Contents
Get a Personalized Demo
See how Torq harnesses AI in your SOC to detect, prioritize, and respond to threats faster.
AI isn’t a tool you bolt onto your existing SOC. It’s forcing us to fundamentally rethink how security organizations are structured, staffed, and measured. CISOs who treat 2026 as a transition year will fall behind. The ones who redesign their AI SOC org chart now will build teams that operate at machine speed.
I believe there’s a real shift in the landscape that’s going to require organizations to completely rethink and redesign the way they deliver modern security. That’s not hyperbole; it’s why I made the move to Torq as Field CISO.
I’ve spent the better part of 15 years doing security transformation — current state to future state, rinse and repeat. But I’ll be honest: the piece in the middle has fundamentally changed. It’s no longer about shuffling headcount between ops, GRC, and architecture. It’s about designing an entirely different operating model. And if you’re still thinking about AI as simply “adopting a new tool,” you’re not thinking big enough.
What’s Breaking in the Traditional SOC Model
Let me start with what made me realize incremental change wasn’t going to cut it.
It’s the scale. There’s always been a talent shortage — that’s nothing new. But the attack surface is growing more complex by the day. It’s not just attacks on your organization anymore. You’ve got third parties, cloud sprawl, and AI-powered threats that evolve faster than your team can write detection rules. And no matter how many human resources you throw at the problem, you’re always battling coverage, response time, and the fundamental limitation of human speed.
Here’s the uncomfortable truth: we keep trying to fix machine-speed problems with traditional methods, and the more we do, the further behind we get.
And the promise of “one platform that does everything”? That’s already disappointed most of us. What I’m seeing now is a shift toward thinking about data and automation as the horizontal layers that cut across every vertical, rather than buying another point solution for another discipline.
So if everyone agrees AI adoption is necessary, why hasn’t it happened at scale? It’s not budget. It’s not belief. It’s hesitation.
There’s an accountability gap. Everyone’s looking at each other — IT, data, security — asking, “Who’s going to grasp the nettle?” Who’s going to put a stake in the ground and take a direction on AI adoption? Leaders hesitate because they don’t want to go in a direction that might not work out. It’s not fear exactly. It’s waiting for permission.
From my experience? Whichever function steps forward first will benefit most. The others become customers of that team. And security is uniquely positioned to lead this, because automation and AI cut across everything we do.
The New AI SOC Org Chart: Outcome, Judgment, Execution
If a CISO were building a security organization from scratch today (no legacy structure, no inherited headcount), what would it look like?
I’ll tell you what it wouldn’t look like: the traditional vertical model based on hierarchical structures, siloed roles and responsibilities, and tenure-based progression. That model is dissolving, whether we like it or not.
Today’s forward-thinking CISO is about to embark on a revolutionary step change. It’s time to embrace a purposeful shift to outcome-based teams, working holistically across pools of human and technical resources to achieve innovative and optimized risk reduction.
I see the model moving toward three distinct layers:
- Outcome layer: This is where you define strategic objectives: where we are now, where we need to be, and what success looks like. The people here are your architects, strategists, risk practitioners, and transformation leads. They’re no longer managing a vertical. They’re defining the outcomes the entire function needs to deliver.
- Judgment layer: This is where specialists provide oversight. They ensure quality and policy compliance. They make decisions on irreversible actions. They lead complex incidents and facilitate post-incident learning. These are your senior practitioners, people with deep expertise who can validate whether the execution layer is delivering the right results.
- Execution layer: This is where AI and automation operate, continuously, consistently, at machine speed, within predefined guardrails. This layer never sleeps. It provides 24/7/365 coverage. It’s the foundation everything else is built on.
The transformation model I’ve used throughout my career still exists: current state, future state, and a program to get from one to the other. But the piece in the middle has changed. It’s no longer about “What does the org look like? How many people in ops versus GRC versus architecture?” Those silos and verticals… they’re going to dissipate.
Instead, groups of people will come together and use elements of different technologies to deliver a service or product that achieves an outcome. It’s almost like a dev squad. Agile teams. That’s not something security organizations are used to, but it’s where we’re headed.
