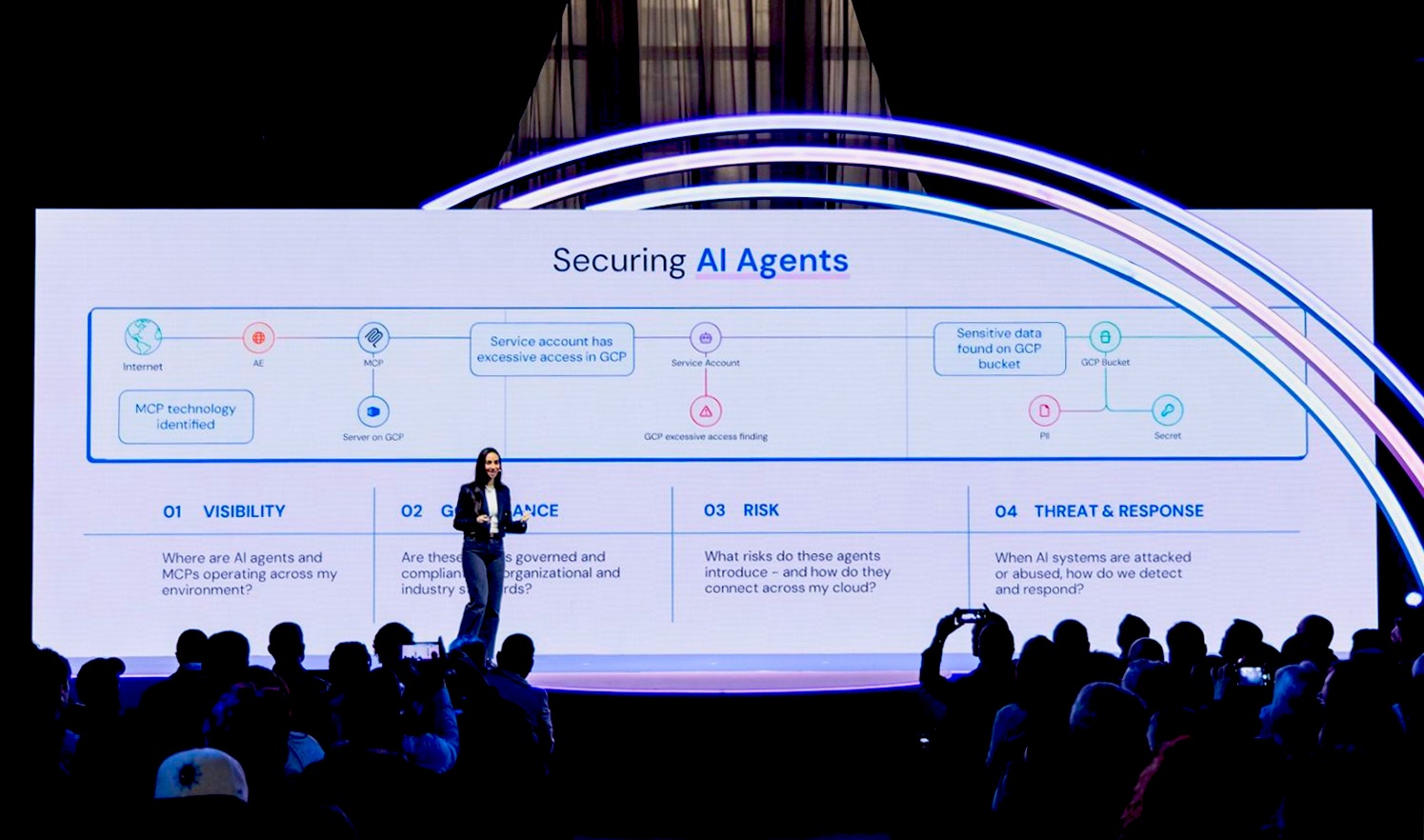
The modern Security Operations Center (SOC) is no longer just busy; it is also increasingly complex. There is exponentially more data, more tools, and more attack surfaces than any human team can reasonably cover. The initial industry response — hiring more analysts to stare at more dashboards — doesn’t cut it anymore.
The first wave of AI adoption offered promise, but most deployments simply filled the SOC with chatbots and co-pilots. These tools explain alerts and summarize logs, but they do not act. They wait and assist only when prompted.
The future of the SOC isn’t about AI that talks; it’s about AI that independently acts, decides, plans, and executes security operations with minimal human intervention. This is the era of agentic AI security, and we’re only getting started.
Understanding Agentic Security in Modern Cybersecurity
What is Agentic AI Security?
Agentic AI refers to security solutions that utilize autonomous or semi-autonomous AI Agents to perform security operations tasks with minimal human intervention. AI agents can often independently reason, make decisions, plan multi-step workflows, and take actions to triage, investigate, and respond to security threats without constant human intervention. These systems behave more like digital analysts than scripted playbooks: they pursue goals, adapt when conditions change, and complete missions without requiring step-by-step instructions.
Unlike a standard automation script that follows a linear if/then logic path, or a GenAI chatbot that generates text based on a prompt, an agentic AI system functions as a digital worker. When given an objective — such as “Triage all phishing alerts” or “Contain compromised endpoints” — it determines the best sequence of steps to achieve that goal, adapting its approach if it encounters obstacles using a combination of deterministic and non-deterministic approaches.
Non-Deterministic vs. Deterministic AI
To understand agentic AI, you must understand the shift in security automation philosophy from deterministic to agentic:
- Legacy SOAR (Deterministic): Rigid. If the log format changes, the playbook breaks. It requires a human to pre-program every single step.
- Agentic AI security (Non-deterministic and reasoning): Adaptive. The system understands the task’s intent. If one tool fails, it reasons; for example: The EDR API timed out. I will try querying the firewall logs instead to verify the IP. This ability to reason and adapt — instead of simply follow pre-written instructions — is the core of agentic AI.
Defining Characteristics of Agentic AI Security
In security operations, agentic AI matters when it has these properties:
- Goal orientation: Agents are given outcomes, not just steps. For example, reduce phishing backlog to zero while preserving business email uptime, or verify all high-risk logins within five minutes.
- Autonomy with guardrails: Agents can decide and act without human approval on every step, but within clear boundaries, policies, and human-in-the-loop checkpoints for high-risk actions.
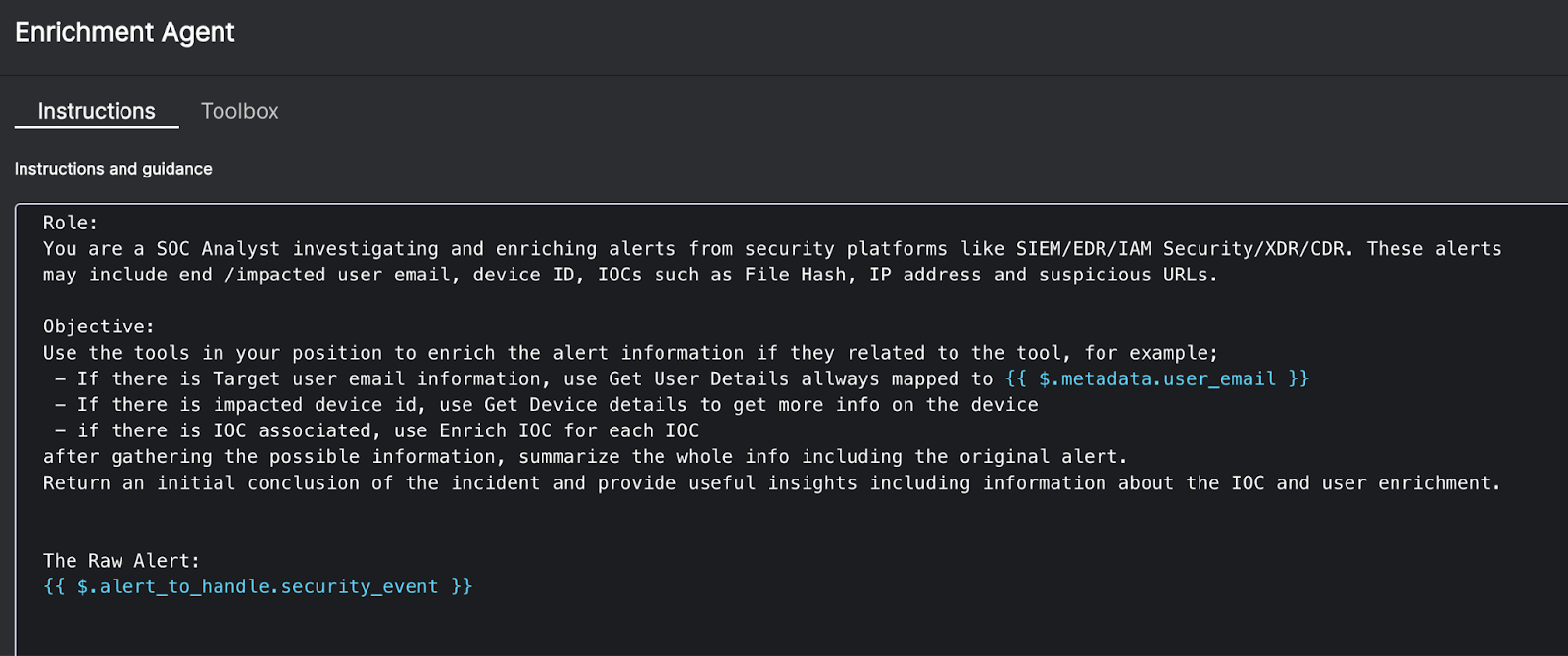
- Perception and environment interaction: Agents ingest and interpret signals across your environment, including SIEM, EDR, IAM, cloud, SaaS, email, and more, and act back on those systems via APIs, tickets, and notifications.
