Consistent Multi-Cloud Security Operations
Unified alert correlation, deduplication, and automated triage across AWS, Azure, GCP, hybrid cloud environments, and more.
Torq HyperSOC™ automatically ingests, normalizes, and correlates security alerts from disparate cloud-native security tools, providing centralized visibility and intelligent triage across your entire multi-cloud infrastructure with automated response workflows.
Measurable Multi-Cloud Security Improvements
75%
faster alert processing
90%
duplicate alert reduction
60%
faster cross-cloud MTTR
Multi-Cloud Security Alert Chaos
Organizations operating across multiple cloud platforms face an overwhelming deluge of disparate security alerts from native cloud security services, creating operational blind spots, alert fatigue, and delayed incident response across distributed infrastructure.
Alert Fragmentation Across Clouds
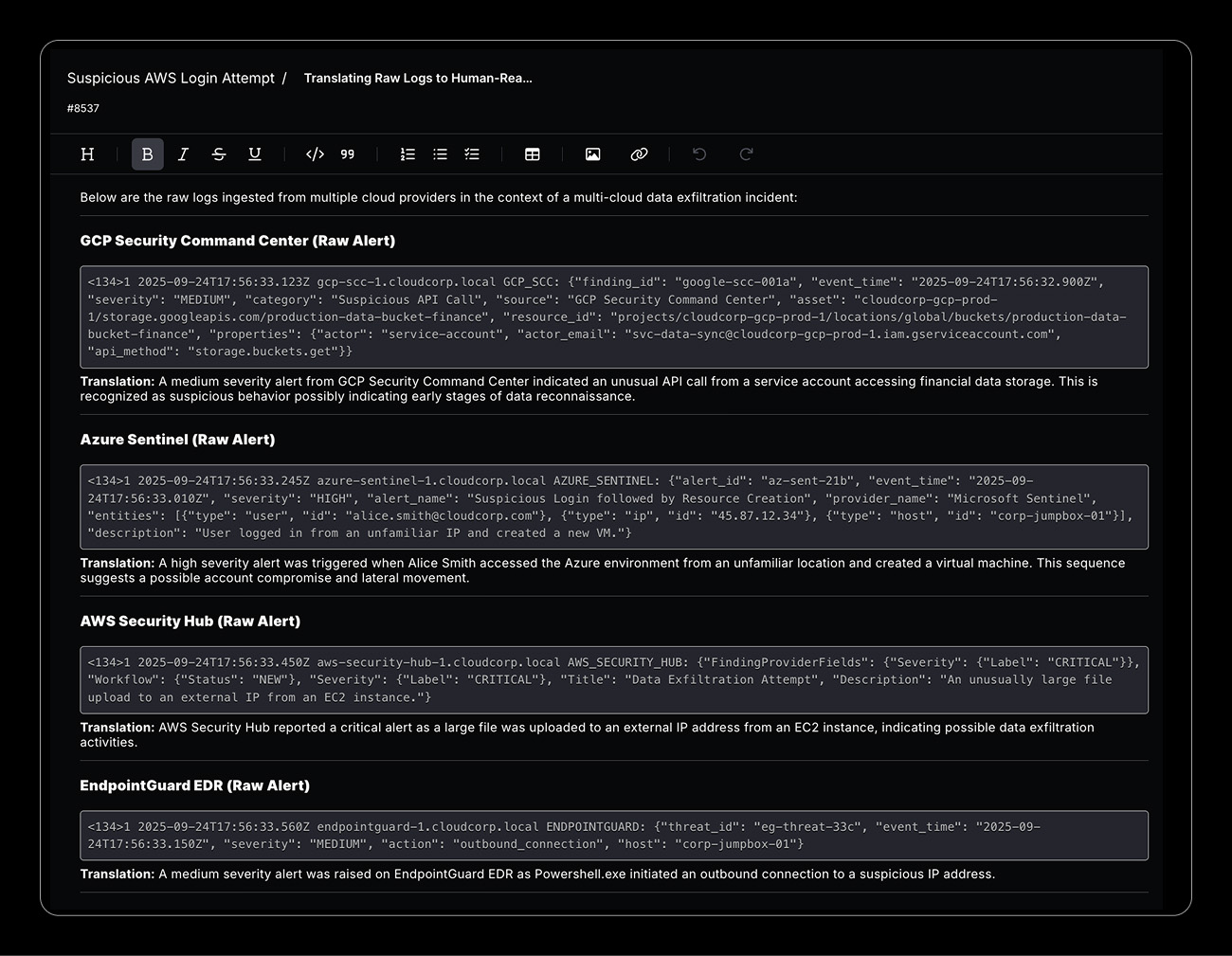
Security alerts scatter across AWS Security Hub, Azure Sentinel, Google Cloud Security Command Center, and third-party tools — each with unique formats, severity scales, and contextual data structures.
