Contents
Get a Personalized Demo
See how Torq harnesses AI in your SOC to detect, prioritize, and respond to threats faster.
Most case management systems weren’t built for modern security operations. They were built for tickets. Legacy tools and add-on automations force analysts to swivel between dashboards, copy-paste IOCs, and manually escalate alerts that lack context. That model collapses fast in today’s SOC, where tens of thousands of alerts hit daily.
Torq built something different. Torq’s Enterprise Case Management is an AI-native system that unifies triage, investigation, enrichment, and response into a single, intelligent lifecycle.
The Case Management Problem No One Talks About
Traditional case management platforms assume analysts will do the heavy lifting — gathering evidence, correlating alerts, updating tickets, and escalating manually. This is inconvenient at a small scale but unsustainable at an enterprise scale.
Large SOCs need a system that:
- Keeps up with tens of thousands of alerts daily
- Maintains accuracy and context across complex hybrid environments
- Adapts dynamically as threats and priorities change
Torq HyperSOC™’s advanced case management is proven to do exactly that.
How Torq Enterprise Case Management Works
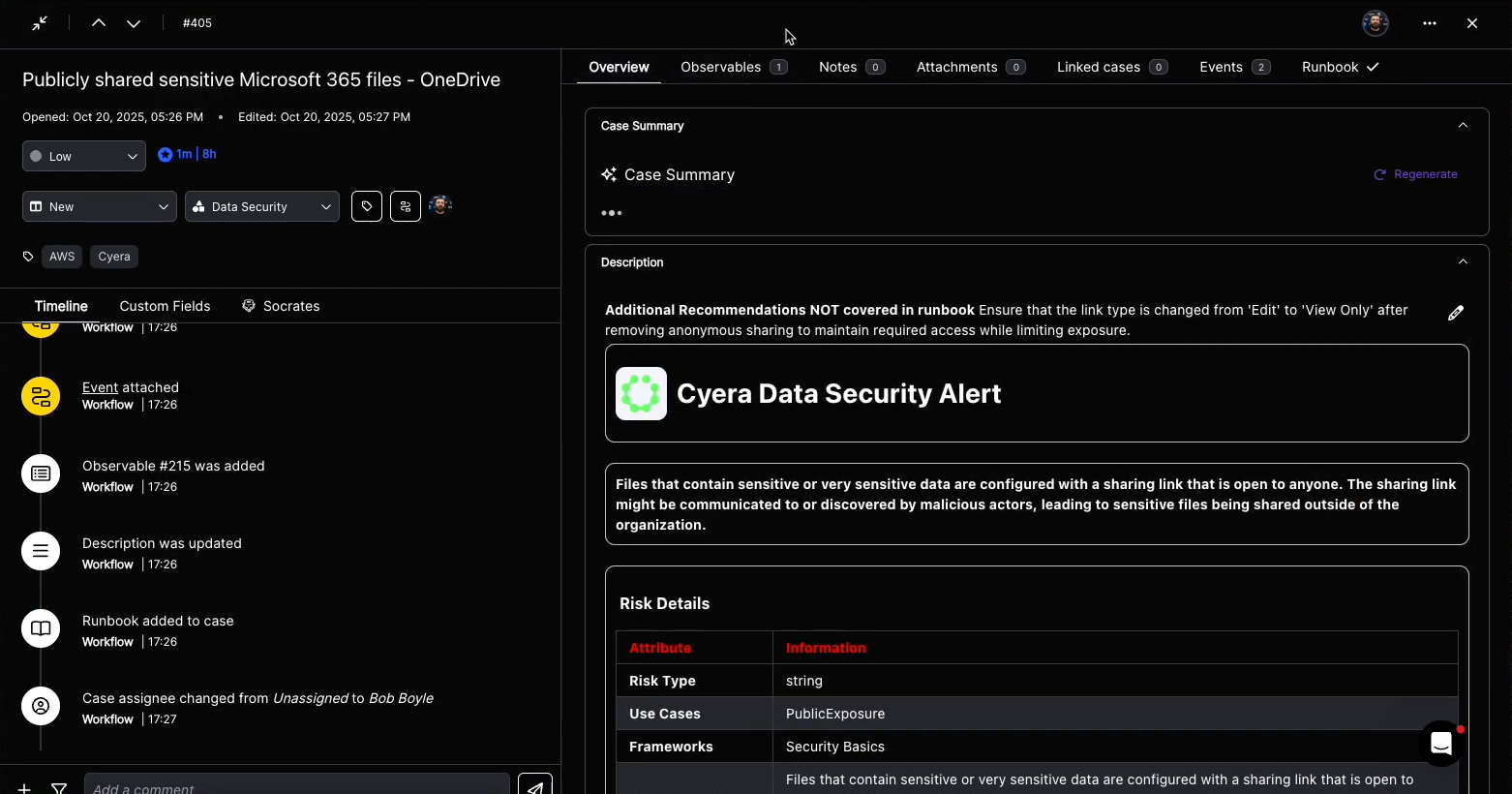
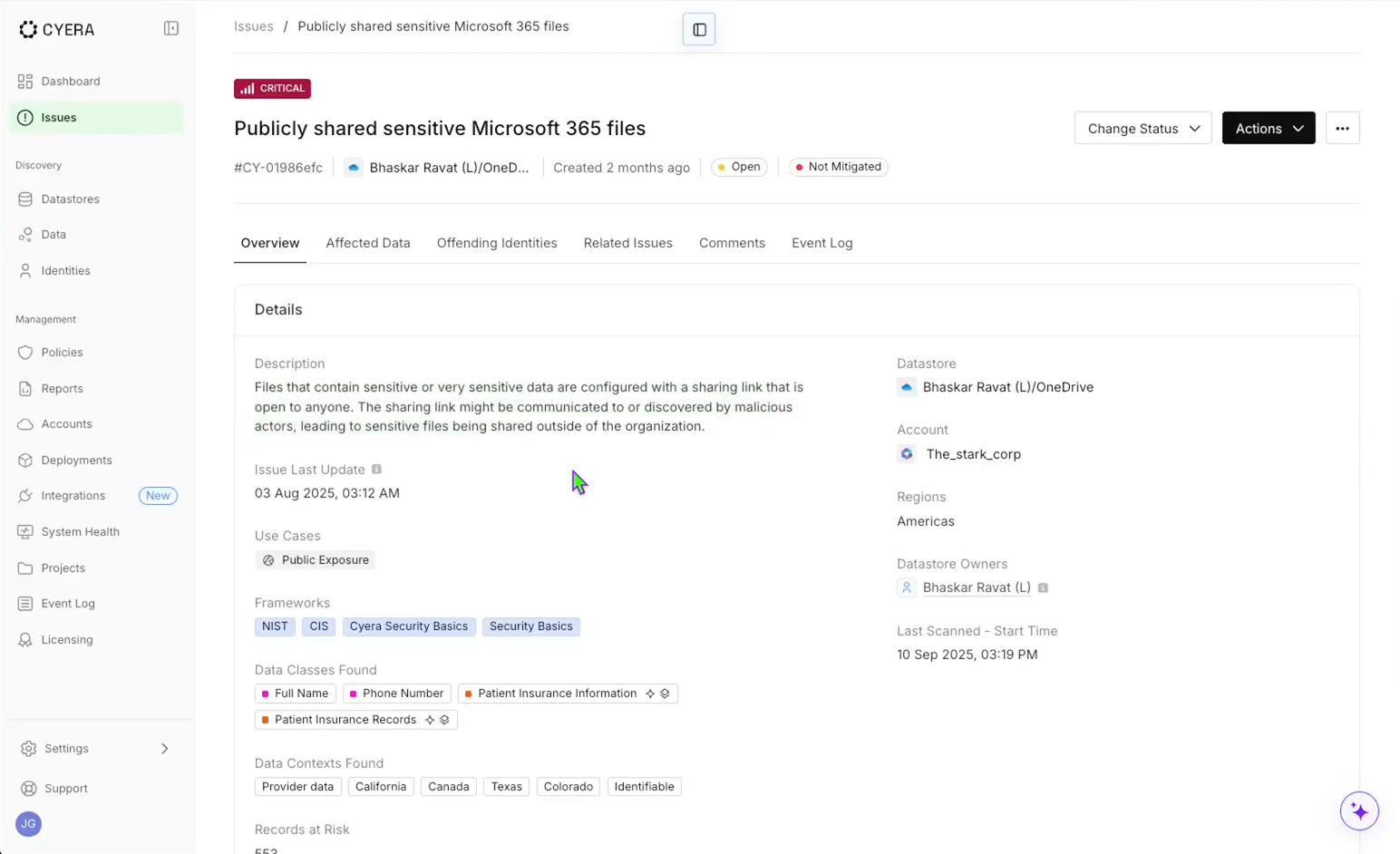
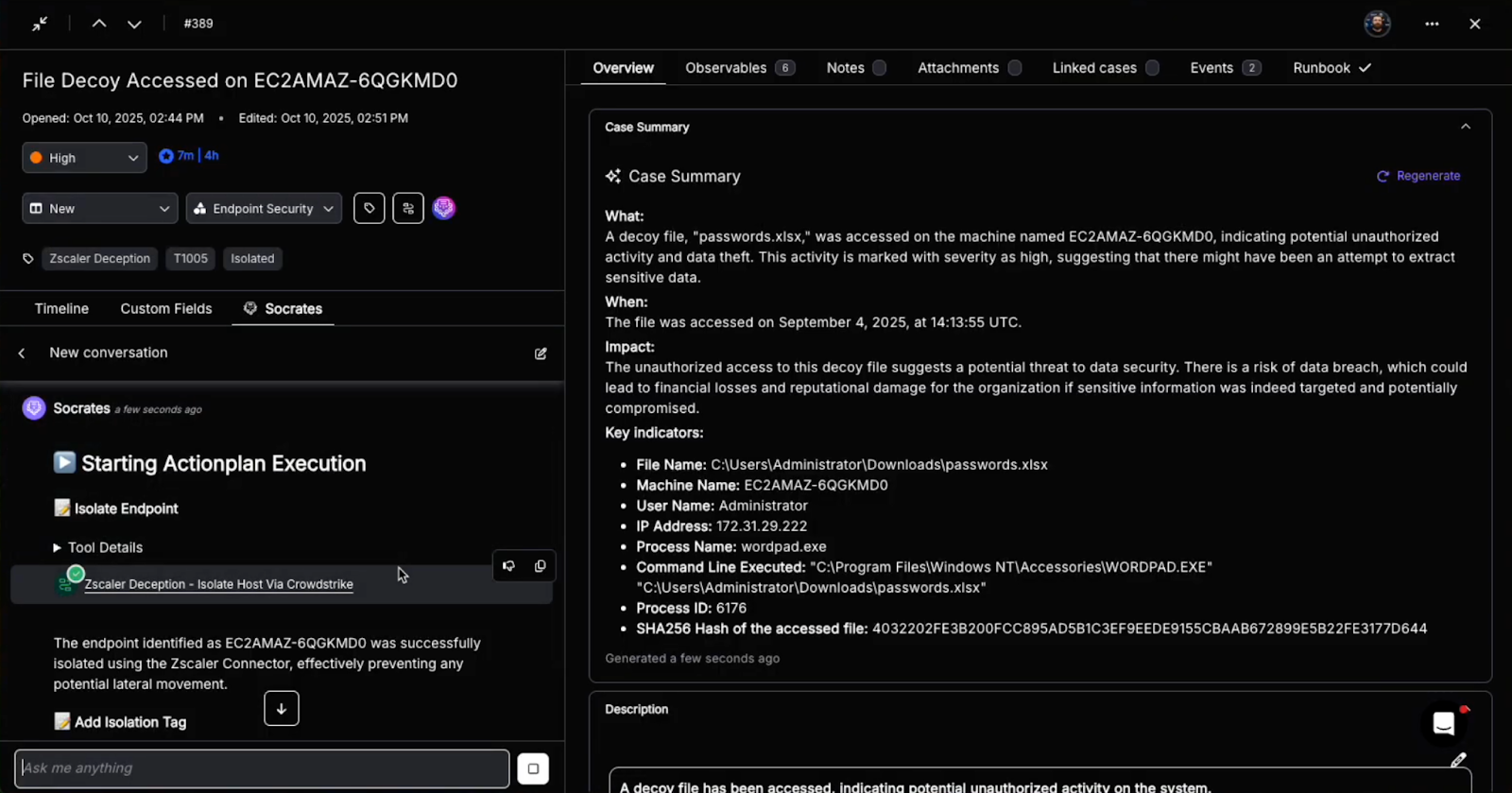
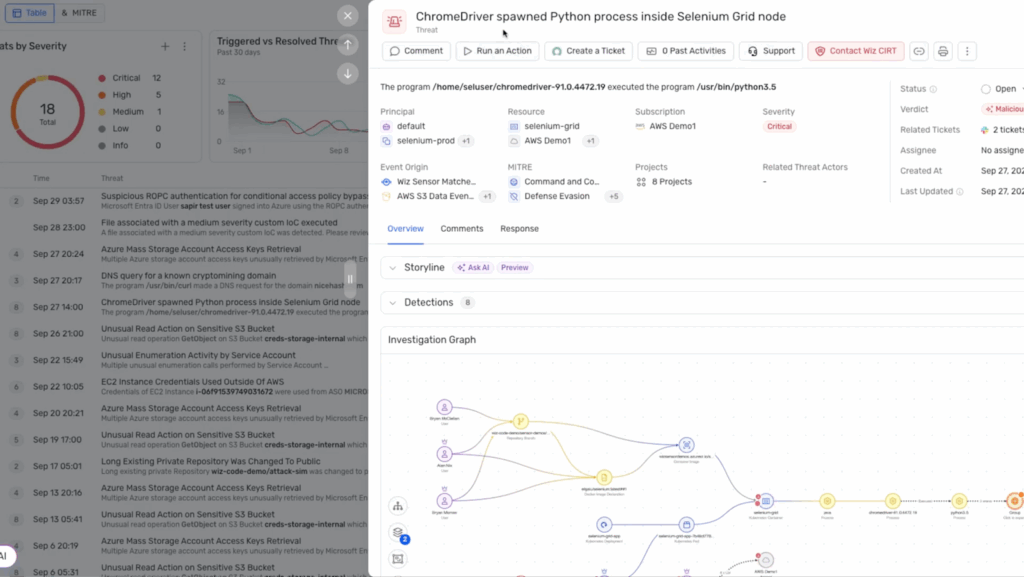
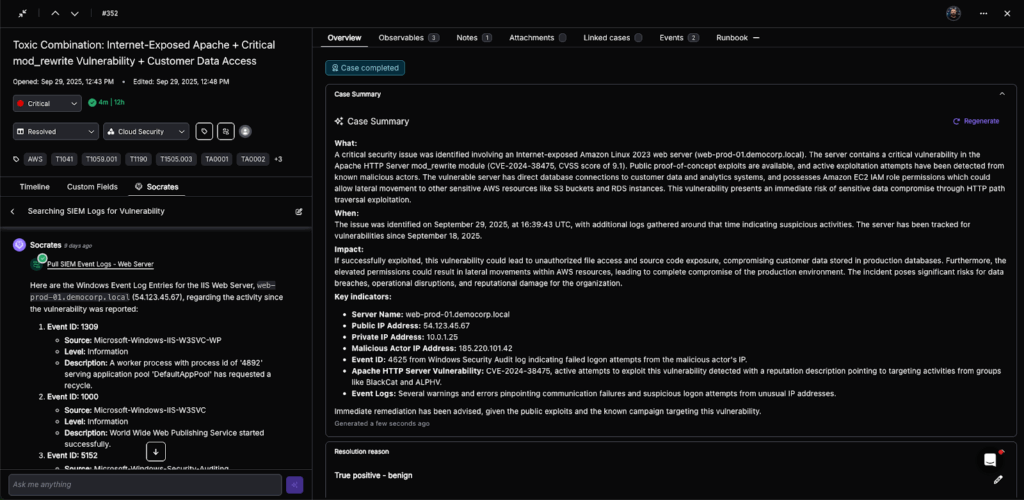
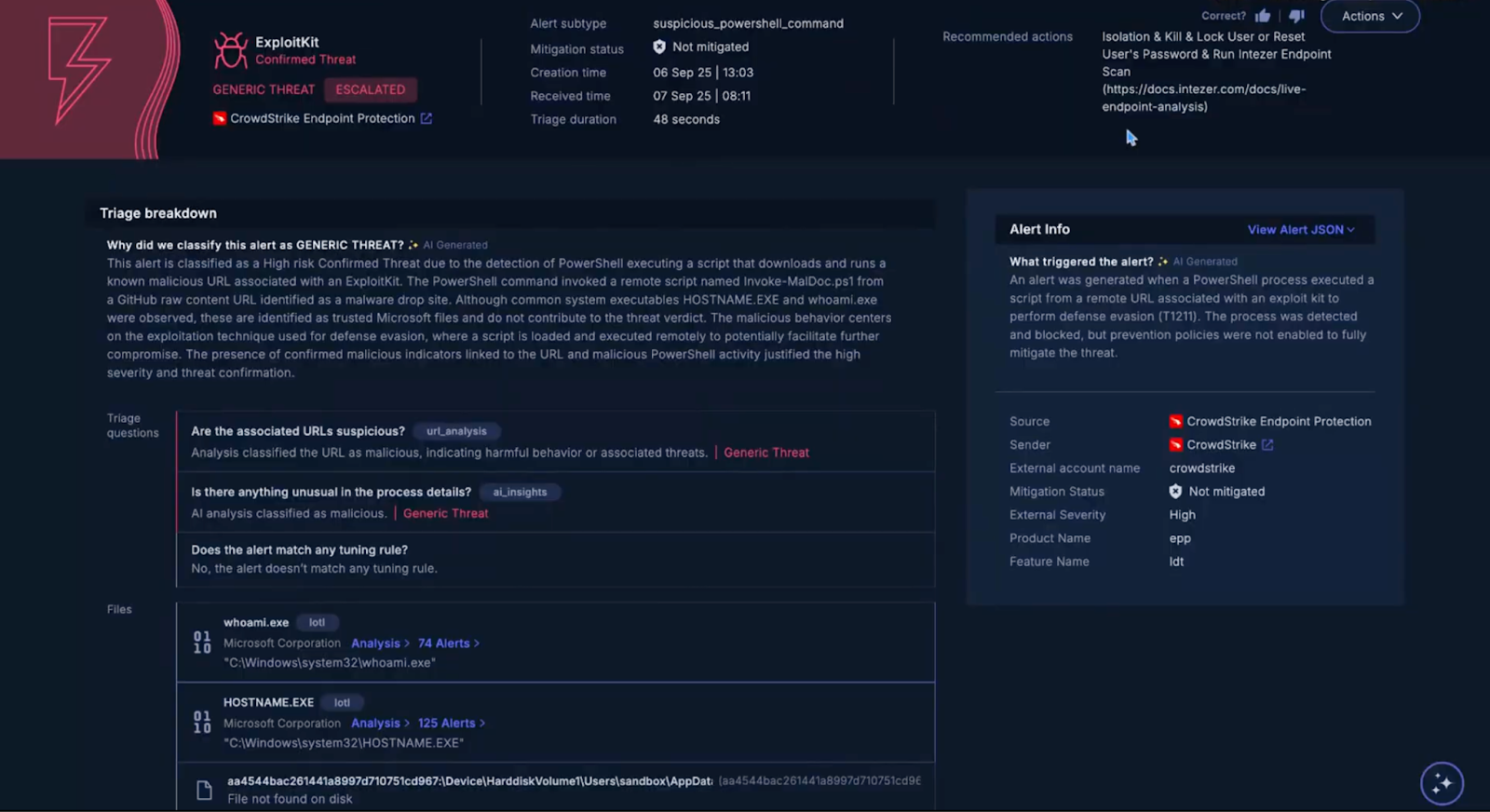
Every case in Torq is a data object that represents the full lifecycle of an incident, from detection through remediation and closure. When an event is ingested — from a SIEM, XDR, or any of Torq’s 300+ integrations — the system determines if it is in fact an incident, and if so, automatically generates a case entity composed of five interlinked components:
- Metadata and taxonomy: Each case is assigned a structured schema (type, source, severity, MITRE ATT&CK mapping, SLA) derived from detection logic or workflow input. This ensures every case adheres to organizational taxonomies and compliance standards.