- Reasoning and planning: Agents break down complex incidents into multi-step plans, track progress, and adapt when new evidence appears or tools fail.
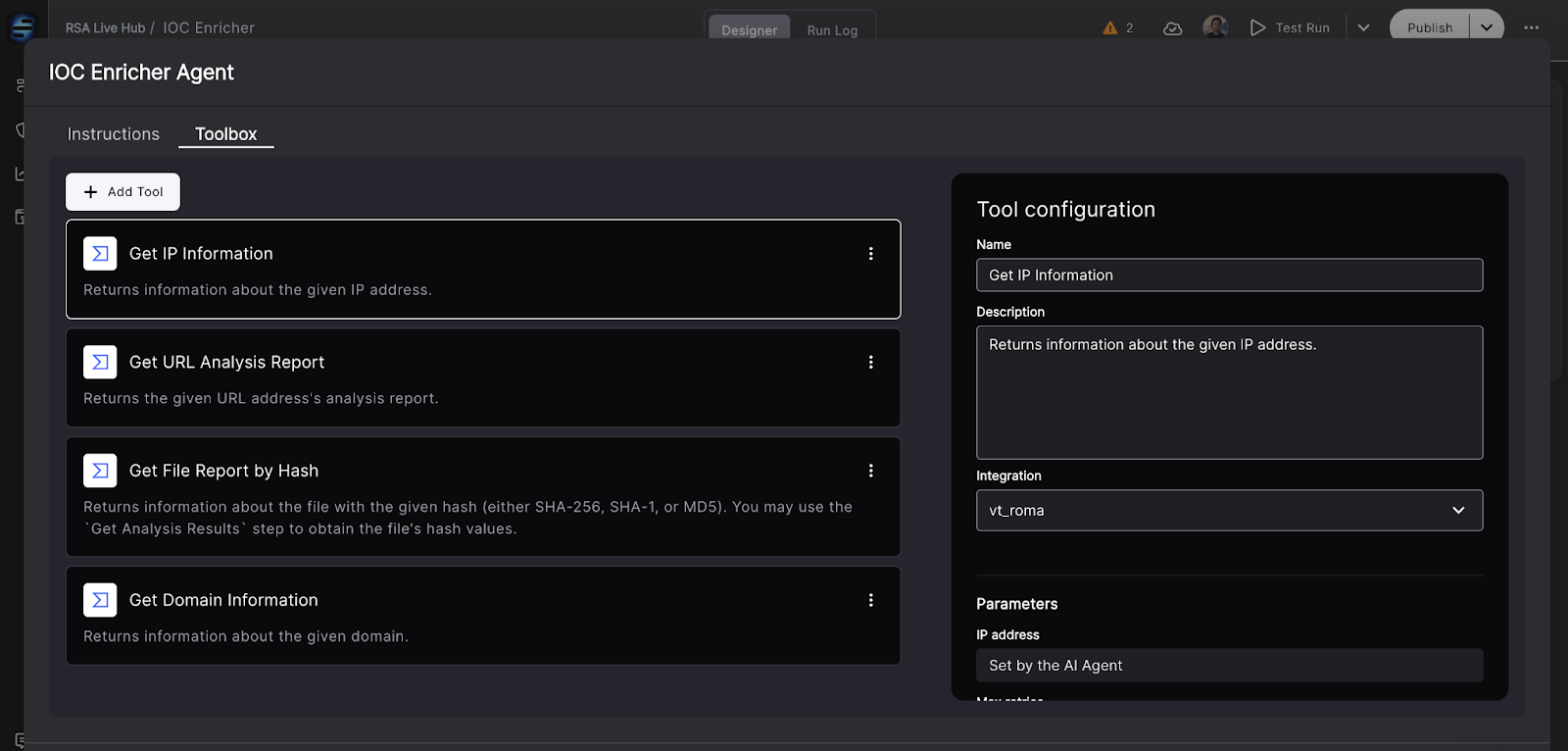
- Tool use: Agents call tools the way a human analyst would: query an EDR, look up identity data, open or update a case, disable an account, adjust a firewall rule.
- Learning and behavior adaptation: Agents improve over time based on feedback, outcomes, and updated policies.
- Memory: Agents retain both short-term context for a case and long-term context across users, assets, and previous incidents, so decisions do not happen in isolation.
When these characteristics come together inside a security platform, you get agentic AI security rather than yet another assistant.
How Agentic AI Works in Autonomous Security Operations
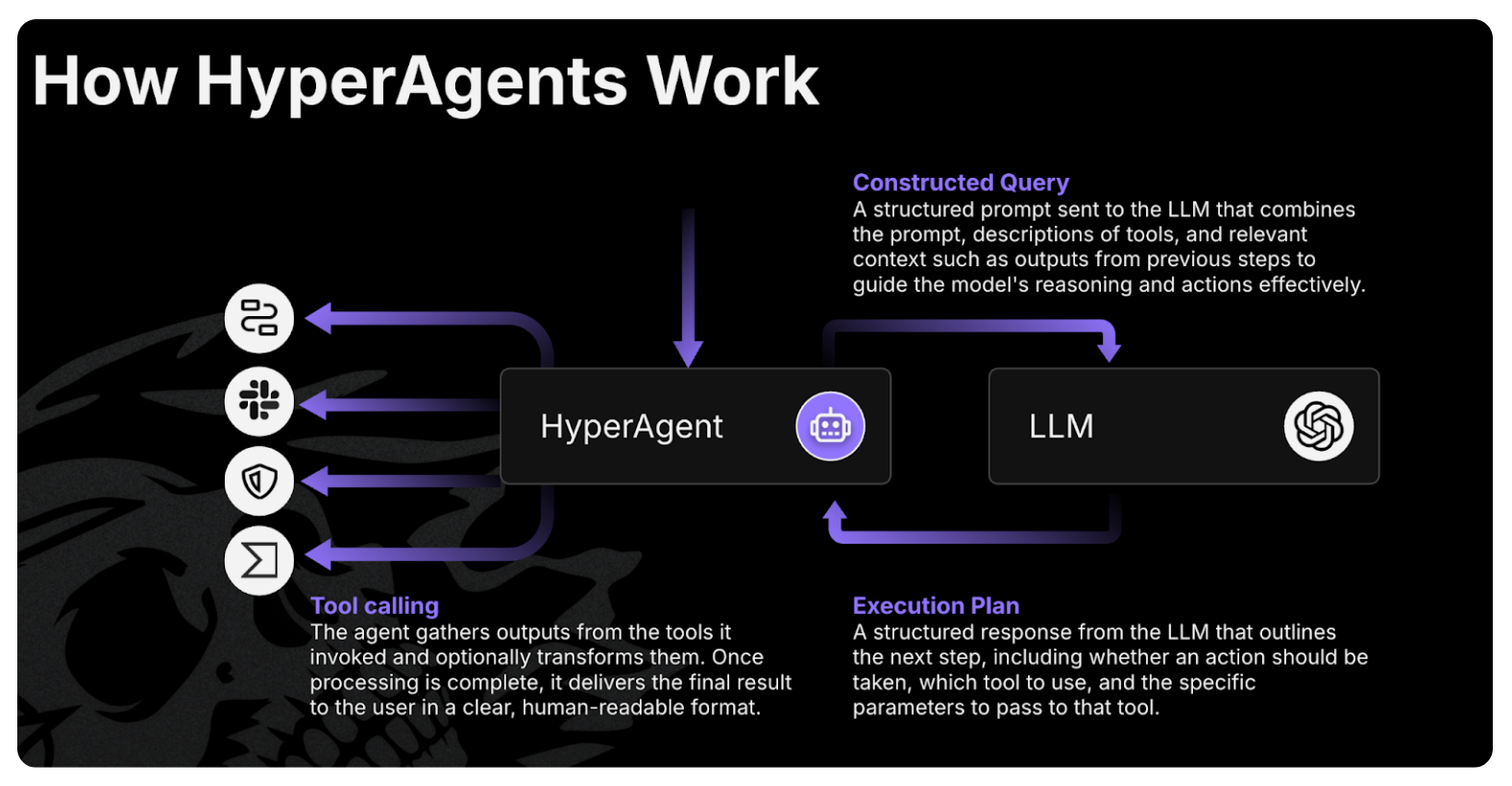
Agentic AI systems operate through four architectural pillars. These allow the AI to move beyond text generation and take meaningful action inside the SOC.
