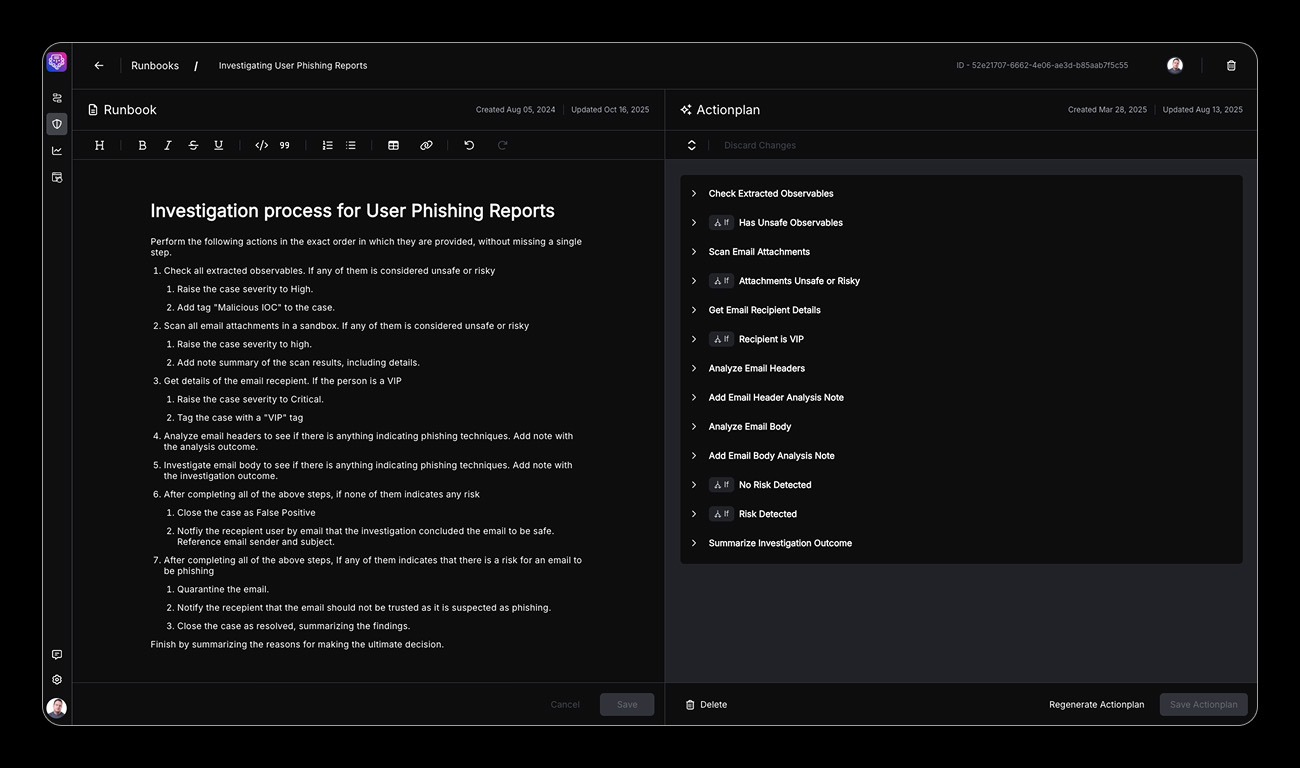
SOC Incident Response
Agentic AI and Hyperautomation platform for autonomous threat detection and response
Transform your Security Operations Center with AI-driven Torq Hyperautomation™ that accelerates threat detection, investigation, and response while reducing analyst workload by 90%. Torq HyperSOC™ enables autonomous SOC operations through intelligent agent coordination and machine-speed response capabilities.
