Contextual Threat Intel Enrichment
Transform raw threat data with actionable security intelligence using AI-powered context and automated correlation.
Torq HyperSOC automatically ingests, correlates, and enriches threat intelligence from disparate sources in real time, providing comprehensive context for faster, more accurate threat detection and response across your entire security stack.
Measurable SOC Performance Improvements
10X
faster IOC analysis
35%
lower breach probability
50%
faster MTTD
Disconnect Between Threat Data and Threat Intelligence Creates Security Blind Spots
Security teams are drowning in disconnected threat indicators from multiple sources. Without proper context and correlation, IOCs remain isolated data points that slow investigations, increase false positives, and allow real threats to slip through undetected.
Fragmented Intelligence Sources
Threat indicators arrive from OSINT feeds, commercial intelligence providers, internal security tools, and incident investigations, but remain siloed across disparate systems without unified context.
Manual Correlation Bottlenecks
Analysts spend hours manually cross-referencing IOCs across multiple platforms, delaying critical threat hunting and incident response activities while attackers maintain persistence.
Contextless Alert Overload
Security tools generate thousands of alerts with minimal context, creating noise that obscures genuine threats and leads to alert fatigue among overstretched SOC analysts.
How Torq Transforms Threat Intelligence
Torq HyperSOC automatically ingests, correlates, and enriches threat intelligence from disparate sources in real time, providing comprehensive context for faster, more accurate threat detection and response.
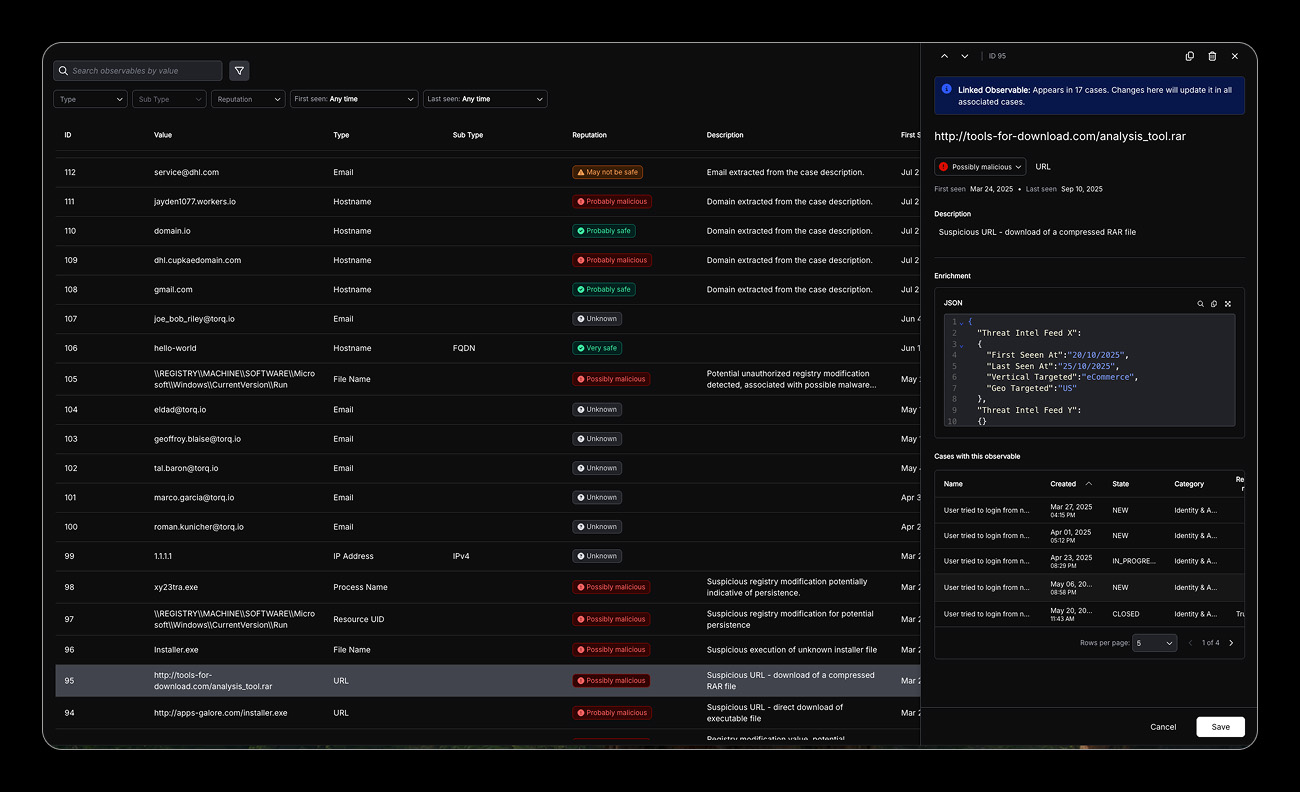
Automated Multi-Source Correlation
Flexible ingestion pipelines allowing advanced deterministic or AI-driven normalization, correlation and analysis, including live updates to existing in-flight security cases related to the threat intelligence data.
