Contents
Get a Personalized Demo
See how Torq harnesses AI in your SOC to detect, prioritize, and respond to threats faster.
As organizations embrace zero trust and strengthen identity protections for human users with multi-factor authentication (MFA), privileged access management, and strict authentication controls, a major blind spot remains: non-human identities (NHIs).
These include API keys, service accounts, OAuth apps, and machine-to-machine credentials, often holding powerful privileged access yet lacking visibility, rotation, or governance. Attackers have taken notice, increasingly exploiting these unmanaged digital identities to breach environments and escalate attacks.
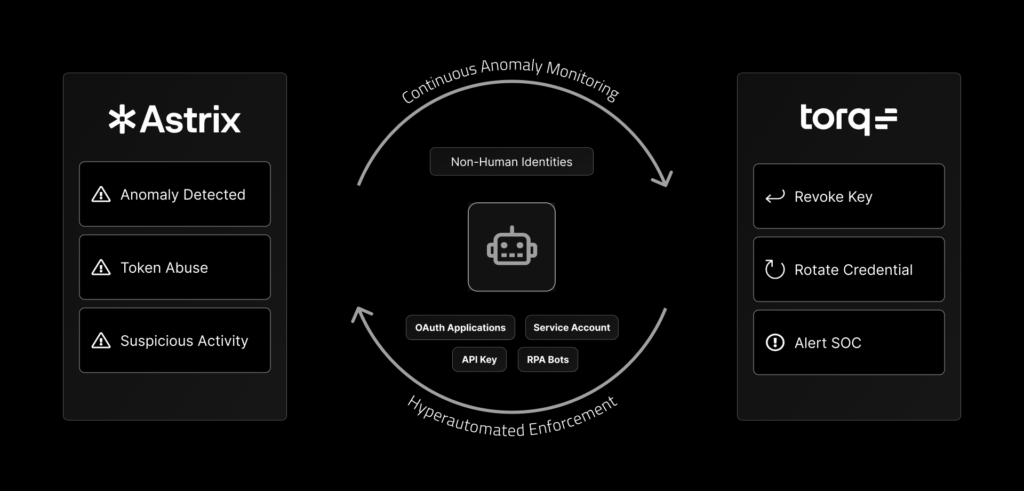
That’s why Torq and Astrix have partnered to deliver a fully automated, intelligent solution for securing NHIs. The solution combines Astrix’s real-time behavioral detection with Torq’s no-code remediation workflows to continuously protect against identity-based breaches.
Why Non-Human Identity Security Needs to Be a Priority
Cybersecurity teams invest heavily in protecting user identities, securing login credentials, and enforcing authentication. However, the rising number of non-human identities (NHIs) often escapes similar scrutiny, creating significant security vulnerabilities. NHIs have become a primary attack vector due to widespread lack of visibility, weak governance, and unmanaged permissions.
Non-human identities (NHIs) are digital identities used by machines, applications, scripts, and services to access systems, data, and resources. Examples include API keys, service accounts, OAuth applications, and robotic process automation (RPA) bots. These identities often have privileged or persistent access but lack proper oversight, lifecycle management, and security controls like credential rotation, MFA, or behavioral monitoring. As organizations increase automation and cloud adoption, NHIs now outnumber human identities, making them a growing target for attackers and a critical priority for identity security.
Common risks associated with NHIs include:
- Over-permissioned or over-privileged access
- Lack of credential rotation and MFA
- Unused tokens and keys increasing vulnerability
- Poor visibility across cloud and SaaS integrations
- Increased susceptibility to credential-based cyberattacks
The Hidden Risk Behind Digital Identities
Non-human identities frequently possess highly privileged access with little oversight. Service accounts, API keys, OAuth applications, and other machine identities can remain active indefinitely without periodic checks, making them prime targets for exploitation. Credential misuse or breaches involving these identities often go unnoticed until damage is already done.
Why Traditional Identity Management Falls Short
Traditional identity solutions, such as Identity Access Management (IAM) and Privileged Access Management (PAM), primarily focus on human users. They enforce policies like MFA, regular password rotation, and robust activity monitoring. These tools, however, are not built for automated services or non-human identities, leaving a substantial gap in security posture.