New: Enhanced multi-agent investigation with 50% faster mean time to detection (MTTD). Learn more
Measurable SOC Performance Improvements
50%
faster mean time to detection (MTTD)
90%
of responses
automated
35%
reduction in
breach probability
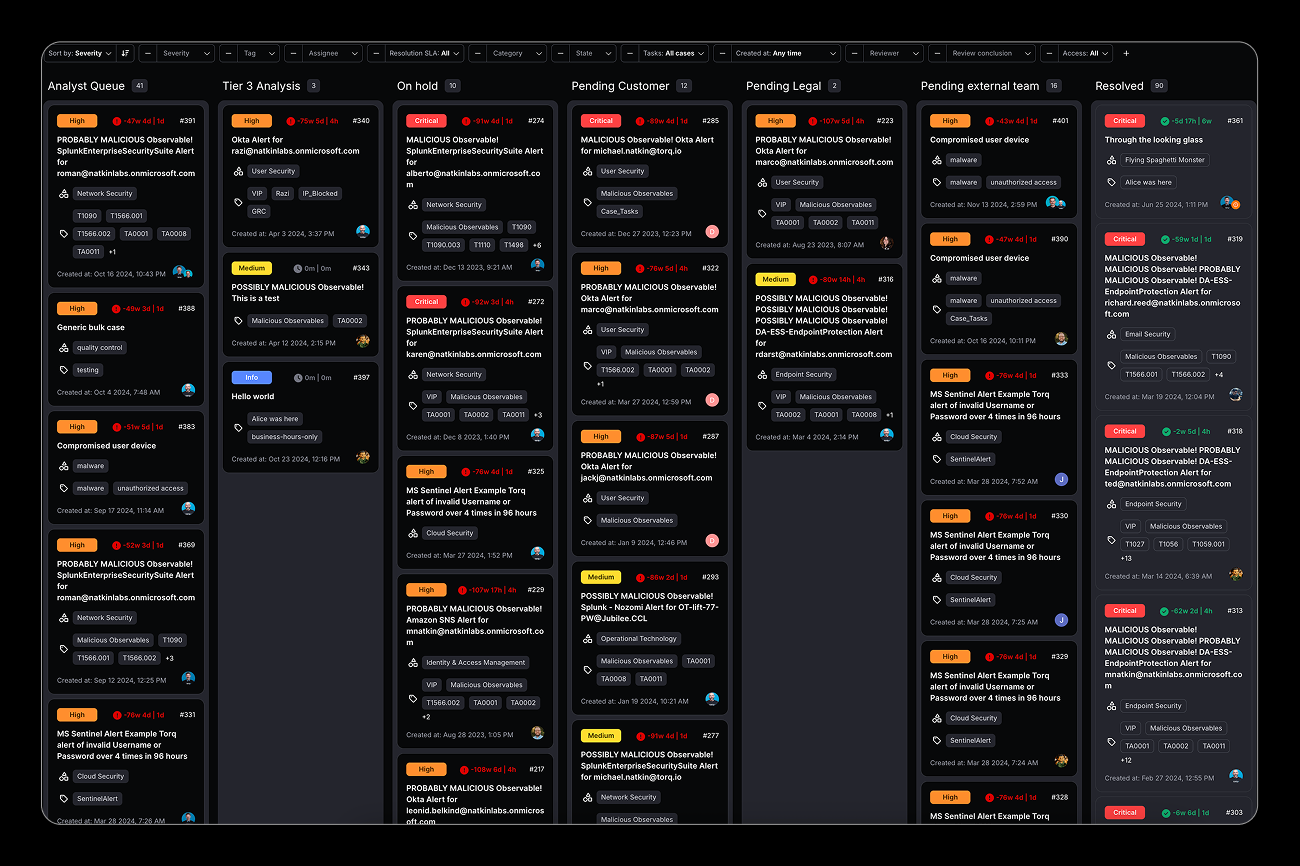
Modern SOCs Face Overwhelming Incident Response Challenges
Security operations centers are drowning in alert fatigue, manual investigations, and fragmented toolsets. Traditional SOAR platforms have failed to deliver the automation promised, leaving analysts overwhelmed and critical threats undetected.
Alert Overload and False Positives:
SOCs receive thousands of alerts daily with 90% being false positives. Analysts spend 75% of their time on manual triage and investigation rather than actual threat hunting and strategic security improvements.
Manual Investigation Bottlenecks
Critical incident response tasks like threat correlation, asset enrichment, and impact assessment require manual effort across multiple tools, creating delays that allow attackers to maintain persistence and escalate privileges.
Fragmented Security Tool Ecosystem
Security teams manage 20+ disparate tools with limited integration, forcing analysts to context-switch and manually correlate data, resulting in incomplete investigations and missed attack indicators.
How Torq HyperSOC™ Revolutionizes Incident Response
Torq HyperSOC™ fuses AI-powered SOC intelligence with hyperautomation to orchestrate your entire security stack, delivering autonomous threat detection, investigation, and response at unprecedented speed and scale.
AI-Powered Alert Triage
Multi-layered AI agents handle alert triage across your security stack. Hyperagents embedded in workflows process and enrich alerts in context, while a purpose-built AI SOC triage solution analyzes incoming signals from SIEM, EDR, and cloud security tools distinguishing genuine threats from noise and routing critical incidents to the right response workflows.
Key capabilities:
- Natural language processing
- ML-based threat scoring
- Contextual alert enrichment
- Automated false positive filtering
- Dynamic priority assignment
- Multi-source correlation
Autonomous Investigation
The hyperautomation engine conducts comprehensive threat investigations by automatically gathering evidence from endpoints, network logs, threat intelligence feeds, and vulnerability databases to build complete attack timelines and impact assessments.
