Contents
Get a Personalized Demo
See how Torq harnesses AI in your SOC to detect, prioritize, and respond to threats faster.
Security Operations Centers (SOCs) continue to struggle in 2025. The perfect storm of growing alert volume, consistent talent shortage, and the well-documented limitations of legacy SOAR solutions have brought many SOC teams to a breaking point. At the same time, bad actors continue to innovate, and cybercriminals have become more sophisticated in their tactics and techniques, including using AI to launch attacks at scale.
Fortunately, AI in the SOC has begun to revolutionize the security operations field, specifically in the area of Tier-1 security analysis. According to Gartner, “By 2026, AI will increase SOC efficiency by 40% compared with 2024 efficiency, beginning a shift in SOC expertise toward AI development, maintenance and protection.”
Why the SOC Needs an AI Analyst
As alert complexity rises, so does burnout and alert fatigue. SOC analysts today spend too much time sifting through noise and manually triaging alerts, rather than taking action to proactively secure the environment. According to the 2024 SANS Detection and Response Survey, more than half of security teams say false positives are a huge problem, and 62.5% are overwhelmed by sheer data volume.
A major reason for this frustration is that security teams are fighting with their own tools. In a recent State of Security 2025 report, Cisco’s Splunk surveyed over 2,000 security professionals in their community to find:
- 59% spend too much time and/or effort maintaining tools and associated workflows
- 51% admit their tools do not integrate well with one another
- 47% face alerting issues
- 32% of teams do not have the requisite skills to be efficient in the SOC
Tier-1 alert triage is overwhelming. Analysts face tens of thousands of Tier-1 alerts per day, and on average, security analysts are only getting to half of the alerts they’re supposed to review. Combined with these SOC inefficiencies, the volume becomes too high for human-only triage. As a result, detection and response times suffer. Gartner says, “AI agents are emerging as a critical solution to enhance efficiency, reduce burnout, and enable teams to focus on strategic initiatives.”
Enter Torq Socrates — the agentic AI SOC Analyst designed to dramatically offload Tier-1 workloads and lead organizations toward an autonomous SOC.
What is an AI SOC Analyst?
An AI SOC Analyst serves as an extension of SOC teams, automating incident response by interpreting natural language instructions in security runbooks to execute tasks such as alert triage, containment, and remediation actions. While an AI SOC Analyst autonomously handles over 90% of Tier-1 tasks, human analysts remain in control of critical decisions and can interface with the AI SOC Analyst using natural language for additional enrichment, investigation, and recommended next steps.
Learn unconventional criteria for evaluating AI SOC analysts >
What Is Torq Socrates?
Socrates is Torq’s agentic AI SOC Analyst — a self-deterministic, autonomous AI Agent that plans, reasons, and acts the way a human SOC analyst would. Unlike SOAR solutions or common Generative AI chatbots, Socrates does not require human instruction or guidance. Socrates understands the SOC objectives and executes complex actions with minimal oversight.
Legacy SOAR and generic workflow automation solutions offer AI chatbots that run on static, rule-based playbooks — controlled by human input. And, while GenAI augments case triage by generating context to help reduce detection and response times, it is still largely reactive and reliant on human analysts to instruct, guide, and manually trigger remediation actions. Agentic AI, on the other hand, represents the next leap towards a more autonomous SOC.
According to IDC’s latest report, agentic AI has enormous potential in cybersecurity as it can process and solve problems the way a human being would. Socrates isn’t reactive — it’s adaptive. To continuously improve and evolve with new threats, Socrates uses:
- Semantic memory to understand prompts and take explicit action
- Episodic memory to learn from past incidents to develop new strategies
- Procedural memory to make decisions on which tools to use and which data to gather
The Anatomy of Socrates: Torq’s OmniAgent
Socrates is more than just a single AI Agent. Socrates sits at the helm of Torq’s Multi-Agent System (MAS), acting as an OmniAgent in charge of coordinating multiple specialized AI Agents. Each of these agents is trained to perform a specific task, and is capable of using sophisticated iterative planning and reasoning to solve complex, multi-step problems autonomously. Torq’s AI Agents include:
- Runbook Agent: Autonomously plans and adapts incident response runbooks with a deep knowledge and understanding of the environment.