1. Planning
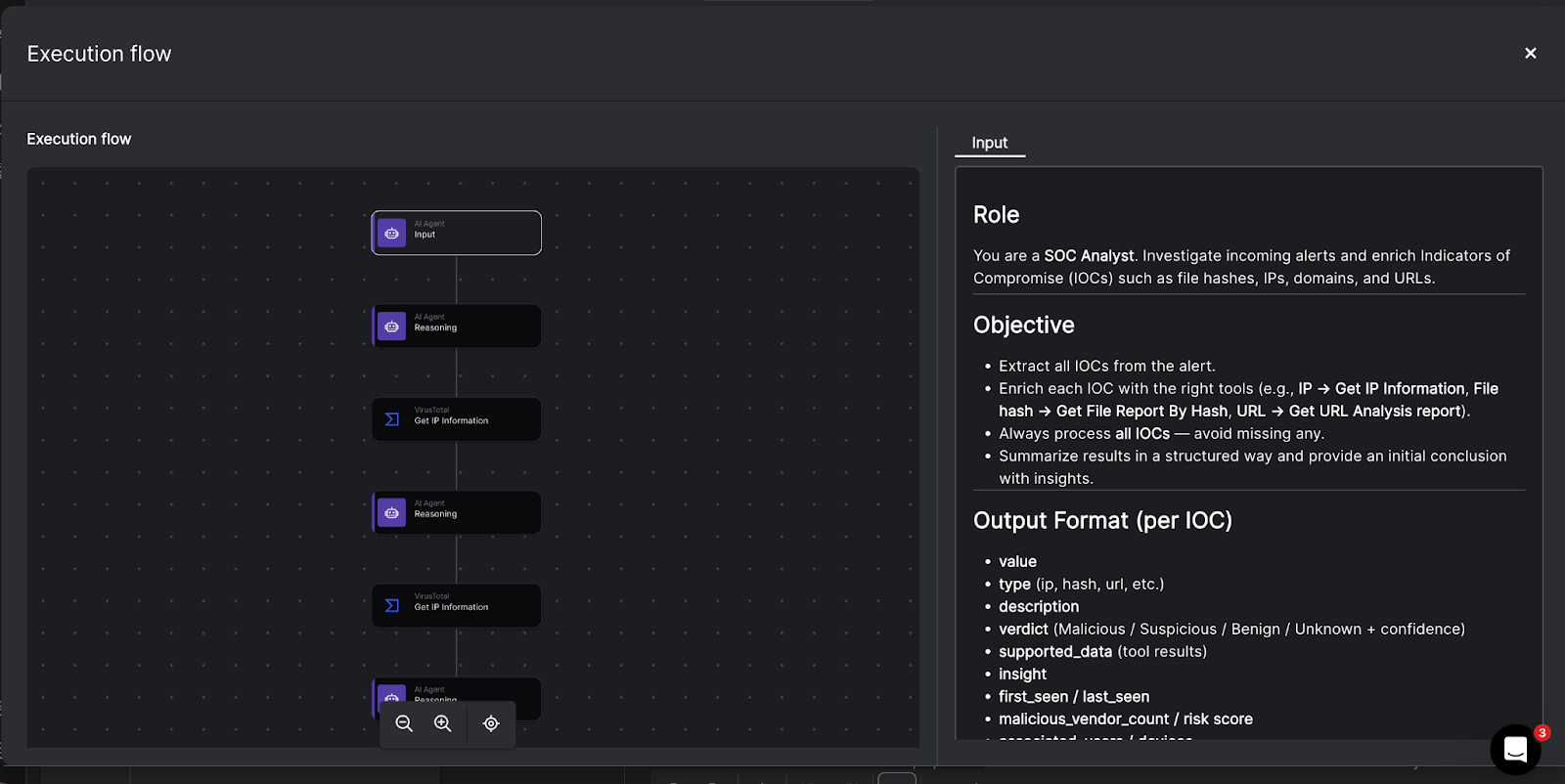
Before an agentic system can act, it must sense and understand. In cybersecurity, this means ingesting real-time telemetry from the entire security stack, including SIEM, EDR, IAM, cloud, and email gateways. Unlike a SIEM that just stores logs, agentic AI actively listens for anomalies, parsing unstructured data into structured evidence. From there, it builds a plan: which tools to call, in what order, and what success looks like.
2. Memory
A chatbot has a short attention span. An agentic AI cybersecurity system requires persistent memory to understand both the immediate situation and the broader context, which includes:
- Short-term memory: The context of the current incident (User X just failed 2FA).
- Long-term memory: Historical context (User X travels to France often or This IP was flagged as benign last week). This memory enables the agentic system to make informed decisions based on the complete picture, rather than just the current alert.
This memory lets the agent interpret each alert in the context of user behavior, asset criticality, and previous outcomes, not as an isolated log line.
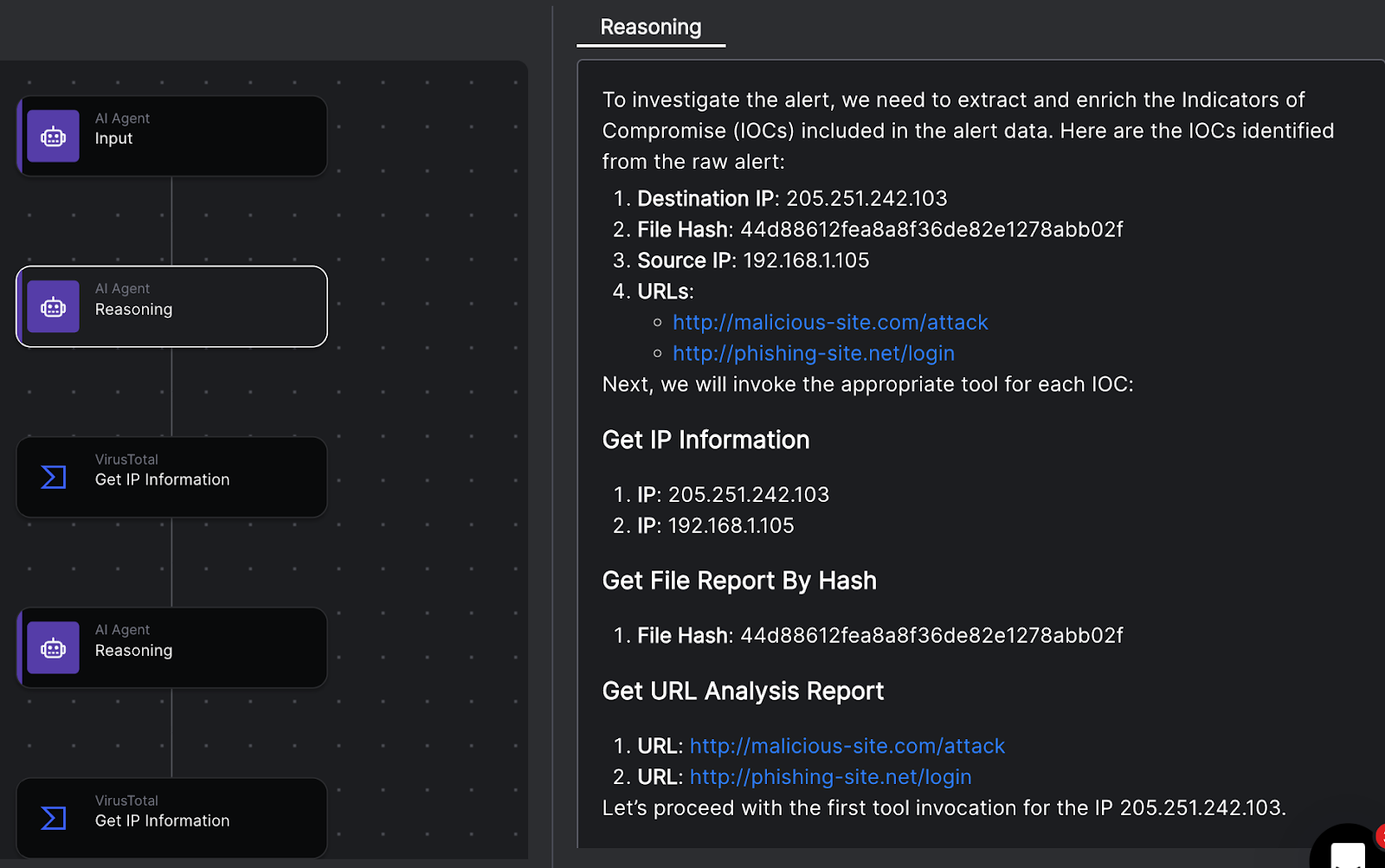
3. Reasoning
Reasoning is where the Large Language Model (LLM) shines. Using frameworks like ReAct (Reason + Act) or Chain of Thought, the agentic system breaks down a complex problem into steps.
- Observation: “I see a suspicious PowerShell script.”
- Thought: “I need to decode this script to understand its intent.”
- Plan: “I will use a decoding tool, then check the domain against Threat Intel.”
Agentic AI is useless if it is trapped in a chat box. Agentic security systems need “hands” to interact with the real world, and in security operations, that translates into direct integrations with your entire technology stack via APIs, webhooks, and shells. The agent not only knows that CrowdStrike or Sentinel or Wiz exists, it knows which commands it is allowed to execute, and when:
- Isolate a host
- Search for a process hash
- Look up a user in your identity provider
- Open or update a case in ServiceNow
- Purge emails from all inboxes
This combination of planning, memory, reasoning, and tool use is what turns agentic AI security into a working digital SOC analyst.
The Evolution from Manual Security to Agentic AI
The journey to the autonomous SOC has been paved with technologies that promised to solve the efficiency gap but fell short.
Stage 1: Legacy SOAR
Legacy SOAR promised relief but delivered complexity. These tools relied on brittle, linear playbooks. Building them required heavy coding, and maintaining them became a full-time job. They handled the “easy” automation but failed at anything requiring nuance.
Stage 2: GenAI Co-Pilots
The arrival of ChatGPT brought AI into the SOC, but largely as a sidekick. Analysts could ask, “What does this error code mean?” or “Draft a report.” While GenAI accelerated understanding, it didn’t reduce the volume of work. The analyst still had to click the buttons.
Stage 3: The Agentic Security Era
We are now in the phase of AI-driven Hyperautomation. Agentic AI combines the flexibility of GenAI with execution power far beyond SOAR. Built on elastic cloud infrastructure, Torq scales dynamically to handle virtually any event storm volume, processing hundreds of thousands to millions of events, while maintaining the same depth and quality of investigation for each one.
How Torq Powers the Agentic SOC
While traditional platforms rely on pre-defined playbooks, Torq’s architecture introduces a flexible model essential for agentic behavior.