Key capabilities:
- Automated evidence collection
- Timeline reconstruction
- Asset impact analysis
- IOC expansion and hunting
- Threat attribution
- Forensic data preservation
Autonomous IR
AI-driven response engine executes contextually appropriate containment and remediation actions across your security stack.
Key capabilities:
- Endpoint isolation & quarantine
- Network segmentation
- User account management
- Automated threat blocking
- Evidence preservation
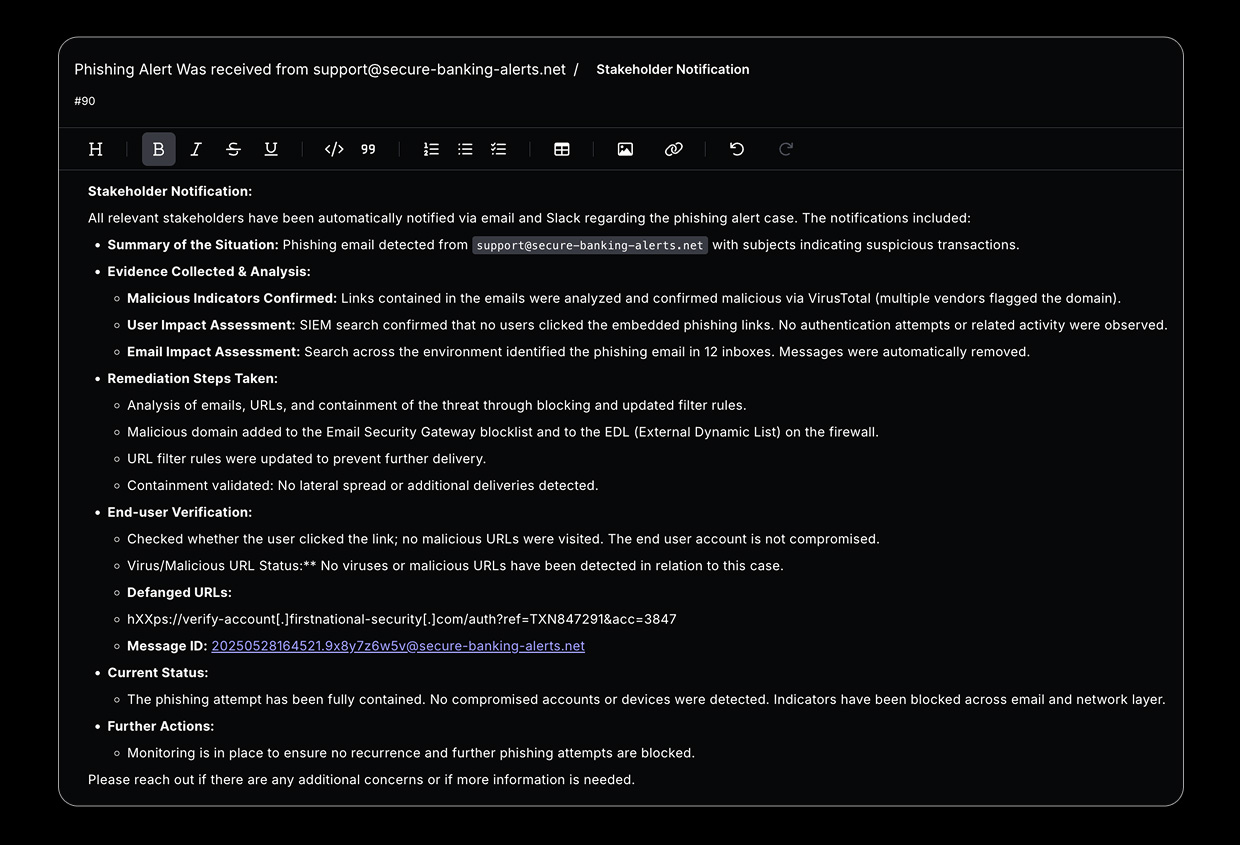
- Stakeholder notification
AI-Native SOC Automation Architecture
Built on cloud-native, zero trust principles, Torq HyperSOC delivers enterprise-grade automation capabilities that seamlessly integrate with your existing security infrastructure to create a truly autonomous SOC.
