Contents
Get a Personalized Demo
See how Torq harnesses AI in your SOC to detect, prioritize, and respond to threats faster.
At Torq, we’re all about pushing boundaries and driving innovation. But we can’t afford to treat security as an afterthought in our relentless pursuit of speed and creativity. As a lean and agile team, we’re constantly challenged to stay ahead of emerging threats without slowing down our momentum.
In this blog, I break down how we Hyperautomated our software development lifecycle (SDLC) to improve security coverage, reduce friction, and keep our R&D teams shipping fast.
The SDLC Challenge: Balancing Speed and Security
Our software engineering teams manage various components and microservices, each with unique functionalities requiring meticulous threat modeling and vulnerability assessments. Modern software engineering integrates open-source and proprietary libraries, introducing potential security vulnerabilities in individual and shared components across teams.
The primary challenge is ensuring these vulnerabilities are continuously identified and mitigated before they compromise the production environment. Simultaneously, it’s crucial to maintain an environment where teams can continue to innovate and deliver high-quality software without being hindered by security concerns.
In short, how do we ensure that potential application security vulnerabilities are identified and resolved before they threaten our production environment while empowering our teams to innovate and deliver high-quality software? That’s where SDLC automation and security Hyperautomation come in.
Building Our SDLC Automation Architecture
Our solution started with integrating an Application Security Posture Management (ASPM) platform, which provided complete control over our supply chain and SDLC. This visibility extends across open-source packages, Dockerfile dependencies, and container images — everything from the far-right side of the SDLC. But visibility alone can be overwhelming.
We needed to take it further by leveraging Torq’s Hyperautomation capabilities. Hyperautomation enabled us to combine no-code workflows, AI-driven orchestration, and system-wide integrations into a single, scalable SDLC framework.
Here’s how our SDLC automation stack works in the context of our Application Security events pipeline:
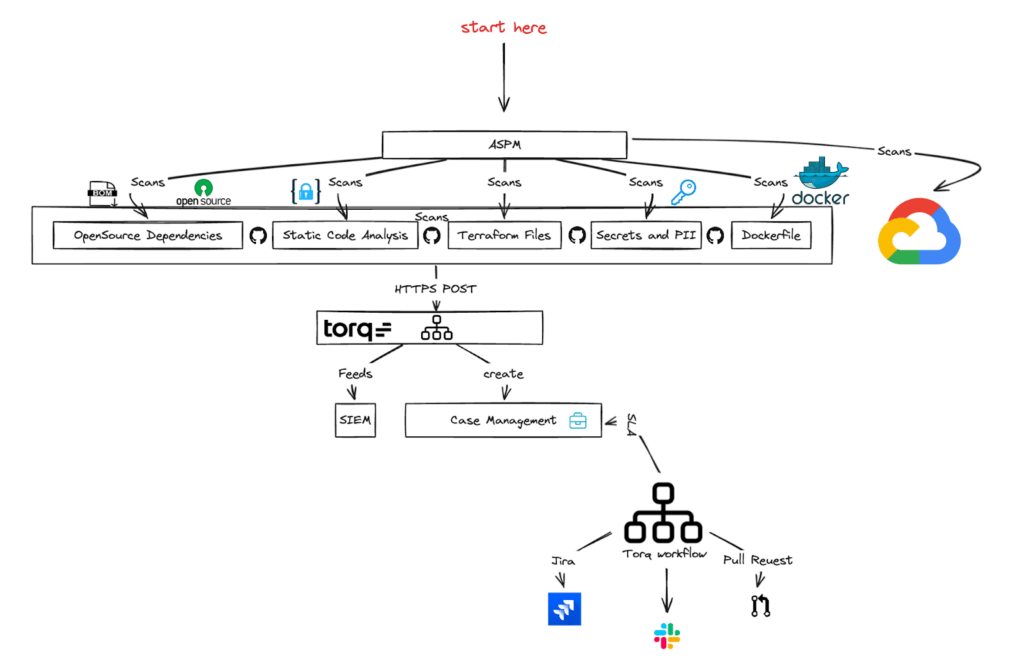
Inside Our Hyperautomated SDLC Pipeline
My vision was simple but ambitious: create a seamless, automated SDLC pipeline that transforms how we manage vulnerabilities. Here’s how we did it:
- Torq workflows: Aggregate vulnerabilities by category (e.g., open-source, SBOM, secrets) and severity, streamlining issue management.
- Centralized case management: A single, aggregated Torq case for each repo, simplifying investigation and eliminating redundant tickets.
- Automation at scale: With one click, generate Jira tickets, pull requests, and Slack notifications, all customized to our R&D teams’ templates.
