Contents
Meet Torq Socrates and learn how a Large Language Model (LLM)-powered AI SOC Analyst can revolutionize SecOps.
Artificial intelligence (AI) in the SOC has generated significant hype in recent years, and separating the promise from reality can be challenging. However, at Torq, AI is not just a concept — it is a reality that is revolutionizing the SecOps field, specifically in the area of Tier-1 security analysis.
This is increasingly important as cybercriminals become more sophisticated in their tactics and techniques, including using AI to launch attacks at scale. Traditional security tools continue to fall short in detecting and mitigating modern attacks effectively, driving the need for AI-powered autonomous SOC solutions that can reduce the burden on human analysts and shore up defenses.
Introducing Torq Socrates, the AI SOC Analyst
Torq Socrates, the AI SOC analyst, introduces dramatic new efficiencies and incident response accuracy by hyperautomating key security operations activities using AI. This alleviates security analysts’ critical challenges, including alert fatigue, false positives, decreased visibility, and job burnout. Socrates is an AI Agent based on cutting-edge Large Language Models (LLMs) and Generative AI that intelligently analyzes and understands organizations’ unique SOC playbooks to become an integral extension of their SOC teams.
Imagine having a bird’s-eye view of your complete enterprise environment from on-premise, hybrid to full SaaS applications, with all the relevant information at your fingertips. Torq Socrates makes this dream a reality by utilizing the security tooling already connected to the Torq Hyperautomation platform and performing any actions and activities only when explicitly authorized.
What is an AI SOC Analyst?
An AI SOC Analyst, sometimes known as an “AI SOC Agent”, can serve as an extension of SOC teams that automates incident response by interpreting natural language instructions in security runbooks to execute tasks such as alert triage, containment, and remediation actions. Human analysts remain in control of the processes and critical decisions and can interface with AI agents using natural language for additional enrichment, investigation, and recommended next steps.
AI SOC Analysts are a key component of an AI-powered SOC.
How an AI SOC Analyst Uses LLMs to Perform Tier-1 Tasks
So, how does this transformation happen? Let’s journey through a typical security event and see how tasks previously handled by human analysts are now handled with unprecedented efficiency by Torq’s AI SOC Analyst, Socrates.
