The evolution of cybersecurity tools is nothing short of remarkable, but I suppose they had to be when it isn’t just the Morris Worm you’re worried about. There has been a wave of buzz around the latest technology in years gone by. EDR evolved into MDR, then SASE, and in recent times we’ve seen Immutable Backup take the front seat.
But hey, I’m sure you can’t go far wrong by investing in all these kinds of technologies. The more the merrier, right? Depending on what you read, the number of cybersecurity-related technologies that enterprises have integrated and deployed in their infrastructure is between 45-70*, which is absurd. So, when there are vendors that are working in unison and supporting the idea of a better integrated and more visible cyber picture, it sounds like a win-win. This idea of your EDR, SASE and Email Security vendor working in tandem is a dream come true, right?
Some things don’t change unfortunately, and cybersecurity teams and CISOs are still being asked to do the impossible. Those age-old problems don’t budge easily: shortage of cyber professionals and resources, and a plethora of cyber vendors offering too many tools and too many processes. “With great tools, come great alerts,” or something along those lines, is what we’re typically told.
Who’s expected to deal with these additional alerts created from all of these technologies? Just because they integrate well, doesn’t mean they’re contributing to what the main focus should be: improving your cybersecurity posture and reducing the risk to your organization’s workforce.
Some things do change, however. The new generation of CISOs don’t want to overload their teams with work to churn out results. They want to work smarter. They see business, people, and technology as one that can work together to get results.
CISOs are looking at the bigger picture. Empower the cyber teams, let them develop their skill sets, so they can return their knowledge and value back to the company. They’re not relying solely on the latest tech to churn through alerts and let the team on the ground deal with the processes.
The saying goes, “Train your people enough so they can leave, and treat them well enough so they don’t want to.” Nailed it.
Your infrastructure security engineer wants to develop into an AWS architect, but is too busy dealing with CSPM alerts. Your cyber analyst has aspirations of being a CISO themselves one day, but is bogged down by suspicious user activity, and misses all those opportunities to gain additional knowledge, learning how to present and communicate better, or simply lacks a development in strategic mindset to tackle problems. And that lack of development means they look elsewhere. Cybersecurity roles are notorious for job hopping, and I think that’s because the dreams of complex, technical and exciting projects are brushed away by daily firefighting.
Give the power back to the people, including the techies that are literally running the show, and retain them longer. But how? First, strip your mind of all pre-existing knowledge and thoughts on legacy SOAR. Those time consuming, low use case producing, pro-services heavy technologies are a thing of the past.
Hyperautomation is reforming how cyber teams, top to bottom, left to right, are approaching their CyberSecOps. The time to automate every task that comes from the latest and greatest cyber technologies you invest in, because it’s perfectly viable, is now. Torq’s enterprise-grade security hyperautomation has made that possible.
The barrier to entry is no longer a dedicated DevSecOps team of 5 who can code in every language A through Z. Cyber and dev teams have spent years trying to create use cases with legacy SOAR vendors, and might be lucky if they publish 4 or 5 workflows/playbooks in a year. With Torq, the entry need only be a laptop, mouse and keyboard. Maybe a slight oversimplification, but it’s not far wrong. The ability to imagine, create and publish a workflow is now astonishingly rapid with Torq.
So, yes, the latest tech tools are great to have, the integrations will no doubt provide you with additional advantages and help secure your workforce, and sure they’ll do what they say on the tin. But the real power in your CyberSecOps is their new found time, being in control of alerts and tasks, and effectively remediating all of those alerts with a hands-off approach where possible. Torq is the tool to augment everything you have, say (and show) how we give time back to your teams, as well as increase the efficacy and ROI of other tools. Here’s a sneak peek at what time you could be saving:
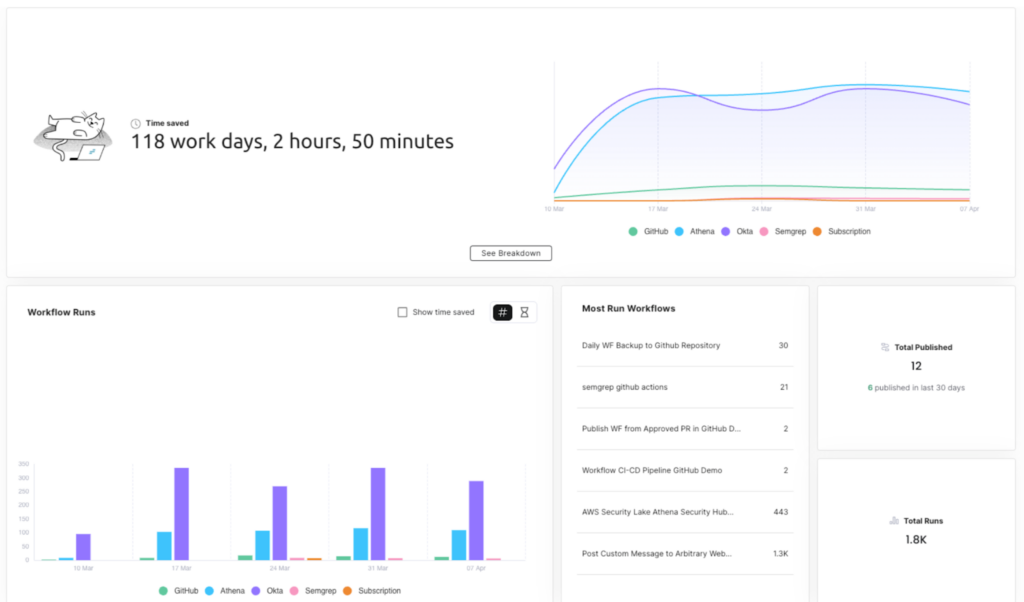
If you’ve miraculously found time between all your alerts to read this, don’t take my word for it; put our hyperautomation platform to the test. Any and all CyberSecOps or CloudOps processes you want automating – we’ve got you!
CSPM, IAM, alert remediation, email phishing response, threat hunting, and secure access to sensitive data – honestly the list is only limited to your imagination (or in my case, a word count).
* https://www.infosecurity-magazine.com/news/organizations-76-security-tools/