Contents
Get a Personalized Demo
See how Torq harnesses AI in your SOC to detect, prioritize, and respond to threats faster.
Traditional vulnerability management is falling behind. Manual workflows stall progress. Legacy SOAR drags teams down. Siloed tools leave dangerous gaps. The result is delays, blind spots, and risk exposure that compound fast. Human error and inefficiency are baked into the process, costing teams more than time. It’s compromising compliance, degrading customer experience, and overwhelming analysts.
It doesn’t have to be this way.
This blog breaks the vulnerability management lifecycle into six steps, each primed for automation. We’ll show you how to modernize your workflows using Hyperautomation and agentic AI. This is how modern SOCs move faster, respond smarter, and stay in control.
What is the Vulnerability Management Lifecycle?
Vulnerability management is the continuous process of identifying, evaluating, prioritizing, remediating, and monitoring security weaknesses (vulnerabilities) across an organization’s systems, networks, and applications. Its goal is to reduce the attack surface by proactively addressing vulnerabilities before cybercriminals can exploit them.
The vulnerability management lifecycle is a continuous, systematic process for identifying, assessing, prioritizing, remediating, and monitoring security vulnerabilities within an organization’s IT infrastructure. It’s a crucial part of any cybersecurity strategy, aiming to manage risks and minimize the potential for cyberattacks proactively.
The vulnerability management lifecycle includes:
- Discovery of all assets in the environment
- Assessment of vulnerabilities using automated scanners and threat intelligence
- Prioritization based on factors like severity (i.e., CVSS score), exploitability, and business impact
- Remediation or mitigation through patching, configuration changes, or compensating controls
- Validation and monitoring to confirm fixes and detect re-exposure or new risks
- Reporting and improvement to refine processes and boost efficiency
Today’s dynamic cloud environments demand more than reactive security. As modern IT environments grow more complex and dynamic, traditional approaches that rely on manual processes and fragmented tools can’t keep up. The rapid change in cloud infrastructure and the constant emergence of new vulnerabilities make it nearly impossible for security teams to identify and act on every risk in time.
Automating the vulnerability management lifecycle — across asset discovery, scanning, prioritization, remediation, and validation — helps teams move from reactive to proactive. By integrating data from scanners, threat intelligence platforms, Configuration Management Databases (CMDBs), and ITSM (IT Service Management) systems, automated workflows can continuously identify critical issues, assign ownership, and trigger remediation actions.
Organizations can ensure consistent, efficient, and scalable risk mitigation with a well-defined and automated vulnerability management program. The result is faster response, reduced exposure, improved compliance, and a more resilient security posture.
The 6 Steps of Vulnerability Management Lifecycle You Can Automate Today
Step 1: Asset Discovery and Vulnerability Assessment
Before vulnerabilities can be managed, organizations must first identify every asset in their environment. This step begins with building a complete, real-time inventory of IT assets — including endpoints, servers, cloud workloads, SaaS apps, IoT devices, and shadow IT — across on-premises, cloud, and hybrid environments. Critical vulnerabilities often go undetected without accurate asset discovery, leaving organizations exposed.
Once discovered, assets should be classified based on business importance, data sensitivity, and exposure level. Security frameworks like the CIS Controls or ISO standards can help guide this classification process to ensure consistent, policy-driven prioritization.
Vulnerability assessment follows closely behind discovery. Organizations conduct scheduled or continuous scans using tools like Qualys, Tenable, or Rapid7 to identify known vulnerabilities. Automated scans are augmented by penetration tests and configuration audits, which simulate real-world attack scenarios and uncover deeper misconfigurations that scanners might miss. These assessments provide the foundation for informed, risk-based decision-making in later stages.
Key metrics for this step include asset discovery completeness, vulnerability coverage rate, and time to discovery. Organizations that automate asset discovery and vulnerability scanning reduce blind spots, accelerate detection, and set the stage for a proactive vulnerability management lifecycle.
