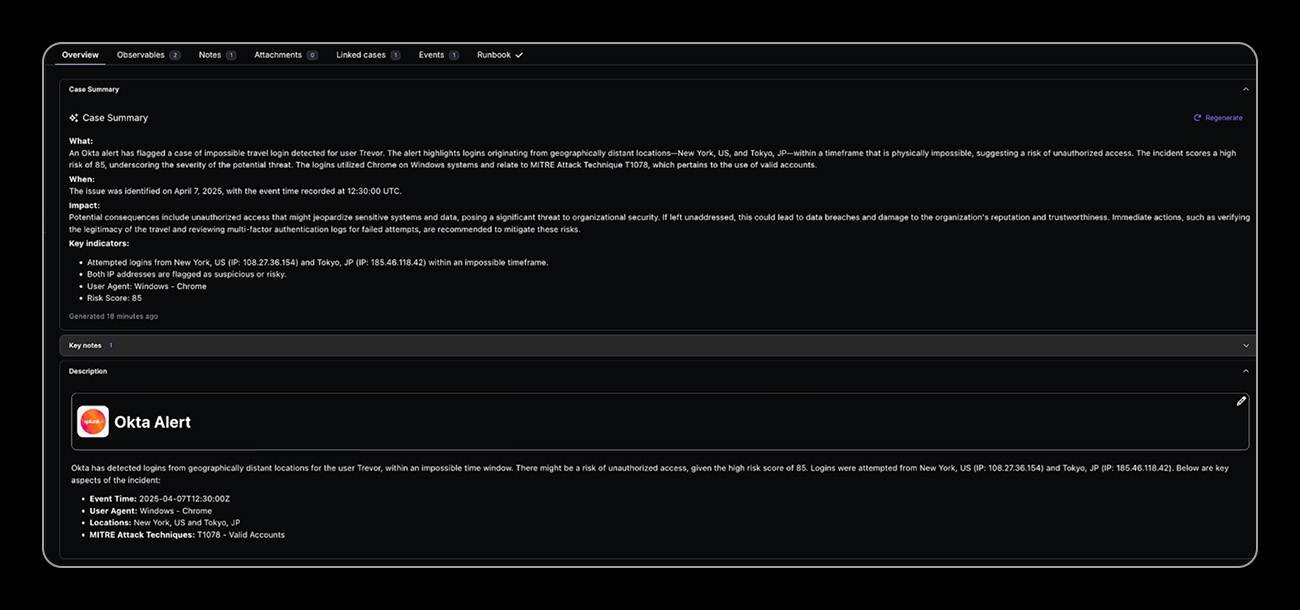
Cloud Access – Identity Threat Detection and Response (ITDR)
Detect, analyze, and respond to impossible travel scenarios with contextual geolocation analysis and automated response workflows to guard access to your cloud environments
Torq HyperSOC™ identifies physically impossible authentication patterns by analyzing login and access locations, timestamps, and travel velocity. When a user account accesses cloud environments from geographically distant locations within an impossible timeframe, Torq instantly correlates threat intelligence, assesses risk, and orchestrates immediate containment actions across identity systems, MFA platforms, and endpoint security tools.
Measurable Impact on Account Takeover Prevention
3x
faster MFA re-enrollment for high-risk users vs. manual processes
<1 min
average detection to response time
90%
decrease in account takeover dwell time
Cross-Cloud Identity Threats Present Critical Detection Challenges
Traditional authentication systems fail to detect sophisticated account takeover attacks that exploit geographically dispersed access patterns. Manual correlation of login locations and timestamps leaves organizations vulnerable to credential theft, where attackers operate from distant locations while legitimate users remain active. The delay in detection allows threat actors to exfiltrate data, establish persistence, and escalate privileges before security teams can respond. Non-uniform login and access logs across various cloud platforms add to the complexity, allowing malicious actors to hide suspicious activities.
Delayed Geolocation Correlation
Manual analysis of authentication logs across multiple systems creates detection delays, allowing compromised accounts to maintain access for hours or days while security teams piece together geographic anomalies across time zones and authentication platforms.
Geographic-Based False Positives
Security analysts must manually correlate access logs across multiple systems, investigate suspicious activities, and coordinate response actions, which can create critical delays during active attacks.
Insufficient Contextual Analysis
Traditional impossible travel detection lacks context on user behavior patterns, device fingerprints, and authentication methods, leading to missed attacks when threat actors use sophisticated evasion techniques.
