Contents
Security teams are drowning — managing 10,000+ daily alerts, stretched thin by an ongoing cybersecurity talent shortage, and struggling to keep up with evolving threats. The solution? Security automation, particularly AI-driven security Hyperautomation.
What is Security Automation?
Security automation leverages automated workflows to handle critical cybersecurity tasks at machine speed— eliminating time-consuming manual processes like threat detection, analysis, and response. By automating these repetitive tasks, organizations can increase efficiency and accuracy and ensure a consistent security posture against threats.
The gold standard of security automation is AI-driven Hyperautomation, enabling security teams to move beyond simple automation and build an autonomous SOC for even greater efficiency and security gains.
Cybersecurity is essential to every organization — but without automation, it’s slow, resource-intensive, and prone to human error. Manual workflows bog down security teams, stretching time and resources thin while leaving gaps in threat detection, assessment, and remediation. Automating security not only accelerates response times but also ensures accuracy, eliminating costly mistakes and inefficiencies.
Cybersecurity automation uses technology to identify, understand, and respond to threats within your organization’s environments and to execute repetitive and time-consuming tasks. In other words, when you automate security, much of the grunt work can be handled by software, with limited, if any, manual intervention. This is especially useful when dealing with a high volume of alerts, allowing the software to filter out the low-priority and false positives threats and prioritize the critical ones, escalating to human analysts only when necessary.
Security automation has become table stakes for SOC teams in today’s connected digital world.
How Security Automation Works
Security automation functions by integrating data from numerous security tools, applying artificial intelligence (AI) for threat detection, and enabling autonomous decision-making for immediate response.
Hyperautomation combines GenAI, agentic AI, and extensive integration capabilities to enable seamless, real-time threat management across all environments, significantly enhancing detection and response capabilities.
Why is Security Automation Necessary?
Large organizations, from Fortune 500 companies to global multinationals, face existential security challenges that demand security automation solutions, including:
- Expanding attack surface: Security teams face alerts on alerts on alerts, from phishing and endpoint vulnerabilities to insider threats and fraud. Without automation to filter, prioritize, and respond to these threats at machine speed, teams simply can’t keep up.
- Global cybersecurity talent shortage: According to ISC2, the estimated cybersecurity workforce gap is 4.76 million. SOC teams are stretched thin, and this problem is only getting worse. As tech stacks expand across multi-cloud environments, security teams’ capability to manage them is maxed out. Cloud security automation isn’t replacing analysts — it’s making their jobs possible.
- Siloed security architecture: SecOps teams manage 70+ security tools across environments. Without integrations to combine these workflows, security teams face misaligned processes, inefficient work, and manual effort that slow down response times.
“60% of line of business users agree an inability to connect systems, apps and data hinders automation.” – ZDNET
Benefits of Automating Security
Enhanced efficiency: Cybersecurity automation eliminates repetitive tasks like data analysis and incident investigation. By streamlining workflows, security teams can dramatically reduce time-consuming processes, improve mean-time-to-respond (MTTR), and alleviate operational fatigue — boosting productivity, agility, and overall security resilience.
More accurate response: Manual processes run the risk of human error. Security automation minimizes this risk by implementing consistent detection and quicker responses. It also shortens the time-to-action for remediation, preventing further risks to the business.
Reduced analyst burnout: By automating time-consuming manual processes, security automation lightens workloads and prevents the constant alert fatigue that drains security teams. Automation frees up time for analysts to develop their expertise instead of getting bogged down in repetitive, busy work.
Scalable deployment: Automation in security centralizes tooling, enriches security cases with contextual intelligence, and provides real-time updates across platforms for seamless teamwork.
Reduced costs: Automation can help optimize resources and operational expenses by eliminating manual tasks, streamlining workflows, reducing the need for specialized staff, and improving resource allocation. It can also help avoid data loss, reputational damage, and other financial losses from security incidents.
Stronger compliance: Leveraging security automation tools to manage reporting and compliance activities decreases regulatory risk.
Faster MTTD/MTTR: Reduces alert fatigue by quickly identifying and remediating threats.
Autonomous Case Management: AI-driven automation manages incidents from detection through resolution, eliminating manual bottlenecks.
Full-lifecycle Response: Comprehensive automation enables end-to-end threat handling.
Cybersecurity Automation Types and Tools
Several tool types enhance security automation:
- Hyperautomation: Combines advanced AI, machine learning, and integration capabilities, enabling autonomous decision-making and remediation, thus significantly outperforming traditional tools.
- XDR (Extended Detection and Response): Provides integrated visibility and automated responses across endpoints, network, and cloud environments.
- SOAR (Security Orchestration, Automation, and Response): Coordinates security tools, automating predefined responses (though now largely replaced by Hyperautomation).
- AI Ops (Artificial Intelligence Operations): Uses AI to analyze vast datasets, detect anomalies, and automate responses proactively.