How Torq Can Automate This: Torq integrates with your asset inventory, CMDB, cloud providers, and endpoint detection tools to ingest asset data continuously. No-code workflows automatically reconcile discovered assets across hybrid environments, keeping your inventory current without spreadsheets or manual audits. Clients can also use Torq to trigger validation workflows when new, unmanaged assets appear, alerting security teams to take immediate action.
Step 2: Vulnerability Scanning and Detection
With assets identified and inventoried, the next step is systematic vulnerability scanning. Continuous scanning ensures that new vulnerabilities are identified immediately, not just during scheduled review windows. Modern scanners integrated with SIEMs, EDRs, and threat intelligence platforms can detect vulnerabilities and push findings into workflows.
Equally important is the normalization and automation of scan data. Without these key systems, teams often struggle to analyze findings from multiple tools or formats. Automated ingestion pipelines ensure scan results are normalized, deduplicated, and enriched with contextual metadata so teams can prioritize issues efficiently. This minimizes human error and eliminates manual data wrangling, allowing analysts to focus on threat mitigation rather than spreadsheet management.
How Torq Can Automate This: Torq connects directly to vulnerability scanners like Tenable, Qualys, and Rapid7 to ingest real-time scan results. It normalizes disparate data formats and enriches them with contextual metadata, like asset criticality, owner, and business function, then automatically routes findings into triage workflows. Torq eliminates bottlenecks by auto-tagging vulnerabilities based on severity, source, and exploitability, and escalating only the ones that matter.
Step 3: Risk-Based Vulnerability Prioritization
Not all vulnerabilities pose the same threat, and relying solely on Common Vulnerability Scoring System (CVSS) scores often wastes time and leads to missed priorities.
Effective vulnerability prioritization combines multiple factors: severity ratings, real-time threat intelligence, asset value, exploitability, and the potential business impact if compromised. A vulnerability on a public-facing application used by customers carries far more weight than one on an internal test server, even if their CVSS scores are identical.
This stage involves applying structure and strategy to vulnerability triage. It requires input from multiple systems and stakeholders and the ability to evaluate each vulnerability in context, not just in isolation.
How Torq Can Automate This: Torq automates prioritization by combining CVSS scores, threat intelligence, asset importance, and business impact. Risk-scoring models are baked into workflows that assign ownership based on asset tags or business unit and notify the right team instantly. AI Agents dynamically adapt prioritization workflows to changing threat intel, for example, reprioritizing based on active exploitation reports from MISP or Recorded Future.
Step 4: Remediation and Patch Deployment
Once vulnerabilities are prioritized, the next step is action — and this is where many organizations get bogged down. Patch management and remediation can be time-consuming, error-prone, and resource-intensive, especially when handled manually.
Coordinating patch deployment, configuration changes, and policy enforcement is complex. Different systems, ticketing queues, and ownership models often introduce delays that extend mean time to remediate (MTTR). Critical asset patching may sometimes be skipped entirely due to a lack of visibility or process bottlenecks.
The key to making remediation effective is ensuring it’s consistent, policy-driven, and well-integrated with existing IT and security infrastructure. Automated workflows streamline this process.
How Torq Can Automate This: Torq triggers auto-remediation actions the moment a vulnerability crosses a risk threshold. Whether that’s opening a ServiceNow ticket, deploying a patch through CrowdStrike, or updating firewall rules — Torq coordinates every step across ITSM, EDR, and config management systems. Torq lets you define remediation SLAs by risk level, then automatically tracks and escalates any patching delays.
Step 5: Validation and Continuous Monitoring
Even after a patch is deployed or a mitigation is applied, teams must validate that the vulnerability is truly resolved and that the fix hasn’t introduced new risks. Organizations can be left with a false sense of security without a clear validation process.
This step is also where continuous monitoring comes into play. Threats evolve, and systems change, meaning previously resolved vulnerabilities can resurface or emerge in the same risk areas. Keeping tabs on those changes in real time is essential to maintaining a strong security posture.
Beyond operational assurance, validation and monitoring also feed key performance indicators (KPIs). Metrics like mean time to validate, remediation success rate, and recurring vulnerabilities offer insight into program effectiveness and guide continuous improvement.
