For security teams, properly managing which users can access resources and governing the level of access those users have is about as basic as locking the door at night.
Understandably then, there are thousands of options available to fine-tune or revoke access, and it’s likely that issues come up daily for most companies—if not hourly. But chasing alerts every time a user needs access to a new resource or manually auditing systems to see what entitlements they already have are poor uses of an analyst’s time. These are the classic signs that a process needs to be automated.
Torq can help your team automate these controls in a number of different ways using pre-built workflows. In combination with JumpCloud, organizations can easily implement layers of security that make sense to both end-users and auditors. By quickly moving cloud-based identities among different groups, IT admins and security teams can add in the conditions of access that make sense for each resource, regardless of where the users are.
This blog will focus on just-in-time (JIT) access for temporary permissions using JumpCloud user groups and Slack. JumpCloud user groups can allow access to SSO applications, provision users, authenticate network access, and even create local profiles across Mac, Windows, and Linux devices. In this example, we will show how to easily provision access to SSO applications.
How Torq Automates JIT Permissions
This workflow runs when credentials are requested by a Slack command, and if approved, adds users to a JumpCloud user group. When the time limit for access has expired, the user will be automatically removed from the user group, revoking permissions and closing security gaps.
How it works:
- A user invokes a Slack command, triggering a temporary access request.
- JumpCloud then pulls the groups that the user already belongs to, and Torq compares them to applications that have been configured to provide JIT access.
- Slack asks the user which group they would like access to and for how long.
- Torq then sends the access details to a designated Slack channel and requests approval on behalf of the user.
- If access is rejected, or the request times out, the user is notified through Slack.
- If access is approved, the user is added to the group in JumpCloud and receives a notification.
- When the predetermined timer expires, Torq sends a command to JumpCloud to remove the user from the group, and the user is notified through Slack.
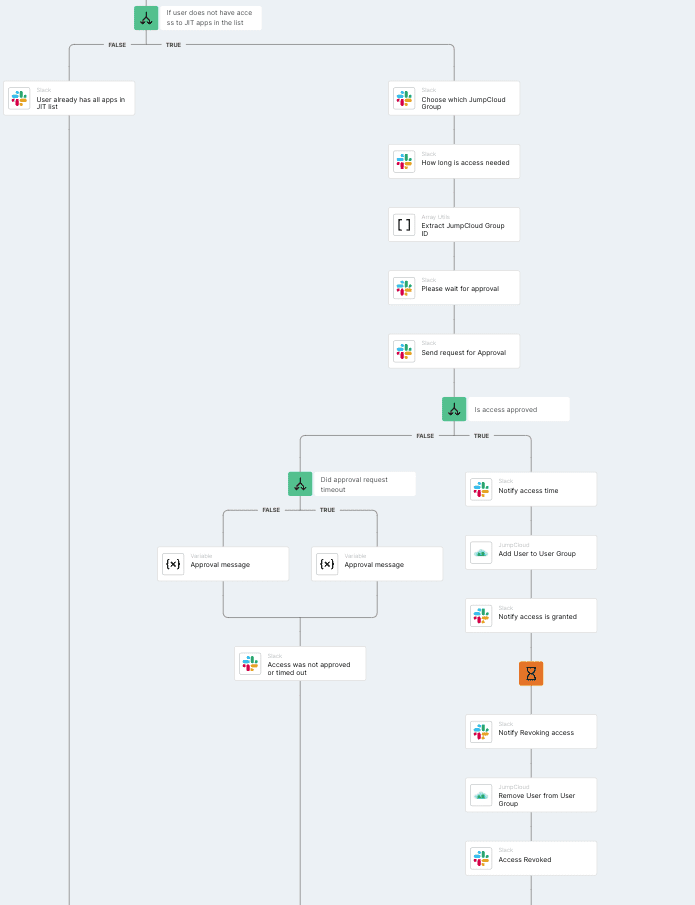
Workflow builder in Torq showing the steps for just-in-time access
As with all workflow templates, users can modify this to align with organizational policies. For example, if a log event is required, steps can be added to log the access into ServiceNow or Jira.
Using this workflow helps consolidate work into a single medium—Slack channels—and automates user-driven tasks like requesting access. But it still maintains the crucial “human in the loop” for determining if the access is appropriate and/or necessary. Users get access when they need it, and analysts avoid the toil of small tasks. Another win for automation.
Get the JIT Workflow Template
Torq users can find this JIT workflow in the app along with many others for managing identities and access, like Suspend Accounts with No Logins after N Days and Ask User to Confirm Failed Login Attempts.
Get Started Today
Not using Torq yet? Get in touch for a trial account and see how Torq’s no-code automation accelerates security operations to deliver unparalleled protection.



