Consolidation or Collapse of Legacy SIEM?
Industry Analysts Signal End of Legacy SIEM as Operational Costs Continue to Rise
If you are a cybersecurity professional, it’s hard to ignore the recent shift in the SIEM landscape unless you’ve been living under a rock… or more likely, under the crushing weight of terabytes worth of disconnected SIEM logs. Let’s catch everyone up to speed anyway:
- March 2024: Cisco completed its $28 billion acquisition of Splunk, a significant move in the SIEM market.
- May 2024: Palo Alto Networks (PAN) announced the acquisition of IBM’s QRadar SaaS assets, facilitating the migration of QRadar SaaS customers to Palo Alto’s Cortex XSIAM platform.
- May 2024: LogRhythm and Exabeam, two major SIEM providers, announced their merger to create a unified entity specializing in AI-driven security operations (expected to close in the third quarter of 2024).
The consolidation – and collapse – of the legacy SIEM space is rapid, ongoing, and for those attuned to the cyclical nature of cybersecurity technology, not entirely surprising. We have seen the “lagging security vendor acquired by large tech titans” story play out plenty of times before. For example, Splunk’s acquisition of Phantom, Broadcom’s acquisition of Symantec, Palo Alto’s acquisition of Demisto, and even Cisco’s prior acquisition of Meraki… or Cisco’s acquisition of Sourcefire… or IronPort… or OpenDNS… or DuoSecurity. More often than not, an acquisition of this magnitude signals two things to the cybersecurity community:
First, the vendor being acquired is struggling to maintain market share, with innovative technologies quickly emerging to solve the challenges causing their churning customers significant reductions in both operational efficiency and security efficacy. We saw this when legacy AV (i.e. Symantec) was overtaken by NGAV/XDR platforms, or as legacy SOAR (i.e. Phantom) began to be overtaken by Hyperautomation solutions, and now again, with the emergence of Next-Gen or Multi-Data SIEM platforms.
Second, the impending expectation of shockingly high renewal costs.
The key difference in this case is that legacy SIEMs, such as Splunk, are not losing customers. And with the massive amounts of highly-regulated sensitive data stored in these legacy SIEM solutions, it’s safe to say they aren’t expecting to do so for a very long time. Regardless of rapidly increasing costs, many organizations fear there is no escape from SIEM lock-in, and that is exactly what the acquiring companies like Cisco and PAN are counting on.
Stuck in the SIEM-ulation?
Skyrocketing Data Volumes and Crippling Renewal Costs Are Holding the SOC Hostage
Historically, SIEM solutions have been the key centralization point of the Security Operations Center (SOC). They were built to enable threat detection and incident response by collecting and aggregating event logs across a multitude of security tools. However, SIEMs were built for an on-premise world, well before the explosion of cloud-based SaaS solutions or the multi-cloud environments that organizations are working with today.
As more and more technologies shift to the cloud, the volume of logs, events, and alerts continue to increase exponentially. According to a recent report The Evolution of the Modern Security Data Platform written by Francis Odum and Josh Trup, the problem is legacy SIEM costs are largely indexed to data volume – meaning the more you ingest, the more you pay. Larger amounts of data ingestion and an increase of integration requirements with new cloud-based security solutions have led to additional SIEM related challenges, such as alert fatigue, manual triage processes, complexities in data conversion, and inadequate scalability and performance. But none, it seems, are more difficult to overcome than SIEM vendor lock-in.
The reality is legacy SIEM solutions are deeply entrenched in the operations of both the Security Operations Center (SOC) and Governance, Risk, and Compliance (GRC) teams. Enterprise organizations are stuck in long-term contracts with their SIEM vendors due to regulatory compliance frameworks that require up to, if not more than, 7 years of sensitive data retention. Some organizations have found creative ways to implement a separation strategy by decoupling compute and storage costs, feeding data into multiple SIEMs. Though more often than not, these are simply cost-reduction strategies without an end-game in sight.
