Contents
Get a Personalized Demo
See how Torq harnesses AI in your SOC to detect, prioritize, and respond to threats faster.
The 2024 SANS Detection and Response Survey sheds new light on some all-too-familiar security challenges: security operations teams are overwhelmed with alerts, struggling to respond fast enough, and tracking the wrong KPIs. Sure, automation adoption is increasing (64% of organizations now leverage it in some capacity), but most SecOps teams are still operating in slow, reactive, and heavily manual environments.
Five Security Challenges Faced by SecOps Teams
1. Security teams are stuck in semi-automation mode.
Most security operations teams think they have automated response mechanisms, but they’re really just babysitting inefficient, semi-automated workflows. The SANS Survey data shows that while 64% of teams have automated response mechanisms in place, less than a quarter have fully automated their processes. That means the vast majority still rely on analysts to manually intervene and execute responses.
2. Slow response times are leaving organizations exposed.
Speed matters. Attackers are betting you’ll take a while to respond to threats. SANS found that a whopping 32.8% of teams take hours to respond to threats, and 41.4% say they respond within minutes. In today’s reality, even minutes can be too slow. Recent data shows that lateral movement breakout times dropped from 62 minutes to 48 minutes, with the fastest recorded breakout happening in just 51 seconds. If a response takes more than a minute, the damage may already be done.
3. Alert fatigue and data overwhelm are killing security team productivity.
It’s loud in the SOC. More than half of security teams say false positives are a huge problem, and 62.5% are overwhelmed by sheer data volume. Every second spent triaging junk alerts is a second not spent investigating real threats — meaning SOCs are burning through their most precious and expensive resource: human focus. Analysts’ expertise is critical for threat investigation and response, yet most of their time is wasted manually sorting through thousands of low-value alerts that should’ve been filtered out in the first place. This wastes time, burns out analysts, and, worst of all, lets real threats slip through.
4. Security teams are still tracking the wrong KPIs.
The most surprising part of the survey responses is that more than 50% of security teams aren’t even tracking KPIs like Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR). Instead, they’re tracking vanity metrics like the number of incidents detected — or, worse, they don’t have enough data to measure their own efficiency. Without the right data, SOC teams cannot optimize performance or reduce response times.
5. SOAR is holding teams back.
SOAR was supposed to be the answer to security automation… right? The majority of respondents use SOAR for threat response, but half still rely on manually running commands to respond to threats. This proves what we at Torq already know: SOAR hasn’t lived up to its promise. SOAR platforms were supposed to automate security workflows, but most teams still struggle with slow response times, rigid playbooks, and high maintenance overhead.
The Fix: An Autonomous SOC Powered by AI-Driven Hyperautomation
