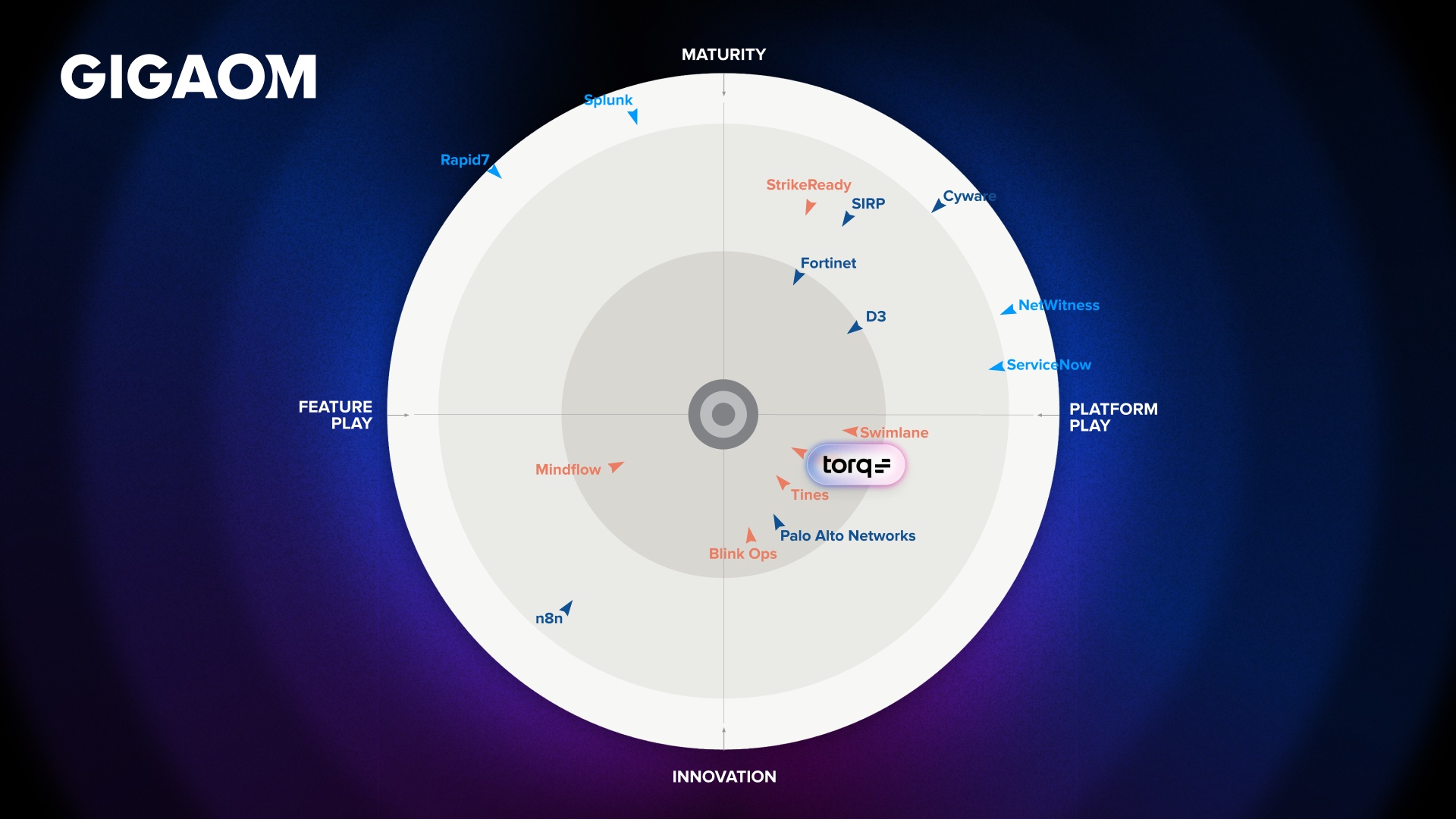
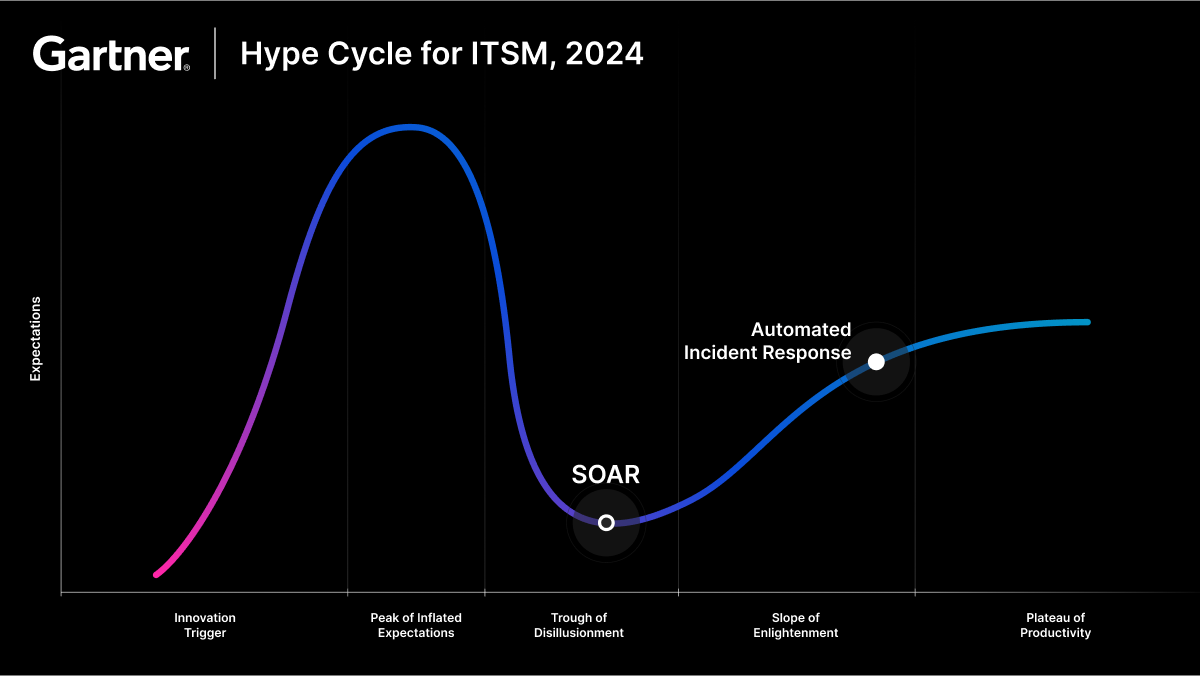
What is Security Hyperautomation?
Hyperautomation is a term that’s taking the cybersecurity world by storm. It’s now being used by many security companies, but what does it mean and how is it transforming SecOps for the better?
Security Hyperautomation
is a Critical Enabler
Connect siloed security solutions and threat patterns. Gartner defines Hyperautomation as a business-driven, disciplined approach that organizations use to rapidly identify, vet, and automate as many business and IT processes as possible. Security Hyperautomation involves the orchestrated use of multiple technologies, tools, or platforms, including: artificial intelligence (AI), machine learning, low-code/no-code tools, packaged software, and other types of decision, process, and task automation tools.
With a rise in malware and phishing threats among enterprises and an increase in adoption of IoT and BYOD trends, Allied Market Research indicates there is a need for hyperautomation in security. The global cyber-talent shortage prevents companies from scaling their hiring and operations. eSecurity Planet recommends that hyperautomation is the first step to take because it protects and preserves a business’s ability to grow.
Hyperautomating your enterprise security is one of the most effective investments your organization can make. The report notes that with the right application, hyperautomation delivers significant productivity and efficiency. Gartner estimates the overall impact to be extremely high, so the time to capitalize is now.