- Investigation Agent: Performs deep-dive investigations in seconds, uncovering hidden patterns across disparate data sources and tools to pinpoint root causes and assess threat impact.
- Remediation Agent: Executes remediation actions, closing the loop with verifiable outcomes, either by autonomously following the associated runbook or through human-in-the-loop response.
- Case Management Agent: Gathers real-time and historical data, organizes case timelines, highlights key indicators, and reprioritizes incidents based on evolving information.
This agentic AI architecture is supported by first in class Retrieval-Augemented Generation (RAG) and Model-Context Protocol (MCP) technology that helps the Torq MAS dynamically accelerate SecOps outcomes by improving detection and triage accuracy, while reducing MTTD and MTTR.
How an AI SOC Analyst Performs Tier-1 Tasks
So, how does Socrates leverage Torq’s MAS to perform Tier-1 security tasks? Let’s look at this Command and Control attack detected by Crowdstrike and see how tasks previously handled by human analysts are now handled with unprecedented efficiency by Torq’s AI SOC Analyst, Socrates.
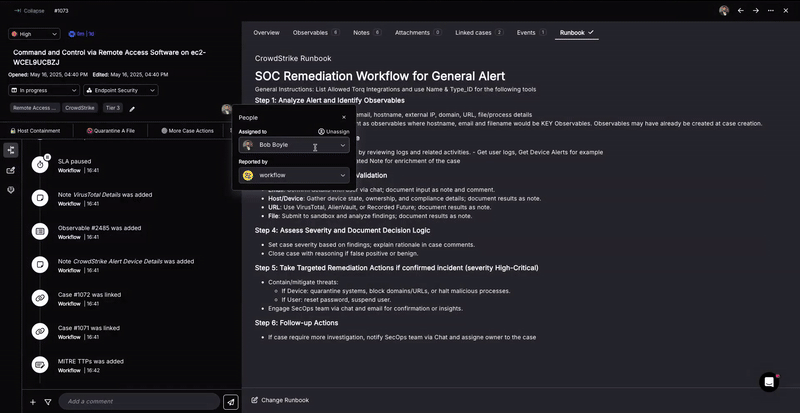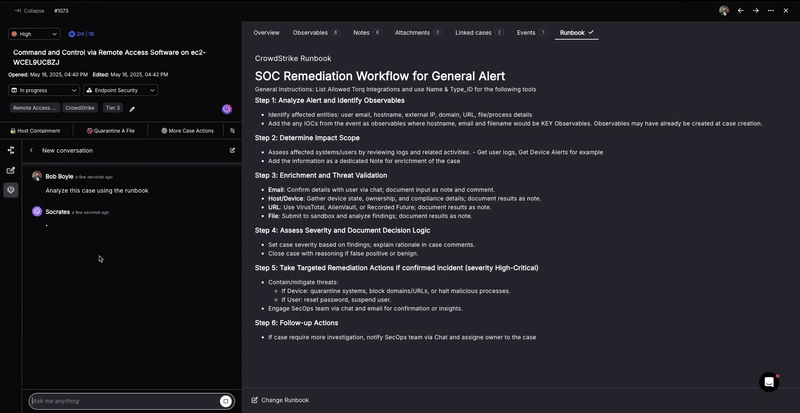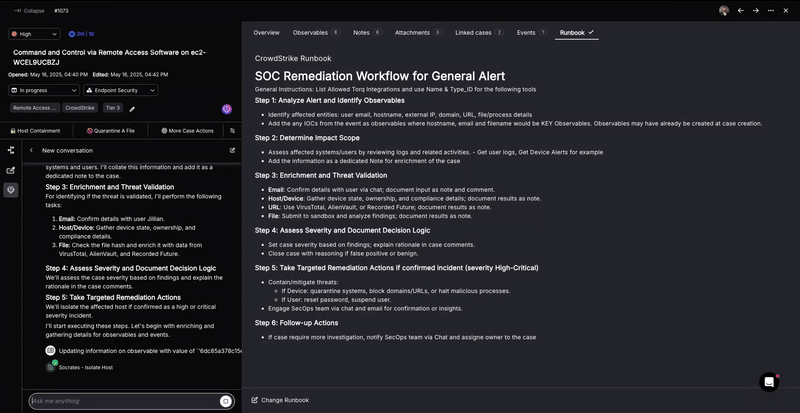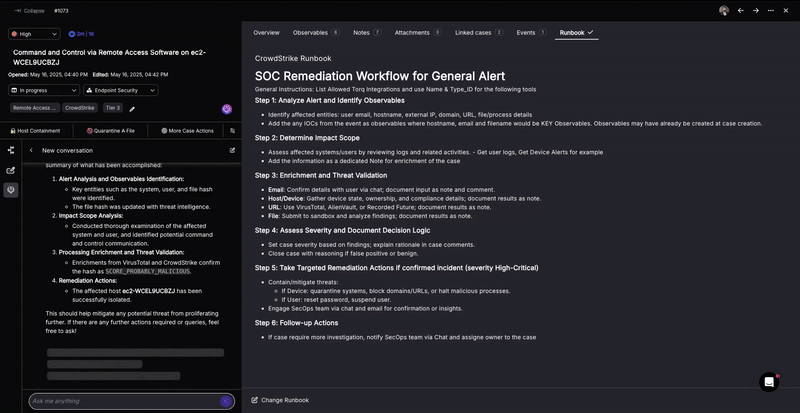
1. Automatic Runbook Analysis
When a security event arises, an analyst traditionally consults a “runbook” – a guide specifying the response to that specific type of event. Today, these “runbooks” exist in all modern SOCs and are prepared by senior architects to benefit Tier-1 and Tier-2 analysts.
Torq Socrates looks at outcomes of historical cases and associates the appropriate runbook based on the observables of the new case. Socrates automatically analyzes runbooks written in natural language, typically containing step-by-step procedures for handling various security incidents. By analyzing the semantic meaning of the natural language instructions, the AI SOC Analyst derives action flow from the recommended response strategies for different security events.
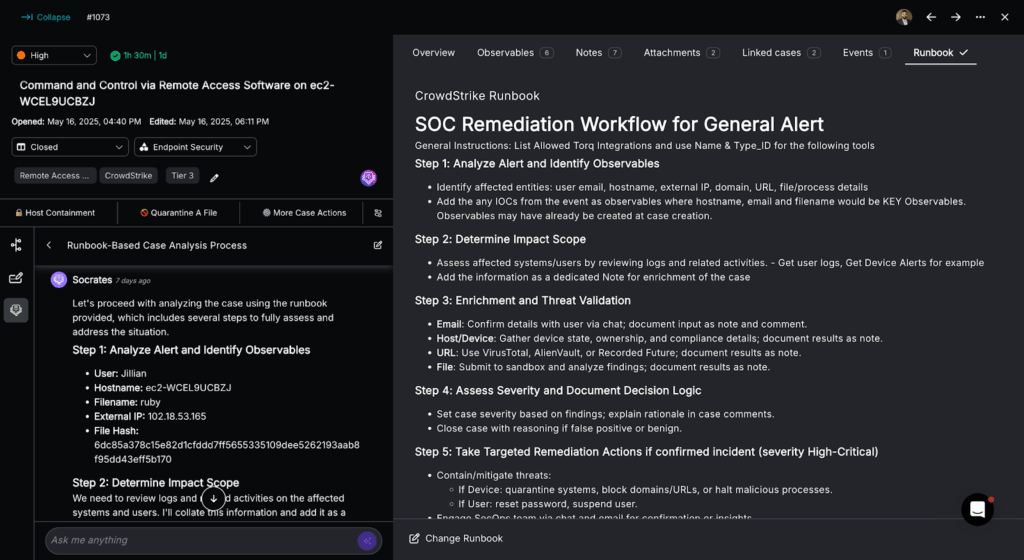
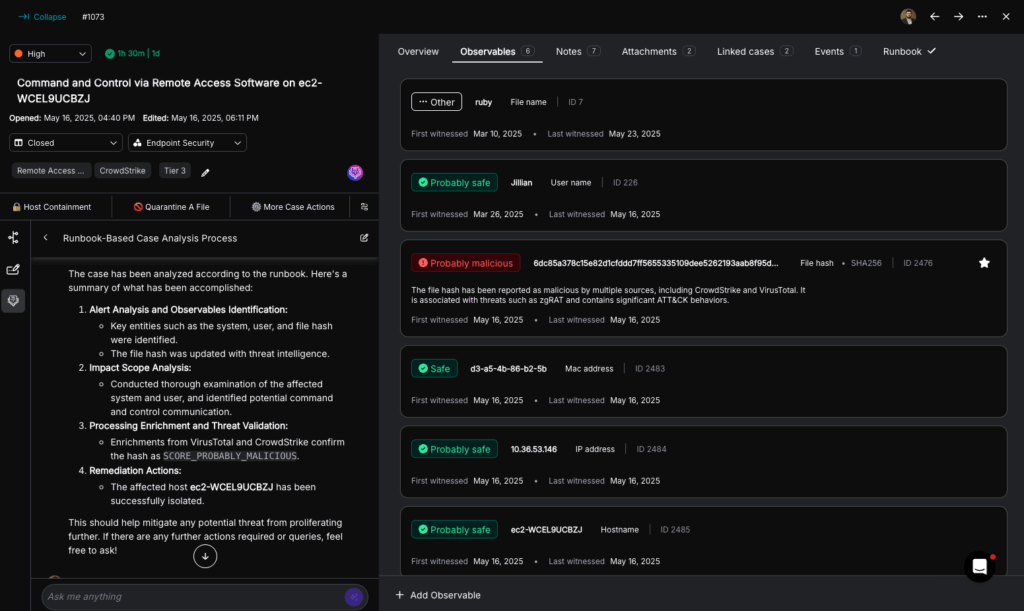
2. Deep Research Incident Investigations
The many security tools available in the arsenal of Tier-1 SOC analysts can return a large amount of detailed information. The analyst’s goal is to synthesize this information into a decision about which next steps to take, according to the runbook’s guidance.
