Contents
Get a Personalized Demo
See how Torq harnesses AI in your SOC to detect, prioritize, and respond to threats faster.
TL;DR
The problem: Attackers achieve breakout in under 48 minutes. The average alert investigation takes 70 minutes. And 40% of security alerts are never investigated. Most AI in the SOC helps at the margins — summarizing alerts, suggesting actions — but doesn’t close the gap.
What actually works: AI-autonomous security operations, where agentic AI triages, investigates, and remediates end-to-end without human intervention on routine cases. Not AI that advises. AI that acts.
Five questions to ask vendors: Does it act or just advise? Does it integrate across your full stack? Is every decision explainable? Can you configure where autonomy ends, and human judgment begins? Can they show measurable outcomes from real deployments?
Bottom line: The distinction between AI-assisted and AI-autonomous is between incremental improvement and operational transformation. The SOCs that win in 2026 aren’t the ones with the biggest headcount — they’re the ones that let AI handle volume while humans handle strategy.
The math doesn’t work anymore. Attackers now achieve breakout — moving from initial access to lateral movement — in under 48 minutes. Meanwhile, the average alert investigation takes 70 minutes.
AI in security operations was supposed to fix this. Instead, most implementations have delivered chatbots bolted onto legacy workflows, alert summarization that still requires human action, and ML-based detections that generate more noise than signal. These implementations help at the margins, but they don’t solve the core problem: volume, speed, and the widening gap between attacker efficiency and defender capacity.
And it gets worse. According to the SACR AI SOC Market Landscape 2025 report, 40% of security alerts are never investigated at all. Another 61% of security teams admitted to ignoring alerts that later proved to be critical incidents.
The real opportunity isn’t AI-assisted security operations. It’s AI-autonomous security operations. And the difference between those two concepts is where outcomes live.
Why Most AI in Security Operations Falls Short
Let’s be honest about what AI in the SOC has actually delivered over the past few years. Mostly, we’ve seen alert summarization tools that save analysts a few minutes of reading. Chatbot interfaces that answer questions but don’t take action. Machine learning detections promise precision but deliver false positive rates that make analysts want to throw their laptops out the window.
These tools help at the margins. But they don’t fundamentally change the operational reality. Analysts are still drowning. The SANS 2025 SOC Survey confirms that 66% of teams cannot keep pace with incoming alert volumes. Almost 90% of SOCs report being overwhelmed by backlogs and false positives.
Most AI Stops at Analysis — That’s the Problem
Here’s the thing most AI vendors won’t tell you: their solutions only address the first step of the threat lifecycle. Triage? Covered. Investigation? Partially. Response? “That’s on you.”