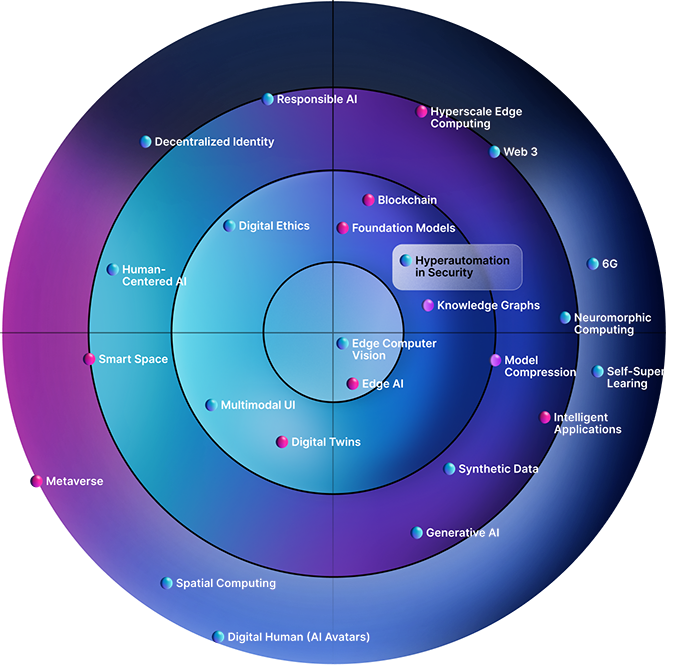
The Gartner Emerging Tech Impact Radar: 2023 report features “Hyperautomation in Security” as a Critical Enabler. Based on time-to-adoption, it is one of the most impactful emerging technologies and trends in 2023.
Too Many Tools
The overabundance of cybersecurity tools creates significant issues for organizations. While these tools are designed to protect, their sheer number can lead to inefficiencies, gaps in security, and increased complexities for analysts. The word “consolidation” is at the forefront of many organizations as they are tasked to do more with less. The threat landscape hasn’t changed; however, budgets definitely have, forcing CISOs and CFOs to be more deliberate on the tools they choose and extracting significantly more value from their existing tools that are often vastly underutilized.
Security Hyperautomation is not just about automating tasks; it’s also about intelligently integrating and orchestrating a multitude of tools to work in harmony. For organizations grappling with tool overload, hyperautomation offers a structured and efficient way to maximize each tool’s value and potential while ensuring a cohesive and robust cybersecurity strategy.
“60% of line of business users agree an inability to connect systems, apps and data hinders automation.”
Multi-Cloud Complexity
Today, 76% of organizations now operate in multi-cloud environments. Yet, at the same time, as businesses increasingly rely on multi-cloud environments to optimize operations and flexibility, they’re faced with intricate challenges tied to managing and securing these complex infrastructures. Multi-cloud configurations bring unique vulnerabilities and configurations that can be hard to track manually.
Hyperautomation is a formidable ally for cybersecurity professionals, providing streamlined processes facilitating efficient detection, analysis, and response to potential security threats across multi-cloud ecosystems, including private, public, and SaaS environments.
“71% of CIOs say the explosion of data produced by cloud -native technology stacks is beyond human ability to manage”
Difficulty in Retaining and Hiring Security Talent
There is an unprecedented demand for experienced cybersecurity professionals, but the supply is limited. Because of the scarcity, it has been difficult for organizations to find and retain qualified cybersecurity personnel, leading to burnout due to workloads and employees accepting more competitive job offers. Retaining talented professionals is a recurring issue in cybersecurity. It’s not just about finding the right people; it’s also about keeping them engaged and passionate about their jobs. Rather than security analysts being bogged down by repetitive tasks and constant searches for indicators and other suspicious activities, these professionals can immensely benefit from embracing automation.
By hyperautomating routine security tasks, Torq helps fill this gap, enabling security professionals to focus on more complex tasks that require human expertise. Further, Security Hyperautomation creates an environment in which cybersecurity analysts feel valued, and see a clear path for growth. Concurrently, it equips organizations with tools to scale cybersecurity operations to combat threats effectively. In a domain where demand for skilled professionals far outstrips supply, Security Hyperautomation emerges as a strategic tool for both retention and operational scalability.
![]()
“71% of analysts feel very or somewhat burned out at work, and the number one most frustrating aspect of the job is spending time on manual work.”
How Security Hyperautomation Outperforms SOAR
10X Faster ROI
70X Reduction in Time-to-Block Malicious Traffic
800% Improvement in Execution Time
How Hyperautomation
Benefits People
Enhanced job satisfaction
Enables security analysts to focus on complex issues requiring human intuition, expertise, and decision-making.
Reduced employee burnout
Reduces the workload and tedium by automating routine tasks.
Follow the sun (24/7/365) availability
Supplement your IT security teams with AI-powered security automation, enabling security teams to respond to security incidents and alerts around the clock without human intervention.
Professional growth and upskilling
Enables more time for learning, mentoring, and development versus performing ‘busy work’ better suited for AI to analyze at scale consistently.