The answer to these existential security challenges isn’t manually tuning SOAR, tweaking detection rules hoping something works, or hiring more analysts (Be real: Where are you even finding them? The SANS Survey found the majority of security teams struggle with lack of skilled personnel). The real fix is an autonomous SOC powered by AI-driven Hyperautomation: a SOC that invests in AI and automation to eliminate inefficiencies, take action at machine speed, and, ultimately, shorten response times.
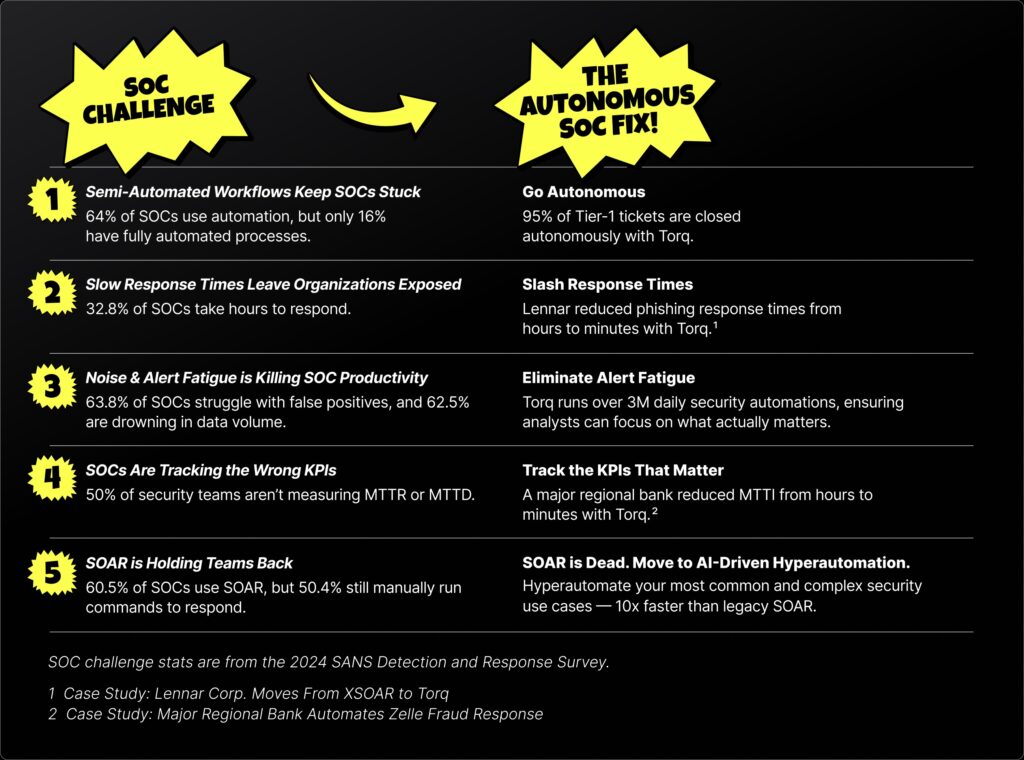
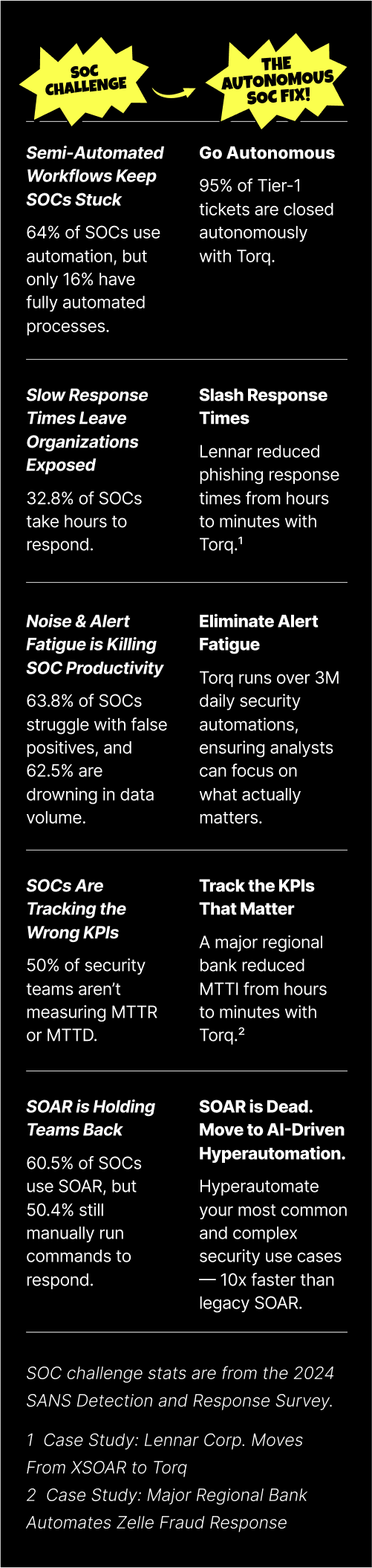
1. Go autonomous.
Ditch the scripts, stop the manual tuning, and let AI take over. An autonomous SOC removes the need for engineers to build, maintain, and tweak workflows with extensive coding. Instead, teams can simply describe a workflow, use case, or outcome using natural language to guide agentic AI as it implements workflows to secure the organization faster than ever before. An autonomous SOC can handle 95% of Tier-1 cases — allowing security teams to focus on critical, high-impact threats, rather than babysitting outdated playbooks or struggling with the limitations of rigid SOAR architectures.
“With Torq Agentic AI, the answer is yes to questions such as: Are analysts happier? Are they sticking around? Do they have time to focus on more interesting and complex investigations? Are MTTM and MTTR lower? Torq Agentic AI extends and enhances our team so it can make better decisions more quickly — resulting in stronger security all around.”
2. Slash response time.
With SOC automation, alerts don’t sit in a queue waiting for an analyst to take action. AI-driven Hyperautomation instantly takes action to investigate alerts, enrich cases, and contain threats — isolating infected endpoints, disabling compromised accounts, and blocking malicious infrastructure before damage is done. Unlike SOAR’s static playbooks, an autonomous SOC leverages AI to tirelessly and intelligently analyze and remediate massive volumes of security incidents, shrinking response times from hours to seconds.
3. Eliminate alert fatigue.
AI Agents don’t just process alerts — they triage and prioritize them. AI-powered SOCs use sophisticated planning and contextual reasoning to filter out low-fidelity alerts, suppress false positives, and escalate only the alerts that matter. Analysts no longer have to sift through thousands of useless alerts — AI handles the noise so teams can focus on critical security risks.
4. Track the right KPIs.
An autonomous SOC should be able to measure security response and provide visibility into operations. Instead of requiring analysts to manually track and compile data, AI can capture and log detection times, response actions, and remediation speeds automatically. SOC leaders finally get a clear picture of what’s working, where bottlenecks exist, and what to optimize.
5. SOAR is dead. Ditch it.
SOAR is simply too slow, rigid, and high-maintenance to keep up with modern SOC demands. An autonomous SOC doesn’t rely on pre-scripted playbooks — it builds, executes, and adapts automation dynamically, all in natural language. With AI-driven Hyperautomation, security teams move faster than attackers, not the other way around. See the difference.
It’s time to move past the limitations of SOAR and slow, reactive security operations. Take your SOC autonomous — learn how easy it is to switch to AI-driven Hyperautomation from Torq.