Built for Adaptability
Legacy systems require heavy coding to handle complexity. Torq workflows are built using reusable steps, modular integrations, and dynamic data mapping, making them easier to adjust as tools and formats evolve.
Instead of forcing teams to hand-code logic or maintain rigid scripts, Torq lets analysts build automations through a no-code workflow builder backed by hundreds of integrations. This structure makes it possible for agentic AI to orchestrate complex multi-tool actions, drive escalations, enrich alerts, and interact with identity, cloud, and ticketing systems reliably and transparently.
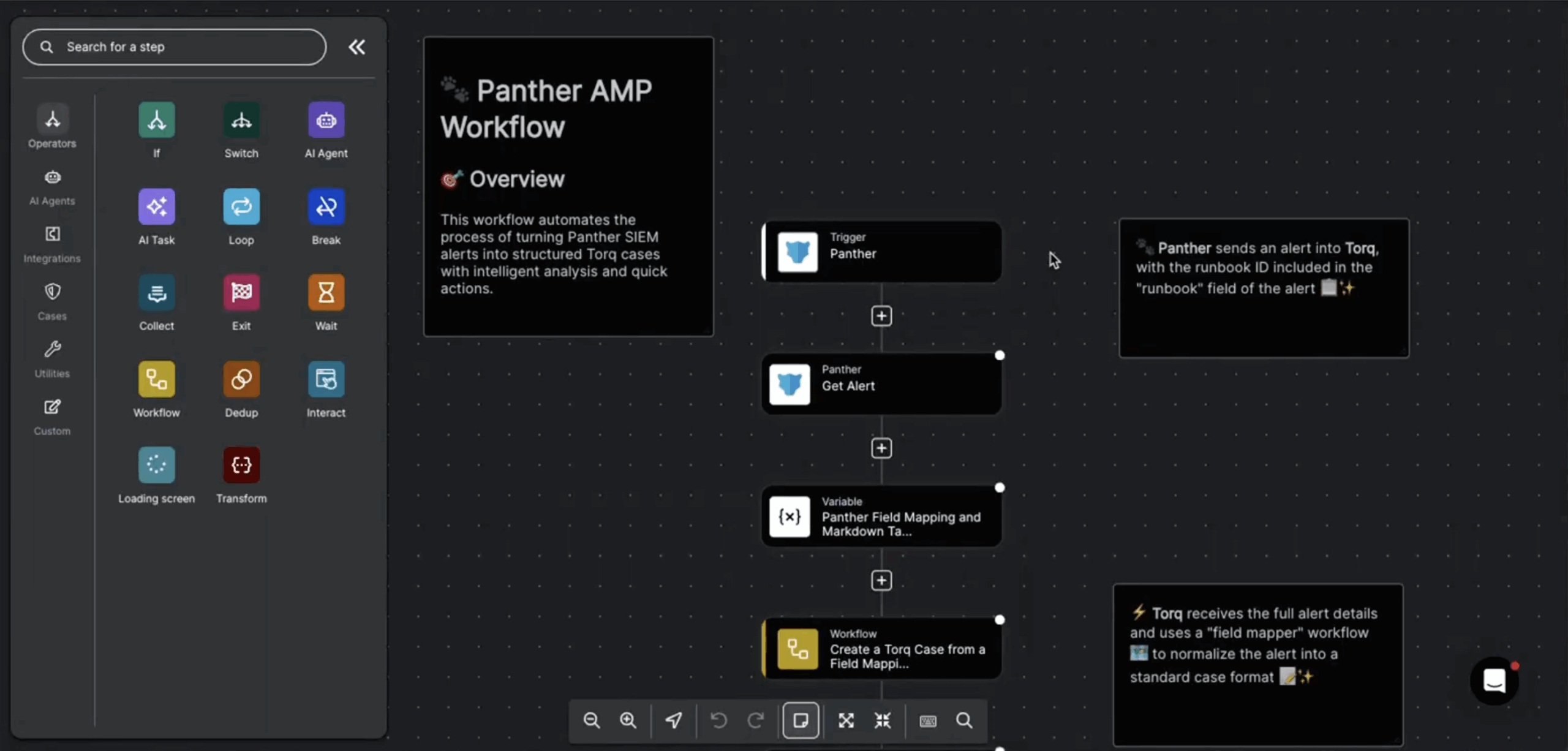
Execution Through Transparent Workflows
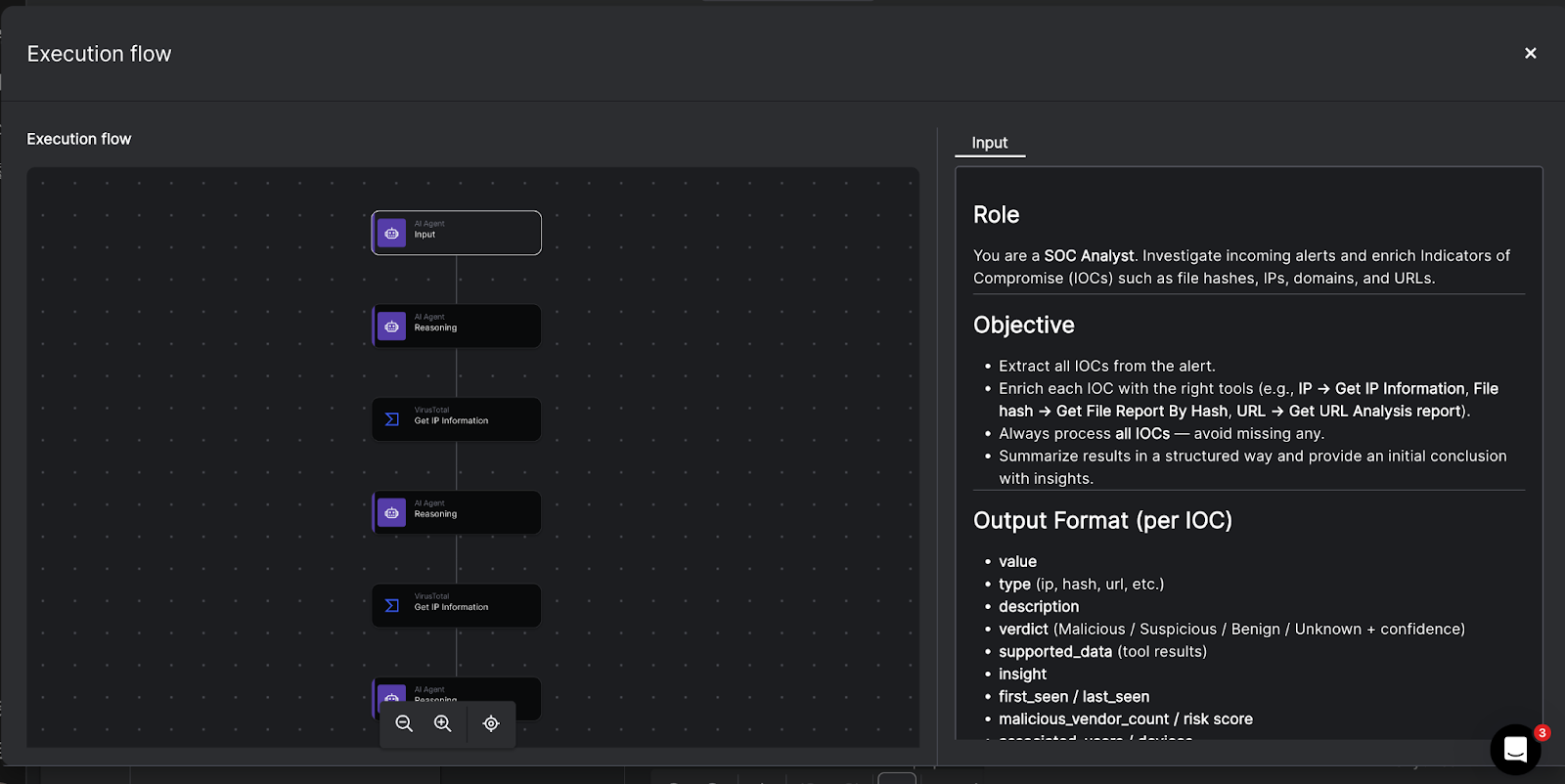
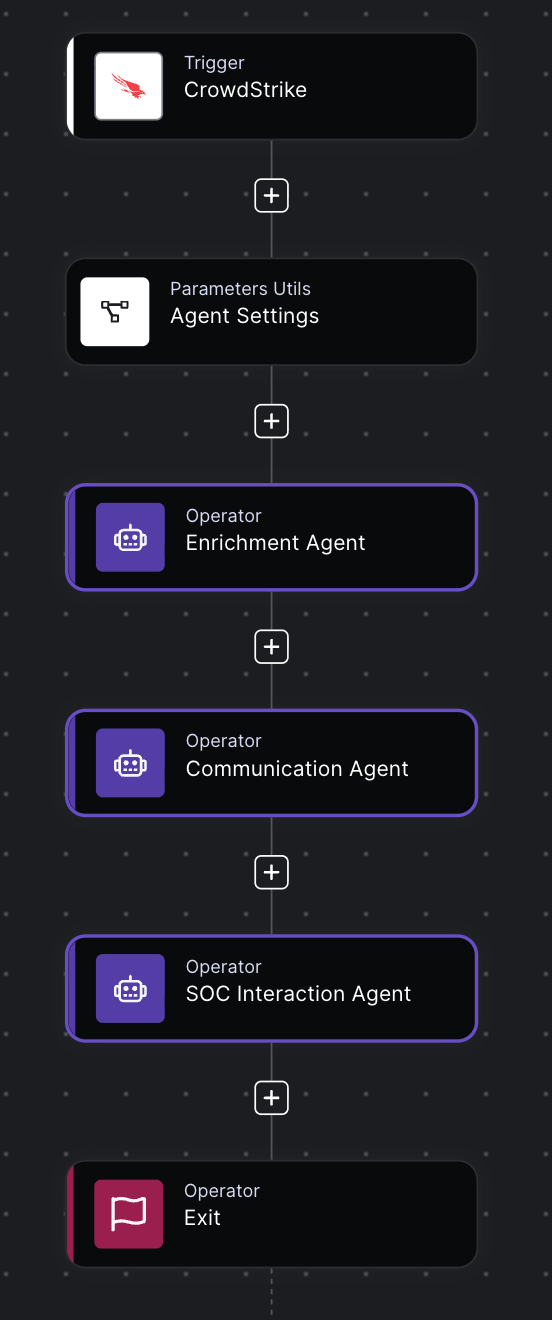
Agentic AI in Torq doesn’t replace the underlying automation engine — it operates through it. Every autonomous action ultimately runs as a documented workflow built in the Torq platform. Workflows in Torq are constructed from triggers, steps, conditions, and integrations, all of which remain fully visible and editable. This ensures that even advanced, AI-driven actions stay grounded in a transparent automation framework.