- Daily Service Level Agreement (SLA) reminders: Automated workflows ensure SLAs are met, keeping teams on track and focused.
I used Torq’s workflows to categorize and aggregate issues, while centralized case management simplifies investigations for R&D teams. Automation facilitates generating Jira tickets, pull requests, and Slack notifications, keeping teams aligned with daily SLA reminders. This ensures our teams can focus on what matters most — innovation without compromise.
Below is an illustration of what that automated SDLC flow looks like:
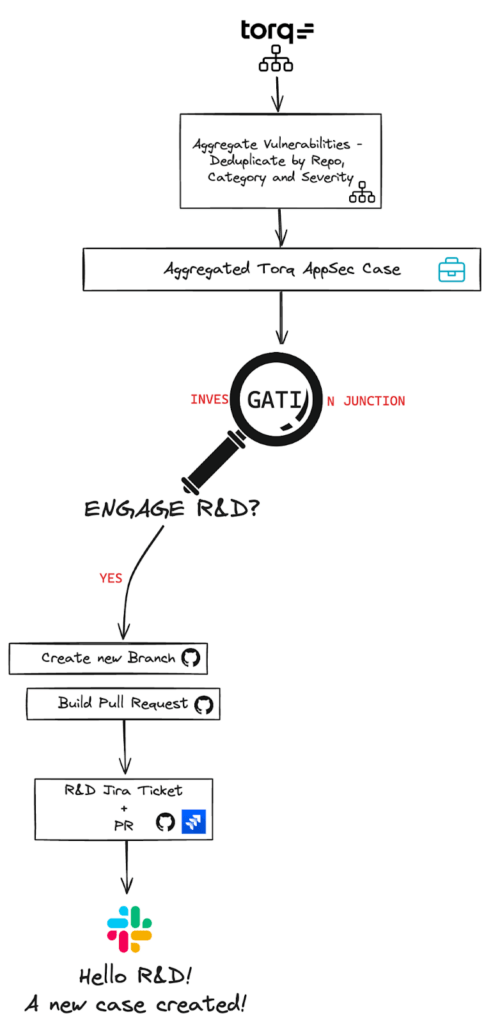
The SDLC Automation Implementation In Action
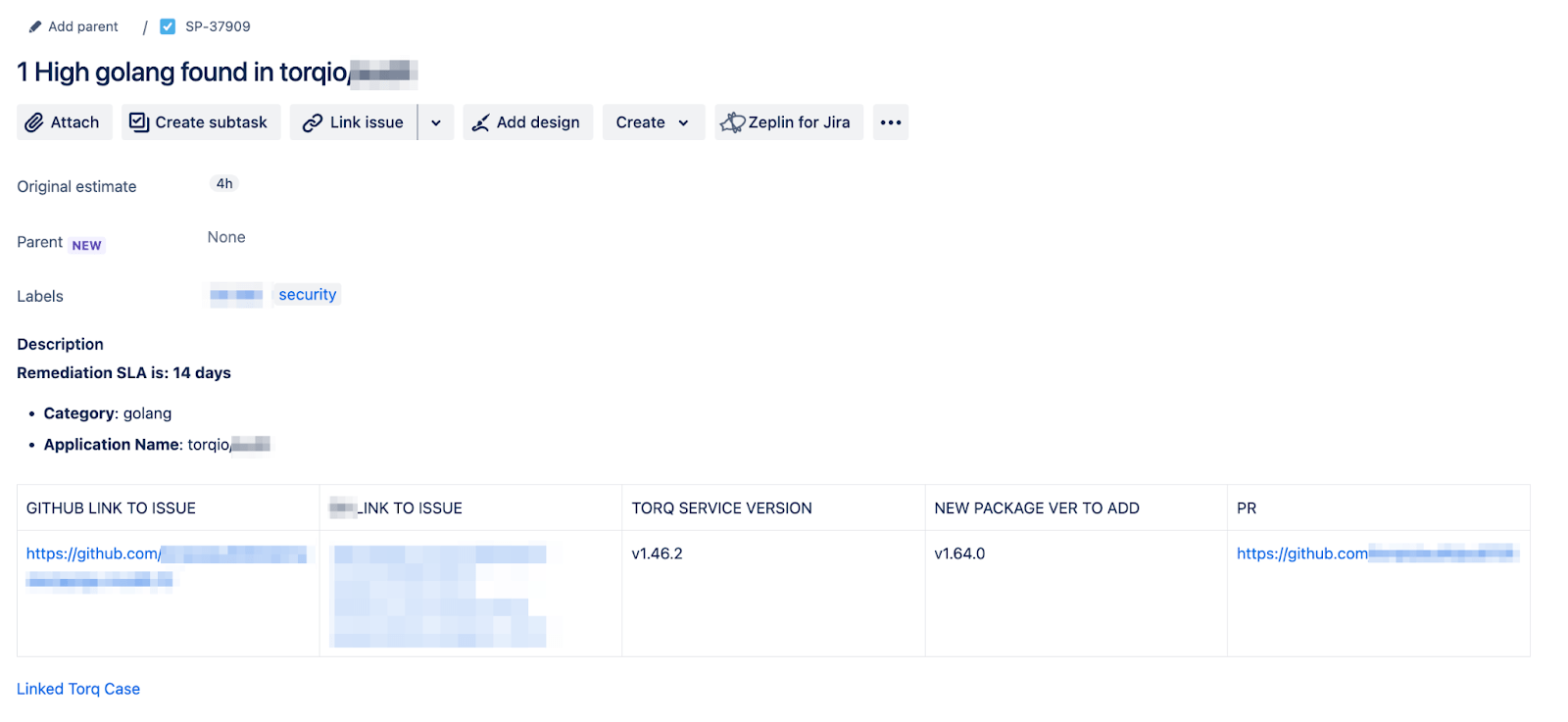
When the ASPM flags a new issue, Torq automatically creates a centralized case grouped by severity and category for that specific repository — eliminating duplicate tickets and reducing noise.
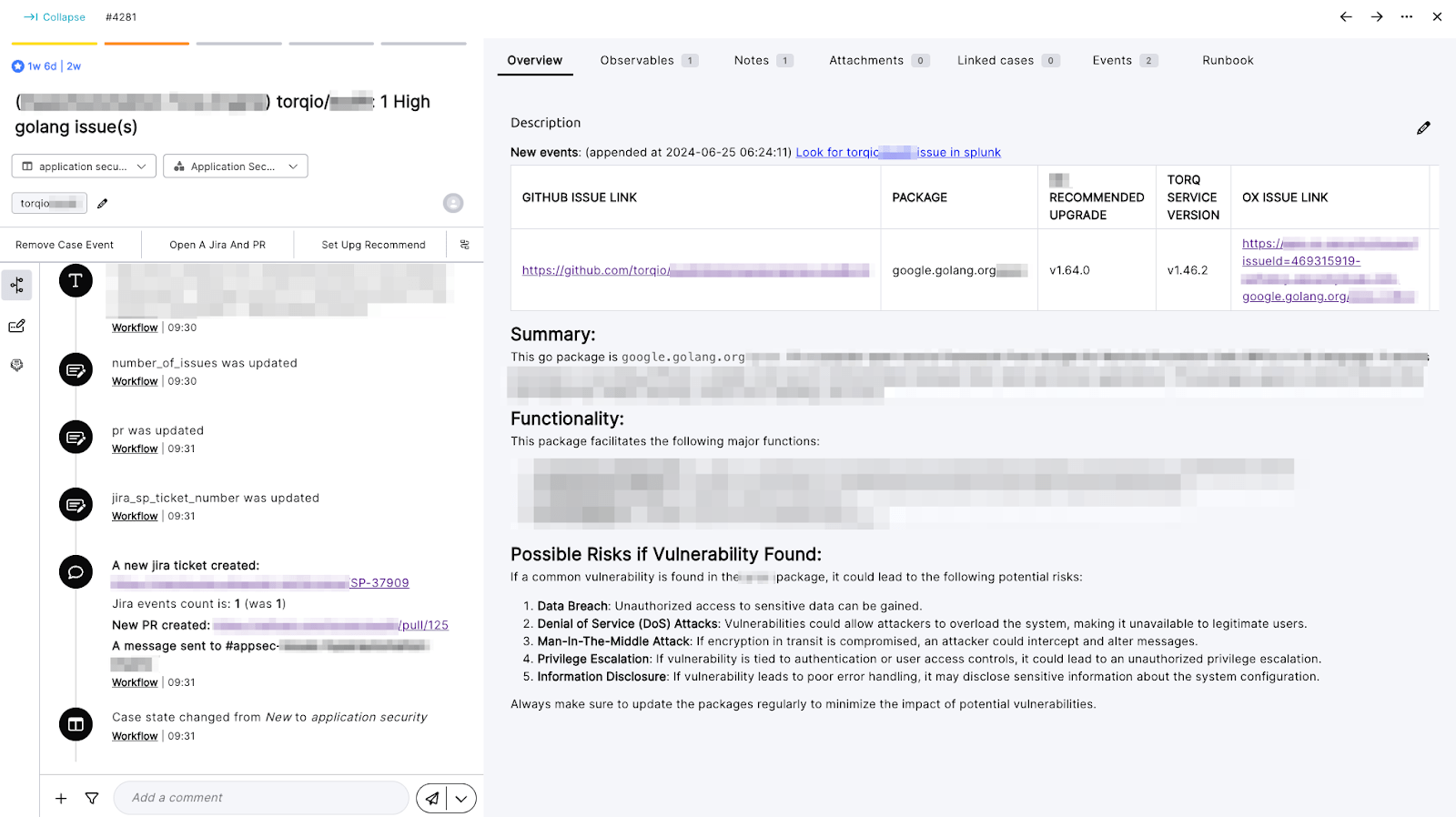
The case includes a detailed table with affected packages, suggested upgrades, a risk verdict, and direct links to GitHub and ASPM findings.