Will AI Replace SOC Analysts? Displaced, Not Replaced
Now, the question I get asked most: “If AI handles 90-95% of Tier-1 work, does that mean we’re cutting headcount?” In my humble opinion, that’s completely the wrong way to think about it.
AI isn’t there to replace people. It’s there to increase capacity, coverage, and response speed — continuously and consistently, within predefined guardrails that ensure outcomes.
Ask anyone in a security function, from CISO to Tier-1 analyst, and they’ll tell you they haven’t got anywhere near enough time to cover all the aspects of their role that they should. AI gives that time back.
The way I think about it: analysts won’t be replaced, they’ll be displaced:
- Those with architectural and engineering skills, the thought leaders, and innovators keeping up with technological advances, will move into the outcome layer, helping define what the organization needs.
- Those who are GRC-focused, specialists in their domain, very experienced, and who know what they’re looking for — they’ll move into the judgment layer, building workflows, validating outputs, ensuring the function is delivering the right results.
- The execution layer becomes AI-native. Fewer and fewer humans working at human speed will be required in roles that demand machine speed. We can’t have that function lagging as it does today.
And here’s the thing: CISOs are desperate for headcount. If I can take people doing fairly mundane, repeatable operational tasks and move them into something that motivates them more, gives them career development, and allows them to use new skills? That’s a good thing.
You can’t replace the face-to-face skills needed to liaise with your business, understand strategy, educate stakeholders, or provide context and judgment on complex situations. That’s very, very hard for AI at the moment. So it’s back into that judgment box. Human skills become more valuable, not less.
What the AI SOC Org Chart Looks Like in Practice
Let me give you a concrete example of how this AI SOC org chart works in practice: a Detection, Response & Containment team in this new model. The outcome: Rapidly detect, contain, and limit business impact.
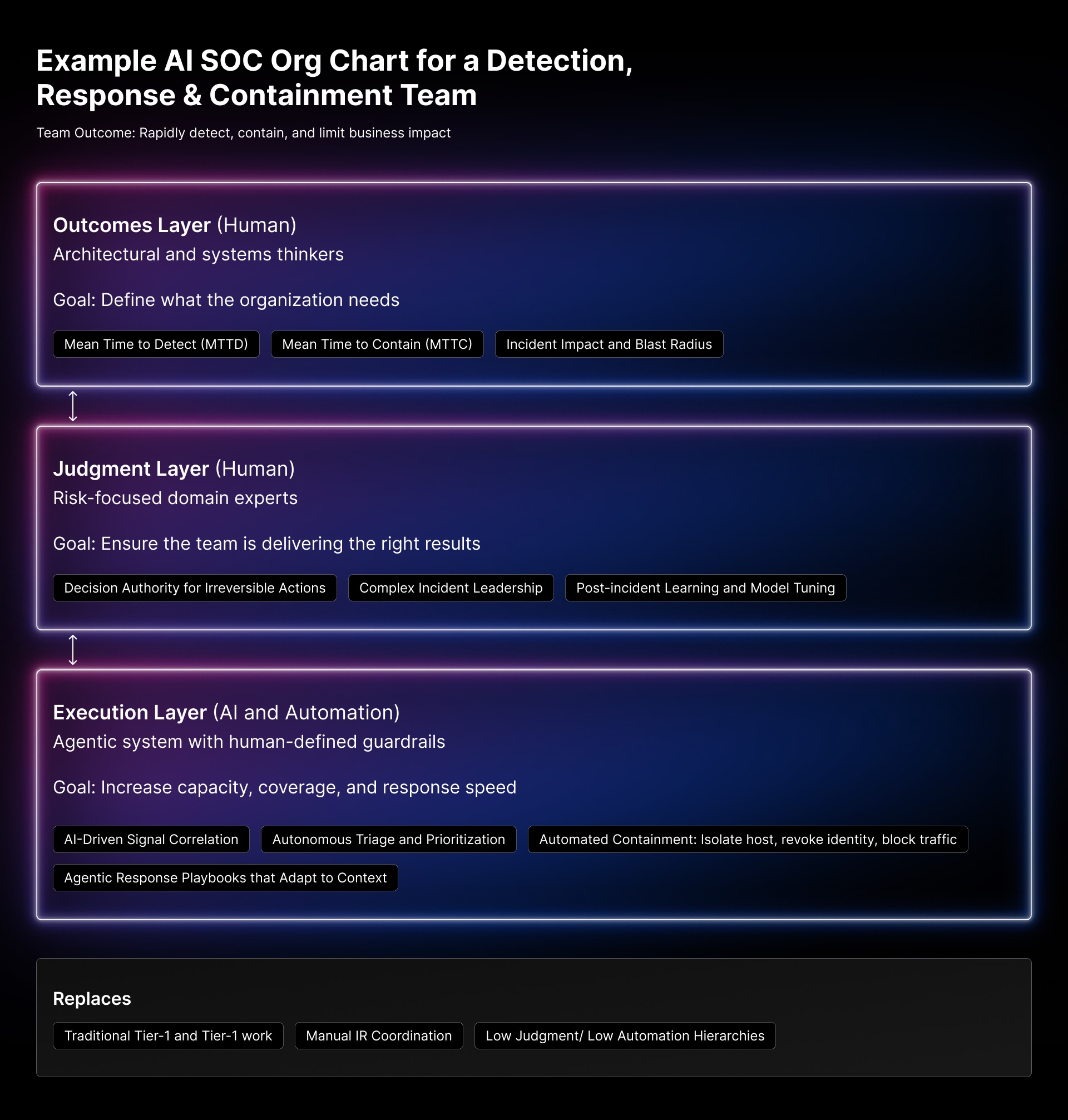
What traditional teams does this replace? Tier-1 and Tier-2 SOC. The low-judgment, low-automation work that’s been burning analysts out for years.
The future is high judgment plus high automation: AI-orchestrated, outcome-driven teams. Strategy and architecture designing outcomes. Specialists assuring operations through judgment. Automation and AI performing continuous and consistent execution.
The great thing about this model is that it’s just as applicable outside the AI SOC. It will soon start making sense to adjacent functions like Privacy, GRC, and IT Operations. It won’t be long before the wider organization adopts this as a common language.