Cross-Cloud Correlation Gaps
Multi-stage attacks spanning AWS EC2, Azure VMs, and GCP instances remain invisible due to lack of unified correlation — enabling threat actors to exploit cross-cloud security blind spots.
Manual Triage Bottlenecks
SOC analysts manually pivot between cloud consoles, correlate alerts across platforms, and struggle with inconsistent severity scoring — leading to delayed response times and missed critical threats.
How Torq Unifies Multi-Cloud Alert Management
Torq HyperSOC™ provides comprehensive alert correlation, normalization, and automated triage across all major cloud platforms through deep integrations with native security services and third-party cloud security tools.
Cross-Cloud Alert Ingestion
Ingest alerts from AWS Security Hub, Azure Sentinel, GCP Security Command Center, and 200+ cloud security tools, normalizing formats and correlating related incidents across cloud boundaries in real-time.
Key capabilities:
- Real-time alert ingestion
- Cross-platform correlation
- Timeline reconstruction
- Multi-cloud normalization
- Duplicate elimination
- Impact assessment
Intelligent Automated Triage
AI-driven triage system that analyzes alert context, cloud asset criticality, and threat intelligence to automatically prioritize incidents, escalate critical threats, and route alerts to appropriate response teams based on cloud environment and severity.
Key capabilities:
- Context-aware prioritization
- Automated escalation
- SLA enforcement
- Asset criticality mapping
- Team routing
- Dynamic re-scoring
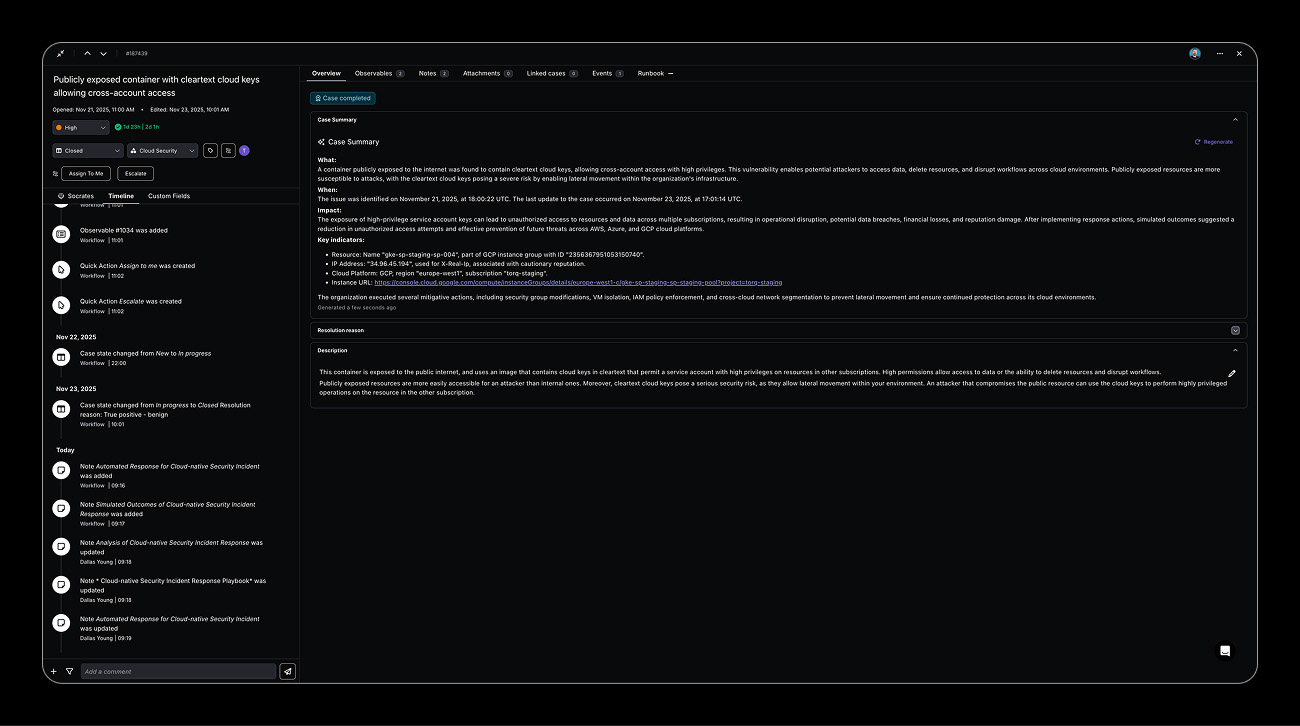
Automated Response
Cloud-native response automation that triggers coordinated containment actions across AWS, Azure, and GCP simultaneously, including security group modifications, VM isolation, IAM policy enforcement, and cross-cloud network segmentation.