If action is needed, R&D can trigger a predefined workflow with one click, auto-generating a Jira ticket, a pull request, and a Slack notification, all while staying aligned with SLA requirements.
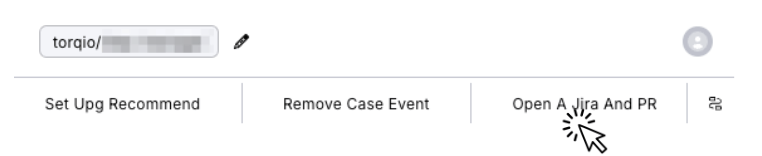
With enriched data and automated context in hand, our dev teams can patch vulnerabilities quickly. Each remediation follows Torq’s change management and SDLC policies, flowing through peer review and automated deployment like any standard feature or update.
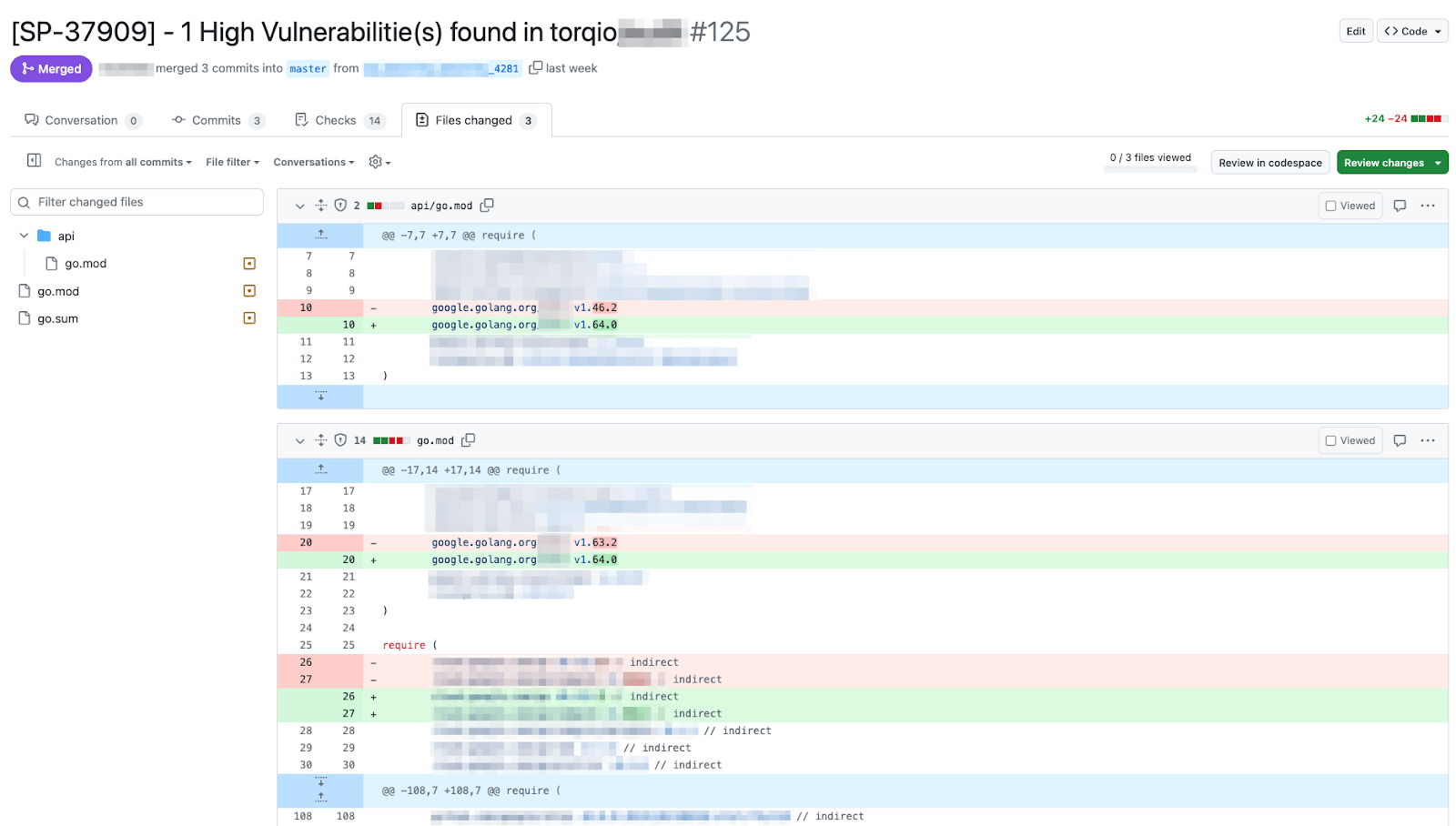
SLA Compliance Made Simple
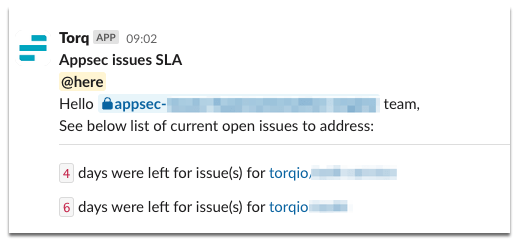
In line with Torq’s policy, every issue is assigned a severity-based SLA. To ensure timely resolution, a daily automated workflow reviews open cases and notifies each R&D team of their remaining time to address these issues. SDLC automation keeps teams on track, ensuring vulnerabilities are managed effectively without disrupting ongoing development.
That’s the power of SDLC Hyperautomation: fast and repeatable.
When To Implement SDLC Hyperautomation
