This post was previously published on The New Stack
Discovering security threats is good and well. But, in many cases, simply knowing that a threat may exist is not enough.
Instead, you also need threat intelligence enrichment. Threat enrichment plays a critical role in helping to evaluate and contextualize threats, root out false positives and gain the insights necessary to mitigate risks as efficiently and quickly as possible.
Keep reading for a primer on how threat enrichment works, why it’s important and where to look to get key insights from threat intelligence data.
What Is Threat Intelligence Enrichment?
Threat intelligence enrichment is the process of gaining context through security threat data in order to better understand the threat.
For example, imagine you’ve detected port scans against your servers. You know the IP addresses of the hosts from which the port scans originated, but you don’t know much more than this.
In this case, threat intelligence enrichment could include insights such as where the offending servers are located and which operating systems they are running. This information may, in turn, be useful for determining whether you’re dealing with a probe against your network from a generic botnet or a port scan operation that originates from a more sophisticated group of attackers, like state-sponsored actors. Threat intelligence enrichment could also inform you whether port scans like the type you’ve experienced are associated with any specific known risks, like a pervasive malware attack recently launched against other organizations.
All these additional threat data insights would provide you with the information you need to react as intelligently and efficiently as possible to block the threat. They would also help you know how dangerous the threat might be. For example, a threat from a generic botnet is probably less risky than a targeted attack by sophisticated threat actors, and threat enrichment helps you know the difference.
Which Threat Enrichment Data Do You Need?
The data that threat intelligence enrichment provides can vary widely in scope and form. In general, however, the more data you have to contextualize a threat, the better.
At a minimum, threat enrichment data should include information about where a threat originated, which resources it affected and when the threat was detected or was active. You should also determine whether the threat was correlated chronologically with any separate attacks or attempted attacks that took place against other systems.
In some cases, threat intelligence enrichment can go deeper. For example, as noted above, threat enrichment might provide details about whether the pattern of security events you’ve witnessed is associated with a specific type of attack or group of attackers. This type of information is usually generated by security researchers who systematically study cyber events.
Threat Intelligence Data Sources
There are many ways to obtain threat data that enables threat intelligence enrichment. You should take advantage of all threat intelligence sources available to you.
Start by compiling as much data as you can from your own internal systems to provide context on a threat. This includes information like the time a threat was detected and the systems it affected, as noted above.
You can also use threat intelligence databases or feeds, which record information about known threat types, patterns and actors. Some of these sources, like MISP, are free and open source. Others are proprietary. They either require subscriptions , or are built into proprietary security platforms you use.
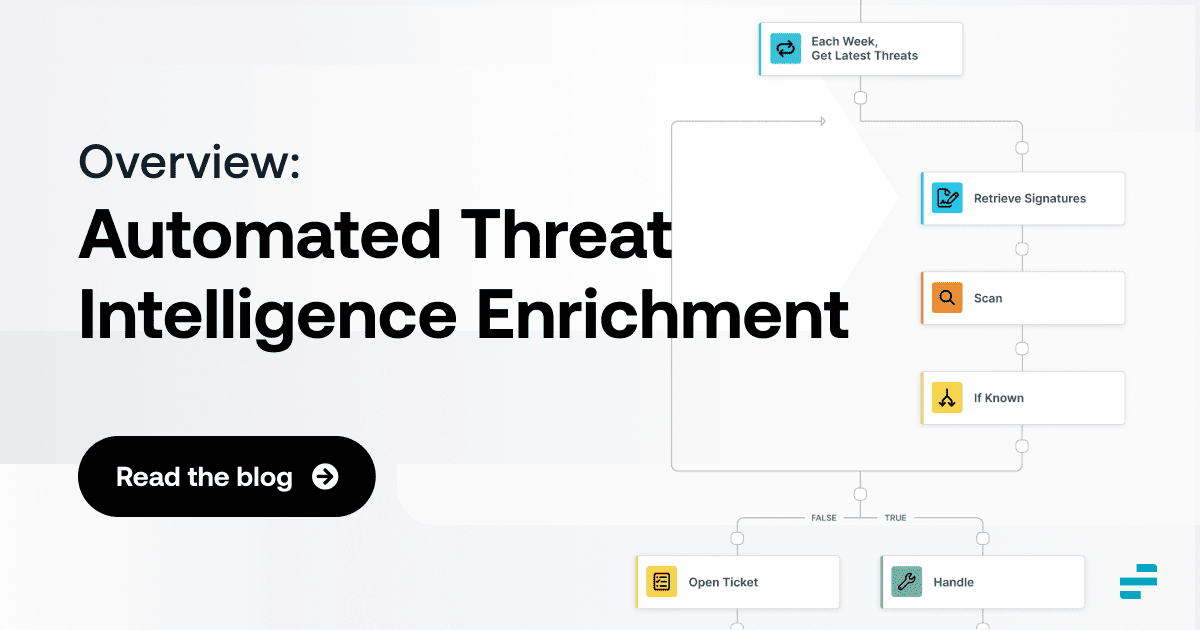
Automating Threat Intelligence Enrichment
You can, of course, manage your threat intelligence data manually by correlating and comparing it by hand.
That approach, however, is not practical at scale. A better strategy is to usef automation tools like Torq, which provides continually updated threat intelligence by automatically collecting enrichment data about threats that may affect your business. An automated approach to threat intelligence enrichment not only saves your team time, but also helps you take full advantage of as much threat data as possible.
Putting Automated Threat Enrichment to Use
To a large extent, you can automate the operationalization of threat intelligence data by using it to drive automated workflows. You can, for example, configure specific actions based on threat enrichment data.
In some cases, however, threat enrichment will require some manual effort. In the case of complex threats, your team will need to study enrichment data by hand to determine the best course of action.
But in general, you should take advantage of automation wherever possible. The more you automate, the faster you can block threats and the lower your overall security risk.