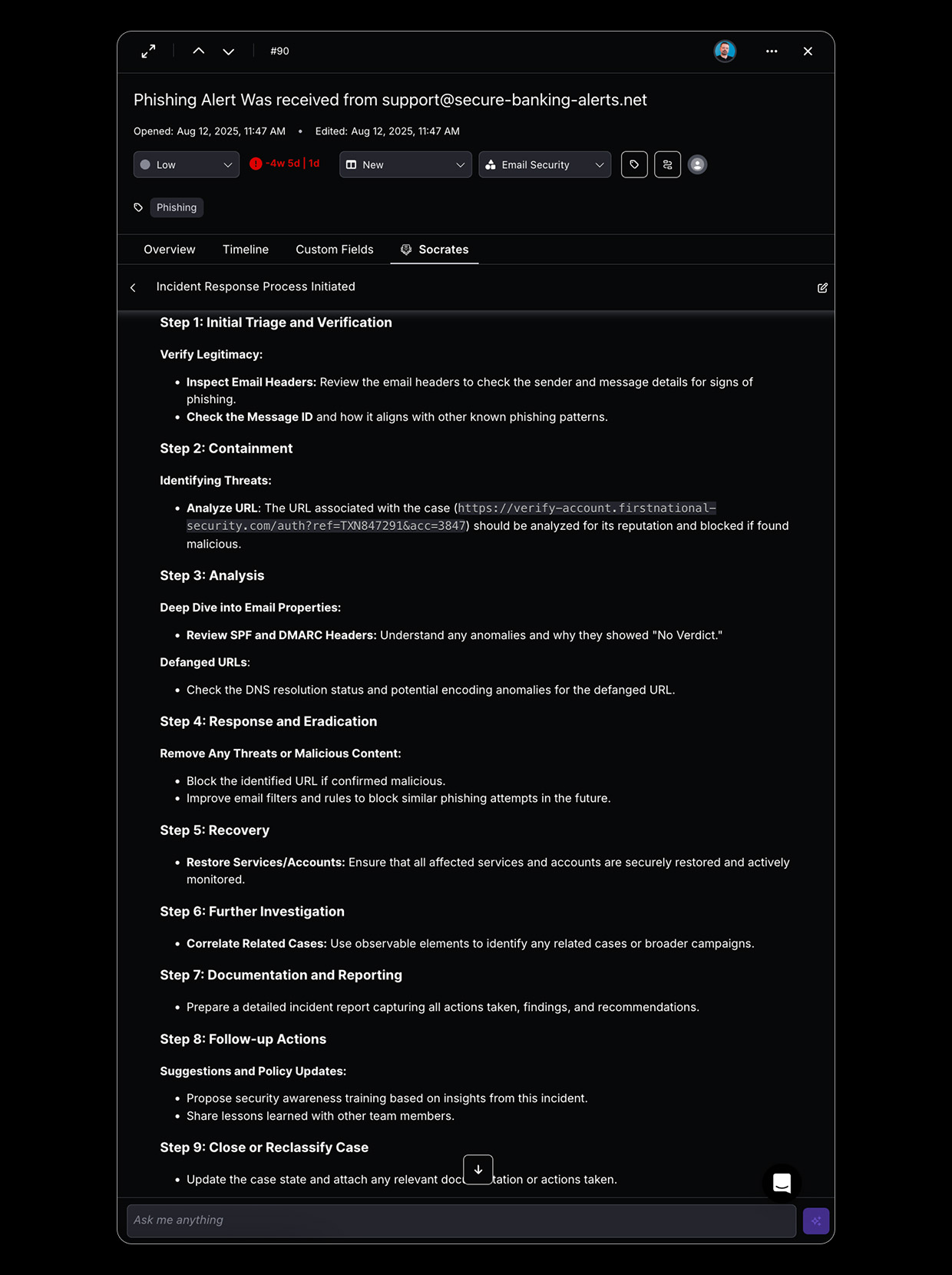
Socrates AI Agent
Natural language-driven AI that understands security context, generates custom playbooks, and makes autonomous decisions based on threat intelligence and organizational policies.
No-Code Automation Engine
Drag-and-drop workflow builder with 1000+ pre-built integrations enables security teams to create sophisticated automation without coding expertise or IT dependencies.
Real-Time Case Management
Intelligent case orchestration that automatically tracks incidents from detection to resolution, maintaining chain of custody and providing real-time visibility into SOC operations.
Full-Stack Security Integration
Native integrations with SIEM, EDR/XDR, cloud security, identity management, and threat intelligence platforms enable unified orchestration across your entire security ecosystem.
Autonomous Threat Hunting
AI-powered threat hunting that proactively searches for indicators of compromise, emerging attack patterns, and advanced persistent threats across your environment.
Compliance Automation
Automated compliance reporting and evidence collection for regulatory requirements, security audits, and incident documentation with immutable audit trails.