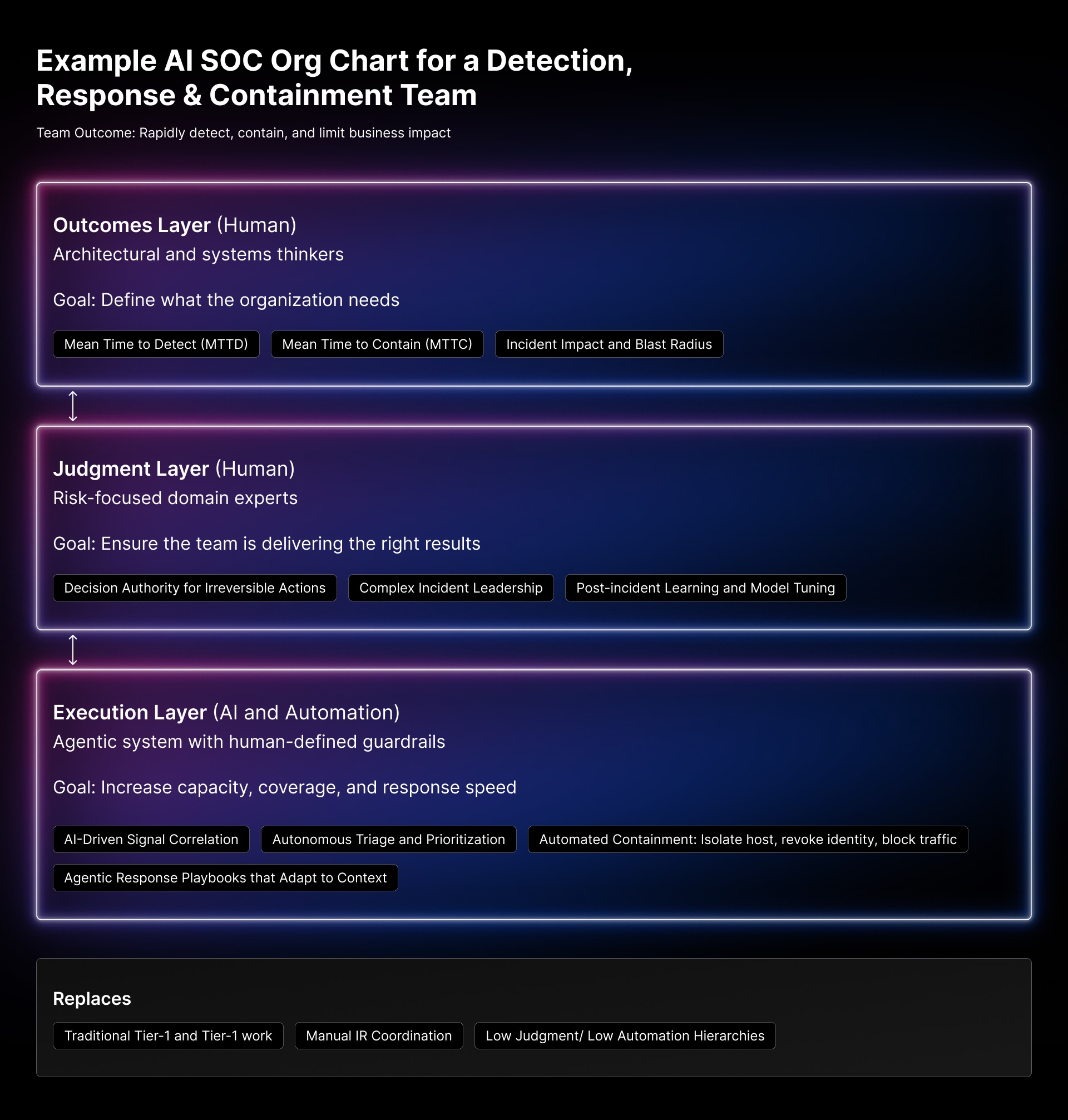
A true AI SOC must manage the complete threat lifecycle — from triage through investigation to response. The work doesn’t end once you’ve identified a threat. The Agentic SOC takes action and closes cases. Autonomously.
Most “AI in the SOC” products are really just analysis tools with a chat interface. They’ll tell you what’s happening. They might even tell you what to do about it. But they won’t actually do anything. That still requires a human to click buttons, switch tabs, copy data between systems, and execute remediation steps manually.
The AI SOC that actually works looks different:
- Triage: AI ingests and normalizes telemetry from across your security stack, correlating and deduplicating events to reduce noise. It delivers verdicts that separate false positives from actual risk — before alerts ever reach a human.
- Investigate: Specialized AI agents gather evidence, assemble timelines, and summarize findings. No more manual enrichment across six browser tabs.
- Respond: Contain. Coordinate. Remediate. AI executes response actions autonomously and ensures critical threats reach the right people.
What AI in Security Operations Should Actually Do
The shift that matters isn’t from manual to AI-assisted. It’s from AI-assisted to AI-autonomous. That means AI that doesn’t just summarize alerts, but triages, investigates, enriches, and remediates — end-to-end, without human intervention unless escalation is genuinely required.
This is where agentic AI enters the picture. Unlike traditional automation or generative AI that responds to prompts, agentic AI sets goals, plans actions, and executes. It reasons through problems. It adapts to context. It operates with the autonomy of a skilled analyst, but at machine speed and scale.
Here’s what this looks like in practice:
- An alert fires from your EDR. Within seconds, AI enriches the alert with data from your SIEM, correlates related events across IAM and cloud infrastructure, identifies the affected user and endpoint, checks asset criticality, and reviews recent behavior patterns.
- If needed, it contacts the user via Slack to verify suspicious activity.
- Based on the investigation findings and predefined runbooks, it either remediates autonomously — isolating the endpoint, revoking sessions, updating blocklists — or escalates to a human analyst with full context and recommended actions.
No human touched that workflow unless escalation was required. The entire process completes in minutes, not hours.
At Torq, this is exactly what our AI SOC delivers. Socrates, our AI SOC Analyst, coordinates a multi-agent system where specialized AI Agents handle triage, investigation, remediation, and case management in parallel. According to IDC, organizations using Torq can automate more than 95% of Tier-1 analyst tasks. That’s operational transformation.
The human role doesn’t disappear; it evolves. Analysts stop clicking through repetitive alerts and start supervising AI operations, handling the truly complex cases, and doing what they actually got into security to do: hunt threats, improve defenses, and outthink adversaries.