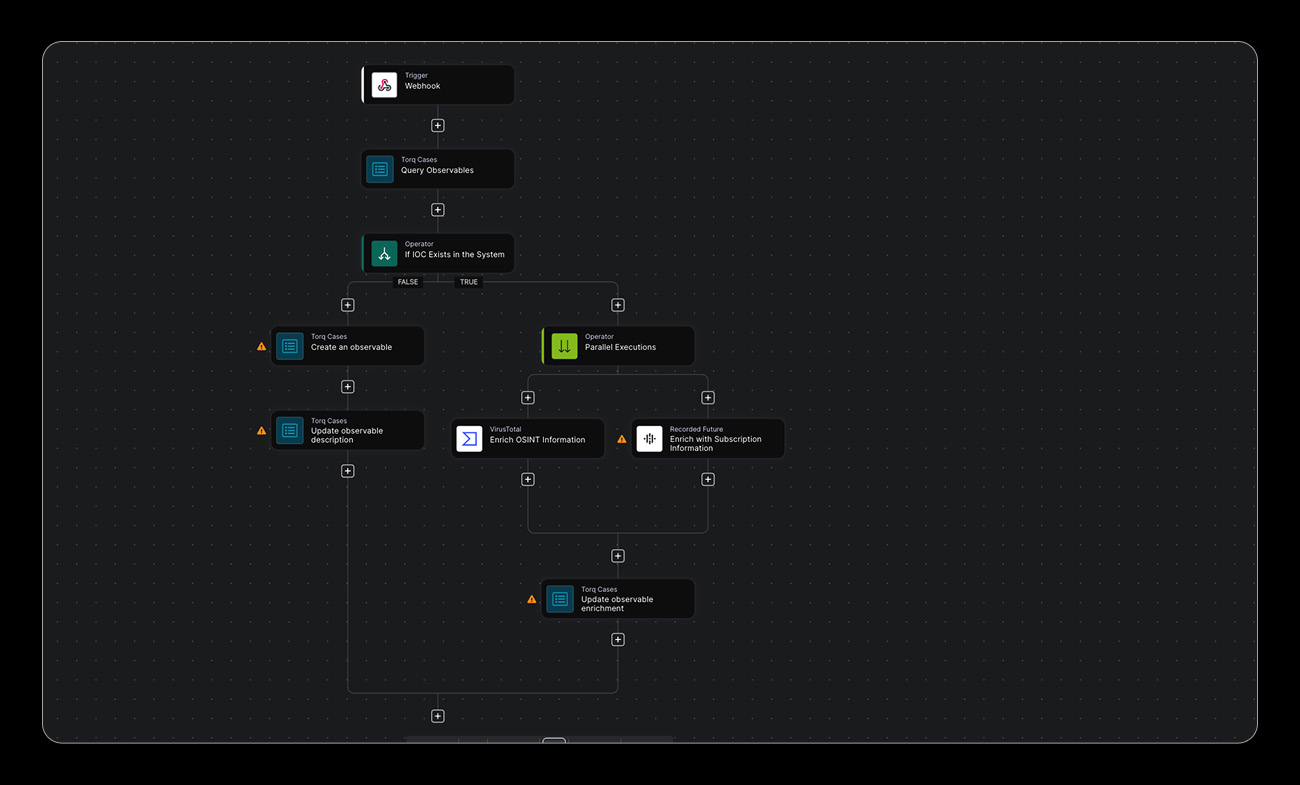
Key capabilities:
- Advanced pipelines for IOC processing
- Scalable cross-platform integration, normalization, correlation of data
- AI for data extraction, normalization, and inference
- High-performance data transformation engine
- Historical threat mapping, scalable observability and reporting
- Multi-feed integration and orchestration
AI-Powered Context Analysis
Leverage available context information correlated with the threat data to provide concise actionable view of the event, suggested investigation and remediation actions to be taken to complete handling of the event.