How Torq Automates Identity Threat Detection and Response
Torq HyperSOC™ integrates with identity management systems, SaaS applications, IaaS platforms, endpoint protection platforms, and network security tools to provide real-time detection and automated response to unauthorized access attempts through intelligent workflow orchestration.
Continuous Access Analytics
Contextual analysis that continuously monitors user authentication patterns, privilege usage, and access anomalies across Active Directory, cloud identity providers, and privileged access management systems to detect unauthorized access attempts in real-time.
Key capabilities:
- Close to real-time authentication and access activity monitoring
- Lateral movement tracking, cross-cloud activities correlation
- Service account anomaly investigation
- Privilege escalation investigation and response
- Credential abuse identification and containment
Context-Aware Response Intelligence
Enrichment engine that correlates unauthorized access attempts with threat intelligence, user behavior baselines, and asset criticality to determine appropriate response severity and automatically execute proportional containment measures based on risk assessment.
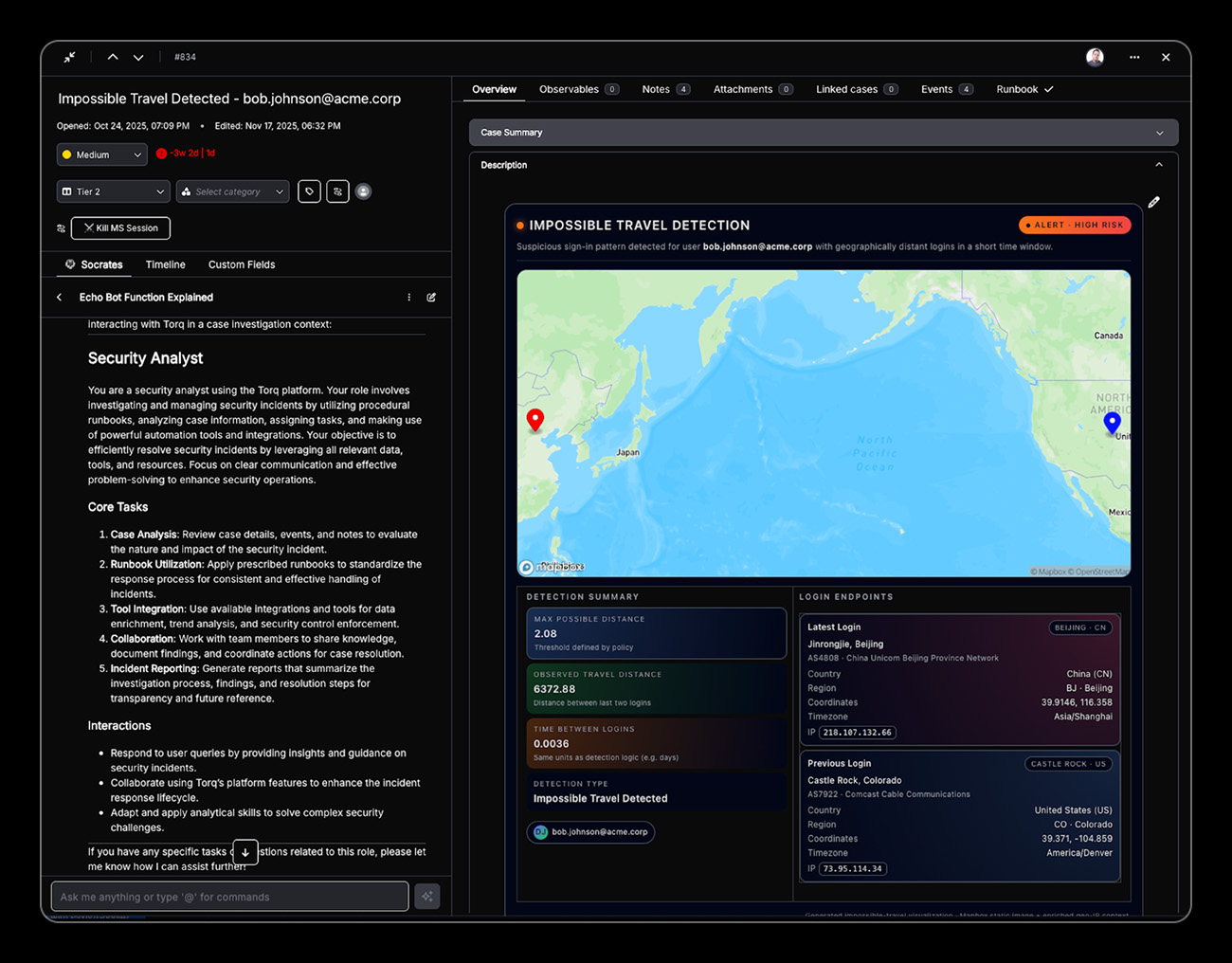
Key capabilities:
- Near real-time IP geolocation mapping
- Time zone correlation analysis
- VPN and proxy usage detection orchestration
Automated Response & Remediation
Intelligent response orchestration that automatically executes graduated containment actions based on risk scores, user roles, and threat context. Coordinates account suspension, MFA challenges, session termination, and security team notifications within seconds of detecting impossible travel patterns.