The Future of AI in Security Operations
Attackers aren’t waiting for defenders to figure out AI. They’re using it now — to generate convincing phishing campaigns, automate reconnaissance, identify vulnerabilities faster, and scale attacks that would have required teams of humans. According to the Verizon 2025 DBIR, synthetically generated text in malicious emails has doubled over the past two years. Here’s how defenders can win.
Near-term: Agentic AI becomes the standard operating model for high-performing SOCs. Organizations that don’t adopt will fall further behind as attackers increasingly leverage AI to accelerate their own operations. The asymmetry between offense and defense will widen for those relying on human-only workflows.
Multi-agent systems: Rather than a single AI handling everything, specialized agents coordinate complex investigations in parallel — one analyzing network traffic, another examining endpoint behavior, another correlating identity signals. These agents collaborate and cross-reference findings, achieving investigative depth that would require a team of senior analysts working in concert.
5 Key Considerations for Implementing AI in Your SOC
Before you sign another vendor contract, ask these questions:
1. Does it act or just advise? AI that suggests actions still requires human execution. That’s a copilot, not an autopilot. Look for AI that can execute remediation within defined guardrails — isolating hosts, disabling accounts, removing malicious emails — without waiting for human approval on routine cases.
2. How does it integrate? Point-tool AI creates more silos. If your AI solution only works with one data source or one workflow, it can’t deliver cross-environment correlation or end-to-end automation. You need AI that orchestrates across your entire stack — SIEM, EDR, IAM, cloud, ticketing, collaboration tools — simultaneously.
3. Is it explainable? Black-box AI doesn’t fly with auditors, compliance teams, or analysts who need to trust the system. Every decision, every action, every escalation should have a clear audit trail showing exactly what the AI observed, what it concluded, and why it took the action it did.
4. What’s the human-on-the-loop model? Full autonomy isn’t always appropriate. High-severity incidents, sensitive systems, and novel attack patterns may warrant human review. Look for configurable guardrails and escalation paths that let you define where autonomy ends and human judgment begins — and adjust those boundaries as trust develops.
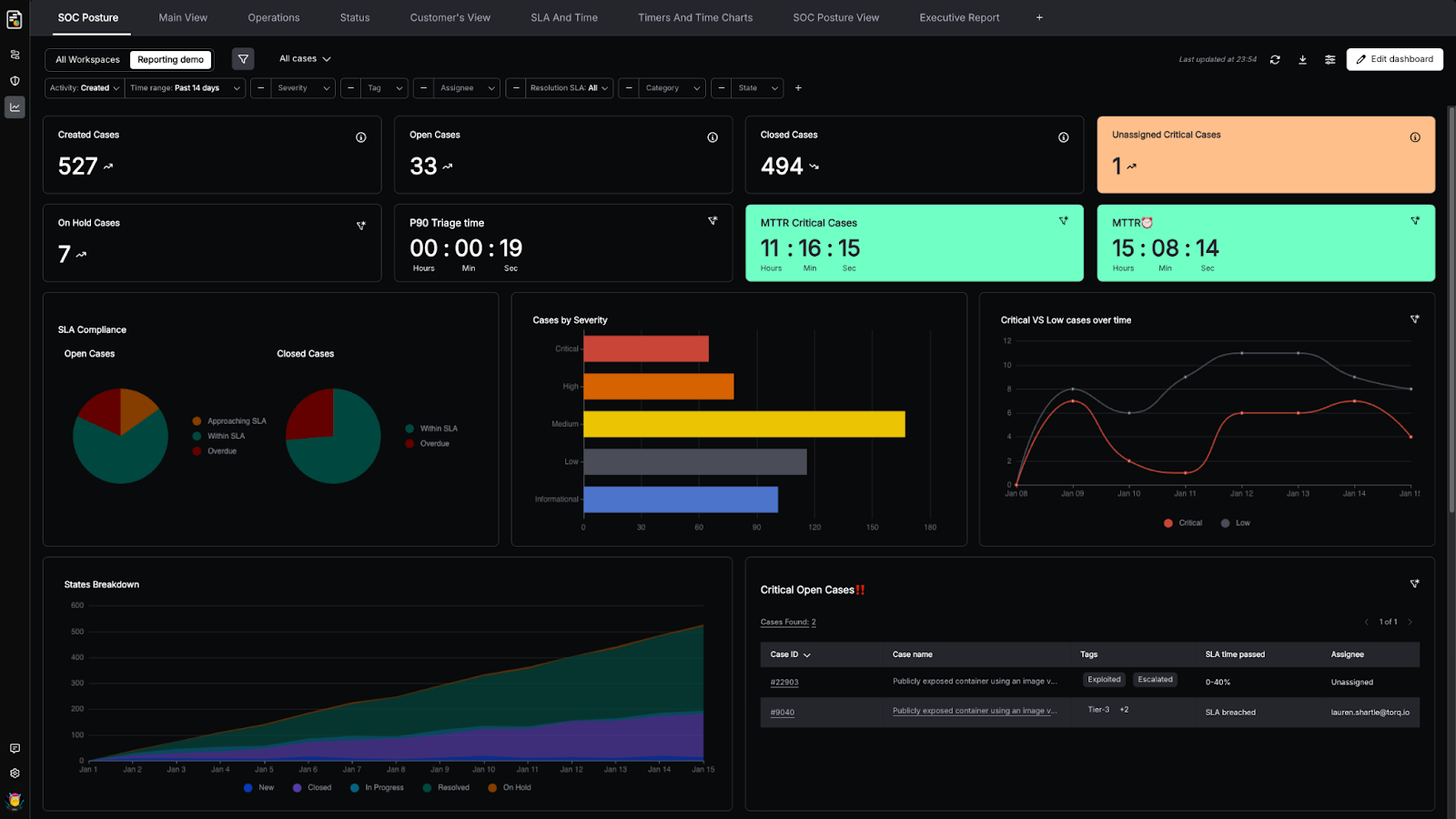
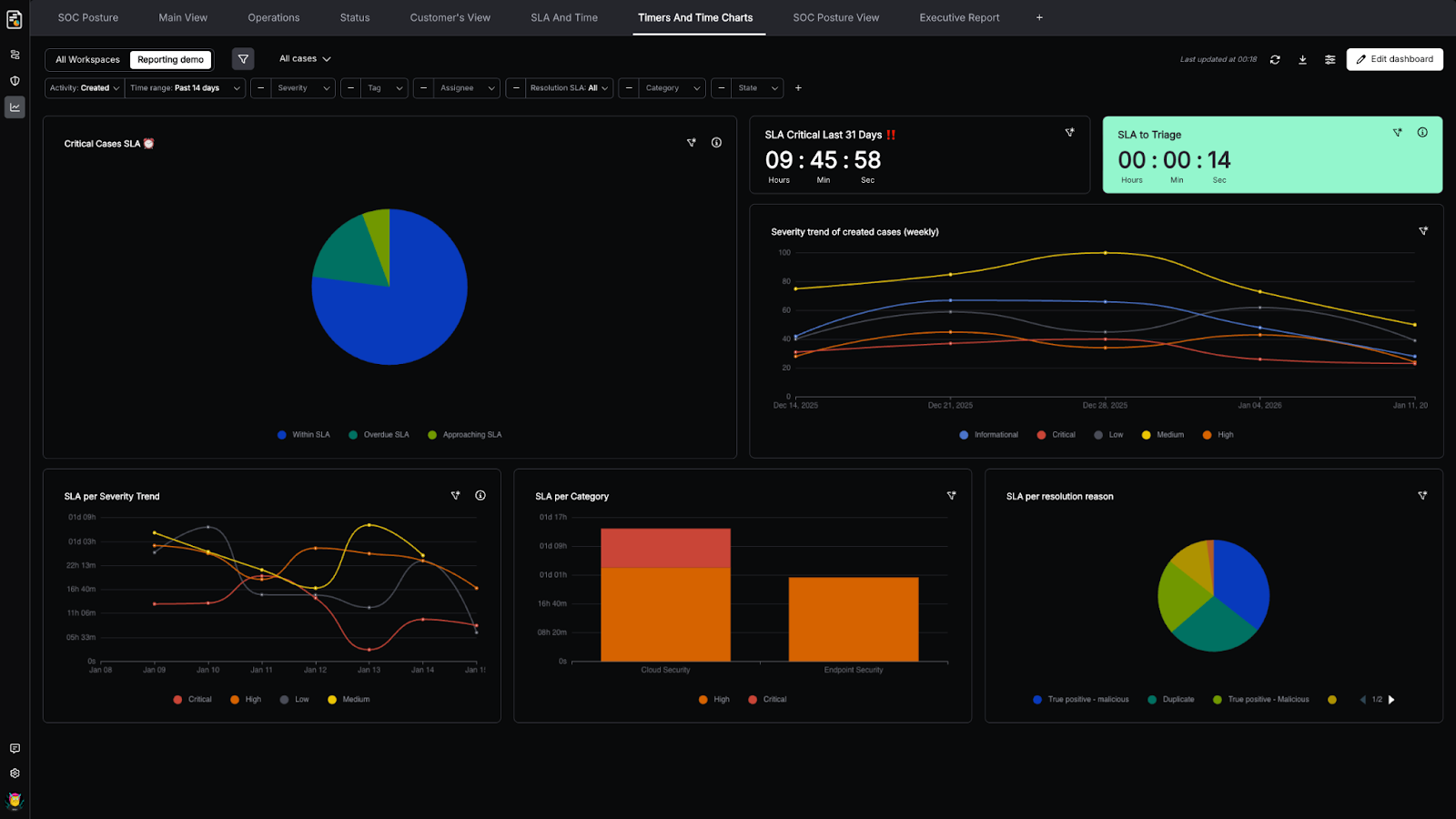
5. Can you measure outcomes? If the vendor can’t show concrete metrics — MTTD reduction, MTTR improvement, alert clearance rates, analyst hours saved — it’s vaporware. Demand proof of impact from real deployments, not theoretical capabilities.