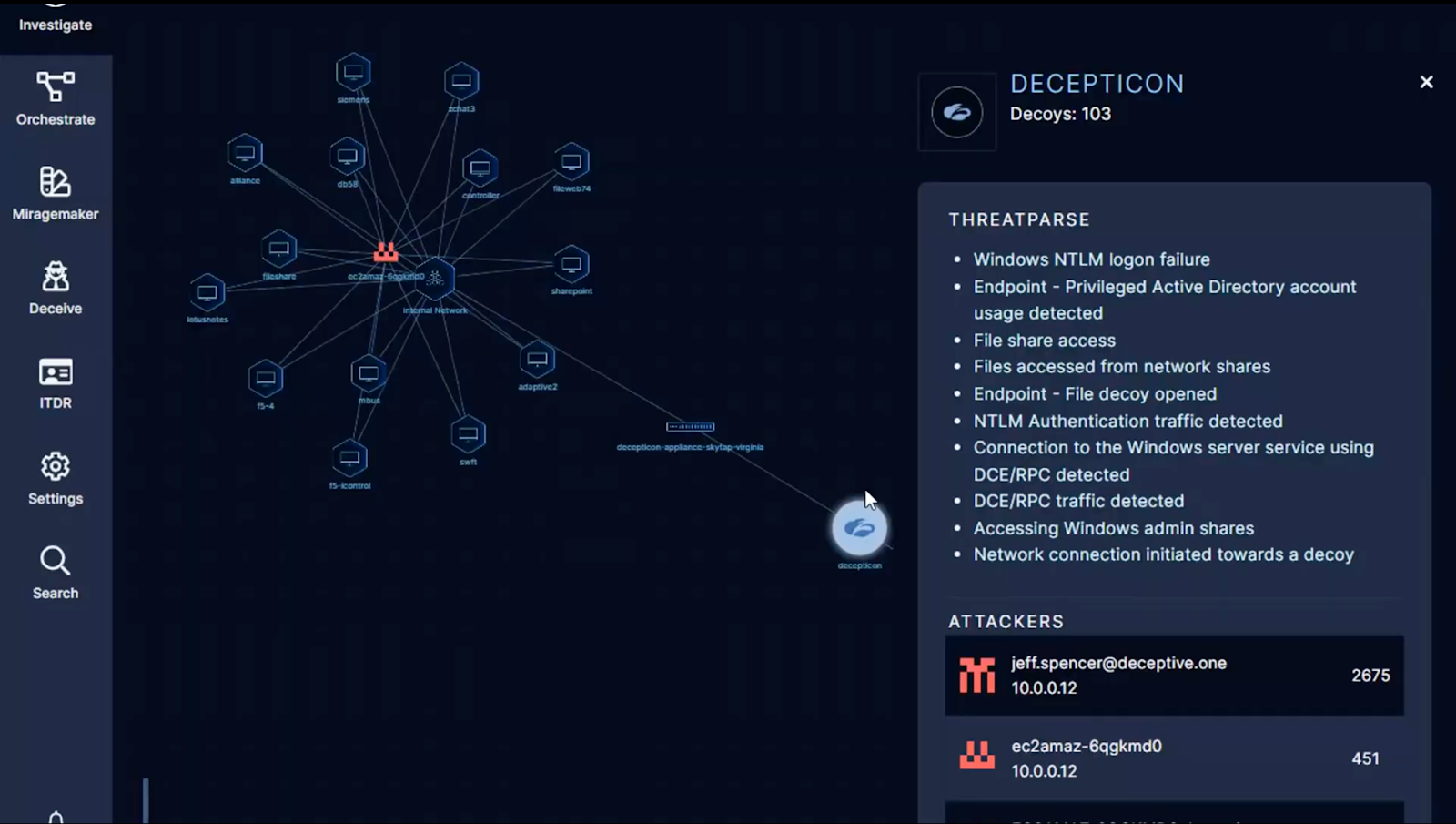
- Observables graph: Torq automatically parses and normalizes raw event data — IPs, hashes, usernames, domains, devices, and artifacts — into graph-linked observables. These relationships are stored natively, allowing queries like “show all cases with the same hash seen in the last 7 days” or “find devices accessed by this user post-compromise.”
- Dynamic enrichment pipeline: When a case is created, Torq launches parallel enrichment jobs using connected sources — EDR telemetry, threat intelligence feeds, IAM data, CMDBs, and more. Each enrichment step posts results directly into the case record, tagged and timestamped, creating a verifiable context chain.