How it Works
1. Intelligent Alert Ingestion
- Torq ingests, normalizes, and processes thousands of security events from multiple disparate sources in real time through native integrations, event streaming, APIs, and other technologies, becoming a de facto communication bus for organizational, actionable security and information events.
- Torq’s flexible multi-workspace architecture enables high-scale event collection across multiple environments, while guaranteeing SLAs even under heavy load.
- Torq’s advanced operational controls identify event bottlenecks and proactively adjust resource allocations to handle event floods and ensure continuous operations.
2. AI-Powered Triage & Prioritization
- Ingested events are processed by powerful, performant automated processes, allowing contextual enrichment, correlation, deduplication, and event analysis, performed either through flexible deterministic workflows or flexible out-of-the-box or completely bespoke AI Agents.
- Event triage can take into account both threat and organizational context, collected through hundreds of out-of-the-box integrations with relevant IT, cybersecurity, communication, and business-line tools used in the organization.
- Upon completion of triage and prioritization, out-of-the-box case templates can be used to create a system of record of prioritized events requiring further investigation.
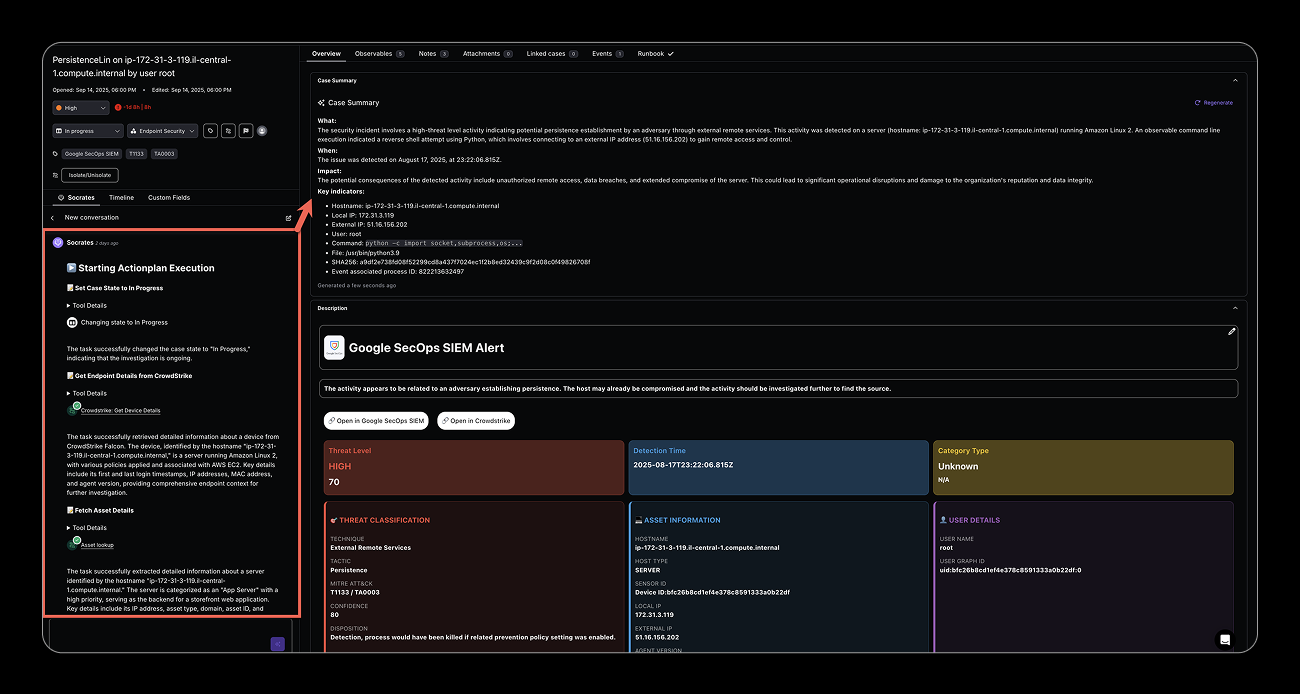
3. Autonomous & Human-in-the-Loop Investigation
- Torq provides a sophisticated case management system with customization options and AI components that guide analysts through response workflows. Multiple response and escalation strategies are available to analysts at their fingertips, with the system dynamically recommending the optimal path based on threat characteristics, business context, and historical outcomes.
- Specialized AI agents work in parallel to automatically investigate threats, gathering forensic evidence across your security infrastructure, correlating data from multiple sources, and building comprehensive case contexts that would typically require hours of manual research.
- Flexible reporting system helping security operations managers analyze operational KPI and outline required improvements, guiding the investments in automating processes according to the desired outcomes.