The biggest barrier to severing ties with a legacy SIEM solution is that while ingestion and retention costs are considered expensive, they are relatively cheap when compared to the costs associated with retrieval and removal of old logs from cold storage. This makes a SIEM rip-and-replace initiative a non-starter, and most organizations have come to terms with the fact that they may never escape the constraints of their SIEM contract. But with every day an organization is not migrating their day-to-day log storage off their legacy SIEM, they continue to extend the length of that contract, one day at a time.
The Emergence of the Multi-SIEM Strategy
How Multi-SIEM Offers More Scalable and Cost-Effective Data Aggregation in the Cloud
There are a number of business-related reasons why organizations may adopt a multi-SIEM strategy. For example, mergers and acquisitions may result in security teams falling into an inherited multi-SIEM approach. Or it may even be as simple as a newfound lack of trust in the anticipated innovation of their legacy SIEM technology following the recent acquisitions we’ve seen piling up across the SIEM landscape.
The main benefit that is driving organizations to adopt emerging best practices when it comes to data aggregation and event management, however, is cost reduction. An explosion in the volume and variety of data being ingested has made legacy SIEM a major burden on an organization’s budget. As a result, rather than attempting a costly rip-and-replace, teams may strategically choose which data is deemed important enough to send to the SIEM. The missing data, in turn, leaves gaps in the detection and investigation of potential security threats.
As the need for a modern, cost-efficient approach to data management and security event aggregation has become more clear, a new evolution of cloud-native data platforms have emerged to help mitigate these SIEM challenges. A number of unique approaches have emerged such as ETL Data Orchestrators, Next-Gen SIEMs, Cloud Security Data Lakes, or Multi-Data SIEMs. Whether they intelligently filter and cleanse logs before routing events and alerts to a SIEM, or decouple security analytics from the logging layer while structuring security data to better enable real-time detection and threat hunting – these cloud-native solutions are all centered around more scalable and cost-effective cloud data management.
Many organizations in the process of transitioning from an on-prem to a full-cloud or hybrid-cloud environment may choose to use this opportunity as a launch pad towards eventual migration. As more application and IT infrastructure moves to the cloud, they begin siphoning data away from their legacy SIEM provider into a more cloud-friendly option. Even if this means some data remains in legacy systems, especially considering the enormous cost of shipping existing data hosted in an already on-prem SIEM to the cloud, a multi-SIEM approach is still significantly more cost-efficient.
While the cost-reduction benefits of a multi-SIEM strategy have already been realized by forward thinking SOC teams, there is still hesitancy to separate data storage across many enterprise grade organizations who have become so accustomed to legacy SIEM way of life. Afterall, the original purpose of a SIEM solution was to have a centralized source of truth for all security logs, events, and alerts to coordinate investigation and response. Is decentralizing that data across multiple sources not taking a step backwards in security operations?
Achieving the Multi-SIEM with Torq Hyperautomation
Seamlessly Integrate Existing Processes Across Multiple SIEMS and Security Data Lakes
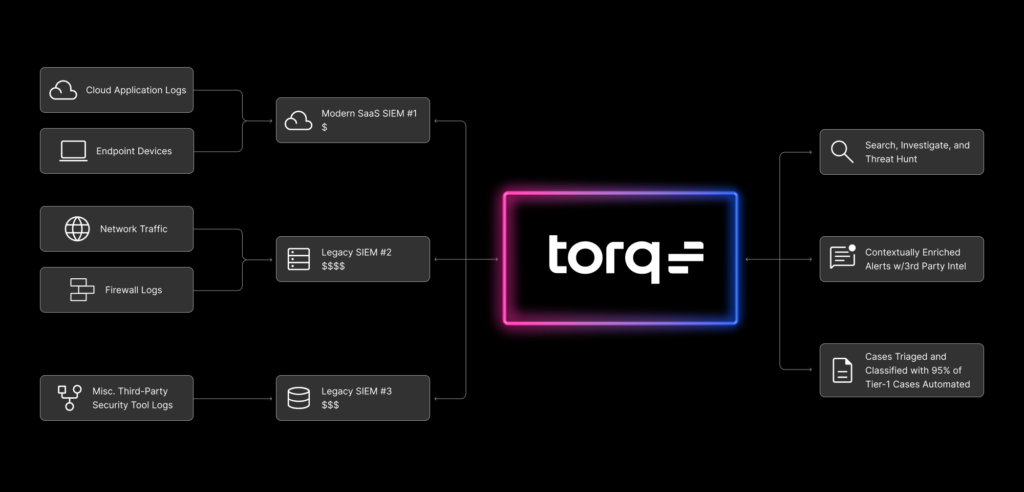
Hyperautomation enables the SOC to effectively achieve a multi-SIEM strategy without impacting existing processes or operational efficiency. It is the layer that sits on top of whichever SIEMs are ingesting logs, events and alerts allowing automated triage, investigation and remediation. With Hyperautomation, existing processes and workflows can run in parallel, automating actions within multiple SIEM solutions simultaneously instead of manually running the same actions multiple times across disparate data sources. This means organizations who want to free themselves from the legacy SIEM stranglehold finally have the key to unlock the cost-savings benefits of a multi-SIEM strategy, as well as the confidence that there is a definitive light at the end of the long, dark SIEM lock-in tunnel.