Just as human analysts rely on insights from the runbook, Socrates can assist in automating investigation or even incident response tasks. This includes executing tasks such as alert triage, data enrichment, containment, and remediation actions, which speeds up response times and reduces the manual effort required from human analysts.
An agentic AI SOC Analyst like Socrates excels at processing both structured and unstructured security tool data. This enables it to analyze complex information and create dynamic decision trees based on runbook analysis. These decision trees adapt to the specific context of each incident, allowing for more efficient and accurate incident handling. For example, Socrates can determine: Is the file malicious? Is the user a very important person (VIP)? Is the activity frequent or infrequent during a specific time period indicating anomalous behavior?
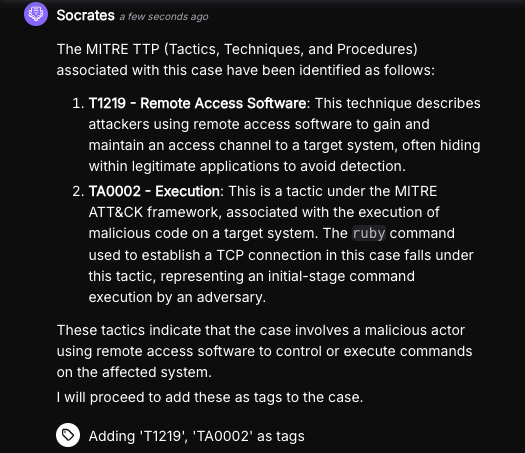
3. Knowledge of Security Frameworks for Context
More experienced alert triage specialists bring their own contextual knowledge and understanding of networking, endpoint architecture, and attack techniques into the mix.