4. Intelligent Response & Escalation
- Threat containment and remediation strategies, implemented as dedicated hyperautomation workflows with bespoke AI Agents driving response actions inside the organizational environment, are leveraged autonomously or on demand by analysts working on the cases.
- Human-in-the-loop (requiring ad-hoc approval) or automated communication and escalation strategies involving 3rd party policy enforcement points, such as isolating compromised endpoints, revoking user access rights, blocking malicious sources, and providing an immutable audit trail for every action.
- Adaptive workflows driven by Agentic AI with a dedicated layer enforcing consistency of the process and compliance with the organizational guidelines and guardrails.
Security Stack Integration
HyperSOC seamlessly integrates with your existing security infrastructure through our comprehensive library of connectors and AI-generated integrations.
SIEM & Log Management
Splunk, Elastic, QRadar, Sentinel, Sumo Logic, and custom log sources
Endpoint Detection & Response
CrowdStrike, SentinelOne, Microsoft Defender, Carbon Black, Cortex XDR
Network Security
Palo Alto, Fortinet, Cisco, Check Point, Zscaler, Cloudflare
Cloud Security
AWS Security Hub, Azure Sentinel, GCP Security Center, Prisma Cloud
Identity & Access Management
Active Directory, Okta, Ping Identity, CyberArk, BeyondTrust
Threat Intelligence
VirusTotal, ThreatConnect, Anomali, Recorded Future, MISP
Real-World SOC Incident Response Scenarios
Discover how Torq HyperSOC transforms complex security incidents into automated, coordinated responses that neutralize threats while preserving evidence and maintaining business continuity.
Ransomware Attack Response
Critical
When ransomware indicators are detected, Torq immediately isolates affected endpoints, identifies the attack vector, maps lateral movement, and coordinates containment across network, identity, and backup systems while preserving forensic evidence.
Data Exfiltration Detection
Data Protection
Unusual data access patterns trigger automated investigation that correlates user behavior, network traffic, and data classification to identify potential data theft, implement DLP controls, and coordinate legal and compliance response.
Privilege Escalation Attack