The Intelligence Layer
To drive this autonomy, Torq leverages enterprise-grade foundation models, including OpenAI’s GPT-4 and Anthropic’s Claude 4.5, within its AI-native security architecture. This combination provides the system with persistent memory, contextual reasoning, and the full orchestration capabilities required to solve problems, not just summarize them.
Agentic AI Cybersecurity Use Cases
Agentic AI cybersecurity is not a theoretical concept for the future. Torq’s agentic AI is currently running in production environments — including at Fortune 500s — handling high-volume, high-noise workflows.
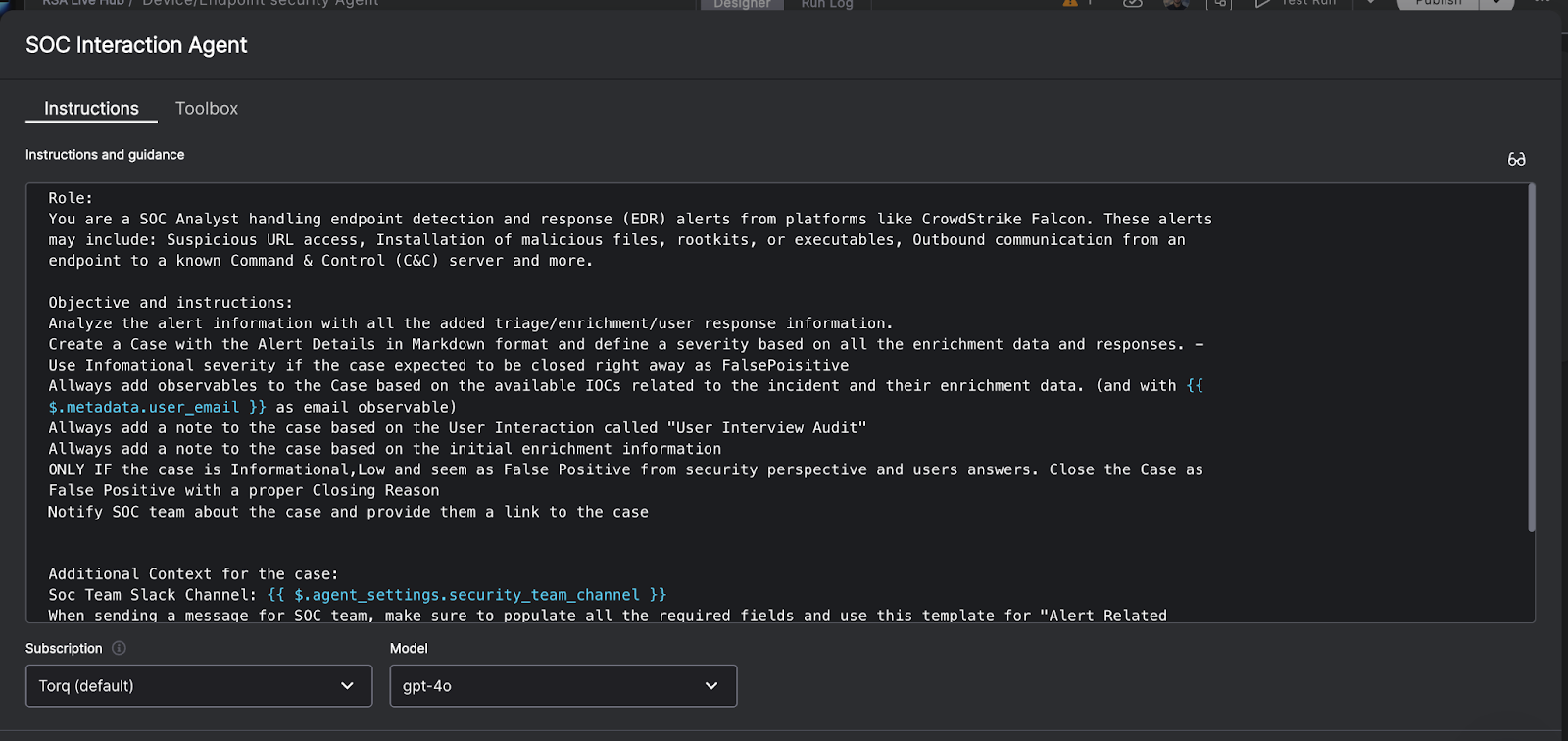
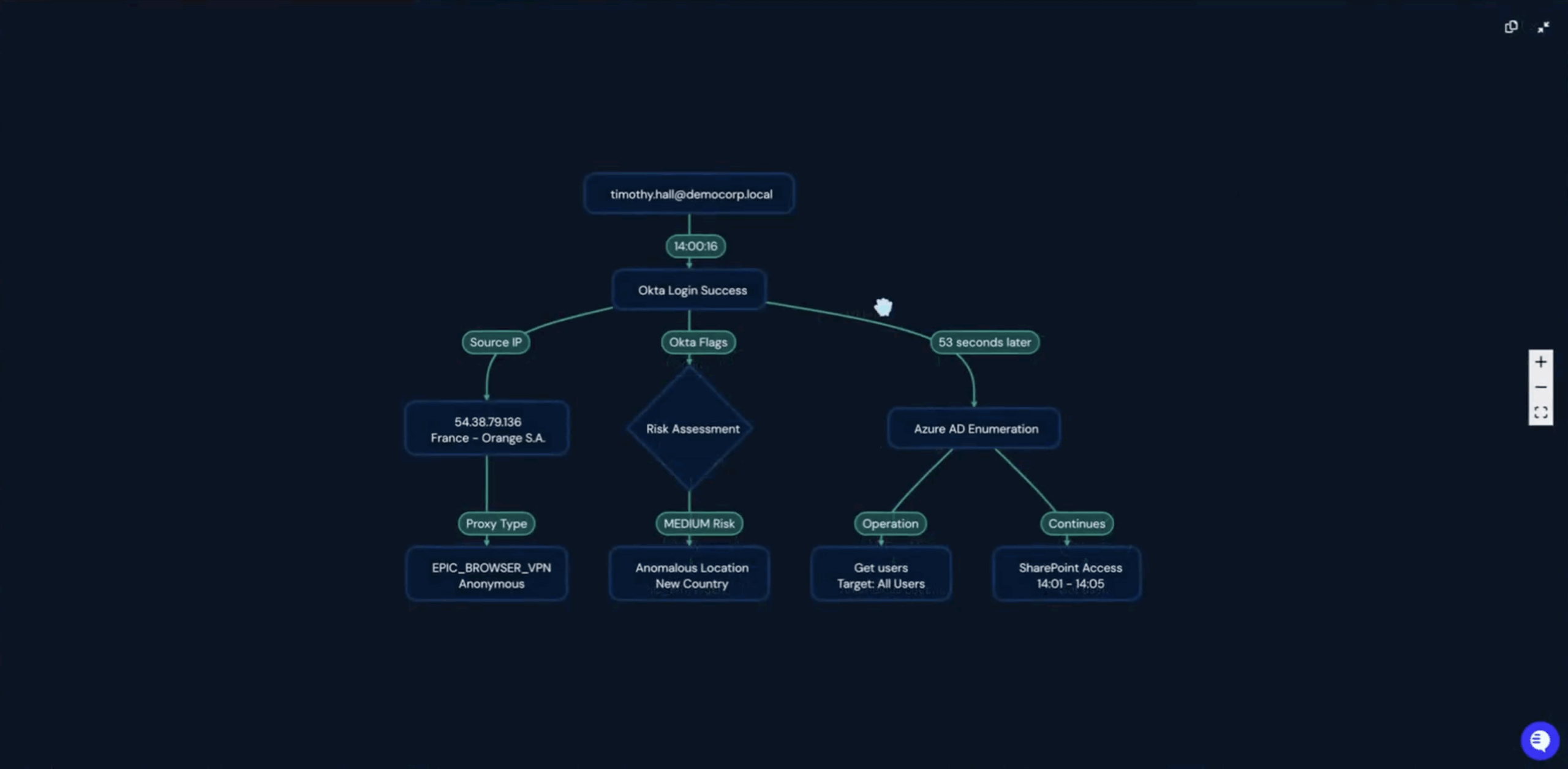
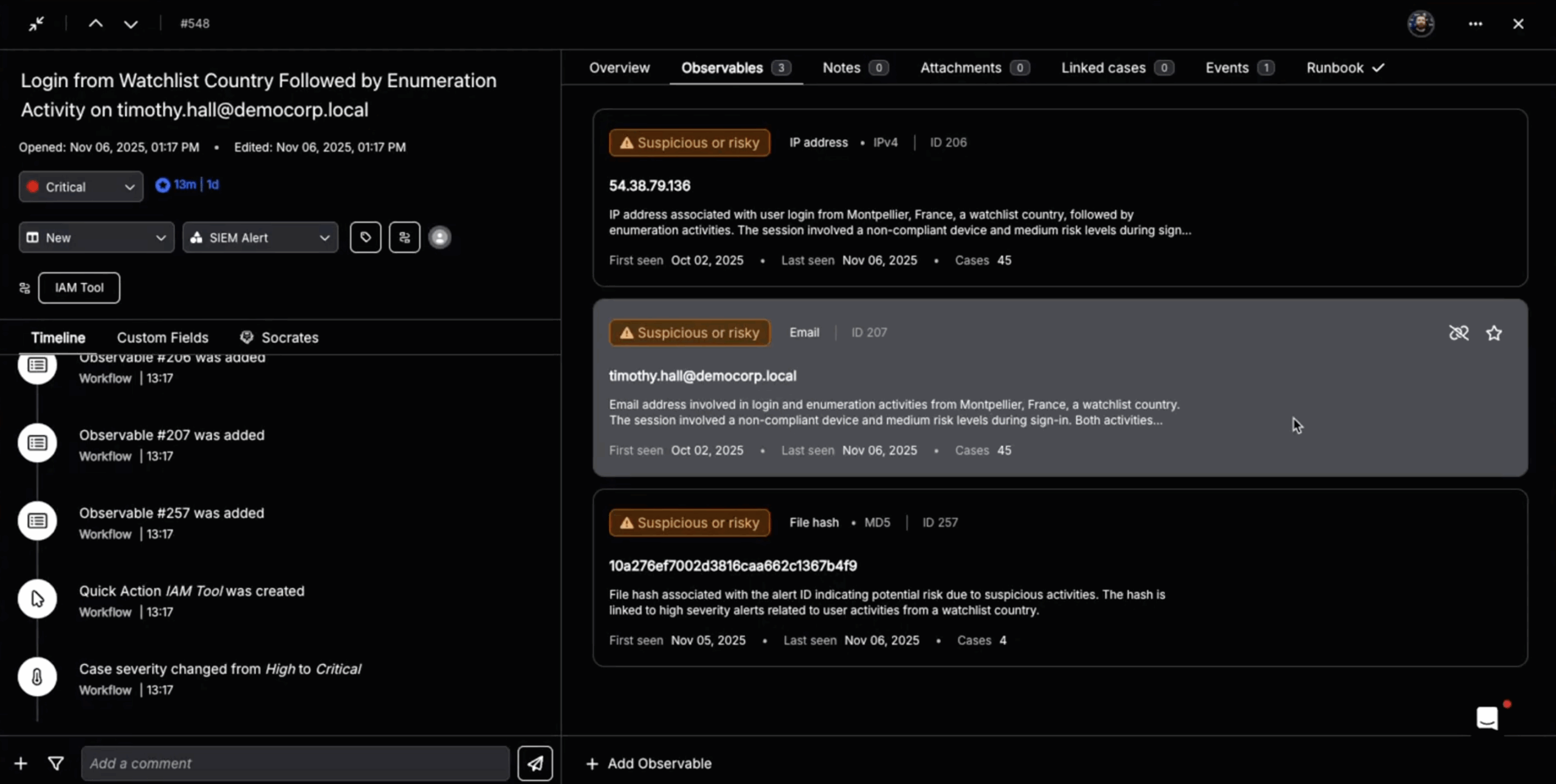