1. Automatic Runbook Analysis
When a security event arises, an analyst traditionally consults a “runbook” – a guide specifying the response to that specific type of event. Today, these “runbooks” exist in all modern SOCs and are prepared by senior architects to benefit Tier-1 and Tier-2 analysts.
Torq Socrates automatically analyzes runbooks written in natural language, typically containing step-by-step procedures for handling various security incidents. By analyzing the semantic meaning of the natural language instructions, the AI SOC Analysts derives action flow from the recommended response strategies for different security events.
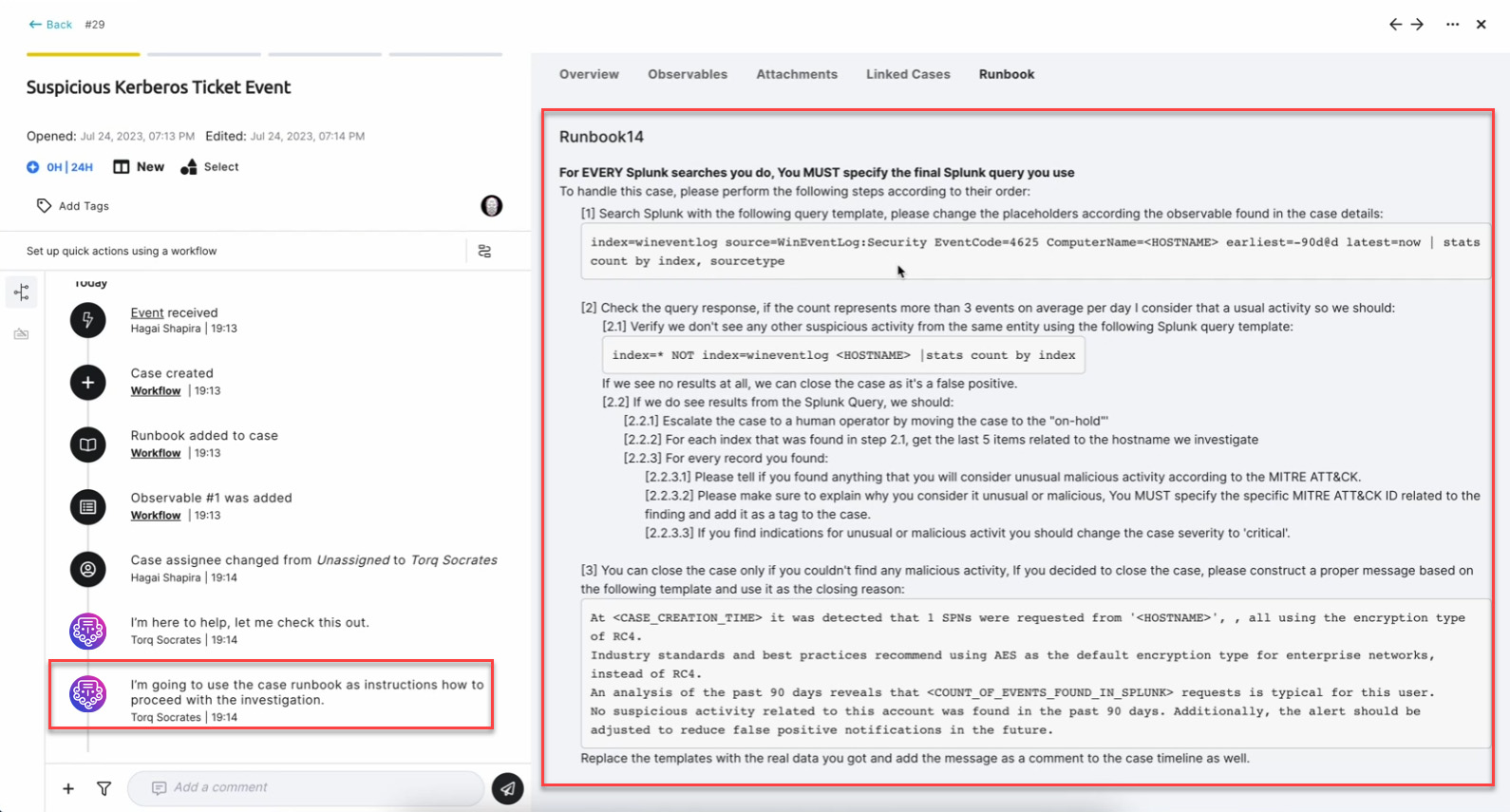
2. Workflow Choice to Perform the Designated Runbook Actions
The next step for a human analyst is to carry out the activities outlined in the runbooks, choosing the proper tool and executing the instructions.
Based on the content of the runbook, the AI SOC Analyst utilizes its semantic analysis capabilities to suggest suitable workflows and security tools from the list of ones explicitly made available inside the Torq platform. These workflows align with the specific steps outlined in the document conveyed in natural language.
Each workflow made available to Torq Socrates comes with a natural language description of the tasks it can accomplish.
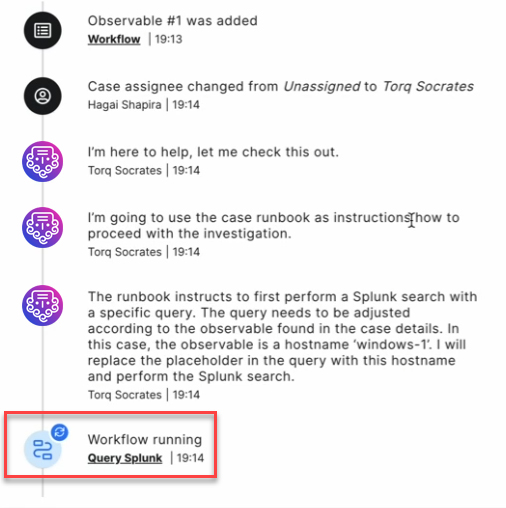
3. Interpreting the Outcome of Executed Actions to Follow the Next Step Prescribed by the Runbook
Various security tools available in the arsenal of Tier-1 SOC analysts can return a large amount of detailed information. The analyst’s goal is to try and synthesize this information into a decision about which next steps should be taken according to the runbook’s guidance.
An LLM-powered AI SOC Analyst like Socrates excels at processing both structured and unstructured security tool data. This enables it to analyze complex information and create dynamic decision trees based on runbook analysis. These decision trees adapt to the specific context of each incident, allowing for more efficient and accurate incident handlingFor example, Socrates can determine: Is the file malicious? Is the user a very important person (VIP)? Is the activity frequent or infrequent during a specific time period indicating anomalous behavior?
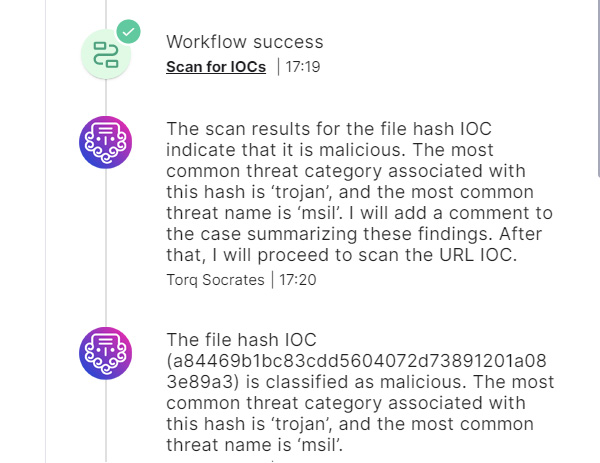
4. Leveraging Knowledge of Security Frameworks for Context
More experienced alert triage specialists bring their own contextual knowledge and understanding of networking, endpoint architecture, and attack techniques into the mix.
