Cloud Misconfiguration Detection & Remediation
Continuously monitor, detect, and automatically remediate cloud infrastructure misconfigurations across multi-cloud environments
Torq HyperSOC™ integrates with leading Cloud-Native Application Protection Platform (CNAPP) tools and cloud-native security services to provide automated triage, prioritization, and remediation of critical vulnerabilities that expose your cloud infrastructure to security threats and compliance violations.
Measurable Cloud Security Improvements
90%
faster remediation
85%
faster threat identification
95%
compliance automation
Cloud Misconfigurations Create Critical Security Gaps
Organizations struggle to maintain secure cloud configurations across dynamic, multi-cloud environments. Manual processes can’t keep pace with rapid infrastructure changes, leaving critical security gaps that expose sensitive data and create compliance violations.
Configuration Drift
Cloud infrastructure changes rapidly through DevOps automation, creating configuration drift that exposes resources through overly permissive security groups, unencrypted storage, and excessive IAM privileges.
Multi-Cloud Complexity
Different security models across AWS, Azure, and GCP create inconsistent security postures, with security teams unable to maintain unified policy enforcement across cloud platforms.
Alert Overload
CSPM tools generate thousands of misconfiguration alerts without context or prioritization, overwhelming security teams and delaying remediation of critical exposures.
Vulnerability Management
Cloud-deployed components often contain vulnerabilities that only surface after production deployment, creating a critical window of exposure. Traditional scanning processes fail to catch misconfigurations and exploitable weaknesses in live infrastructure, leaving security teams to discover threats reactively rather than preventing them.
How Torq Automates the Detection and Remediation of Cloud Misconfigurations
Torq HyperSOC orchestrates multiple cloud security tools to provide comprehensive misconfiguration detection, intelligent prioritization, and automated remediation across your entire cloud infrastructure.
Continuous Configuration Monitoring
Integrates with leading CSPM tools and cloud-native security services to continuously scan cloud infrastructure, automatically detect misconfigurations against industry frameworks, and maintain real-time security posture visibility.
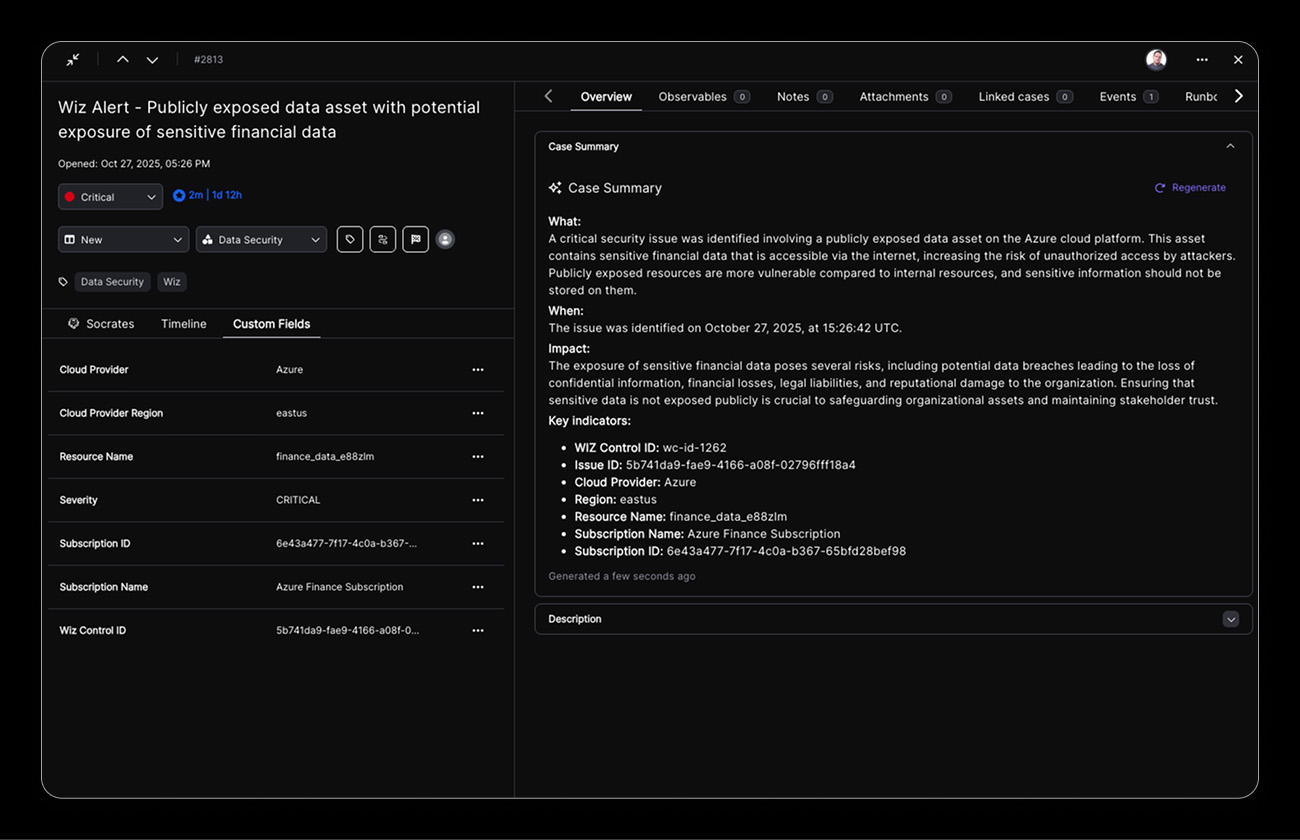
Key capabilities:
- Automated triage and remediation of misconfigurations
- CIS/NIST framework alignment
- Compliance policy automation