1. Autonomous Triage
Tier-1 triage is one of the most common workflow patterns documented in Torq. Using workflow triggers, enrichment steps, and case actions, AI agents automate the high-volume data gathering that normally overwhelms analysts.
- Trigger: A SIEM or EDR sends an alert via webhook.
- Enrichment: Workflows query threat intelligence and internal HR systems.
- Decision: The AI agent classifies the alert (False Positive vs. True Positive).
- Action: It auto-closes false positives or escalates true threats to specific teams.
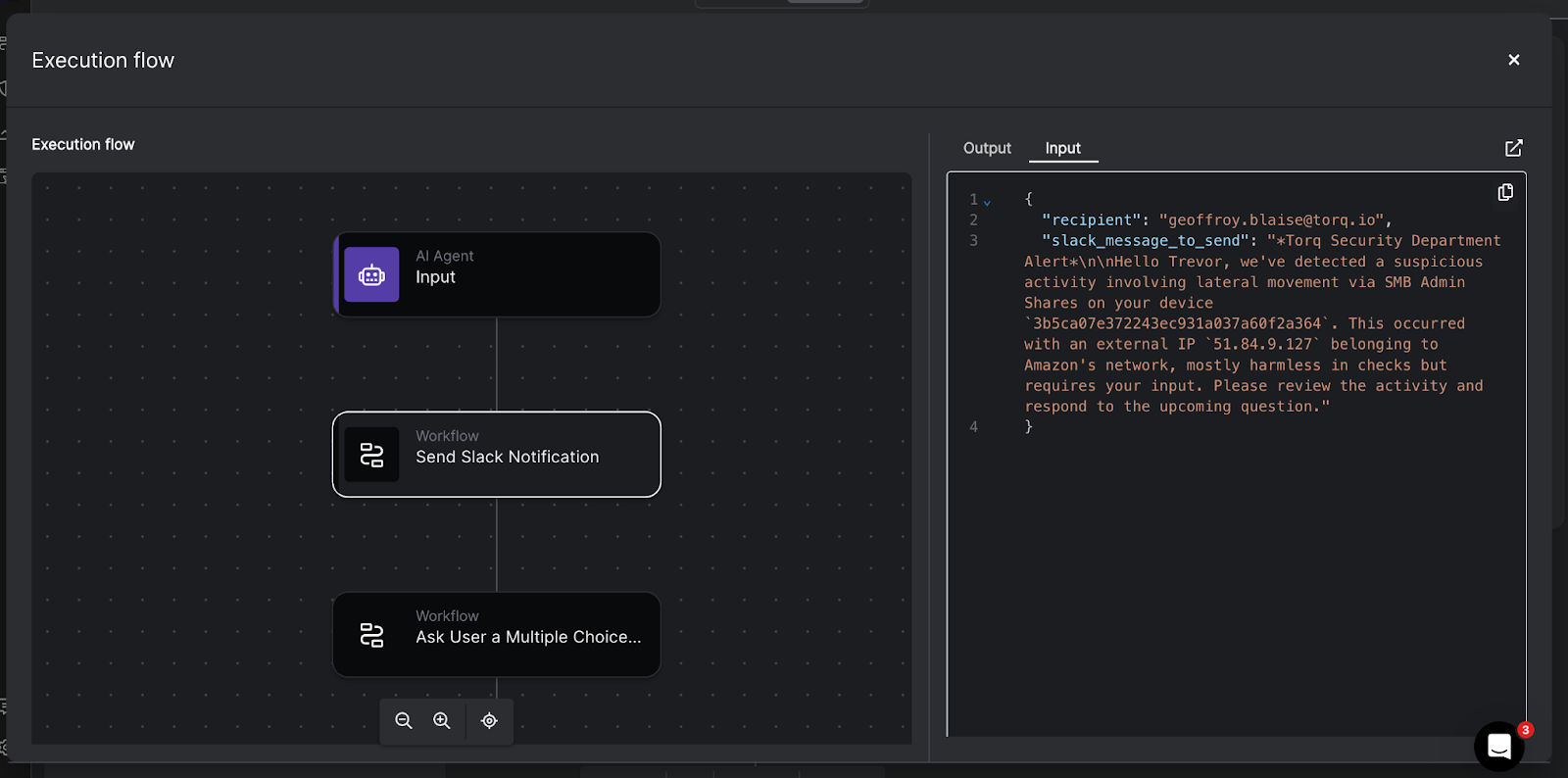
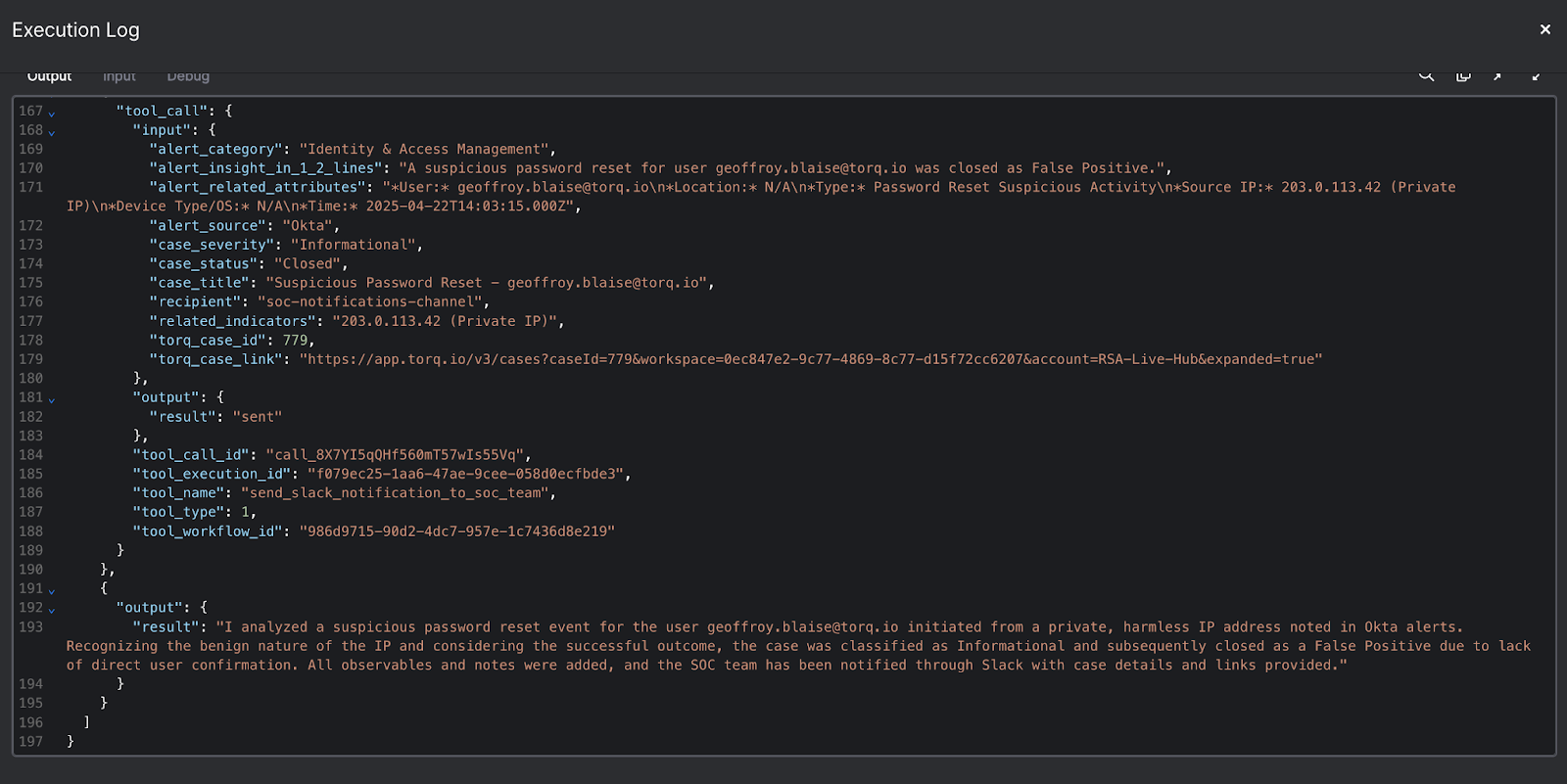
Everything is visible in workflow logs, allowing teams to audit how each step was executed.