How Torq Can Automate This: Torq ensures that every remediation action is followed by automatic verification. It coordinates post-patch scans, checks system health, and updates real-time vulnerability status. If a scan fails or a system shows signs of re-exposure, Torq reopens the case and notifies the right teams.
Torq’s workflows also power continuous monitoring across your environment, triggering alerts and actions the moment new vulnerabilities are detected. All validation results are logged with full audit trails, giving teams a clear, compliant record of what was fixed, when, and how.
Step 6: Reporting and Improvement
The final — and often most overlooked — step in the vulnerability management lifecycle is reporting and continuous improvement. This stage turns tactical remediation work into strategic insight, enabling security teams to track performance, share results with stakeholders, and refine processes over time.
Effective reporting starts with capturing and consolidating key metrics from across the lifecycle. These include mean time to detect (MTTD), mean time to remediate (MTTR), validation success rate, outstanding vulnerabilities by risk level, and SLA adherence. Automation can generate these reports in real time, pulling directly from ITSM, scanning tools, and case management systems, eliminating manual data gathering and improving accuracy.
But reporting isn’t just about compliance dashboards or CISO updates. It’s also about communicating clearly across teams. Security analysts need detailed, technical data to investigate root causes. IT and DevOps teams need actionable task lists and timelines. Executives need business-aligned summaries showing risk reduction, operational efficiency, and ROI. Torq’s AI case summaries and customizable reports ensure the right insights reach the right people.
Beyond communication, this stage powers process improvement. Every vulnerability managed, every patch deployed, and every false positive investigated is an opportunity to learn. Were there delays in detection? Was ownership misrouted? Did remediation workflows succeed automatically, or require manual overrides?
Automation platforms like Torq can highlight bottlenecks, track repetitive tasks, and suggest optimizations for future cycles, helping teams evolve with the threat landscape.
How Torq Can Automate This: Torq aggregates lifecycle metrics — MTTR, patching trends, asset coverage, false positives, and more — into real-time dashboards. It automates reporting to different stakeholders (security, IT, execs) and uses historical data to optimize future workflows. With Torq’s intelligent case summaries and agentic AI analysis, your team gets metrics, insights, and improvement recommendations after every cycle.
Visualizing the Automated Vulnerability Management Workflow
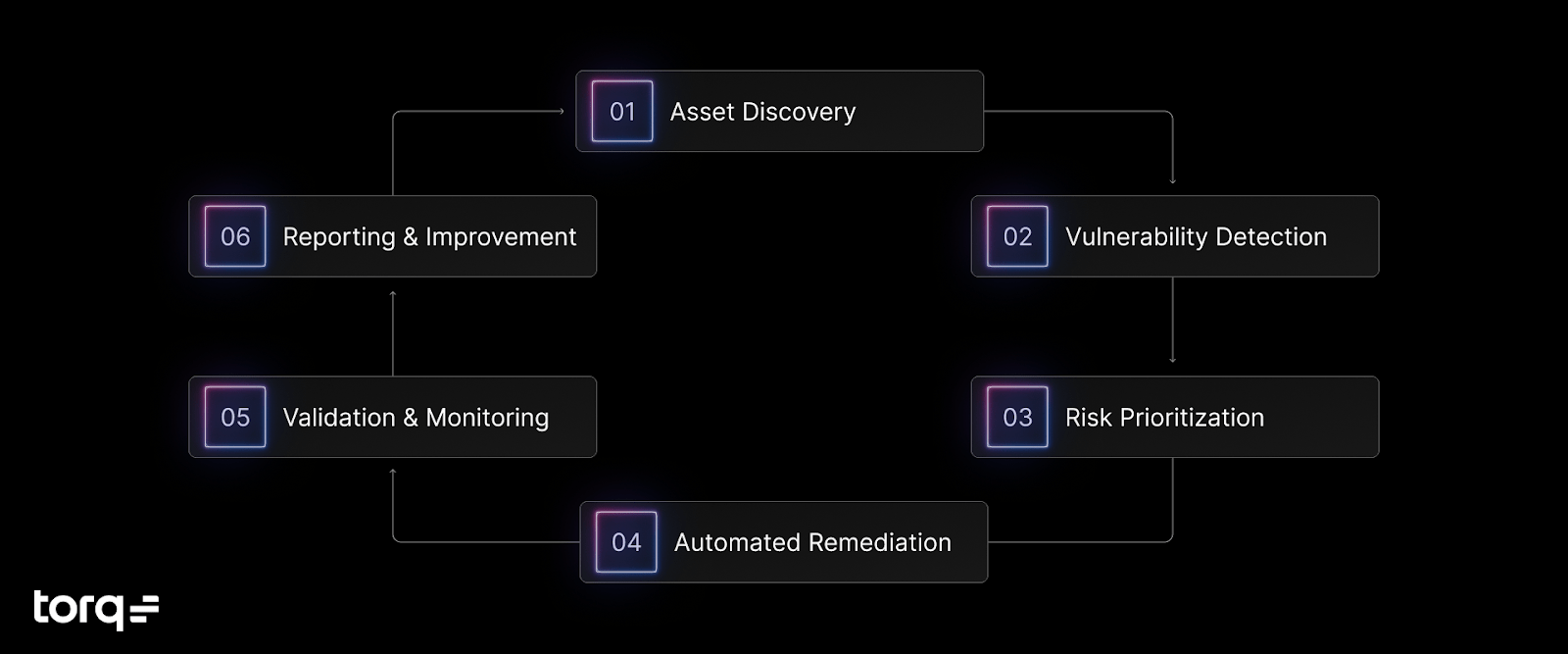
