“Purpose-built does not scale.” That’s what IDC says in its latest research report “How Hyperautomation Is Used to Reduce Gaps and Inefficiencies in Network Cybersecurity.”
What does that mean? It means that your monitoring point products, like legacy SOAR, just don’t cut it any longer. They can’t scale in today’s hybrid cloud and multi-cloud environments without piling on more tools, further fueling tech stack sprawl.
The report notes that SOAR, SIEM, XDR, and EDR were conceived as on-premises solutions and security’s shift left – the idea that security begins at the time of code development – was not considered. This creates an inherent inability to scale. Additionally, the tools are often too complex and their effectiveness has dwindled in today’s modern, often cloud-based, security environments.
“No matter how you slice it, the cybersecurity platform strategies of today are holding on by a narrow margin. Too many processes are still being done manually,” IDC Research Vice President, Security & Trust Products Christopher Kissel writes, later adding, “Without continually adding new point products and appliances (which also take time to install), none of the current detection and response platforms are going to scale no matter how experienced or disciplined a security operations team is. “
But all is not lost. Hyperautomation and its many benefits can help pull enterprises out of the legacy point product pit of despair.
The IDC report notes that hyperautomation enables:
- Visibility and control of the heterogeneous network real estate, and all environments and for all processes and role players.
- The ability to predict security gaps, proactively assess the network, and ultimately secure the network.
- Proper contextual awareness including more than security logs (firewall, NetFlow, antivirus, etc.), and integration fabrics
- Automation of everything that can and should be automated
- Extensible capabilities using no code, low code, or full code with potential leveraging of generative AI to automate even more tasks.
How does that stack up against legacy SOAR? Here’s IDC’s breakdown:
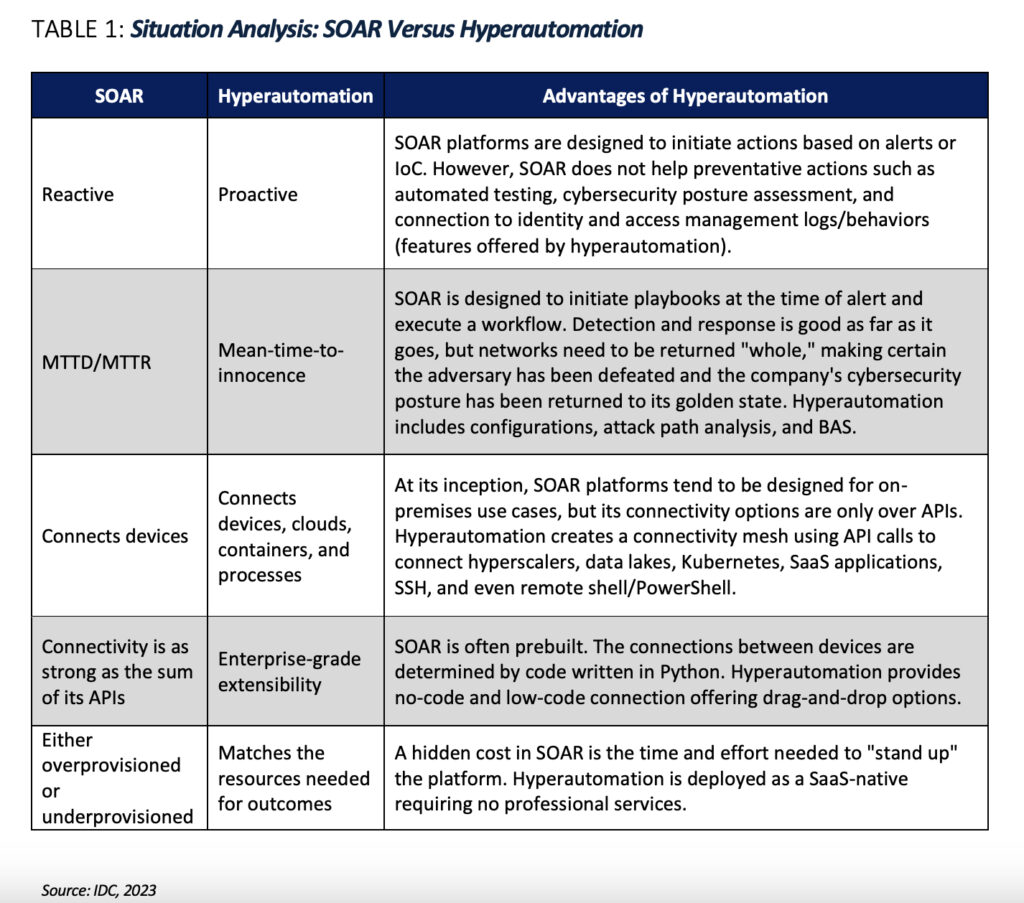
According to the IDC report, hyperautomation is proactive, where legacy SOAR is reactive; hyperautomation connects devices, clouds, containers, and processes, where legacy SOAR connects devices; hyperautomation delivers enterprise-grade extensibility, where legacy SOAR offers connectivity only as strong as the sum of its APIs; and hyperautomation matches the resources needed for outcomes, while legacy SOAR has to either be over- or under-provisioned.
And when it comes to hyperautomation, Torq is leading the charge.
“The Torq hyperautomation approach is more comprehensive than what is offered in contemporary cybersecurity tooling,” the report states, adding “ Torq provides an end-to-end visibility, prevention, and detection application that entails the entire digital estate of a business.”
Don’t just take our word for it. Read the full IDC report, “How Hyperautomation Is Used to Reduce Gaps and Inefficiencies in Network Cybersecurity,” and you’ll see how Torq Hyperautomation is beating legacy SOAR.