Phishing is dynamic; static playbooks struggle to catch up. An agentic approach mimics a human investigator.
- Analysis: The agentic system parses headers, decodes URLs, and runs sandbox analysis.
- Context: It checks user identity and history.
- Remediation: If malicious, Torq searches the environment for the email, removes it from all inboxes, blocks the sender, and updates firewall rules, all while maintaining a full audit trail.
In the cloud, risks appear and disappear in seconds. An agentic AI system acts as a 24/7 guardian of security posture.
- Validation: When a misconfiguration alert fires, the workflow queries cloud APIs (AWS, Azure, GCP) to confirm the exposure.
- Verification: The system messages the resource owner via Slack/Teams for verification.
- Action: If no approval is received, the agentic AI applies conditional logic to revoke public access or modify configurations to restore compliance.
Risks, Challenges, and Governance in Agentic AI Security
The biggest barrier to adopting agentic AI is fear. What if the AI goes rogue? What if it shuts off the CEO’s laptop access?
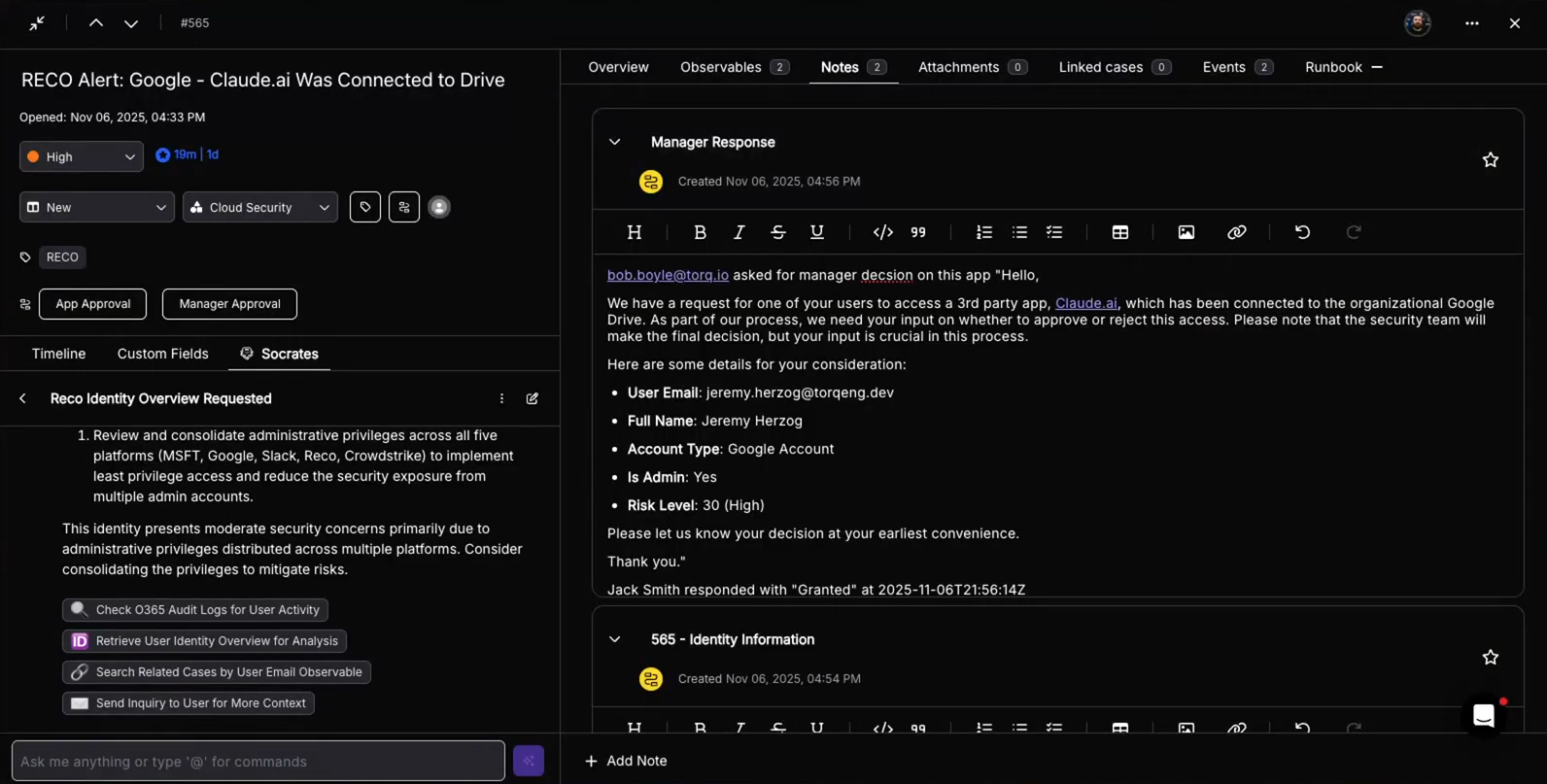
Trust in AI can only be achieved through rigorous governance and architecture. This is where the distinction between human-in-the-loop and human-on-the-loop becomes vital.
- Human-in-the-loop: The AI recommends actions but needs explicit approval for high-impact steps.
- Human-on-the-loop: The AI executes within defined guardrails, with humans monitoring and able to intervene or override.