LLMs are trained on an immense body of natural language documents containing information about the above and more. This allows the semantic analysis of an LLM to match between the observed outcome of a security tool and the technique described in a documented framework, such as the MITRE ATT&CK framework.
Using the above technique, Torq’s AI SOC Analyst Socrates leverages the information available in numerous documents describing attack frameworks, such as the MITRE ATT&CK framework, and maps its tactics and techniques to the outcomes observed in the security event being analyzed.
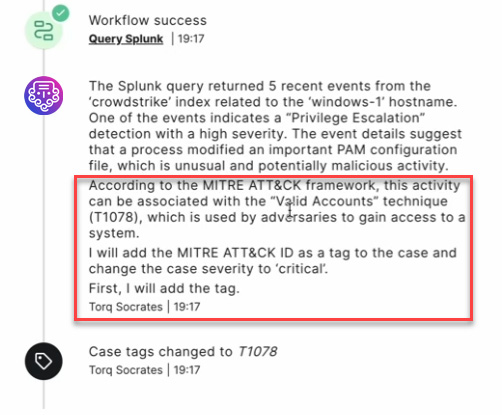
5. Automated Incident Investigation
Just as human analysts rely on insights from the runbook, Socrates can assist in automating investigation or even incident response tasks. This includes executing tasks such as alert triage, data enrichment, containment, and remediation actions, which speeds up response times and reduces the manual effort required from analysts.
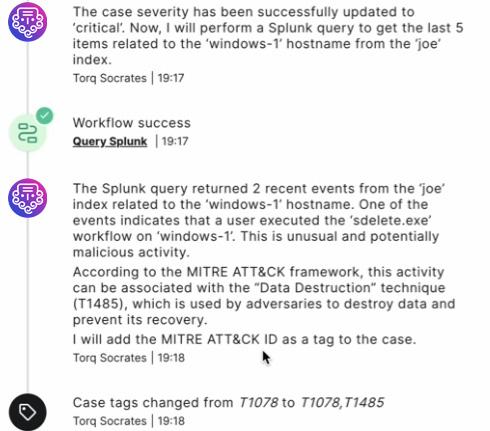
6. Summarizing Relevant Security Case Information
An important pillar of any operational practice is meticulous documentation of all actions taken, decisions, and achieved outcomes.
LLMs have proven to be efficient at rephrasing and summarizing large amounts of natural language text. Torq Socrates leverages this capability to summarize the “conclusions” and desired next steps, and document them in the “case timeline.”
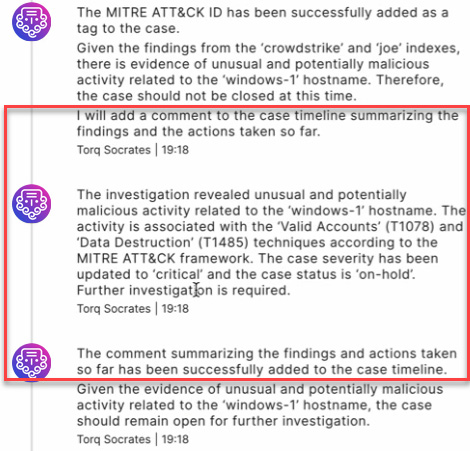
Reducing the Burden on Tier-1 SOC Analysts with AI
Here’s a summary of how Torq Socrates uses powerful LLMs to perform Tier-1 SOC analyst duties:
| Human Tier-1 Analyst | AI SOC Analyst |
| 1. Tier-1 analysts work strictly according to defined runbooks | 1. LLMs effectively analyze natural language text to and break runbooks down into components. |
| 2. Analysts match directives from the runbooks with tools at their disposal. | 2. LLMs are effective at finding similarities, in this case, between a “desired action” and an “available tool to execute this action.” |
| 3. Analysts digest the output of different tools to choose the correct follow-up course of action. | 3. LLMs semantically analyze the output of different tools and match it to the runbook directives related to follow-up steps. |
| 4. Analysts can bring in context from their training. | 4. LLMs can load related context from the myriad of documents scanned during the model’s training. |
| 5. Analysts are required to document all actions taken and the reasoning behind the conclusions. | 5. LLMs summarize the matches made and audit all the performed activities. |
Torq Socrates is designed to handle up to 90% of Tier-1 triage actions by mapping the tasks and activities of human Tier-1 analysts to use cases leveraging LLMs. With Torq Socrates as their AI SOC Analyst, human security analysts remain in charge of processes and outcomes. The AI-powered system introduces dramatic new efficiencies and incident response accuracy, alleviating security analysts’ most critical challenges.
Get the latest on Torq’s AI capabilities >