Key capabilities:
- Cross-cloud containment
- Policy enforcement
- Evidence collection
- Automated isolation
- Network segmentation
- Compliance reporting
Cloud Native Event Processing Pipeline Architecture
Built on cloud-native principles with strong observability and SLA enforcement, Torq’s event processing and Hyperautomation architecture allows executing high-performance automated processes at scale.
Native Cloud Security Integration
Direct API integration with AWS Security Hub, Azure Sentinel/Defender, GCP Security Command Center, and cloud-native security services for real-time alert streaming and bi-directional communication.
Alert Normalization Engine
Advanced data transformation engine that converts diverse alert formats (AWS Finding Format, Azure Alert Schema, GCP SCC Finding) into unified data models for consistent processing and correlation.
Cross-Cloud Correlation Logic
The platform allows identifying related incidents across cloud boundaries using entity relationships, timing analysis, and attack TTPs to reconstruct multi-cloud attack campaigns.
Cloud Observables Management
Maintains historical inventory of cloud assets across AWS, Azure, and GCP that were involved in processed security alerts with ownership and risk level metadata, assisting prioritization and investigation of events.
Multi-Cloud Response Automation
Orchestrates simultaneous response actions across cloud platforms using native APIs — from AWS Lambda and Azure Functions to GCP Cloud Functions — for coordinated threat containment.
Hybrid Environment Integration
Extends correlation capabilities to on-premises and edge environments through secure connectors, enabling unified alert management across hybrid and multi-cloud architectures.
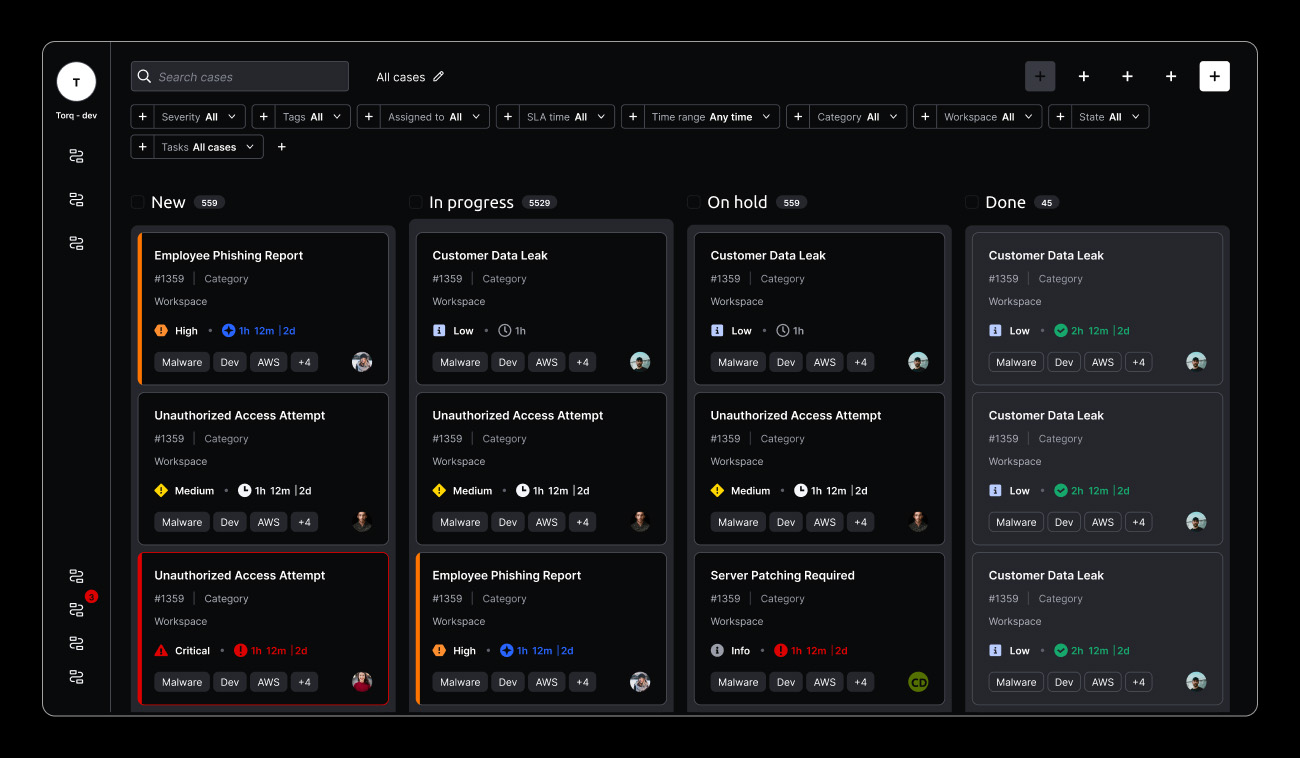
Multi-Cloud Alert Management Scenarios
See how Torq’s multi-cloud alert management transforms complex cross-cloud security scenarios into automated, coordinated responses across diverse cloud environments and attack vectors.
