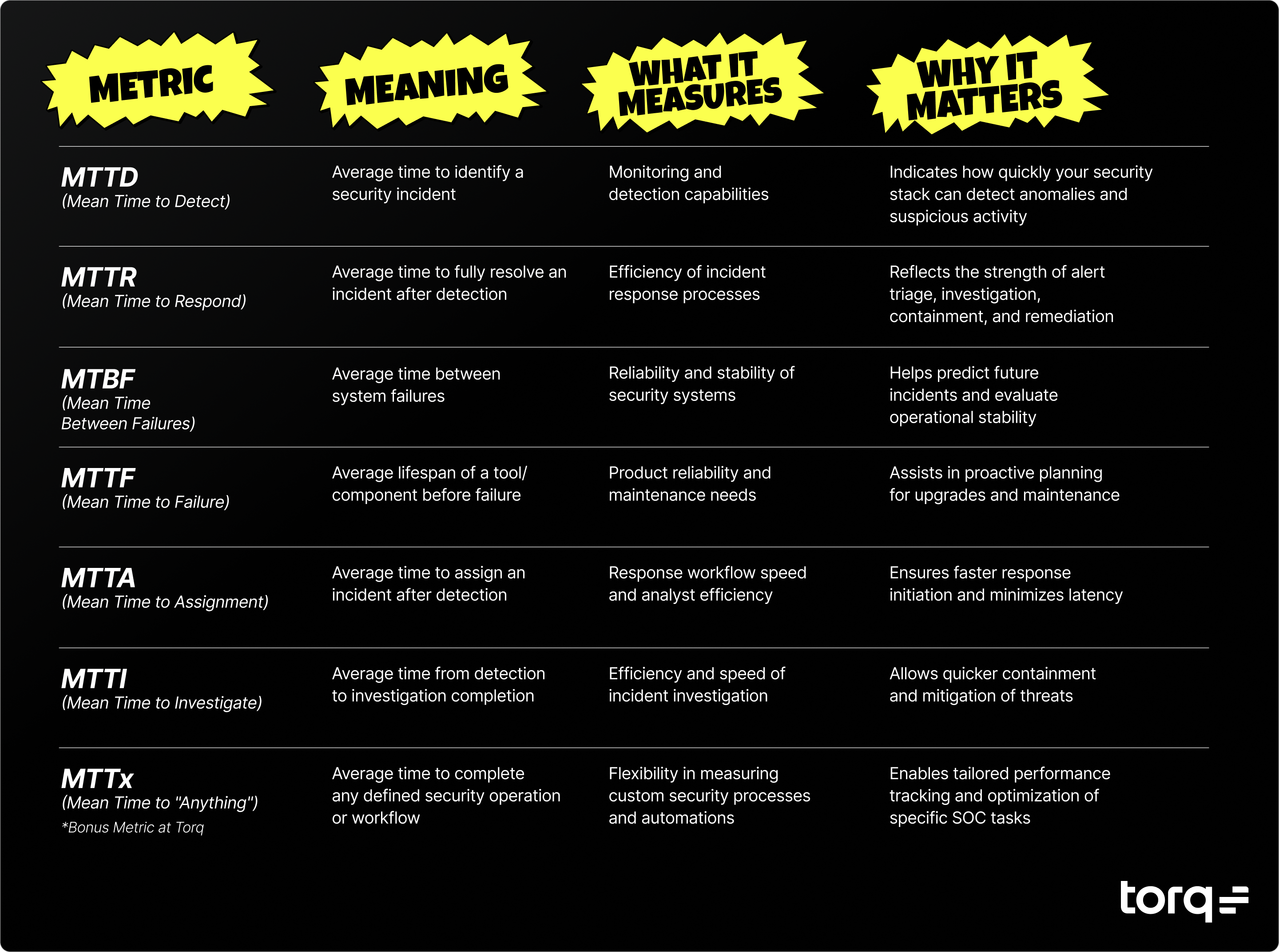
- MTTD (Mean Time to Detect) measures the average time it takes your team to identify that a security incident has occurred. This metric primarily evaluates your monitoring and detection capabilities. A lower MTTD indicates your security stack can quickly recognize anomalies and suspicious activity.
- MTTR (Mean Time to Respond) (sometimes called Mean Time to Resolve) tracks the average time required to respond to and resolve an incident fully. Speed matters; a recent SANS survey found that 33% of teams take hours to respond to threats. That’s too long. A shorter MTTR reflects strong incident response procedures and an agile, responsive security team.
MTTR often involves people and a series of steps that are needed to fix the issue. While MTTD may measure how well an automated alert system performs, MTTR often measures both your systems and the people you depend on to jump into action after an incident.
Together, these metrics illustrate your SOC’s maturity and operational effectiveness. Optimizing MTTD and MTTR directly reduces risk and overall damage from cybersecurity incidents.
How Automation Improves MTTD and MTTR
Security automation plays a pivotal role in dramatically enhancing both MTTD and MTTR, empowering security teams to scale detection and response effectively by:
- Improving detection: Automated systems like SIEM, EDR, and XDR can swiftly correlate vast data sets, instantly surfacing anomalous activities. Automation reduces reliance on manual log analysis, ensuring immediate, accurate threat identification.