Can You Afford to Stay at Human Speed?
AI in security operations isn’t new. But AI that actually works — AI that operates, not just assists — is.
The difference between AI-assisted and AI-autonomous is the difference between incremental improvement and operational transformation. Between hiring more analysts to handle more alerts and fundamentally changing the economics of security operations. Between drowning in volume and actually getting ahead of threats.
The SOCs that thrive in 2026 and beyond won’t be the ones with the biggest headcount or the most tools. They’ll be the ones that figured out how to let AI handle volume while humans handle strategy. The ones that shifted from human-in-the-loop to human-on-the-loop. The ones that made the leap from AI as a feature to AI as the foundation.
The attackers aren’t slowing down. The alert volumes aren’t decreasing. The talent shortage isn’t resolving itself. The only variable left to change is how you operate.
Ready to see AI in security operations that actually works? Download the Don’t Die, Get Torq Manifesto.
FAQs
AI in security operations refers to the use of artificial intelligence to automate core SOC functions — including alert triage, threat investigation, case management, and incident response. Traditional implementations focus on AI-assisted workflows, where AI summarizes or recommends actions that still require human execution. More advanced implementations use agentic AI, where specialized AI agents autonomously triage alerts, gather evidence, make containment decisions, and remediate threats end-to-end — escalating to human analysts only when predefined thresholds require it.
AI-assisted security operations use AI to help analysts work faster — summarizing alerts, suggesting next steps, or surfacing relevant context. The analyst still makes every decision and executes every action. AI-autonomous security operations use agentic AI to handle the full threat lifecycle independently: triaging alerts, investigating cases, executing response actions, and closing cases without human intervention on routine incidents. The human role shifts from executing tasks to supervising AI operations and handling complex escalations.
An agentic AI SOC is a security operations center where AI agents autonomously manage the majority of alert triage, investigation, and response workflows. Unlike traditional automation that follows static playbooks, agentic AI reasons through problems, plans its own investigation steps, adapts to context, and executes response actions within defined guardrails. Multi-agent systems coordinate specialized AI agents in parallel — one analyzing network traffic, another examining endpoint behavior, another correlating identity signals — to achieve investigative depth at machine speed.
AI reduces alert fatigue by automating the triage and investigation steps that consume most analyst time. Rather than requiring humans to manually review, enrich, and prioritize every alert, AI ingests telemetry across the security stack, correlates and deduplicates events, filters false positives, and delivers high-confidence verdicts before alerts ever reach an analyst. According to the SANS 2025 SOC Survey, 66% of SOC teams cannot keep pace with incoming alert volumes. Organizations using AI-autonomous triage can investigate 100% of alerts — including the 40% that would otherwise go uninvestigated — while freeing analysts to focus on genuine threats and strategic work.
When evaluating AI for security operations, ask five key questions. First, does the AI act autonomously or just advise — can it execute remediation, or does it still require a human to click buttons? Second, does it integrate across your full stack (SIEM, EDR, IAM, cloud, ticketing), or does it only work with a single data source? Third, is every AI decision explainable with a clear audit trail? Fourth, what is the human-on-the-loop model — can you configure where autonomy ends and human judgment begins? Fifth, can the vendor demonstrate measurable outcomes from real deployments, including reductions in MTTD and improvements in MTTR, as well as analyst hours saved?