- Multi-cloud platform support
- Resource relationship mapping
- Configuration drift detection
Intelligent Risk Prioritization
Automate risk prioritization by defining custom logic that evaluates asset criticality, data sensitivity, network exposure, and attack vectors according to your organization’s specific business risks, rather than relying on generic severity scores.
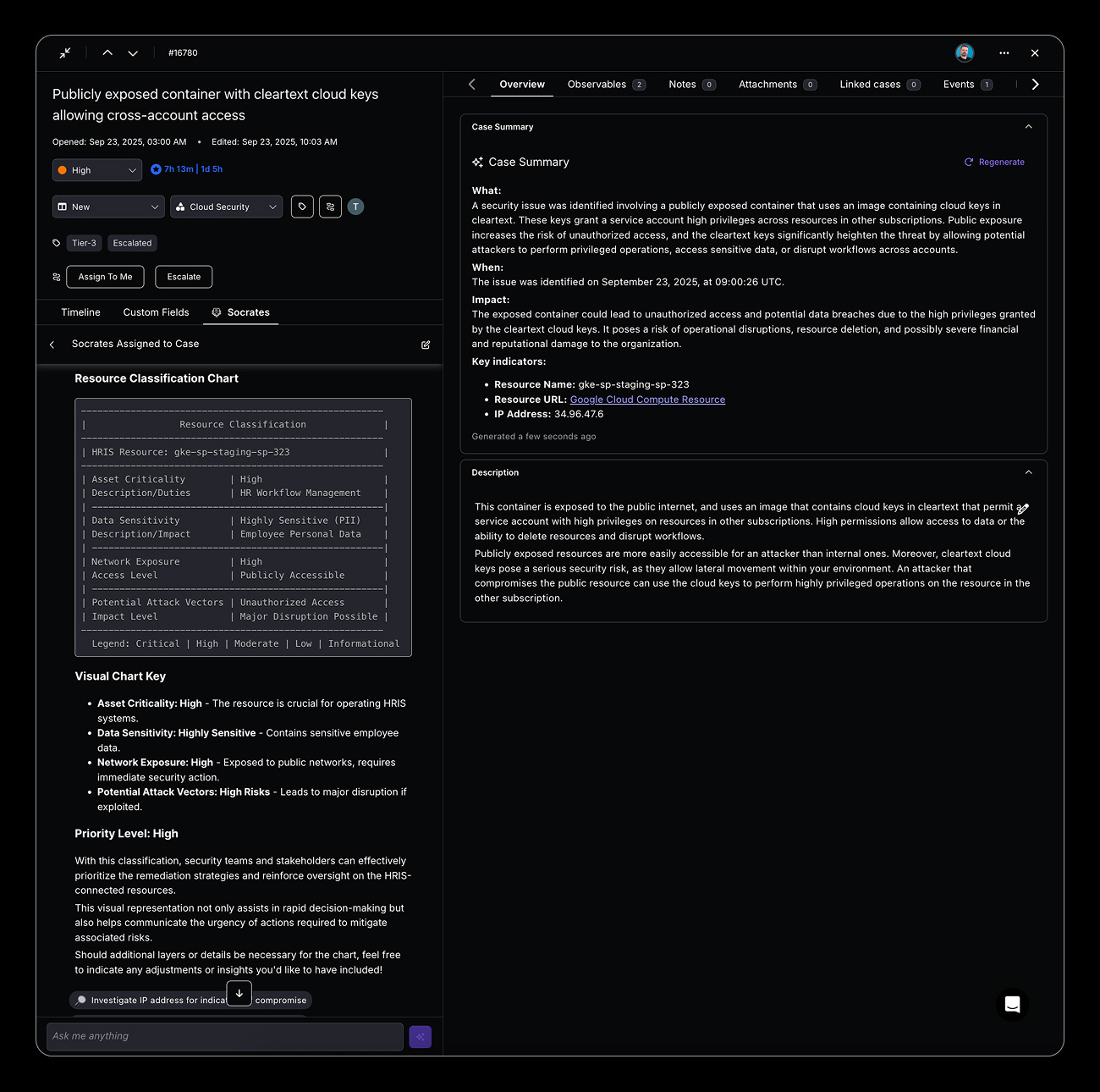
Key capabilities:
- Business impact scoring
- Exposure pathway analysis
- Threat context correlation
- Asset criticality mapping
- Data classification integration
- Dynamic priority adjustment
Automated Configuration Remediation
Policy-driven automation engine that executes pre-approved remediation actions through native cloud APIs, Infrastructure as Code updates, and security tool orchestration to automatically resolve misconfigurations without manual intervention.
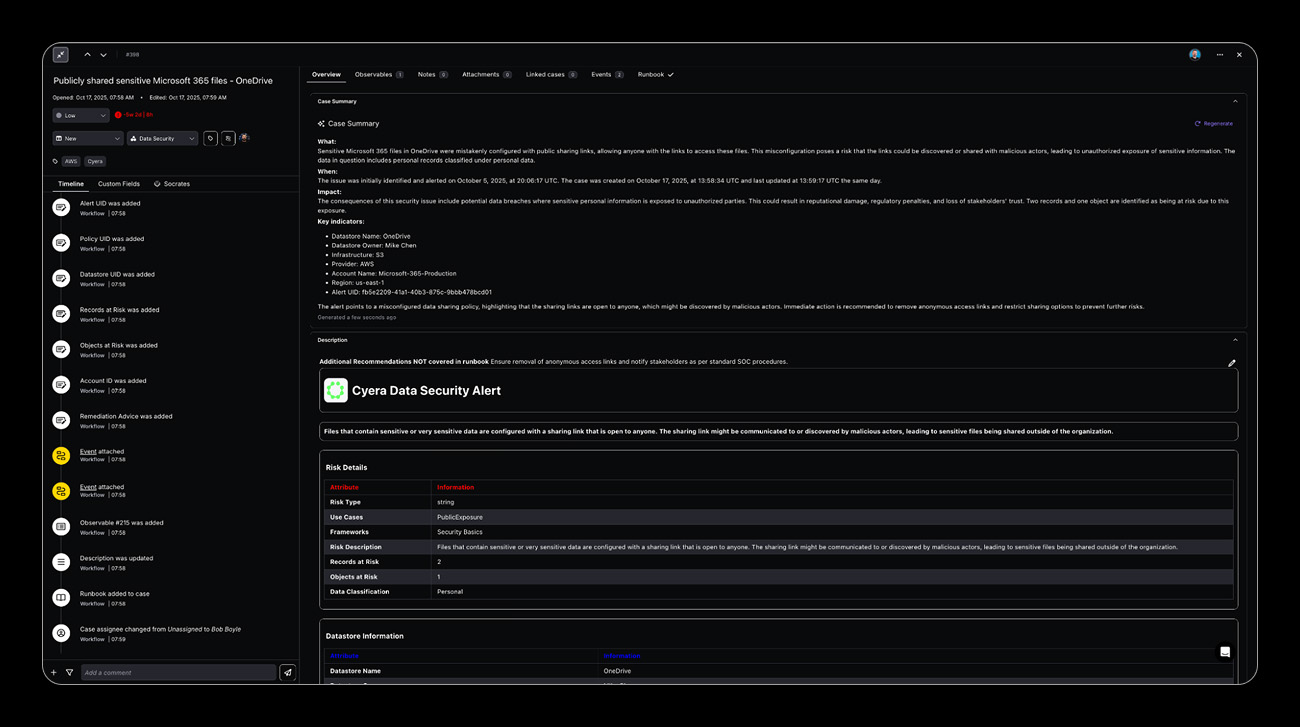
Key capabilities:
- Policy-based automation
- IaC template updates
- Rollback capabilities
- Native cloud API integration
- Change approval workflows
- Audit trail maintenance
Cloud-Native Security Architecture
Built on a cloud-first architecture that integrates seamlessly with your existing cloud security stack, providing scalable misconfiguration detection and remediation across multi-cloud environments.