Each stage features integration points with standard security tools, all unified through no-code automation and adaptive AI workflows, ensuring seamless transitions between each lifecycle step.
How Torq’s No-Code, Agentic AI Transforms VM
Legacy SOAR platforms often promise automation — but deliver rigid, playbook-style workflows that break the moment something unexpected happens. They’re difficult to update, heavily reliant on code, and require constant upkeep to remain useful in fast-changing threat environments. Vulnerability management, in particular, suffers from this inflexibility. New CVEs emerge daily, patch windows shift, and business priorities evolve. Static systems simply can’t keep up.
Torq is built for the opposite. Its modern no-code platform empowers security teams to create and customize complex vulnerability management workflows — without writing a single line of code. Whether integrating with vulnerability scanners like Tenable or Qualys, orchestrating patch actions through CrowdStrike or SCCM, or syncing data across Jira, ServiceNow, and CMDBs — Torq makes it fast, repeatable, and reliable.
Where Torq truly sets itself apart is with agentic AI — purpose-built intelligence that doesn’t just execute tasks, but reasons through them. Torq’s agentic AI dynamically adjusts prioritization models based on live threat intelligence, changes workflows on the fly based on remediation delays or escalation policies, and even recommends new automation paths based on past actions and results.
This creates an entirely different experience:
- No-code flexibility means teams can launch or modify vulnerability workflows in minutes, not days or weeks.
- Dynamic response allows the system to reprioritize or reassign vulnerabilities as business needs or threat conditions shift.
- Human-level reasoning lets agentic AI anticipate gaps or delays, take corrective action, and escalate intelligently, all without manual input.
By combining intuitive workflow creation with adaptive intelligence, Torq transforms the vulnerability management lifecycle from a slow, manual process into a fast, autonomous system. Teams can focus on strategy and oversight while Torq handles the orchestration, remediation, and validation at machine speed — all with full visibility and control. It’s not just automation — it’s Hyperautomation, designed for the pace and complexity of modern cybersecurity.
Reclaim Time. Reduce Risk. Automate Everything.
With Torq Hyperautomation™, every stage of the vulnerability management lifecycle becomes faster, more accurate, and radically more effective. Teams reclaim time, reduce risk, and stay focused on what matters: preventing the next security incident.
Ready to make the shift? Read the SOC Efficiency Guide to see how leading security teams accelerate response, eliminate alert fatigue, and scale operations with Torq.









