For years, efficient Case Management has been one of the single most challenging tasks for security operations professionals. It involves ensuring all threats are proactively identified and prioritized based on risk criticality, and then rapidly investigated and appropriately elevated across all organizational cybersecurity platforms and tools. Optimally, it sets up a near-bulletproof incident response posture that makes the most of an organization’s cybersecurity ecosystem.
However, time and time again, legacy SOAR platforms have failed to deliver on the promise of Case Management. These earlier tools simply can’t keep up with the pace, volume, and variety of evolving cybersecurity threats. They also don’t offer SecOps the flexibility to quickly pivot through records to accurately assess whether or not they’re facing a targeted campaign, a new and novel threat, or an ongoing, pervasive threat that could stop business in its tracks.
The new Torq Hyperautomation platform was purpose-built from the ground up to deliver the comprehensive Case Management capabilities SecOps have been demanding for years, and never benefited from—until now. Unique modern AI co-pilot capabilities drive efficiency even further, ensuring that security analysts are assisted by cutting-edge technology to make the right choices and not miss any details.
Hyperautomating Contextual Security Case Resolution
Torq Hyperautomation is unique in that it rapidly and accurately collects a large number of unprocessed events and signals, and organizes them into contextually-enriched cases, intelligently ordered by severity, priority, and field of ownership. It also orchestrates the analysis and remediation of security cases across multiple organizational functions, and tracks all security decisions in a single dynamic, hyperautomated framework.
The benefits of Torq Hyperautomation’s Case Management approach are significant. By hyperautomating security signal detection, it reduces noise and manual investigations by up to 70%. Its flexible framework also streamlines decision-making and automatically enriches data, cutting through the noise and separating minor, easily-remedied incidents from significant, and existential organizational threats.
Here are some of the key benefits and how they work to streamline your case management processes:
Automated Case Management
Torq empowers organizations with the power to hyperautomate common use cases with repeatable workflow processes that launch all the necessary steps, such as customizable decision trees that integrate human intervention. This includes scenarios such as escalation or case handoff. SOC Analysts can analyze and create workflows to efficiently process a case or issue.
By hyperautomating case management, security teams can streamline workflows and focus on high-priority threats. Torq empowers teams to automatically create, update, and manage cases in response to security alerts, ensuring they can quickly prioritize and respond. Analysts are freed from the mundane to concentrate on higher-level security activities.
Automatically Enriches Security Case Context
Torq’s Use Case management solution automatically transforms large numbers of events and signals into contextually-enriched cases. All cases are ordered by severity, priority, and ownership with the intelligent correlation of signals to open, update, enrich, or close cases, with human interaction being optional.
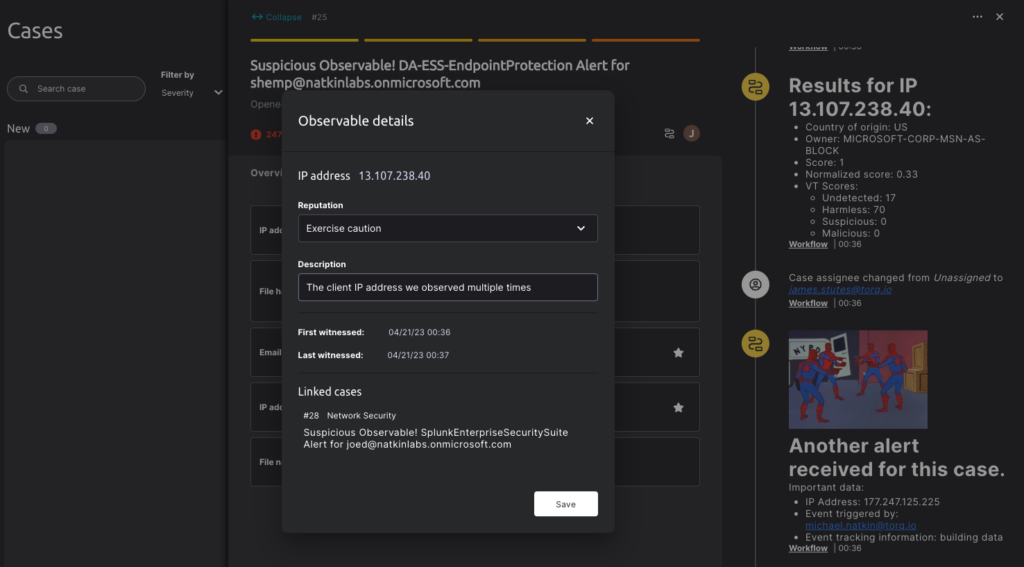
Accelerates Discovery and Remediation of Threats with AI
Torq’s unique ability to hyperautomate case management handling using AI that enriches the context of the situation, so you only need to involve humans when necessary, such as when a judgment call is required. For example, when an alert is automatically sorted by priority, intelligent analysis is performed to determine the next steps with our flexible event-driven workflows that connect any of your existing security tools to perform the required actions.