Automated Access Provisioning
Unified processing of employee requests from Slack, web portals, email, and mobile apps through standardized APIs and natural language understanding.
Policy Engine Integration
Integrates with CNAPP tools, such as Prisma Cloud, Orca Security, and Wiz, to leverage existing policy frameworks and compliance rules for comprehensive coverage.
Risk-Based Analytics
Contextual analysis of resource relationships, data flows, and attack surfaces that automatically prioritizes risks based on potential business impact and exposure severity.
Workflow Orchestration
Orchestrates remediation workflows across multiple tools including Terraform, CloudFormation, and cloud-native security services for consistent policy enforcement.
Compliance Automation
Automatically maps misconfigurations to compliance frameworks (SOC 2, PCI DSS, HIPAA) and generates audit reports for regulatory requirements.
Change Management Integration
Integrates with ITSM platforms and DevOps tools to ensure all remediation actions follow organizational change management processes.
Real-World Cloud Misconfiguration Scenarios
See how Torq’s cloud security orchestration transforms complex misconfiguration challenges into automated, policy-driven remediation across diverse cloud environments and security requirements.
Exposed S3 Bucket Remediation
Data Protection
When CSPM tools detect publicly accessible S3 buckets containing sensitive data, Torq automatically analyzes bucket policies, applies appropriate restrictions, and updates Infrastructure as Code templates to prevent recurrence.
Overpermissive Security Groups
Network Security
Overly broad security group rules are automatically identified, risk-assessed based on affected resources, and remediated through least-privilege rule updates with stakeholder approval workflows.
Excessive IAM Permissions
Identity Security
Privileged IAM roles and policies are analyzed for over-provisioned permissions, with automated right-sizing based on actual usage patterns and security best practices.
Unencrypted Resource Detection
Data Encryption
Unencrypted storage volumes, databases, and data in transit are automatically identified and remediated through encryption policy enforcement and key management integration.
Compliance Violation Response
Compliance
Configuration changes that violate regulatory requirements are automatically detected, prioritized by compliance impact, and remediated through policy-driven automation with audit documentation.
Network Segmentation Gaps
Network Architecture
Missing network segmentation and exposed internal services are identified through network topology analysis and automatically remediated through security group and routing updates.
Enterprise Benefits of Automated Cloud Security
Transform your cloud security operations with intelligent automation that scales with your infrastructure while reducing manual workload and improving security posture consistency.
Continuous Security Posture
Maintain consistent security configuration across dynamic cloud environments with real-time monitoring and automatic drift correction that adapts to infrastructure changes.
Accelerated Compliance
Automatically enforce compliance frameworks with policy-driven remediation that maintains audit trails and generates compliance reports for regulatory requirements.
Reduced Attack Surface
Proactively eliminate security gaps through automated remediation of critical misconfigurations before they can be exploited by attackers.
DevSecOps Integration
Seamlessly integrate security policy enforcement into DevOps workflows with Infrastructure as Code updates and automated security testing.
Operational Efficiency
Eliminate manual configuration tasks and free security teams to focus on strategic initiatives while maintaining comprehensive security coverage.
Cost Optimization
Identify and remediate resource misconfigurations that lead to unnecessary cloud costs while maintaining security requirements.
Cloud Platform & Security Tool Integration
Torq HyperSOC™ integrates with leading cloud platforms and security tools through comprehensive APIs and pre-built connectors for seamless orchestration.
Cloud Platforms
AWS, Microsoft Azure, Google Cloud Platform, Oracle Cloud, Alibaba Cloud
CSPM & Cloud Security
Prisma Cloud, Orca Security, Wiz, Lacework, Aqua Security, AWS Security Hub
Infrastructure as Code
Terraform, CloudFormation, Azure Resource Manager, Ansible, Pulumi
DevOps & ITSM
Jira, ServiceNow, GitHub, GitLab, Jenkins, Azure DevOps
