Empower your security teams to proactively detect and respond to threats with Torq’s hyperautomated case management capabilities
Introduction
Threat hunting is the process of proactively searching for hidden threats in an organization’s environment – a critical modern cybersecurity activity. However, relying on manual threat hunting alone can be time-consuming and resource-intensive. In this blog, we’ll explore how Torq Hyperautomation, with its new automated case management features, empowers security teams to harness the power of next-gen threat hunting, providing a unified, intelligent, and proactive approach to automated threat hunting.
The Evolution of Threat Hunting
In recent years, the cybersecurity industry has shifted towards more proactive and automated threat hunting. This approach helps security teams discover hidden threats and reduce dwell time by automating the detection and response processes. Torq Hyperautomation is designed to accelerate this evolution by providing advanced capabilities for threat hunting and security investigations.
Torq’s Platform: Hyperautomating Threat Hunting
Torq hyperautomates threat hunting, cutting MTTI through the following key features:
- Automated Case Management-By hyperautomating case management, security teams can streamline their workflows and focus on high-priority threats. Torq empowers teams to automatically create, update, and manage cases in response to security alerts, ensuring that they can quickly prioritize and respond to threats. Analysts are freed from the mundane to concentrate on higher-level security activities.
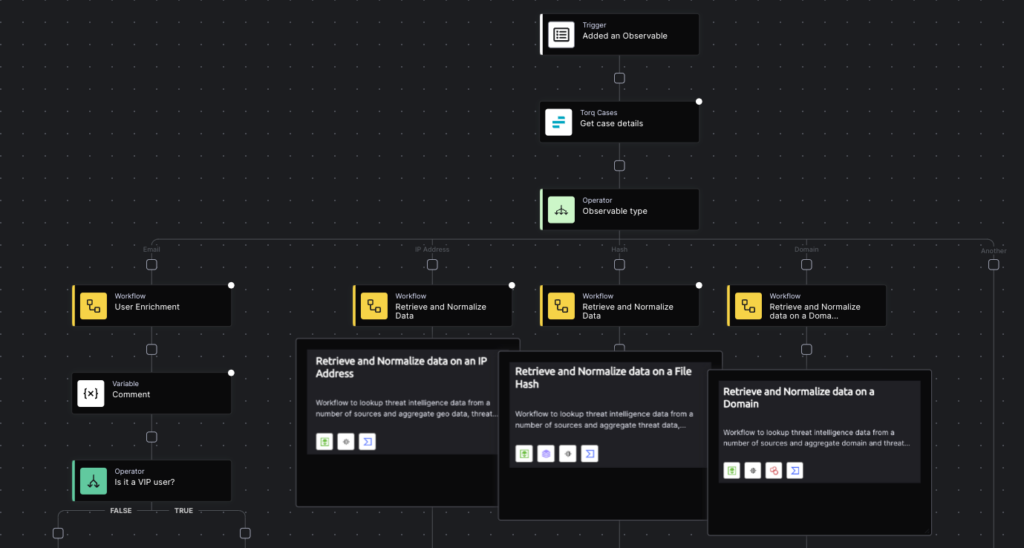
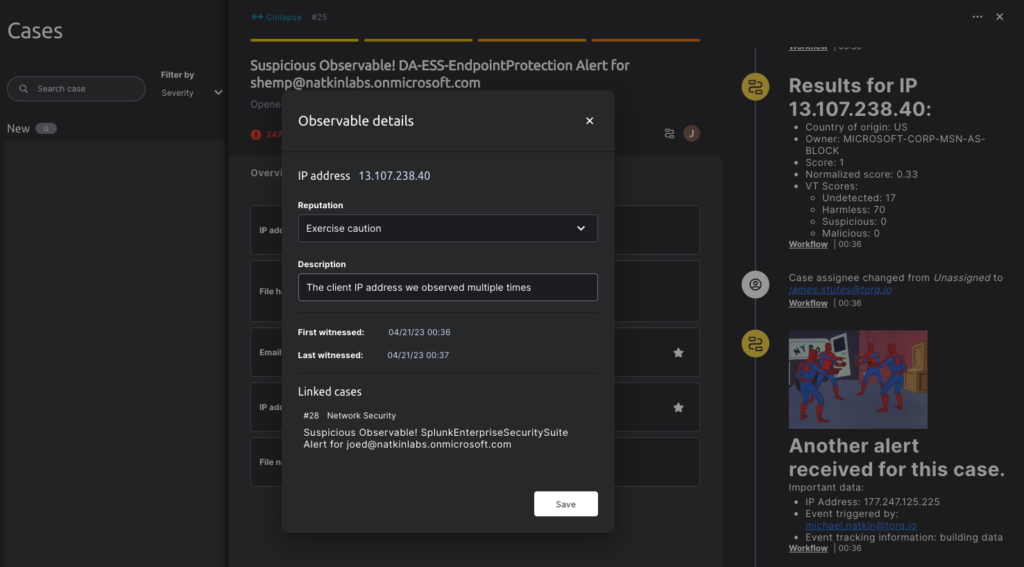
- Observables-Observables are first-class citizen objects representing artifacts of information, such as URLs, domains, and IP addresses. These objects, which are OCSF-compliant, can be associated with one or many cases. This capability empowers security teams to track the relationships between different elements across investigations, unlocking novel and valuable insight.
- Relationship Tracking-Torq’s platform allows security teams to implement correlation, enrichment, and contextualization logics in the workflows they build, leveraging the relationships between observables, cases, and alerts. This helps security analysts identify patterns and uncover hidden threats.
Automated Threat Hunting in Practice
Andy Ellis, Advisory CISO, Orca, and YL Ventures Operating Partner, recently noted that automated threat hunting is about learning all the ways in which an organization is currently blind and shining a light on them. It requires continuous improvement and adaptation, with security teams constantly refining their detection and response capabilities.
With Torq Hyperautomation, security teams can create automated workflows to detect and respond to threats. As teams discover new threat patterns, they can refine the automated detection and response process, making threat hunting more efficient and effective over time. This increases efficiency, reduces burn-out and churn, and maximizes the security operations investment – in human resources and technology.
Conclusion
Torq Hyperautomation, complete with its advanced automated case management features, empowers customers to elevate their threat hunting game activity by providing comprehensive visibility, user-driven context, automation, and advanced analytics. By embracing these capabilities, security teams can remain ahead of evolving threats and protect their organizations more effectively. Experience the power of proactive threat hunting with Torq Hyperautomation, today.
Not using Torq yet? Get in touch to handle this issue, and see how Torq security hyperautomation accelerates security operations to deliver unparalleled protection.