In this example, a suspicious file was detected on the endpoint, and the IT Analyst wanted to check if this particular threat was already known to be suspicious or malicious on VirusTotal.
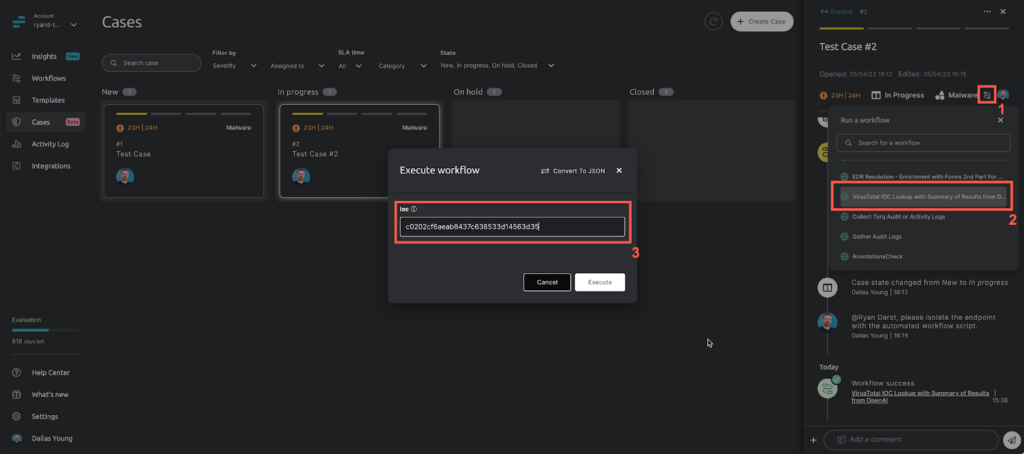
Utilizing the power of ChatGPT, the findings are condensed to two sentences that state that 56 of 71 AV engines detected the threat as malicious. Contrast that with the overly-verbose output that you would typically receive on VirusTotal. This saves tremendous time and summarizes the incident in a readily consumable human-readable format.
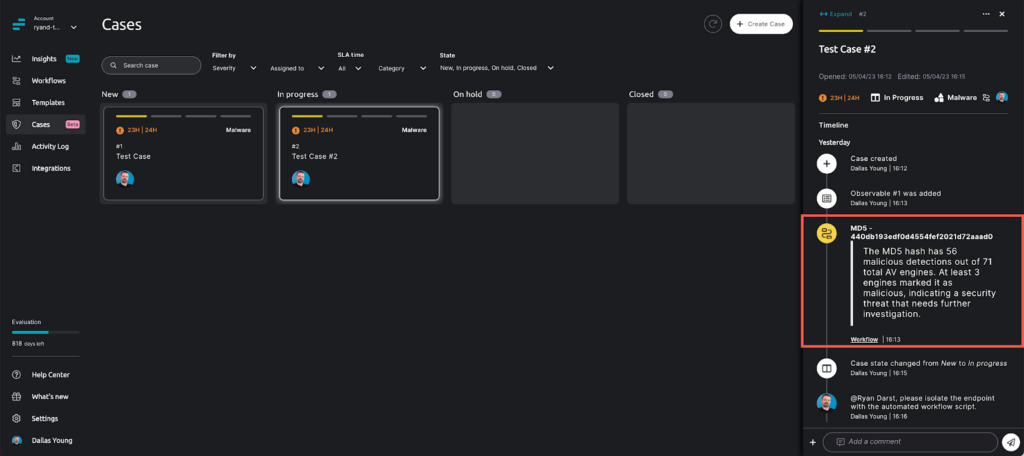
Torq can then execute automatic remediation workflows to run a scan of the environment for persistence anywhere on the network, automatically clean the endpoint, or quarantine it for further analysis by a SOC Analyst.