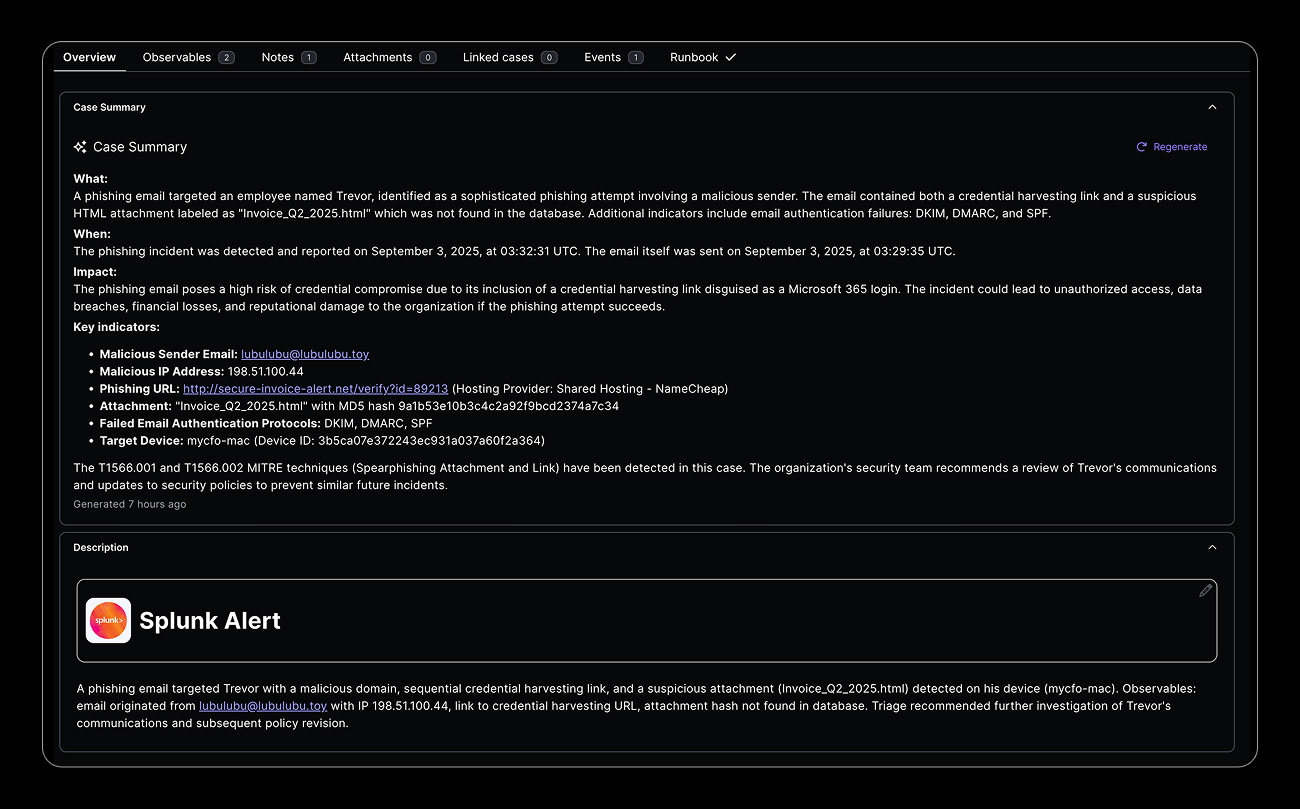
Key capabilities:
- AI-driven threat analysis according to the 4Ws Framework
- Highlighting of key IOCs and main event TTPs
- Initial impact analysis
- Suggested investigation and containment actions
Dynamic Threat Prioritization
Risk-based scoring system that intelligently prioritizes threats based on organizational context, asset criticality, and potential business impact to focus analyst attention on the most critical security events.