Collaborative work environment
Facilitates teamwork among analysts by centralizing the tooling, updating security cases with contextual information, and providing updates across teams in communication platforms like Slack, MS Teams, Discord, Zoom, and many more.
Intelligent user self-service with natural language processing (NLP)
Empowers users who prefer self-service options to quickly and easily make requests or ask questions using natural language to achieve effective resolutions without waiting to speak to a representative.
Contextual Case Management
Auto-prioritizes cases based on your classifications, such as low, medium, and high, within the case management tool and summarizes the key findings, actions taken, and timeline all within the case automatically.
How Hyperautomation
Benefits Processes
Consistent and standardized response to security incidents
Ensuring that security procedures are followed consistently across the organization, further reducing the chances of human error.
Enhance decision-making
Security teams are empowered to make more informed decisions by providing relevant real-time information and analyzing data from multiple sources, prioritizing and providing a detailed assessment of the situation while suggesting appropriate responses.
Unified visibility and monitoring
Consolidates security monitoring and detection across disparate technology platforms with real-time insights into security incidents, allowing security teams to quickly identify patterns and trends in security incidents and adjust their security policies and procedures accordingly.
Contextual case enrichment
Security Hyperautomation uses LLMs in incident response within case management to automate threat detection, integrate threat intelligence, provide contextual analysis, recognize patterns, automate incident triage, recommend response actions, and use NLP.
Automated threat hunting
Security Hyperautomation powered by cutting-edge LLMs, analyzes data from multiple sources to identify patterns, anomalies, and indicators of compromise to help SOC analysts proactively search for environmental threats and vulnerabilities.
Automated threat detection and response
Enables real-time identification, classification, and remediation, reducing the MTTR significantly.
Streamlined compliance management
Streamlines compliance enforcement with continuous scanning of vulnerabilities and misconfigurations with automated alerting, reporting, and remediation.
Optimized cost management and ROI
Ensures efficient resource utilization of people’s time and skill sets by automating security tasks at scale, and extracting maximum value from the existing tooling, allowing for consolidation efforts due to increased inefficiencies.
Automated patch management
Automates the scanning and update process, ensuring all systems consistently receive the latest security patches.
Automated vulnerability management
Seamlessly integrates and automates vulnerability management tools and processes, ensuring timely detection and remediation of threats across your organization.
How Hyperautomation
Benefits Technology
Create powerful workflows in minutes
Launch your first automated flow in minutes with an intuitive and straightforward no-code interface,expert-curated, content-rich templatized workflow library, and intelligent recommendations. Gets security teams started instantly automating manual tasks at scale.
Go beyond APIs with limitless extensibility
Gain vast flexibility to expand use cases with capabilities such as SSH, PowerShell, SQL, Python, BASH, Kubernetes, AWS, GCP, Azure CLI, and other scripting or programming languages.
Connect any application, service, or server
No punching holes in firewalls for VPN services or reverse proxies, because Security Hyperautomation utilizes zero-trust containerized agents making outbound-only connections for on-premise environment connectivity.
Data integration
Facilitates the conversion and normalization of various sources of information into a standardized format autonomously with LLMs, enabling seamless integration and communication between disparate systems and tools, improving the efficiency and accuracy of automated workflows.
Standardized security configuration
Enforces uniform security configurations across on-premise, private or public cloud, and SaaS applications, resulting in a consistent security posture across all environments and resources.
Continuous configuration management
Scans for configuration drifts across on-premise and cloud environments and automatically alerts, reports, and resolves any identified configuration drift issues.
Adaptive access control
Dynamically adjusts access controls based on user classification, behavior, and resource sensitivity in addition to automated user onboarding and offboarding, significantly bolstering an organization’s security posture against account misuse and account compromise.
Leave the Limitations of SOAR Behind Forever
Our customers now rely on our platform for more than 3m daily security automations. In other words, when we say SOAR is dead, we mean it.
The Torq Hyperautomation Platform is the first to automate all workflows and processes across the entirety of modern enterprise security organizations to deliver best-in-class, end-to-end cybersecurity protection. It also offers the world’s first GPT AI-based analytics capability for auto-analyzing cybersecurity incidents, making strategic responses, and informing immediate and long-term defensive measures.
Request a Demo
Ditch legacy SOAR and switch to enterprise-grade, AI-driven hyperautomation.
See it in action.