Best Practices for Security Automation
Maximizing security automation ROI requires:
- Integration: Ensure seamless integration with existing tools
- Customization: Tailor automation workflows to organizational needs
- Regular Updates: Continuously update and refine automated systems
- User Training: Equip analysts to leverage automated systems fully
Challenges and Limitations of Security Automation
Common challenges around security automation include:
- Integration complexity: Difficulty linking legacy tools and data silos.
- False positives: High false-positive rates from insufficient intelligence and correlation.
- Operational complexity: Challenges in maintaining complex automation rules.
Torq solves these challenges with agentic AI, providing seamless integration, adaptive workflows, and accurate threat response.
Security Automation vs. Security Orchestration and SOAR
It’s easy to assume security automation and orchestration are synonymous, but there are many important differences between the two.
Security orchestration was intended to create a more streamlined workflow when connecting multiple tools and processes for security teams to act with greater efficiency and confidence. We all know this didn’t happen (See: SOAR is Dead Manifesto).
SOAR platforms are slow, rigid, and don’t actually speed up processes for SOC teams. With limited integrations, outdated technology, and running on a single server, legacy SOAR hinders security teams’ ability to detect and respond to threats across environments. SOARs were a foundational tool for many SOC teams but are rapidly being replaced by security automation.
Cybersecurity automation brings together different teams, processes, and technologies to drive more efficient and scalable operations across a much broader scope. It does this through no-code, low-code, and even AI-generated workflow building, meaning that these tools can be used by just about anyone, not just security engineers, to define risks, enforce security rules, and remediate threats.
SOAR was built to automate security workflows, but it’s slow, complex, and requires extensive coding. Security Hyperautomation is the next evolution, eliminating inefficiencies with AI and no-code automation. Here’s how they compare.
Security Hyperautomation vs. SOAR
| Security Hyperautomation | SOAR | |
| Architecture | ✔ Cloud-native architecture, elastic scaling | X Monolithic architecture, limited scaling |
| Integrations | ✔ Limitless, extensible, continuous API updates | X Limited, inflexible, requires custom dev |
| Efficiency | ✔ Helps manage risks at scale without adding headcount or requiring specialized resources | X Requires extensive resources and constant maintenance |
| Accessibility | ✔ Allows all stakeholders to define and enforce security requirements | X Requires cybersecurity expertise to configure and operate |
| Automated Response | ✔ No-code automation frameworks can automate threat response based on rules | X Focuses more on orchestrating responses by security professionals than remediating |
| AI Capabilities | ✔ Built-in AI agents for autonomous remediation, workflow building, data transformation, and more | X Limited or non-existent |
| Analyst Productivity | ✔ High, 10x+ operational boost | X Low, prone to burnout |
| Overall Effectiveness | ✔ Future-proof solution, providing comprehensive security coverage and automation | X Limited flexibility, struggles to meet modern SecOps demands |
Ready to pull the plug on your SOAR? Get the migration guide >
How to Pick the Right Security Automation Tool
Choosing the right security automation solution isn’t just about checking a box — it’s about finding a platform that seamlessly integrates with your existing security stack, scales with your needs, and actually delivers on the promise of efficiency and protection. Here’s what to consider:
1. Integration and Compatibility
An enterprise security automation platform is only as good as its ability to integrate with your existing tools. Look for a solution that offers out-of-the-box integrations with all of your key security and IT infrastructure, as well as the flexibility to build custom integrations without requiring extensive coding. The best platforms eliminate manual bottlenecks by enabling security teams to connect their entire stack effortlessly — without waiting on vendor updates or custom development work.
2. True No-Code vs. Customization Capabilities
Some solutions claim to be “no-code” but still require extensive scripting to handle real-world security scenarios. Choose a platform that provides both no-code simplicity and AI-generated workflow building. You shouldn’t have to choose between ease of use and flexibility. A well-designed security automation tool allows security professionals of all skill levels to build workflows while still enabling advanced users to fine-tune automations for complex use cases.
3. AI-Driven Decision Making
Cybersecurity automation has evolved beyond simple if-this-then-that workflows. Modern solutions, like agentic AI-powered automation, don’t just execute pre-defined rules — they can analyze threats in real time, correlate signals across multiple tools, and autonomously remediate low-risk incidents. When evaluating platforms, look for AI-driven insights and contextual automation that help security teams make smarter, faster decisions.
4. Speed and Scalability
At this stage, you should evaluate potential security automation solutions with a Proof of Concept (POC), focusing on ROI and time-to-value. Choose the use cases that are mission-critical to your organization to assess how quickly and easily they can be operational. Additionally, ensure the platform can scale with your needs — handling increasing volumes of security events without performance degradation or the need for constant tuning.
5. Vendor Vision
Security threats evolve daily, and your security automation solution should grow with them. Choose a vendor with a clear vision for innovation — one that’s actively incorporating AI, Hyperautomation, and advanced case management capabilities. The best platforms don’t just keep up with security trends — they redefine them.
Common Security Automation Use Cases and Examples
- Identity and access management (IAM): Automates access control, reducing manual errors.
