Contents
Get a Personalized Demo
See how Torq harnesses AI in your SOC to detect, prioritize, and respond to threats faster.
Modern security teams are wrestling with a new kind of sprawl — one built not on endpoints or networks, but on SaaS. Identity drift, over-permissioned apps, AI tools, and unchecked data access create thousands of risks every day. Most incidents now start with who has access to what, not malware on a machine. And with SaaS adoption surging across every department, the attack surface expands faster than any manual control can keep up.
In Episode 6 of the AMP’d Sessions, we sat down with Todd Wilson, Head of Global Channels and Alliances at Reco, to show how organizations are tackling one of the hardest problems in security today: SaaS access risk. From shadow AI tools to over-permissioned apps to sensitive data movement inside platforms, the attack surface has shifted from endpoints to identities.
Through this integration, Reco maps the movement and Torq fixes it. Together, they turn messy SaaS environments into precise, governed, autonomous workflows.
Reco: Identity-Driven SaaS Visibility for the Modern SOC
SaaS is now the largest attack surface most companies have — and usually the least monitored. AI tools accelerate adoption even further, stacking identity drift, risky permissions, and shadow AI usage faster than humans can track.
Reco solves this by giving security teams deep, identity-first visibility across every SaaS app in use. That includes:
- Full discovery of all sanctioned and unsanctioned SaaS and AI apps
- Mapping who has access to what and whether that access is justified
- Identifying risky permission sets, API scopes, and OAuth grants
- Tracking data movement inside platforms like Google Drive and Microsoft 365
Enterprises often have more than 2,000 AI apps in active use, many granted through social logins, with wide-open access to sensitive data. That visibility alone changes the conversation — but visibility without action just moves the problem.
That’s where Torq comes in.
How the Reco + Torq Workflow Works