Torq makes it simple for SOC teams to integrate with any SIEM solution, and build out automations across a multi-SIEM approach. Torq eliminates the complexity of connecting multiple SIEMs by using Hyperautomation to automatically analyze, triage, and remediate the most critical threats, while reducing alert fatigue and allowing organizations to utilize the full suite of their existing security tools investments.
Torq’s drag-and-drop workflow designer makes it easy for SOC teams to replicate existing workflows and quickly replace a legacy SIEM vendor with their new cloud-native SIEM integration, maintaining existing processes without interruption. For more complex workflows, Torq’s natural language AI workflow builder levels up the SOC analysts’ skillset, enabling them to build and deploy workflows in minutes that run parallel actions across multiple SIEMs and Security Data Lakes. Torq’s purpose built HyperSOC solution will then correlate actionable data into comprehensive security cases and auto-remediate 95% of the entire case management lifecycle.

With Torq as the all encompassing SOC adaptor, organizations can simply stop sending data to their legacy SIEM, begin sending all net-new logs, events and alerts to their new cloud-native SIEM of choice, and leverage hyperautomation to automatically run security operations across a Multi-SIEM architecture without impacting existing processes or sacrificing security data gaps for cost-savings.
How Innovative Companies are Leveraging Hyperautomation to Overcome Legacy SIEM Lock-In
Automate Multi-SIEM Processes to Cut Costs and Operationalize Data Migration
One customer that Torq spoke with about the recent rumblings in the SIEM landscape is planning to use Hyperautomation as a means to an end of their legacy SIEM contract. Following acquisition of their legacy SIEM provider, they were informed their upcoming renewal would nearly double in price and were considering terminating their relationship. However, their security operations are so embedded and reliant on the legacy SIEM, that evaluating a rip-and-replace would be even more costly – not only financially (~2x), but also in labor hours and anticipated security risk. The decision was made to renew and accept the reality that there was nothing they could do about it. That is, until they realized the power of applying their existing Hyperautomation practices towards a multi-SIEM strategy. By running Torq as a layer sitting above both their legacy SIEM and a new next-gen SIEM, focused on cost-efficient data processing in the cloud, they are able to automate parallel processes, realize significant operational cost-savings, and reallocate funds to migrating regulated data from their on-prem storage at a much faster rate than they could previously afford.
The SIEM landscape is rapidly evolving, and at a much faster rate than organizations can plan to remove their sensitive data and get out of their increasingly expensive contracts. While many organizations may feel stuck, there is a way forward. As quickly as legacy SIEM solutions are converging, cloud-native SIEM alternatives are evolving – and with Hyperatuomation as the glue holding the SOC together, organizations are finally able to achieve the benefits of a modern SOC architecture.
Ready to escape SIEM lock-in? Torq enables the Modern SOC to store data anywhere, and operationalize it with Hyperautomation. Get a demo today.