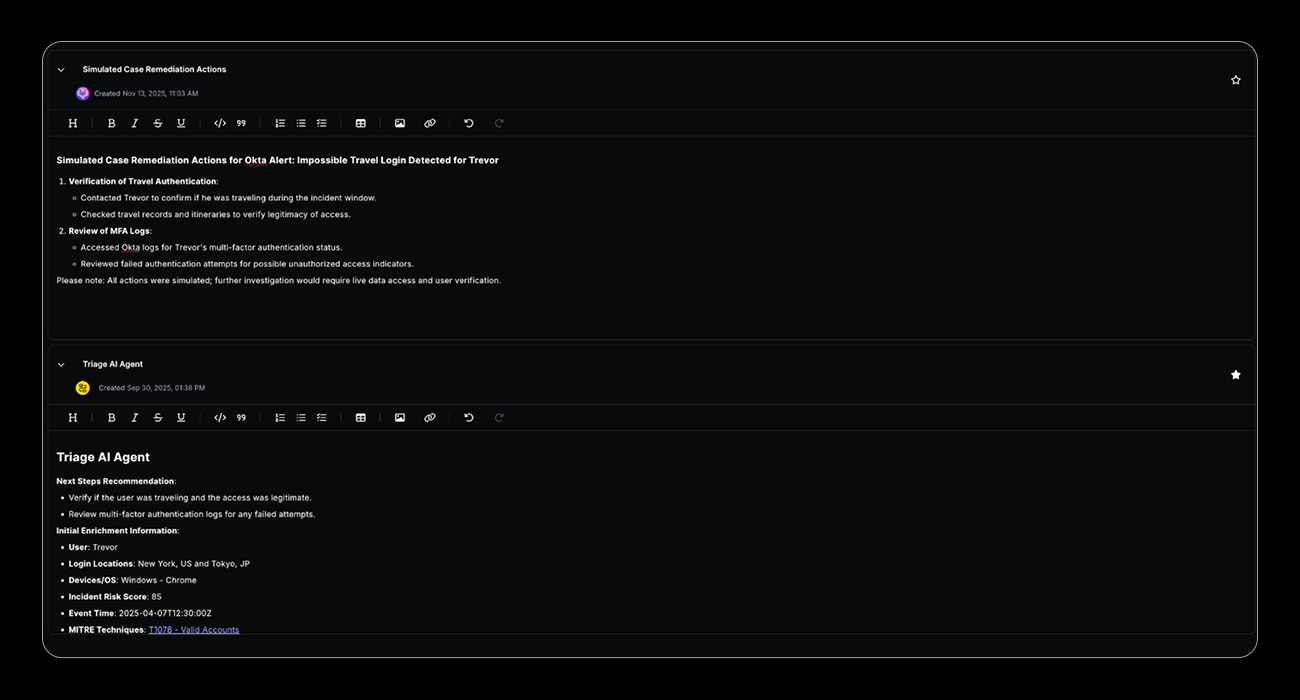
Key capabilities:
- Automated account suspension
- Step-up MFA enforcement orchestration
- Session termination orchestration
- Real-time user notification
- Risk-based response tiering
- Incident ticket creation and incident lifecycle orchestration
Advanced Automated Investigation
Built on an industry-leading security Hyperautomation foundation, Torq’s access control automation integrates deeply with identity providers, privilege management systems, cloud infrastructure providers, and other tools to deliver comprehensive protection against unauthorized access or account takeover.
Multi-Factor Context Analysis
Comprehensive authentication context evaluation, including device fingerprints, browser characteristics, connection patterns, and access behavior to distinguish legitimate travel from account compromise scenarios.