When Reco detects a high-risk SaaS access event — a suspicious AI app connection, abnormal permission grant, or data exposure — it sends that signal straight into Torq HyperSOC™. From there, agentic AI takes over.
Here’s the full flow as demonstrated in the AMP’d episode.
1. Reco Flags a Risky SaaS Access Event
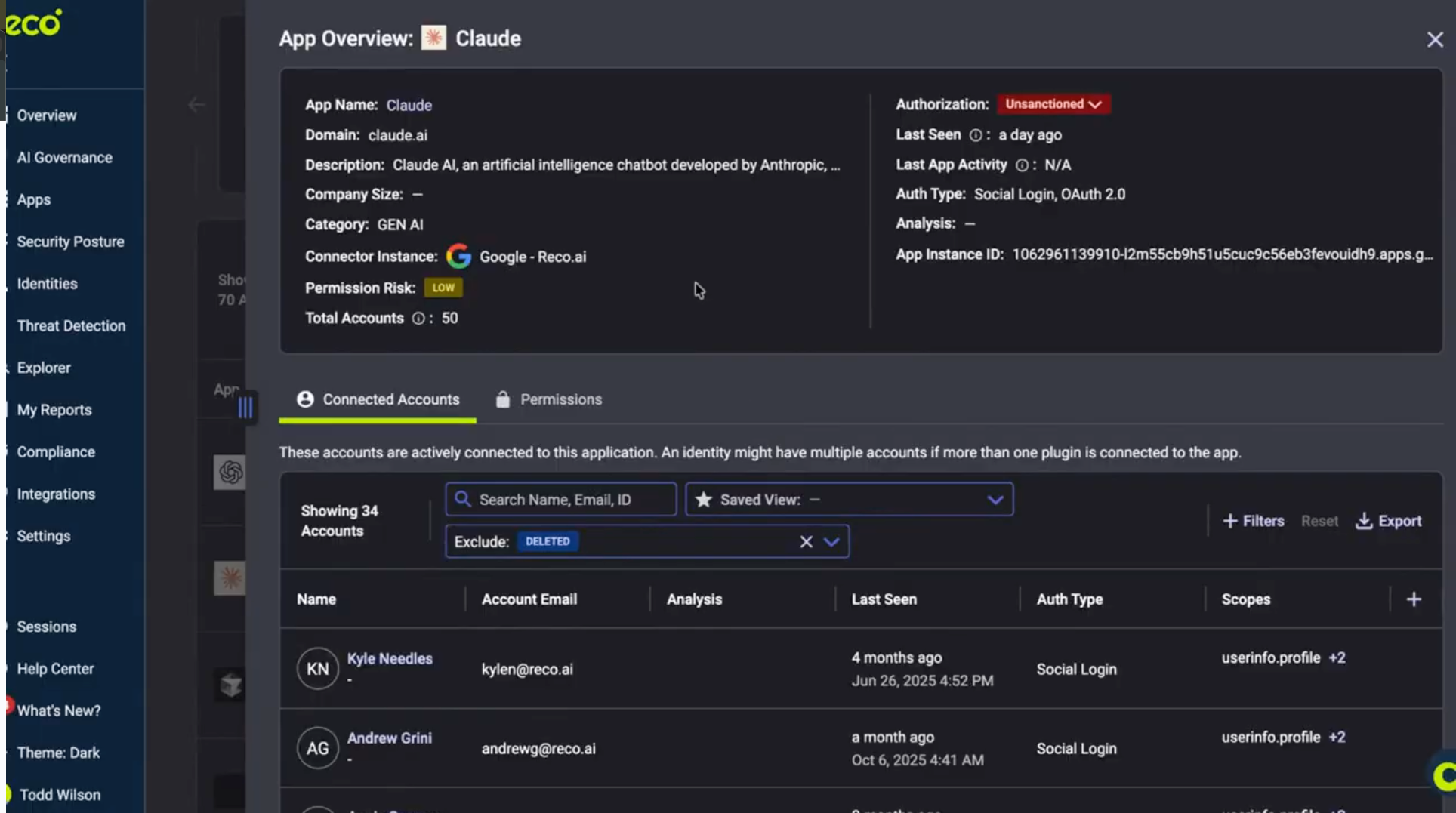
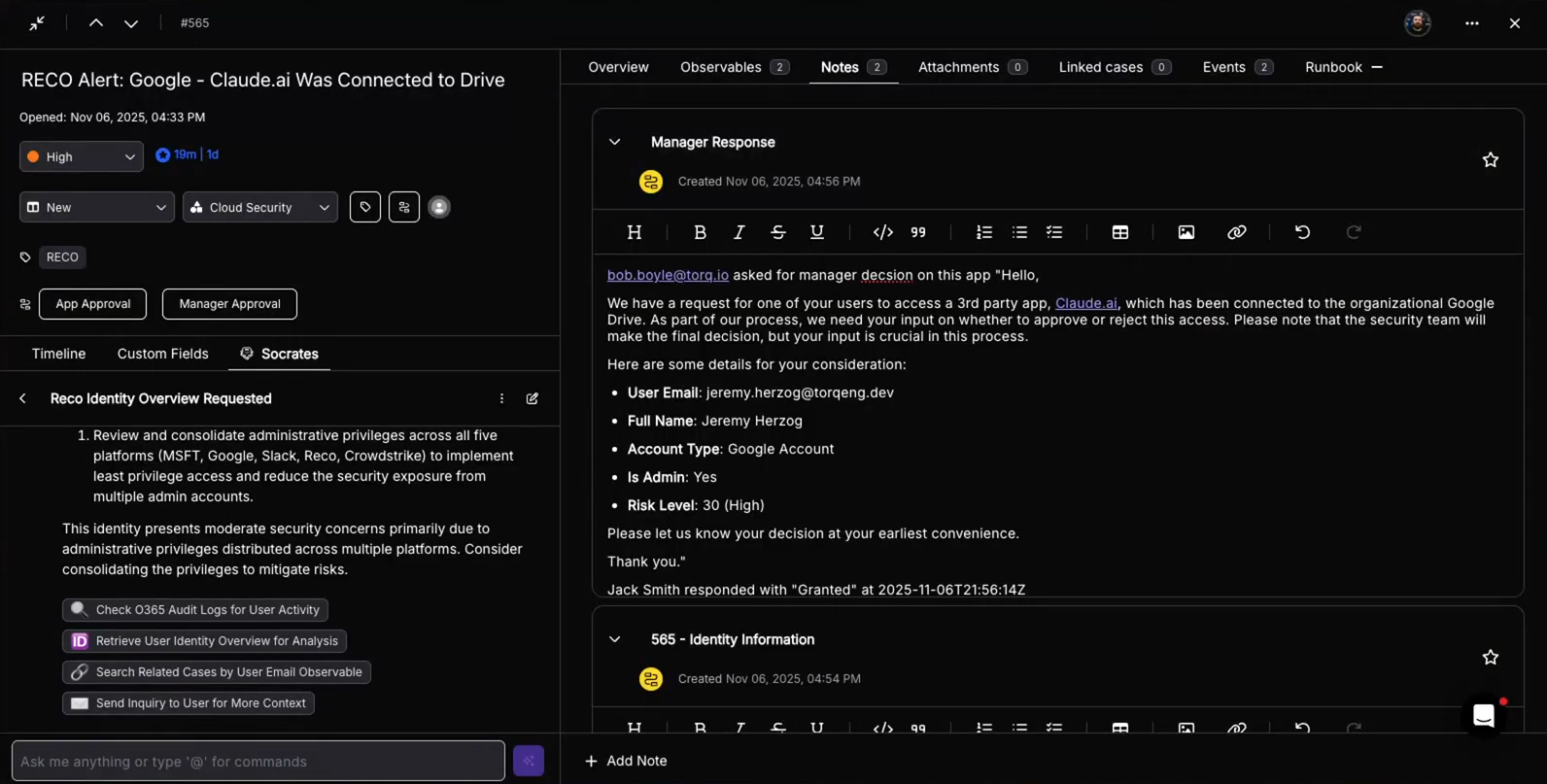
In the demo, Reco identifies a user connecting Claude.ai to their corporate Google Drive — a risky action depending on the user’s role, data access, and organizational policy.
Reco enriches the event with identity context:
- Who the user is
- What they attempted to connect
- What data the app is requesting
- Whether the app is sanctioned, unsanctioned, or unknown
- The user’s data exposure profile (PII, sensitive files, etc.)
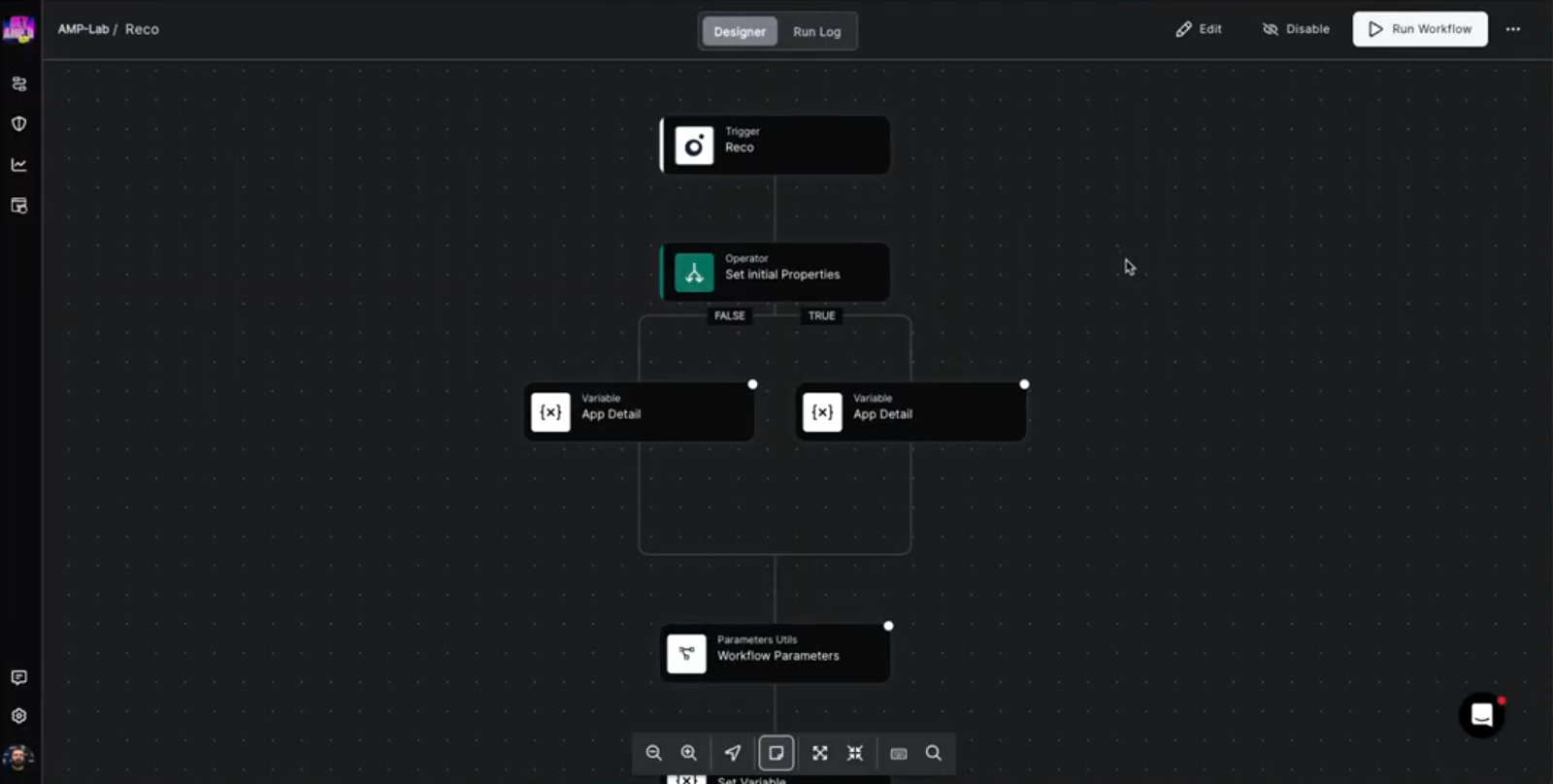
2. HyperSOC Takes Over with Automated Validation and Policy Checks
Torq receives the Reco alert and triggers a Hyperautomated workflow that:
- Pulls Google Workspace identity and group data