AI Agents are trained on an immense body of natural language documents containing information about the above and more. This allows the semantic analysis of an AI Agent to match the observed outcome of a security tool and the technique described in a documented framework, such as the MITRE ATT&CK framework.
Using the above technique, Torq’s agentic AI SOC Analyst, Socrates, leverages the information available in numerous documents describing attack frameworks, such as the MITRE ATT&CK framework, and maps its tactics and techniques to the outcomes observed in the analyzed security event.
4. Leveraging Hyperautomation to Perform Designated Remediation Actions
The next step for a human analyst is to carry out the remediation actions outlined in the runbooks, choosing the proper tool and executing the instructions.
Based on the content of the runbook, the AI SOC Analyst utilizes its semantic analysis capabilities to suggest and trigger suitable Hyperautomated workflows and security tools from the list of ones explicitly made available within the Torq platform. These workflows align with the specific steps outlined in the document conveyed in natural language.
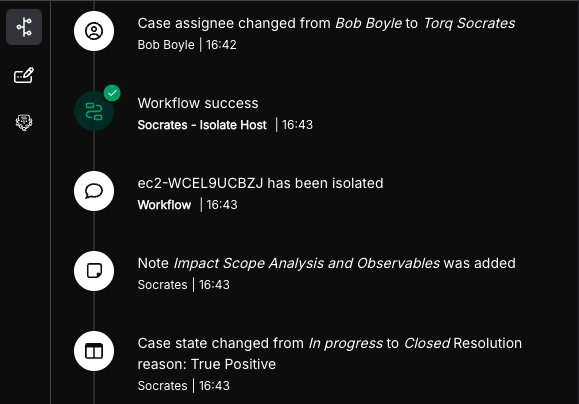
5. Intelligent Case Management and Documentation
An important pillar of any operational practice is the meticulous documentation of all actions taken, decisions, and achieved outcomes.
AI Agents have proven to be efficient at summarizing large amounts of natural language text. Torq Socrates leverages this capability to summarize the “conclusions” and desired next steps, and document them in the “case timeline”. Socrates then reaches back into its toolbox and ability to take action autonomously, marking the case as “closed” and moving the case forward without any human intervention.
How Security Teams Use Socrates Today
Gartner forecasts that by 2028, multi-agent AI in threat detection and incident response will rise from 5% to 70%. For Torq customers leveraging Socrates, this is already their reality.
“I believe the successful use of Torq Agentic AI in SOC operations shows up in practical outcomes. With Torq Agentic AI, the answer is yes to questions such as: Are analysts happier? Are they sticking around? Do they have time to focus on more interesting and complex investigations? Are MTTM and MTTR lower? Torq Agentic AI extends and enhances our team so it can make better decisions more quickly — resulting in stronger security all around.”
Mick Leach, Field CISO, Abnormal Security
Socrates isn’t just another tool — it’s another teammate. And it’s changing the way security gets done. With Socrates, security decisions are made with context, fully automated incident response becomes the default, and agentic AI becomes the connective tissue across previously siloed security solutions that enable SOC teams to move from human-in-the-loop to human-on-the-loop.
According to IDC, Torq HyperSOC, powered by Socrates, helps:
- Eliminate over 95% of Tier-1 analyst workload
- Reduce time-to-remediation by 90%
- Increase case handling capacity 3-5x with zero added headcount
Torq Socrates is designed to handle Tier-1 triage actions by mapping the tasks and activities of human Tier-1 analysts to use cases leveraging agentic AI. With Torq Socrates as their AI SOC Analyst, human security analysts remain in charge of processes and outcomes while introducing dramatic new efficiencies and incident response accuracy, alleviating security analysts’ most critical challenges.
Want to meet Socrates? Request a demo. And get the AI or Die Manifesto to learn strategic considerations and CISO advice for deploying AI in your SOC.