Identity Security
Suspicious administrative activity triggers immediate identity analysis, privilege review, and endpoint investigation to detect credential compromise or insider threats, automatically implementing least-privilege controls and session monitoring.
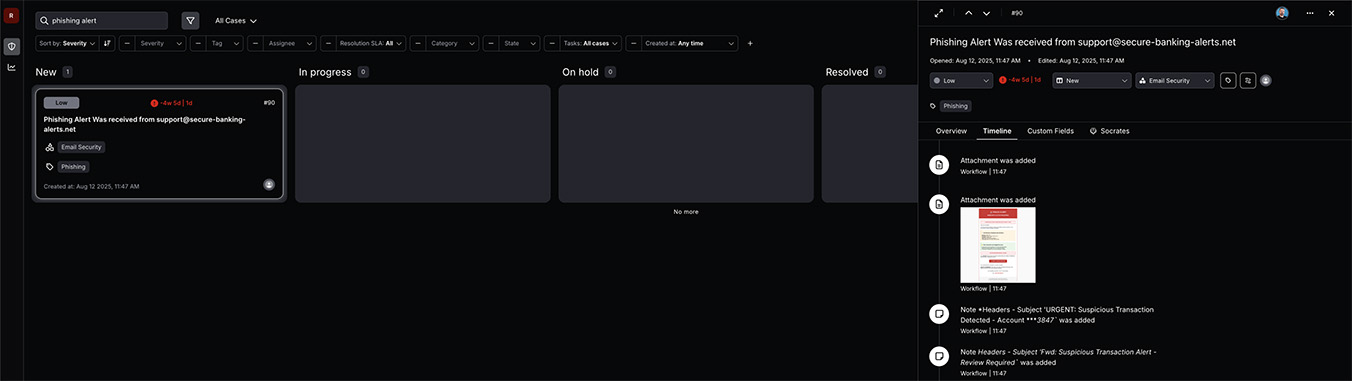
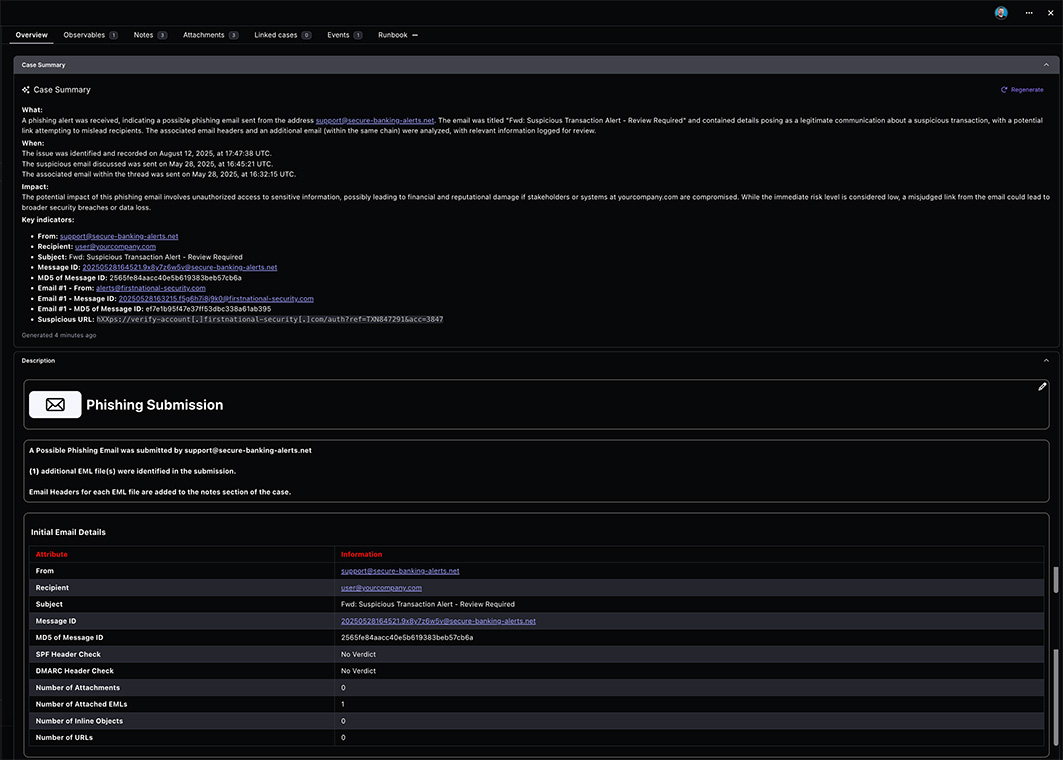
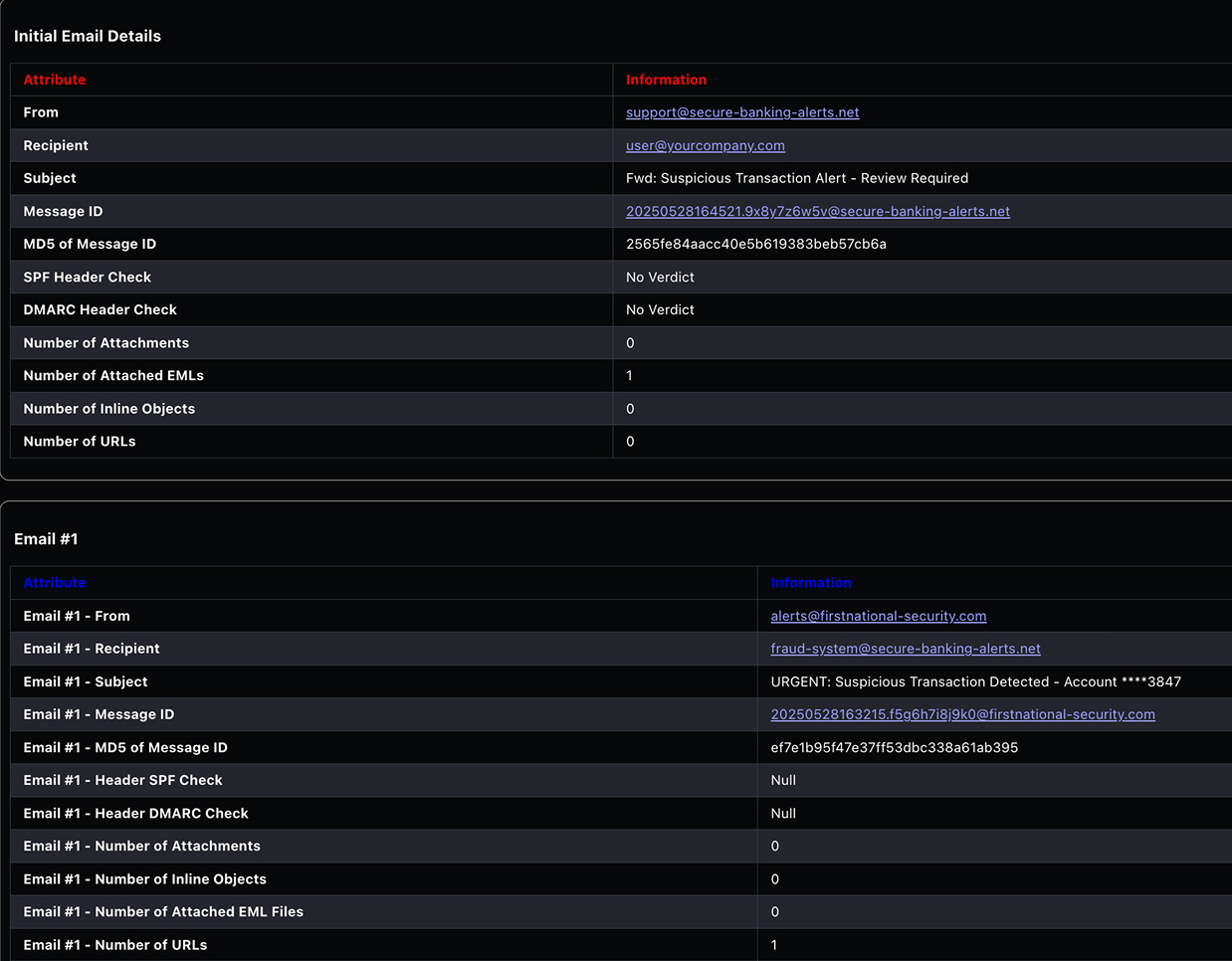
Hyperautomated Phishing Response
Cloud Security
Torq receives and normalizes phishing alerts from all email security tools, creating a unified view of email threats across your entire email infrastructure, and responds to the threats at machine speed.
Network Detection and Response
NETWORK SECURITY
Third-party solutions monitor network traffic in real-time using behavioral analytics, and AI to detect abnormal system behaviors and cyber threats across on-premises, cloud, and hybrid environments to trigger automated incident response, transforming raw network alerts into automated response actions.
Zero-Day Exploitation
Advanced Threats
Behavioral detection of unknown attack patterns triggers immediate threat hunting, IOC generation, and protective controls deployment while coordinating with threat intelligence teams and security vendors for signature development.
Transform Your SOC Operations with Hyperautomation
Eliminate manual bottlenecks, reduce analyst burnout, and achieve autonomous threat response capabilities that scale with your organization while improving security posture and operational efficiency.
Dramatic Reduction in Alert Fatigue
AI-powered triage eliminates 90% of false positives, allowing analysts to focus on genuine threats and strategic security initiatives rather than manual alert investigation.
Accelerated Mean Time to Response
Autonomous investigation and response capabilities reduce MTTR from hours to minutes, containing threats before they can establish persistence or cause significant damage.
Enhanced Threat Detection Coverage
Comprehensive integration across security tools provides 360-degree visibility and correlation capabilities that identify sophisticated attacks missed by isolated point solutions.
Scalable SOC Operations
Hyperautomation scales incident response capabilities without proportional staff increases, handling volume fluctuations and complex attack scenarios autonomously.