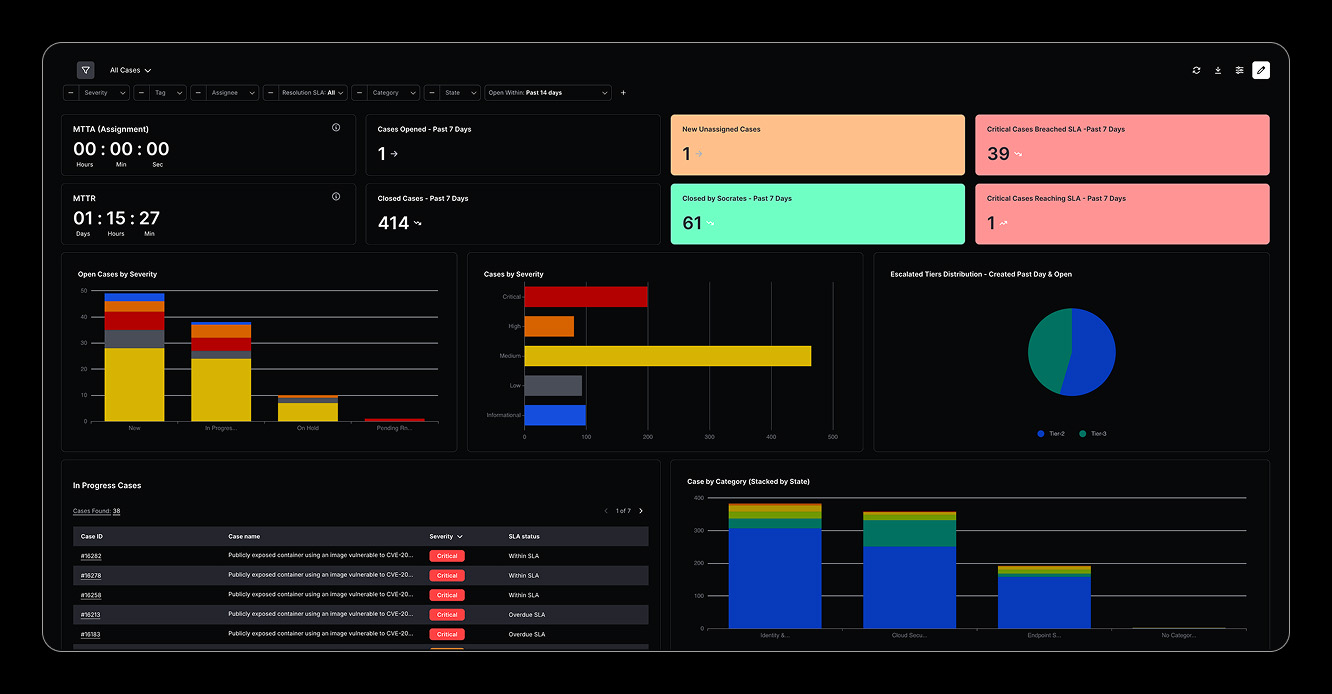
Key capabilities:
- Risk-based scoring
- Asset criticality mapping
- Business impact analysis
- Automated alert ranking
- Context-aware filtering
- Dynamic re-prioritization
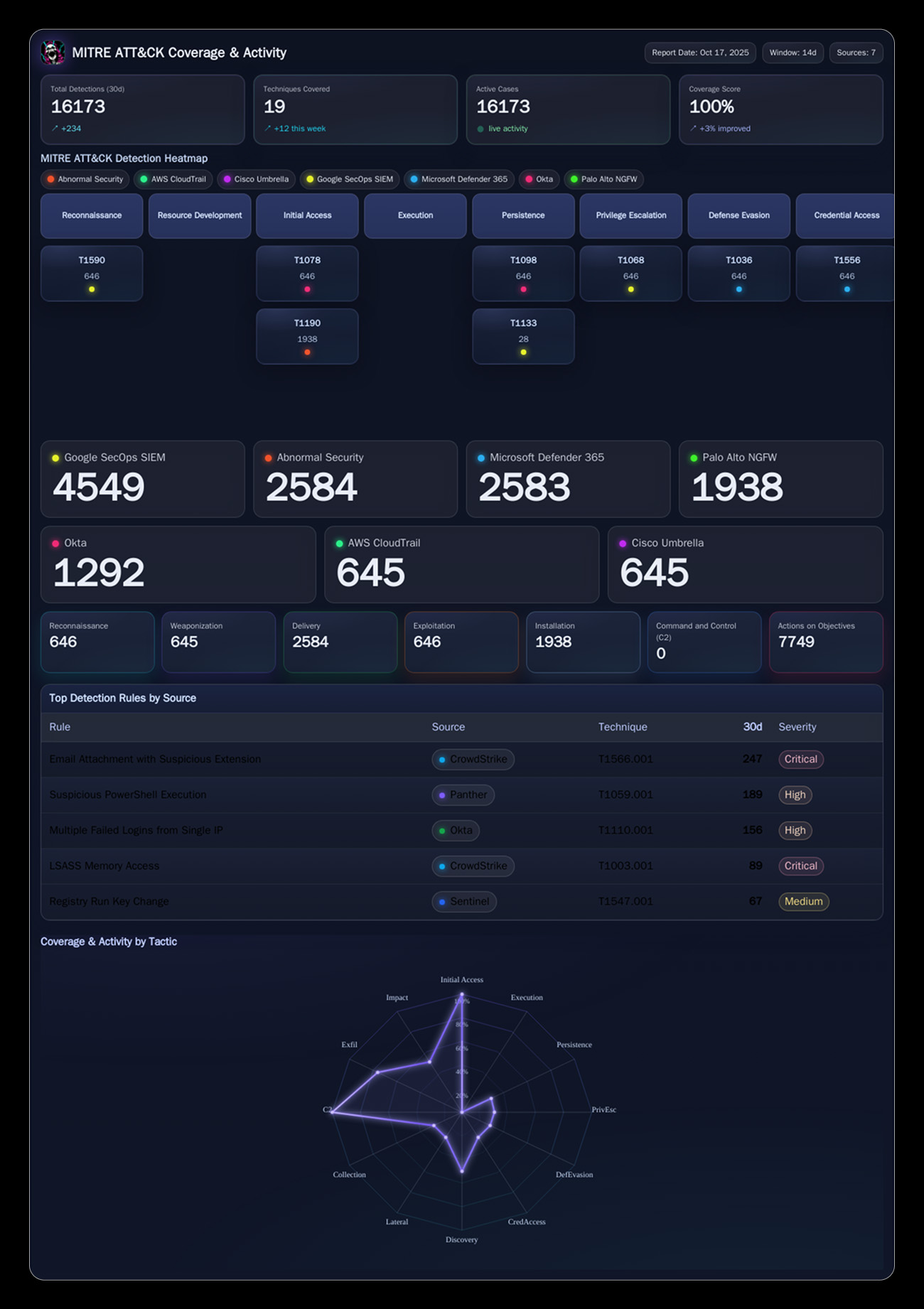
AI-Native Threat Intelligence Architecture
Built on a foundation of advanced AI and Hyperautomation, Torq’s threat intelligence platform seamlessly integrates with your existing security infrastructure to deliver enterprise-grade enrichment capabilities.
Real-Time IOC Processing
Ingests and processes millions of indicators per day from threat feeds, OSINT sources, and internal security tools using scalable cloud-native architecture.