Threat Intelligence Integration
Real-time correlation with global threat intelligence feeds to identify authentication attempts from known malicious IP addresses, compromised infrastructure, and threat actor command-and-control networks.
Identity Provider Automation
Seamless integration with Azure AD, Okta, Google Workspace, Ping Identity, and more for automated account actions, policy enforcement, and authentication flow manipulation in response to impossible travel detections.
Multi-Factor Authentication
Dynamic risk calculations that weigh travel velocity, authentication patterns, threat intelligence, user role, and accessed resources to generate real-time risk scores that drive automated response decisions.
Forensic Data Collection
Automatic preservation of authentication logs, geolocation data, device fingerprints, and session details for investigation teams. Creates comprehensive audit trails linking geographic anomalies to specific access attempts.
Business Continuity Assurance
Graduated response framework that balances security protection with user productivity through risk-based access decisions, temporary access alternatives for legitimate travel scenarios, and automated restoration workflows that minimize disruption while maintaining an optimal security posture.
Intelligent Event Correlation
See how Torq analyzes security events across cloud environments to identify coordinated attack campaigns, lateral movement, and anomaly detection.
Account Takeover
When a DevOps account authenticates from San Francisco at 9 AM PST, then from London 3 hours later, Torq immediately suspends the account, triggers MFA verification, terminates all active sessions, and alerts the security team, completing the entire response in under 90 seconds.
Simultaneous Multi-Location Access
A user account shows authentication attempts from Tokyo and London within minutes. Torq correlates the events, validates the impossible travel velocity, forces account lockout(s), and initiates immediate password reset(s) while preserving complete forensic trails.
Evasion Techniques Identification
An attacker uses VPN infrastructure to mask location and evade simple geo-blocking. Torq uses contextual threat intelligence data to detect anomalous authentication patterns, behavioral deviations, and VPN characteristics, triggering account verification workflows and blocking unauthorized access.
Dwell Time Reduction
Following a credential leak, multiple accounts exhibit unusual travel patterns as attackers test stolen passwords from various locations. Torq identifies the pattern, implements bulk account protection measures, and triggers company-wide password reset campaigns.
Insider Threat Mitigation
Anomalous data access patterns by privileged users trigger enhanced monitoring, access restrictions, and automatic data loss prevention measures while preserving evidence for HR and legal review.
Service Account Compromise Detection
Unusual service account activity patterns trigger immediate credential rotation, service restart orchestration, and dependency mapping to prevent service disruption while eliminating attacker persistence.
Enterprise Benefits of ITDR Automation
Transform your identity security posture with intelligent automation that prevents privilege escalation, contains unauthorized access, and reduces the window of opportunity for attackers to establish persistence in your environment.
Rapid Account Takeover Detection
Detect compromised accounts within seconds of the first impossible travel event, dramatically reducing the time window for data exfiltration, lateral movement, and privilege escalation from days to minutes.
Automated User Experience
Seamlessly protect users without disrupting legitimate activities through intelligent step-up authentication, targeted MFA challenges, and risk-based access controls that adapt to user behavior and context.
Global Coverage at Scale
Monitor authentication attempts and access logs across global infrastructure, scaling the processing of login events at machine-speed, regardless of organization size or geographic distribution.
Complete Audit Trail
Holistic forensic data collection, including geolocation history, device fingerprints, authentication patterns, and automated response actions, provides investigation teams with complete evidence chains for incident analysis and investigation.
Integrations Across Tech Stack for ITDR Automation
Torq HyperSOC™ seamlessly integrates with identity providers, SIEM platforms, cloud infrastructure platforms, and threat intelligence feeds to provide comprehensive identity threat detection and response across your entire authentication infrastructure.
Identity Providers
Active Directory, Azure AD, Okta, Ping Identity, Auth0, AWS IAM, Google Workspace
Multi-Factor Authentication
Duo Security, RSA SecurID, Yubico, Microsoft Authenticator, Google Authenticator, Authy
Cloud Infrastructure
Amazon Web Services, Microsoft Azure, Google Cloud Platform (GCP)
SIEM & Log Management
Splunk, Elastic Security, Microsoft Azure Sentinel, Google SecOps, Sumo Logic, IBM QRadar
Threat Intelligence
VirusTotal, ThreatConnect, Recorded Future, AlienVault OTX, Anomali, MISP