Improved Analyst Productivity
Free security professionals from repetitive tasks to focus on threat hunting, security research, and strategic improvements that enhance organizational security posture.
Comprehensive Audit Trails
Immutable activity logs and automated compliance reporting ensure regulatory requirements are met while providing complete visibility into incident response activities.
SOC KPIs & Analytics
Track critical SOC metrics including Mean Time to Detect (MTTD), Mean Time to Respond (MTTR), alert volumes, false positive rates, and incident closure times. Customizable dashboards provide at-a-glance views of operational health and can be tailored for different stakeholders, from SOC analysts who need tactical metrics to executives who require strategic insights.
Threat Intelligence & Trend Analysis
Visualize attack patterns, threat actor activities, and emerging vulnerabilities affecting your organization. Torq identifies trends in incident types, attack vectors, and affected assets.
Team Performance & Capacity Planning
Monitor analyst workload distribution, case handling times, and skill development needs. The platform tracks individual and team productivity metrics and identifies bottlenecks in your incident response processes, providing insights to support data-driven decisions for staffing, training, and process optimization.
Compliance & Audit Reporting
Generate automated reports for compliance frameworks, including SOC 2, ISO 27001, PCI DSS, and GDPR. Torq records immutable audit trails of all security events, investigations, and response actions. Custom report templates can be configured for internal stakeholders, board presentations, or regulatory submissions with automatic scheduling and distribution.
Business Case
Unlock the full potential of autonomous SOC operations with measurable ROI and proven enterprise results.
“Torq HyperSOC™ is the first solution we’ve seen that effectively enables SOC professionals to mitigate issues including alert fatigue, false positives, staff burnout, and attrition. We are impressed with how its AI augmentation capabilities empower our team to be much more proactive about fortifying the security perimeter.”
Chief Information Security Officer, Fortune 500 Financial Services