- Threat hunting: Continuously detects and responds to threats proactively.
- Cloud security posture management (CSPM): Ensures compliance across cloud environments.
- Email security: Automates detection and remediation of phishing and malware.
- Incident response: Accelerates and automates alert triage and threat containment.
- Vulnerability management: Automates scanning, prioritization, and remediation.
Major Regional Bank Accelerates Phishing and Ransomware with Security Automation
A leading regional financial services organization turned to Torq for security automation to eliminate slow, inconsistent security responses and automate critical processes across its SOC. Facing a growing volume of phishing, ransomware, and fraud threats — along with a shortage of security analysts — the bank needed a solution that could streamline alert triage, investigation, and remediation in real time.
Bypassing legacy SOAR solutions, this top 30 bank found the Torq Hyperautomation platform to be the best fit. By deploying Torq’s low-code/no-code security automation, the bank built and launched 100+ workflows in just three months, reducing mean time to investigate (MTTI) from hours to minutes. Torq’s limitless API integrations easily integrated with the bank’s existing security stack, allowing for a unified, automated approach to phishing and ransomware mitigation.
The Future of Security Automation: Torq Hyperautomation and the Autonomous SOC
Security automation is an important step in modernizing cybersecurity, eliminating manual processes, and accelerating threat response. But the story doesn’t end there.
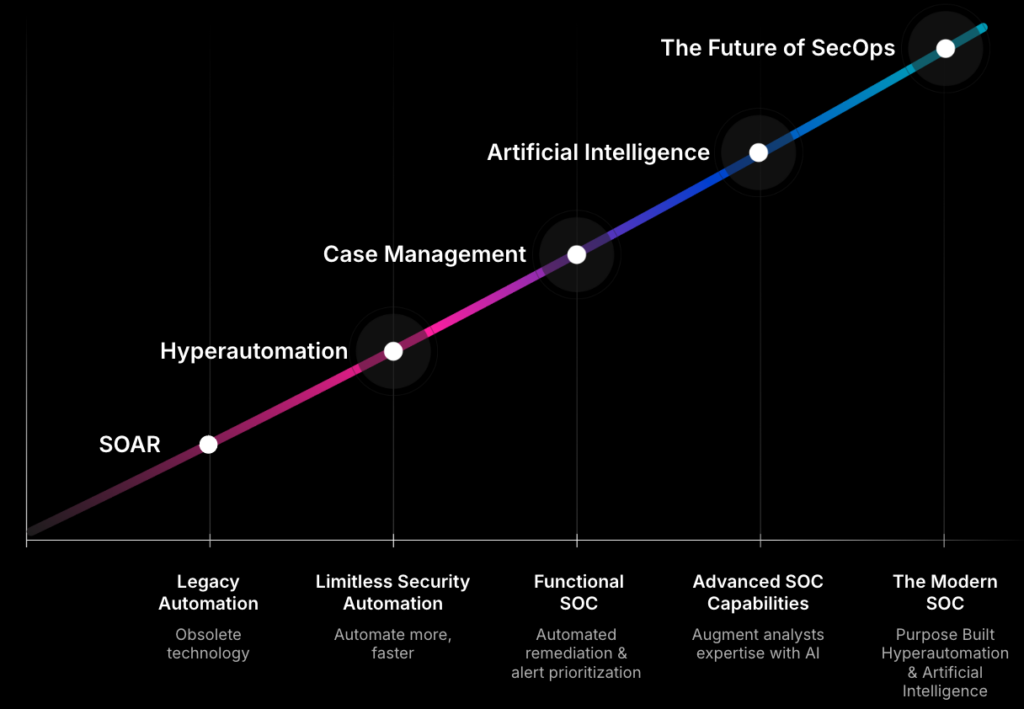
Security Hyperautomation enables SecOps to operate on a new scale thanks to AI-driven decision-making, adaptive workflows, and full-stack interoperability. This shift is powering a natural evolution toward the autonomous SOC, where AI doesn’t just automate security processes but also intelligently manages and optimizes them in real time.
Unlike traditional security automation, which focuses on predefined rule-based responses, Torq Hyperautomation dynamically connects disparate tools, enriches alerts with real-time intelligence, and autonomously executes remediation — all without manual intervention. It integrates AI and large language models (LLMs) to instantly correlate signals across multiple sources, filter false positives, and prioritize critical threats.
Where security automation removes friction, Hyperautomation eliminates inefficiencies entirely — allowing organizations to move from reactive to proactive, self-sustaining security operations. Agentic AI-powered automation can investigate, escalate, and remediate threats autonomously, closing security gaps faster than ever. AI-powered Hyperautomation doesn’t just improve security workflows — it redefines how modern SOC teams operate.
Get Started with Torq Hyperautomation
Choosing the right vendor is crucial — Torq offers unmatched AI capabilities, rapid time-to-value, seamless integration, and true no-code flexibility. See how Torq transforms your SOC into an autonomous security powerhouse.
Want to see how AI-powered security Hyperautomation can transform your SOC?