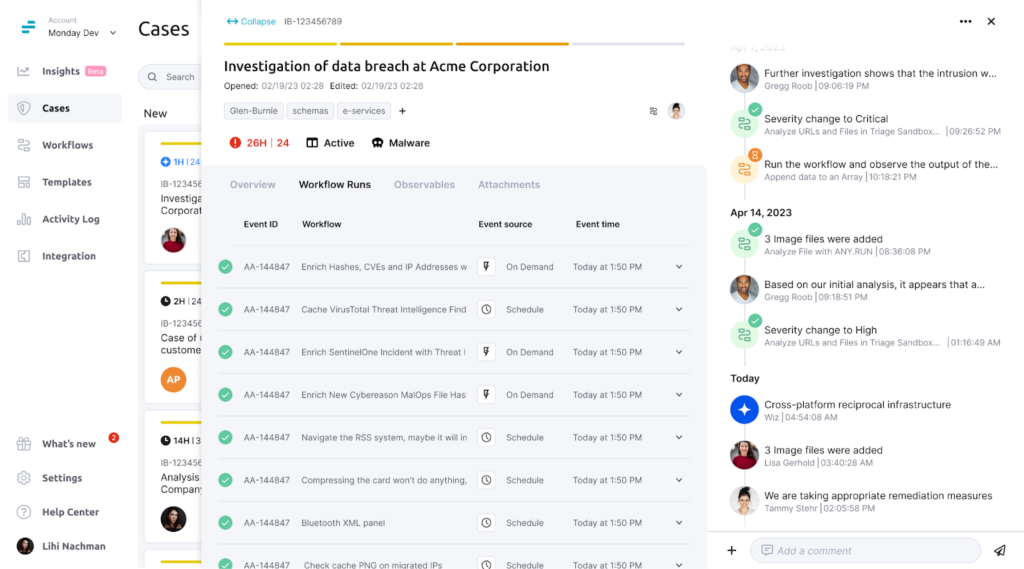
Unified Case Management
SOC Analysts can access a unified view of each case and follow essential processes for handling and resolving cases. Torq’s intelligent case management empowers them to take action confidently, reducing the risk of human error. Handoffs between SOC Analysts occur seamlessly via hyperautomated processes, with all the relevant case details at hand.
Collaboration outside the security operations center is easily done within the platform, which is especially helpful in promoting cross-team collaboration with more complex incidents requiring multiple subject matter experts. Each external team can resolve security issues efficiently using their tools of choice, such as, but not limited to, Atlassian Jira, ServiceNow, Github, and more.
Precision Accuracy and Actionable Outcomes
Torq Hyperautomation’s Case Management capabilities curate accurate and actionable data to identify service and security issues as they develop. Real-time analytics and long-term analysis help identify service trends and determine areas where SOC Analysts or other teams could benefit from improved efficiency as a result of introducing automated investigation and containment strategies and tools. Effective reporting is available to help monitor progress and track performance which helps SOC Analysts resolve cases more efficiently, leading to better outcomes.Want to learn more about how Torq Hyperautomation Case Management can dramatically enhance your security workflows so you can stay ahead of emerging threats? Test drive Torq Hyperautomation, here: https://torq.io/demo/