Advanced Behavioral Analytics
Applies correlation, aggregation, AI-driven context extraction and additional techniques to provide actionable follow-up to Threat Intelligence data.
Cross-Platform Integration
Native integrations with SIEMs, EDR/XDR platforms, threat intelligence feeds, and security orchestration tools through pre-built connectors and APIs.
Contextual Data Fusion
Combines threat intelligence with asset inventory, vulnerability data, and business context to provide risk-based threat prioritization and impact assessment.
Automated Workflow Orchestration
Triggers automated response workflows based on enriched threat intelligence, enabling immediate containment and remediation actions without manual intervention.
Threat Attribution & Tracking
Allows advanced insights and tracking by a graph data analytics of the Threat Intelligence and Cases data covering current and historical threats.
Real-World Threat Intelligence Scenarios
See how Torq’s threat intelligence enrichment transforms complex security scenarios into automated, actionable responses across diverse attack vectors and organizational contexts.
Advanced Persistent Threat Detection
APT Intelligence
When a suspicious IP appears in network logs, Torq automatically enriches it with geolocation data, reputation scores, associated domains, and known APT campaign attribution — instantly revealing if it’s part of a targeted attack against your industry sector.
Malware Family Analysis
Malware Detection
Hash indicators from endpoint alerts are automatically analyzed against multiple threat intelligence feeds, providing immediate context about malware families, attack campaigns, and recommended containment strategies specific to the identified threat.
Phishing Campaign Correlation
Email Security
Email security alerts are enriched with sender reputation, domain analysis, and correlation with ongoing phishing campaigns — enabling automatic blocking of related infrastructure and proactive user notification.
Supply Chain Compromise Detection
Supply Chain Risk
Suspicious activity from trusted third-party domains is automatically correlated with supply chain attack patterns and vendor risk profiles, triggering immediate assessment of potential compromise vectors.
Zero-Day Exploitation Monitoring
Zero-Day Defense
Behavioral anomalies are correlated with emerging vulnerability intelligence and exploit kit tracking to identify potential zero-day attacks before signature-based detection catches up.
Insider Threat Intelligence
Insider Risk
User behavior analytics are enhanced with threat intelligence about compromised credentials, leaked databases, and dark web monitoring to identify potential insider threats or compromised accounts.
Enterprise Benefits of Automated Threat Intelligence
Transform your security operations with comprehensive threat intelligence that scales with your organization’s needs while reducing analyst workload and improving threat detection accuracy.
Enhanced Threat Detection Precision
Reduce noise through contextual analysis and multi-source correlation, allowing analysts to focus on genuine threats rather than investigating benign indicators.
Accelerated Incident Response
Automatically trigger response workflows based on enriched threat intelligence, enabling immediate containment actions and reducing mean time to response (MTTR) by up to 75%.
Proactive Threat Hunting
Enable proactive threat hunting with AI-powered pattern recognition that identifies emerging threats and attack campaigns before they impact your organization.
Strategic Security Planning
Leverage threat actor attribution and campaign tracking to inform strategic security investments and defensive priorities based on relevant threat landscape analysis.
Operational Efficiency
Eliminate manual threat intelligence tasks and free analysts to focus on high-value security activities, improving job satisfaction and reducing analyst burnout.
Compliance & Reporting
Automatically generate comprehensive threat intelligence reports and maintain audit trails for regulatory compliance and executive briefings.
Security Stack Integration
HyperSOC seamlessly integrates with your existing security infrastructure through our comprehensive library of connectors and AI-generated integrations.
SIEM & Log Management
Splunk, Elastic, QRadar, Sentinel, Sumo Logic, and custom log sources
Endpoint Detection & Response
CrowdStrike, SentinelOne, Microsoft Defender, Carbon Black, Cortex XDR
Network Security
Palo Alto, Fortinet, Cisco, Check Point, Zscaler, Cloudflare
Threat Intelligence
VirusTotal, ThreatConnect, Anomali, Recorded Future, MISP