Achieving fully automated vulnerability management may sound like an ambitious goal, but it’s essential for the velocity of modern security operations. Within Torq, we strive for a seamless process from detection to merge. Successful SDLC Hyperautomation can become possible when:
- The vulnerability management program is mature and well-established
- There are consistent, repeatable actions required for product or software updates
- The SDLC includes a robust testing process, acting as a safety net to catch any oversights during automation
The Business Impact of SDLC Automation
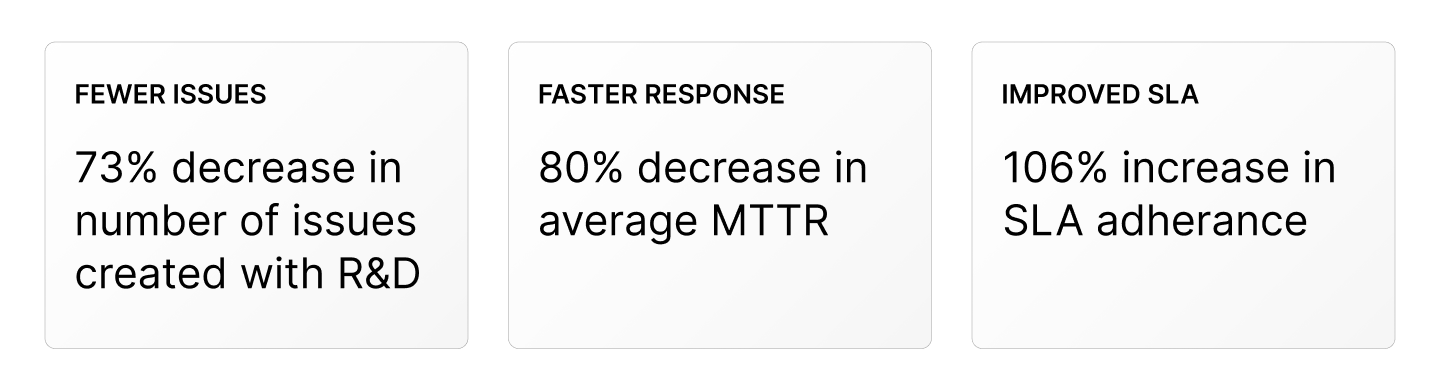
The result of our efforts was a fully automated vulnerability management process that has revolutionized our approach to AppSec. We’ve slashed remediation times, improved SLA adherence, and empowered our R&D teams to deliver secure, high-quality software faster than ever. Here was the quantitative impact:R&D teams to deliver secure, high-quality software faster than ever. Here was the quantitative impact:
Ready to Hyperautomate your AppSec approach? Torq can help you build SDLC automation workflows that scale, simplify security, and eliminate busy work.