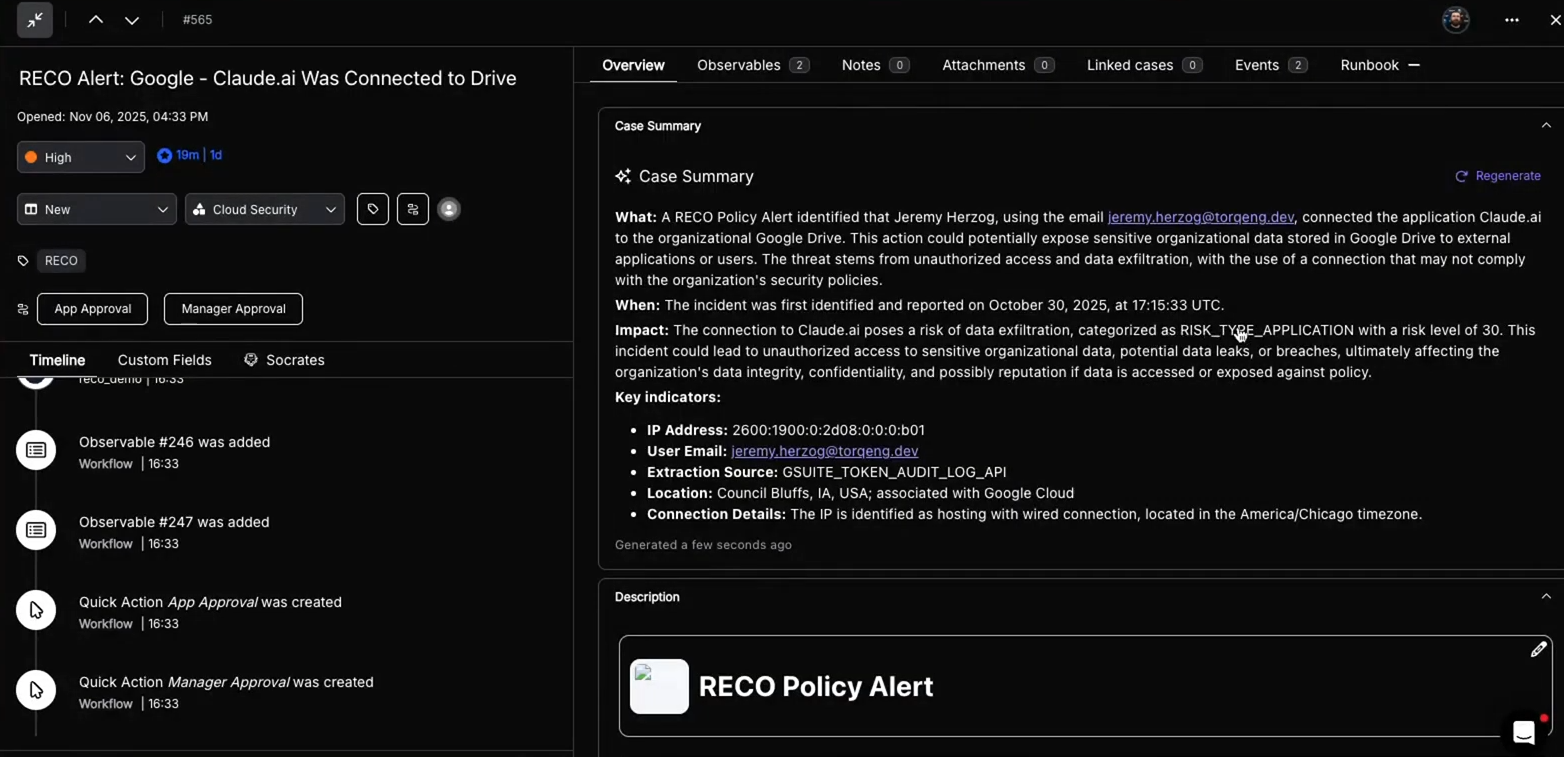
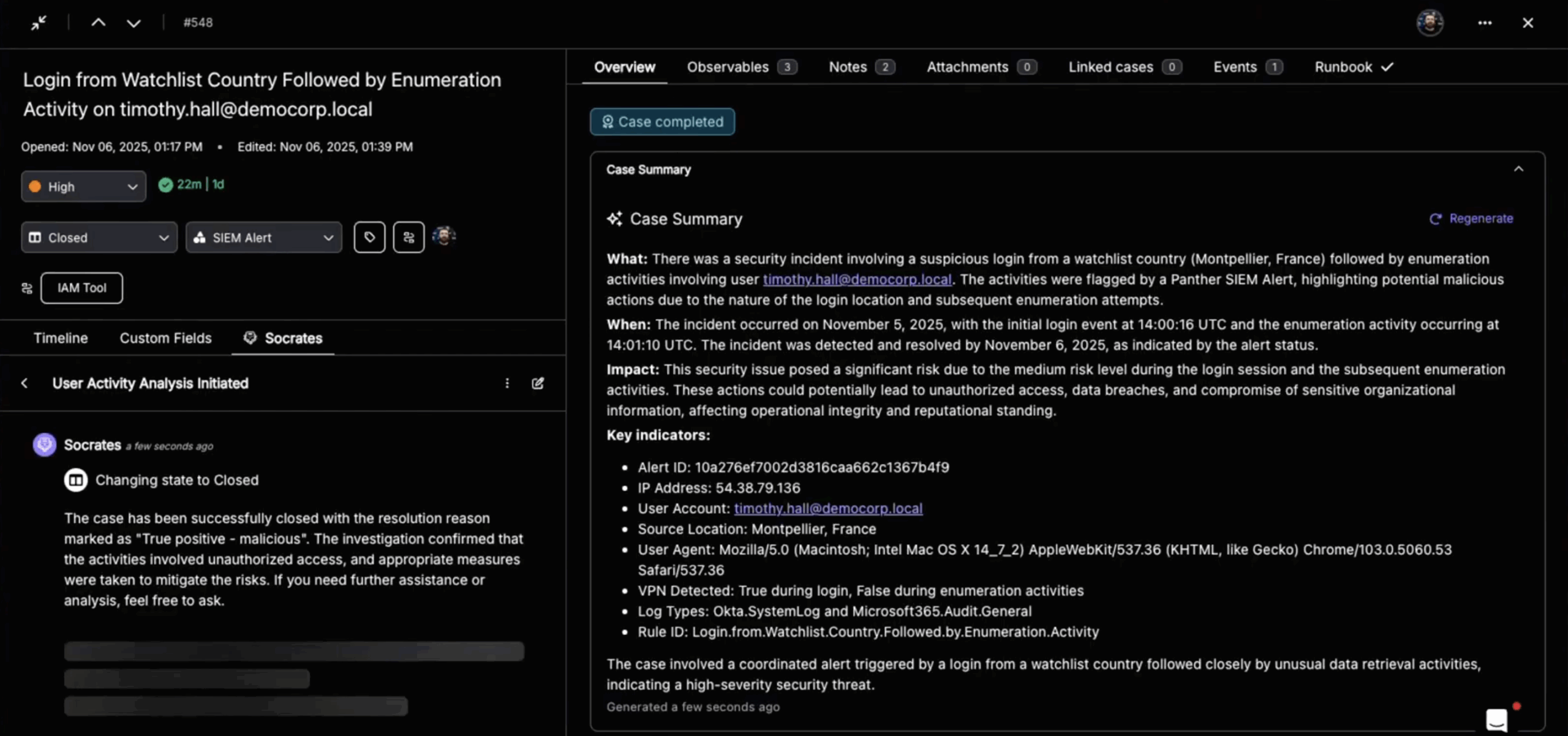
Transparency Through Execution Logs and Case Records
A black box is unacceptable in security. An agentic system must expose its reasoning and actions.
Torq provides detailed execution logs and case histories for every AI-driven workflow, including:
- Inputs and outputs
- Tools called and parameters used
- Timestamps and outcomes
This makes it possible to answer the question, Why did the AI do that? with concrete evidence.
Enforcing Guardrails With RBAC, Permissions, and Approvals
Agentic security requires controls. Torq enforces Role-Based Access Control (RBAC) to limit which users (human or machine) can execute workflows. Critical actions — like account lockouts or network isolation — can be designed with human-in-the-loop approval steps. This ensures that high-impact remediations always require human validation, creating predictable boundaries for the AI.
Getting Started: Building Your First Agent-Ready Workflow
The Torq Knowledgebase outlines exactly how teams can create workflows for agentic AI to operate end-to-end. Start with a high-volume or high-noise process, such as phishing triage or endpoint alert enrichment, and define your desired outcome. In Torq, workflows begin with a trigger (an alert, API call, or scheduled event), followed by a sequence of steps that query systems, enrich data, create cases, or notify users.
Once you build and test the workflow, you can incorporate human approvals, connect additional integrations, and refine logic using execution logs. This documented structure makes workflows dependable, transparent, and ready for agentic AI to orchestrate at scale.
The Future is Autonomous
The shift to agentic AI security is inevitable. The math of the modern threat landscape simply doesn’t support a human-only defense strategy. Attackers are using AI to scale their assaults, which means defenders must use AI to scale their response.
Agentic AI allows organizations to move from a posture of coping to a posture of control. It frees human analysts to focus on threat hunting, strategy, and architecture, while the agentic system handles the noise.
Don’t settle for an AI that just chats. Demand an AI that works. Learn more about how to strategically approach agentic AI in the SOC in our AI or Die Manifesto.
FAQs
How is agentic AI different from generative AI in cybersecurity?
Generative AI (like ChatGPT) is designed as assistants to answer questions, provide recommendations, and create content or summarize text based on prompts. Agentic AI is generative AI embedded within an autonomous execution framework, which uses the same LLM reasoning capabilities but adds persistent memory, tool integration with contextual understanding, and orchestration to execute multi-step security workflows independently. In cybersecurity, this means an agentic system can autonomously investigate alerts, query multiple tools, reason through complex threats, and take remedial actions (such as blocking an IP) without human intervention. GenAI talks; agentic AI acts.
How can organizations effectively govern and monitor agentic AI security systems?
Safe adoption relies on three pillars: transparency (logging the AI’s “chain of thought”), guardrails (restricting high-risk actions, such as locking C-level accounts), and human-in-the-loop checkpoints (requiring approval for sensitive remediations). Platforms like Torq HyperSOC™ build these controls directly into the workflow engine.
Will agentic AI replace human security analysts?
No. Agentic AI replaces grunt work, not people. It handles the high-volume, repetitive work — such as initial triage, data enrichment, and false positive dismissal — that leads to analyst burnout. This enables human analysts to shift their focus to high-value tasks, such as strategic threat hunting, complex incident response, and security architecture.
What are the best use cases for agentic AI security?
Agentic AI delivers the highest ROI when deployed in high-volume, repetitive workflows. The top use cases include autonomous triage (investigating and resolving false positives), phishing remediation (analyzing emails and removing malicious messages), identity protection (verifying suspicious logins via Slack/Teams), and cloud security (automatically remediating misconfigurations, such as public S3 buckets).
What industries are seeing the biggest impact from agentic security adoption?
Industries with high-volume data and strict compliance requirements — such as Finance, Healthcare, and SaaS — are experiencing the most significant impact. The ability to autonomously triage thousands of alerts and enforce cloud posture in real-time is critical for these sectors.
How do I get started with agentic AI in my SOC?
Start by automating Tier-1 triage. Use a platform like Torq to build a workflow that ingests alerts, enriches them with threat intel, and classifies them. Once you trust the AI’s decision-making on low-risk alerts, you can gradually expand its autonomy to include remediation actions, adding human approval steps where necessary.