- Accelerating response: Automation streamlines and accelerates incident response workflows. Tasks like enrichment, analysis, and containment that typically consume significant analyst time become nearly instantaneous. Automation eliminates the manual “grunt work,” allowing analysts to focus solely on complex or high-risk situations.
- Reducing human error: With agentic AI handling the automation, repetitive tasks become consistently executed according to predefined procedures, drastically reducing the potential for mistakes and inconsistencies in handling security incidents.
- Seamless integration: Hyperautomation platforms integrate seamlessly with SIEM, EDR, and XDR tools, delivering rapid data exchange, correlation, and enriched context. This tight integration creates an end-to-end, automated security ecosystem.
In short, automation significantly shrinks the time between detecting a threat and mitigating its impact, providing an immediate, measurable boost to your SOC performance.
How to Measure MTTD & MTTR (with Formulas)
Quantifying your incident response effectiveness requires clear measurement methods. Here’s how you calculate each:

Below is some practical guidance for measuring MTTD and MTTR:
- Consistent tracking: Record timestamps at every key incident stage (i.e., detection, acknowledgment, investigation, and resolution).
- Aggregate metrics: Regularly aggregate these timings to spot trends or inefficiencies in your process.
- Benchmarking: Establish baseline metrics to evaluate the impact of new tools, processes, or automation investments.
5 Related Incident Response Metrics You Should Know
MTTD and MTTR don’t exist in isolation. They are part of a broader landscape of incident response metrics that security teams should be tracking, including:
- MTBF (Mean Time Between Failures): MTBF measures the average time between system failures. It’s useful for evaluating the reliability of security systems and predicting when future incidents might occur. A higher MTBF indicates stable security operations.
- MTTF (Mean Time to Failure): MTTF tracks the average lifespan of a security tool or system component before a failure occurs. It’s commonly used to assess product reliability and helps organizations schedule proactive maintenance or upgrades.
- MTTA (Mean Time to Assignment): MTTA is the average time it takes for an incident to be assigned to a specific analyst or team member after detection. Lower MTTA reduces response latency and enables teams to tackle threats more efficiently.
- MTTI (Mean Time to Investigate): MTTI represents the average time taken from initial detection until the investigation is completed. Faster MTTI means threats can be understood and contained sooner, limiting potential damage.
- MTTx (Mean Time to “Anything”): MTTx is a flexible metric used at Torq to track the average time to complete any defined security operation or workflow. It helps SOC teams measure efficiency across custom actions, automations, or specific tasks unique to their security processes.
Understanding these related metrics provides deeper insight into your security operations and helps identify specific bottlenecks or areas for improvement.
Key Incident Response Metrics Explained
The Hyperautomation Domino Effect in Incident Response
Improving MTTD and MTTR isn’t just about moving faster; it’s about removing the friction between each phase of the incident response lifecycle. Torq Hyperautomation connects the dots across the entire workflow — from detection to assignment, investigation to remediation — creating a seamless chain reaction of automation that compounds every efficiency. Here’s how that automation domino effect plays out in practice:
Faster detection (MTTD): Torq reduces noise by automatically filtering out low-priority alerts and surfacing real threats faster. This shrinks MTTD and ensures analysts aren’t wasting time chasing false positives.
Faster assignment (MTTA): Once a threat is detected, a case is immediately built and assigned to the right resource within Torq’s intelligent case management dashboard. Torq decides in real time whether Socrates — the AI SOC analyst that offloads 90%+ of Tier-1 cases — or a human should take the lead, dynamically reassigning ownership if the threat escalates. That means alerts don’t sit in limbo, waiting to be noticed.
Faster investigation (MTTI): By the time an analyst gets involved, much of the work is already done. Torq HyperSOC automatically enriches and correlates incident data, while AI agents generate case summaries and assign relevant case runbooks. This allows analysts to dive straight into meaningful analysis, not manual triage.
Faster response (MTTR): Response time is reduced by how quickly and efficiently action is taken. Analysts can trigger remediation with a single click or let Socrates respond autonomously in milliseconds. Whether isolating a device, disabling a user, or launching a complex remediation strategy, action happens at machine speed.
Each improvement compounds the next, like dominoes falling one after another. The faster a threat is detected and assigned to the appropriate resource, the faster those resources can be actioned. With Torq Hyperautomation, every second saved is multiplied across the incident lifecycle, delivering exponential gains in speed, accuracy, and scale.
Reduce Your MTTD and MTTR with Torq Hyperautomation
Effectively managing cybersecurity threats requires fast detection and even faster responses. Clearly differentiating MTTD vs. MTTR and understanding related metrics like MTBF, MTTF, MTTA, and MTTI enables SOC teams to target improvements strategically.
The Torq Hyperautomation™ platform offers a proven way to dramatically lower both MTTD and MTTR through real-time incident detection, streamlined automated workflows, and reduced analyst workload. Torq helps organizations minimize alert fatigue, decrease caseload per analyst, and improve overall compliance and efficiency.
Ready to drastically reduce your MTTx? Get practice advice from our Field CISO on how to make your SOC more efficient.