Contextual Cloud Enrichment
ENRICHMENT
Automatically enriches security alerts with relevant threat intelligence, asset context, user, and historical incident data to provide complete situational awareness for faster, more informed response decisions.
Multi-Cloud Data Exfiltration
Data Protection
Suspicious data transfer patterns across AWS S3, Azure Blob Storage, and GCP Cloud Storage are automatically correlated and analyzed for coordinated data exfiltration attempts with immediate access controls enforcement.
Cross-Cloud Insider Threat
Insider Risk
Privileged user accessing sensitive resources across multiple cloud platforms triggers correlation analysis of access patterns, data movements, and risk indicators for potential insider threat assessment.
Third-Party Integration Compromise
Supply Chain
Suspicious activity from SaaS integrations or cloud service providers is correlated across cloud environments to identify potential supply chain compromises with automated isolation of affected services.
Infrastructure Attack Patterns
Infrastructure Security
Coordinated attacks targeting cloud infrastructure components across multiple platforms are identified through correlation of resource access patterns, configuration changes, and security control bypasses.
Enterprise Benefits of Unified Multi-Cloud Alert Management
Transform your multi-cloud security operations with comprehensive alert management that scales with your cloud adoption while reducing complexity and improving threat detection across distributed infrastructure.
Unified Security Operations
Eliminate the need to monitor multiple cloud security consoles by providing a single pane of glass for alert management across AWS, Azure, GCP, and hybrid environments.
Cross-Cloud Threat Visibility
Detect sophisticated attacks that span multiple cloud platforms by correlating related incidents and reconstructing attack timelines across cloud boundaries.
Reduced Alert Fatigue
Eliminate duplicate alerts and false positives through intelligent deduplication and correlation, allowing analysts to focus on genuine security threats.
Accelerated Incident Response
Trigger coordinated containment actions across multiple cloud platforms simultaneously, reducing multi-cloud incident response times by up to 60%.
Compliance Automation
Automatically generate compliance reports and maintain audit trails across cloud platforms to meet regulatory requirements and industry standards.
Scalable Cloud Operations
Scale security operations seamlessly as cloud adoption grows, with automatic discovery and integration of new cloud services and security tools.
Cloud Platform Integration Coverage
Torq provides deep, native integration with major cloud platforms and their security services, ensuring comprehensive alert coverage across your entire multi-cloud infrastructure.
Amazon Web Services (AWS)
Security Hub, GuardDuty, Inspector, Macie, Config, CloudTrail, Access Analyzer, Well-Architected Tool, Trusted Advisor
Microsoft Azure
Azure Sentinel, Defender for Cloud, Defender for Identity, Defender for Endpoint, Azure Monitor, Policy, Activity Log
Google Cloud Platform (GCP)
Security Command Center, Chronicle, Asset Inventory, Cloud Logging, Cloud Monitoring, Policy Intelligence, Access Transparency
Hybrid & Multi-Cloud
VMware Cloud, Oracle Cloud, IBM Cloud, Alibaba Cloud, and on-premises integrations through secure connectors
Cloud-Native Security Tool Integration
Comprehensive integration with cloud-native and third-party security tools deployed across multi-cloud environments for complete alert coverage and response orchestration.
Cloud-Native Application Protection Platforms
Wiz, Orca Security, Palo Alto Networks Prisma Cloud
Cloud Workload Protection
Sysdig, Aqua Security, AWS GuardDuty, Microsoft Defender for Containers