What’s Stopping CISOs from Redesigning Around AI?
So if this is the only path forward, what’s stopping people from moving? There’s unclear ownership. IT, data, security — they’re all looking at each other, asking, “Which one of us is going to do it?” There’s fear of stepping forward first and getting it wrong. There’s a tendency to view AI as just another tool requiring effort and time that teams don’t have.
Here’s how to break through:
- Accept that the future is now. Check Point just documented a threat actor using AI to build an entire malware platform. What was planned as a 30-week development cycle was executed in hours. When threats move at that speed, a security org built around 9-to-5 shifts and procurement cycles isn’t just inefficient. It’s indefensible.
- Start with your current state. Look across your architecture, processes, skills, and resources. But instead of thinking in disciplines, think in outcomes.
- Design the organization of the future with AI and automation at the heart. Start with machine speed. Start with 24/7/365 coverage that never sleeps and delivers consistent results. That’s the foundation. Everything else is built around the edges.
The CISOs who map this out now will be able to deploy and sustain AI-native operations when they need it most — when they’re being attacked. The organizations that try to bolt it on later, that haven’t done the thinking, are going to throw these tools in and find it doesn’t work. It won’t be sustainable. It’ll put them in a worse position when they’re under pressure.
The Security Orgs That Get AI Right… and What Happens to Those That Don’t
In two to three years, the organizations that started designing their adoption journey now will be the ones able to sustain that change when they potentially need it most.
Those that don’t? They’re going to be the ones held up as examples. The companies that hesitated. The ones still looking for perfection instead of recognizing this is no longer early adoption; it’s a necessity.
The model I keep coming back to is this: humans at the edges, AI working at machine speed in the middle. A continuous improvement loop where outcomes are defined, execution is automated, and judgment provides the feedback that keeps everything aligned.
It’s a revolutionary step change. I appreciate that’s quite a leap. But why take a small step when you need to make a jump?
The future isn’t about who has the most analysts or the biggest budget. It’s about who figured out how to let AI handle volume while humans handle strategy. The organizations that design that model now will be the ones still standing when the machine-speed attacks arrive.
And they will arrive.
See how Torq can save your team, strategy, and budget.