- Checks for pre-approved AI app
- Looks for personally identifiable information (PII) exposure tied to the user
- Evaluates the request against business policy
- Automatically revokes the connection if it violates policy
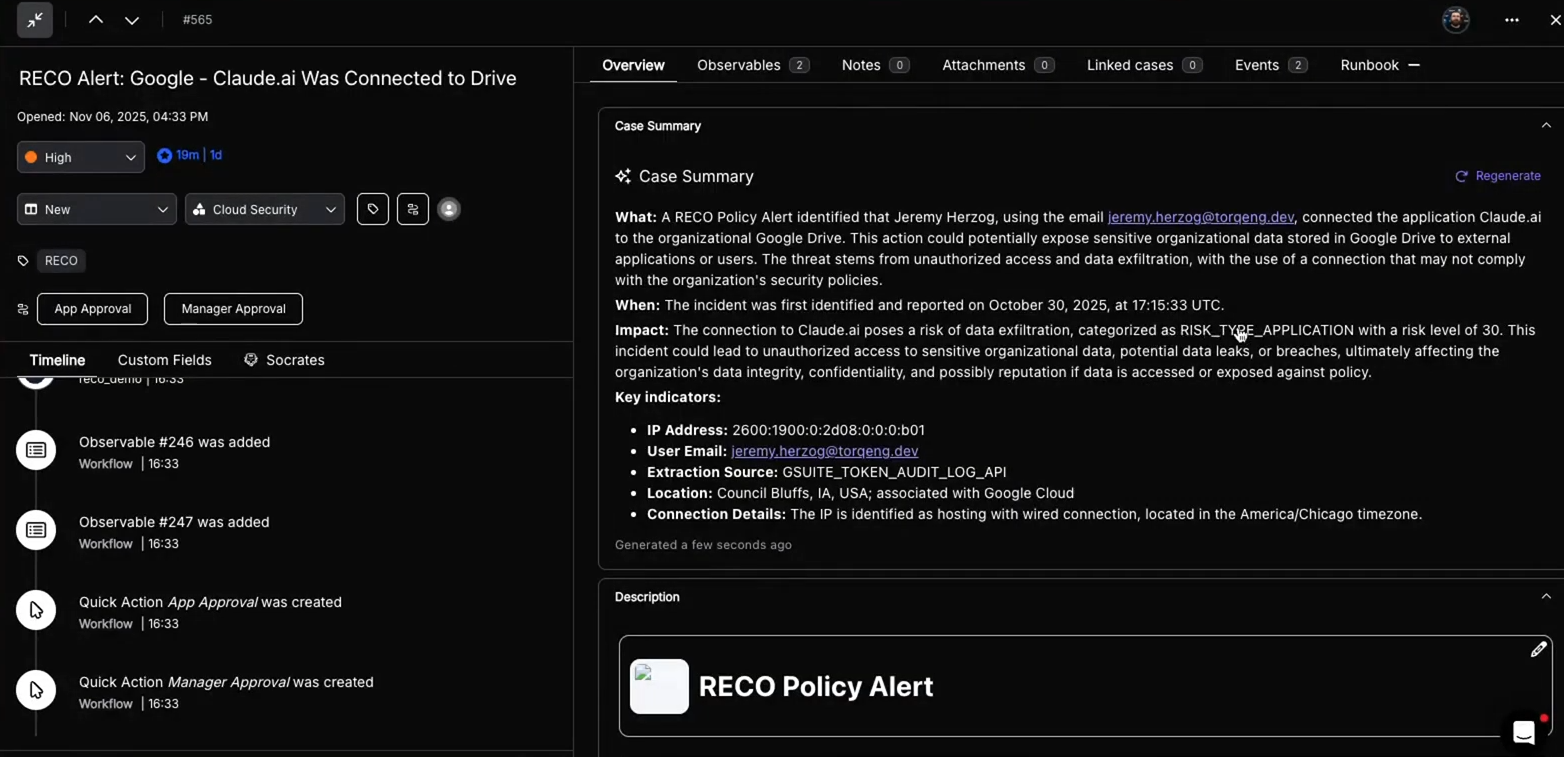
3. Socrates Investigates
If the case requires deeper investigation, Socrates, Torq’s AI SOC Analyst, steps in and:
- Queries Reco for additional identity and permission detail
- Summarizes risk in natural language
- Writes a full AI-generated case summary
- Suggests next-best actions aligned with internal policy
4. Autonomous Remediation
If the access request isn’t inherently malicious but needs validation, Torq handles it with a workflow that:
- Opens a case
- Notifies the user’s manager in Slack
- Summarizes the risk and context
- Asks for approval or denial
- Logs all decisions in an immutable timeline
Once a decision is made:
- If denied: Torq revokes the connection, restricts the user, and sends a notification.
- If approved: Torq removes restrictions and allows the app connection automatically.
Every step is consistent, policy-aligned, and documented. What once took hours of email back-and-forth now happens in minutes — or, in some cases, no time at all, if autonomous closure is enabled.
“What could have taken 8 hours of research is now 15 minutes. So if an analyst has to get involved — which most likely they don’t have to — it’s 15 minutes or zero.”
– Todd Wilson, Head of Global Channels and Alliances at Reco
Better Together: Torq + Reco
The Reco + Torq partnership gives security teams something they’ve never had before: identity-driven SaaS visibility and instant, autonomous control.
Together, we deliver:
- Identity-driven context on every access risk
- AI-to-AI triage and investigation across Reco and Torq
- Autonomous remediation that enforces policy at scale
- Repeatable business workflows for approvals, restrictions, and access requests
- End-to-end auditability of all decisions and automated actions
Watch the full Reco + Torq AMP’d Session to see it in action.