How Torq and Astrix Automate Non-Human Identity Protection
Torq and Astrix seamlessly integrate to deliver a comprehensive solution that automates the detection and remediation of non-human identity risks. By combining Astrix’s advanced behavioral analytics with Torq’s intelligent automation, security teams gain unprecedented visibility and control.
Detecting Anomalous Behavior in Real Time
Astrix Security applies behavioral analysis typically reserved for human identities to NHIs. By monitoring activity patterns, Astrix detects unusual behaviors, unauthorized access, or suspicious usage in real-time, closing gaps often overlooked by conventional identity management solutions.
Triggering No-Code Remediation Playbooks Automatically
When Astrix identifies an anomaly, Torq instantly triggers no-code remediation workflows based on preset rules. These automated playbooks rapidly address issues such as revoking access, rotating credentials, disabling unused identities, or alerting security teams, streamlining threat mitigation, and significantly reducing response times.
Enforcing Least-Privilege Access with Continuous Policy Management
Astrix continuously assesses and identifies NHIs with excessive privileges and dormant or outdated credentials. Torq automates the enforcement of least-privilege access policies by proactively removing unnecessary permissions, revoking unused tokens, and continuously updating identity posture, ensuring minimal attack surface exposure.
Strengthening Authentication and Access Control with Automation
Static access controls and manual credential management are no longer sufficient. As organizations adopt cloud-native infrastructure, DevOps pipelines, and an ever-growing array of third-party services, the number of digital identities — especially non-human ones — has exploded.
Without automation, ensuring secure authentication and effective access control becomes unmanageable at scale. Automating these processes enhances identity hygiene, reduces risk, and allows security teams to enforce policy consistently across complex, dynamic environments.
Simulating MFA and Rotating Credentials Automatically
While multi-factor authentication (MFA) remains a cornerstone of identity security for human users, non-human identities often can’t use MFA in traditional ways. Organizations are turning to automated mechanisms that simulate MFA behavior like enforcing time-limited credentials, rotating keys after specific usage thresholds, or applying context-aware access restrictions. Automatically rotating credentials or secrets based on predefined policies helps prevent unauthorized reuse, reduce the impact of credential leakage, and limit the exposure window for attackers.
Securing Third-Party Integrations and External Access Points
Third-party applications and services can significantly expand an organization’s attack surface if not properly secured. Many breaches originate from overly permissive or forgotten integrations. Automating these external connections’ discovery, evaluation, and control is essential for maintaining security. By continuously monitoring for risky behaviors, organizations can automatically revoke or reconfigure access, enforce least-privilege principles, and minimize external risk without relying on manual reviews.
Common Identity Security Challenges and How Torq Solves Them
Closing Visibility Gaps Across Cloud and SaaS Environments
Torq consolidates identity and security signals from your entire security and tech stack, providing unified visibility into NHI risks. By centralizing this information, Torq enables precise identification and quick remediation of identity-related vulnerabilities across the entire digital ecosystem.
Stopping Credential Misuse and Phishing-Style Exploits
With automated playbooks, Torq instantly identifies and stops credential misuse, proactively revoking compromised tokens, and preventing phishing-like attacks on NHIs. This immediate response capability significantly reduces security risks and minimizes potential damage.
Eliminating Alert Fatigue and Manual Remediation Backlogs
Manual remediation processes can overwhelm security teams, resulting in alert fatigue and delayed responses. Torq autonomously resolves repetitive and high-volume NHI-related incidents, reducing operational overhead and allowing security analysts to focus on strategic security initiatives.
Securing the Future of Identity Security
As the volume and complexity of non-human identities grow, so does the urgency of securing them with the same rigor applied to human users. API keys, service accounts, and automation credentials often fly under the radar, creating a hidden and highly exploitable attack surface. Traditional tools were never designed to manage this scale or speed.
By integrating behavioral detection and intelligent auto-remediation, Torq and Astrix empower security teams to proactively manage identity risk, streamline response, and enforce consistent access controls. The result is a scalable, flexible, and future-proof approach to identity security that addresses today’s threats and tomorrow’s challenges.
Ready to close the gap on non-human identity risk? Request a demo to see how automated identity security works in action.