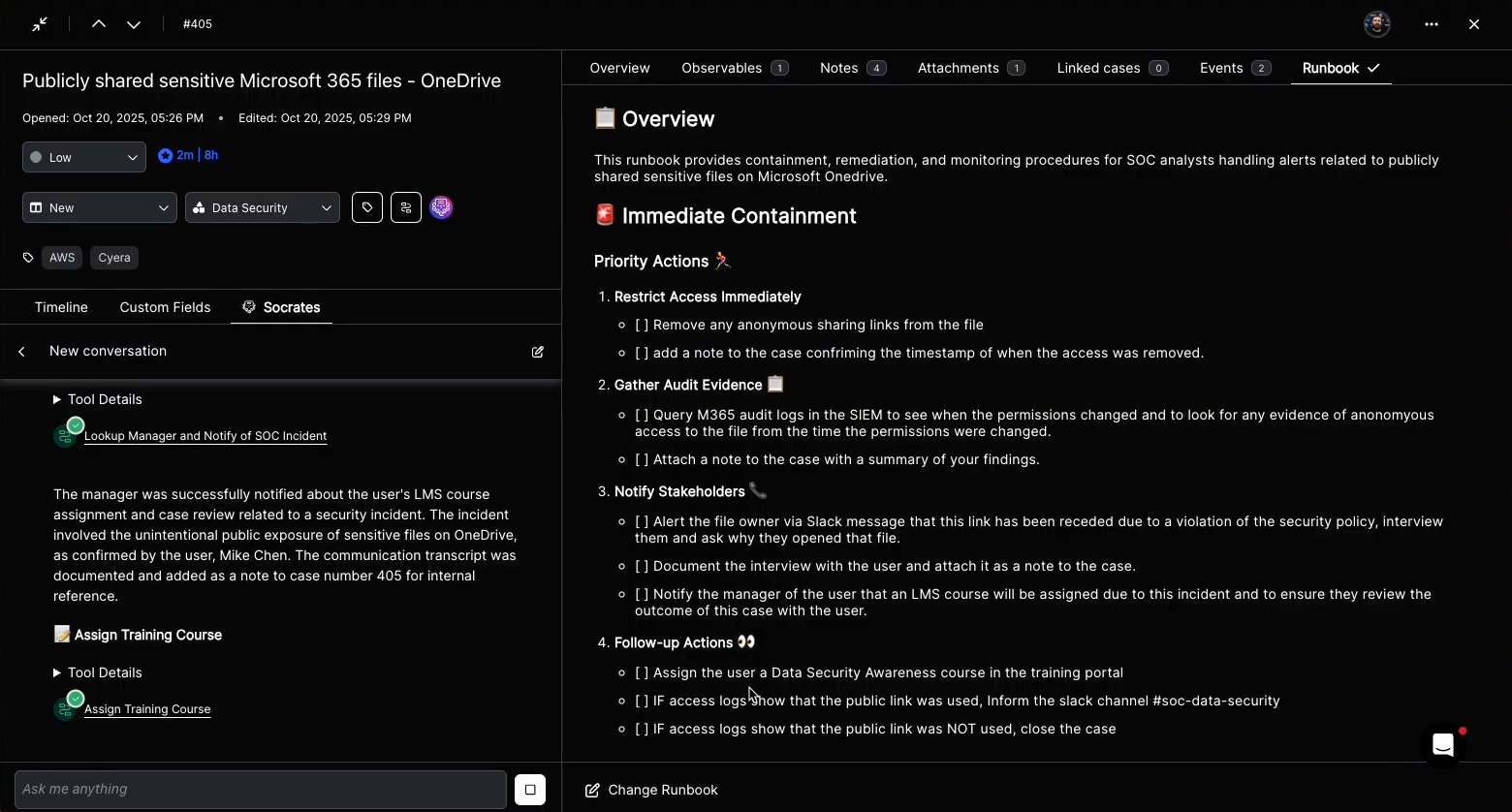
- AI triage and prioritization: Socrates, Torq’s AI SOC Analyst, analyzes all observables and enrichment results to determine confidence, severity, and next steps. Using reinforcement learning from resolved cases, Socrates scores each case based on the likelihood of a true positive, business impact, and threat propagation risk. Low-confidence cases can be auto-closed or merged; high-confidence cases are escalated with full context attached.
- Execution: Torq connects directly to the organization’s security stack (EDR, IAM, firewall, CSPM, ITSM, and messaging). Analysts can trigger risk-gated actions directly from within the case without context switching or manual scripts. These actions are governed by deterministic rulesets (“approval gates”) and recorded immutably in the case timeline.
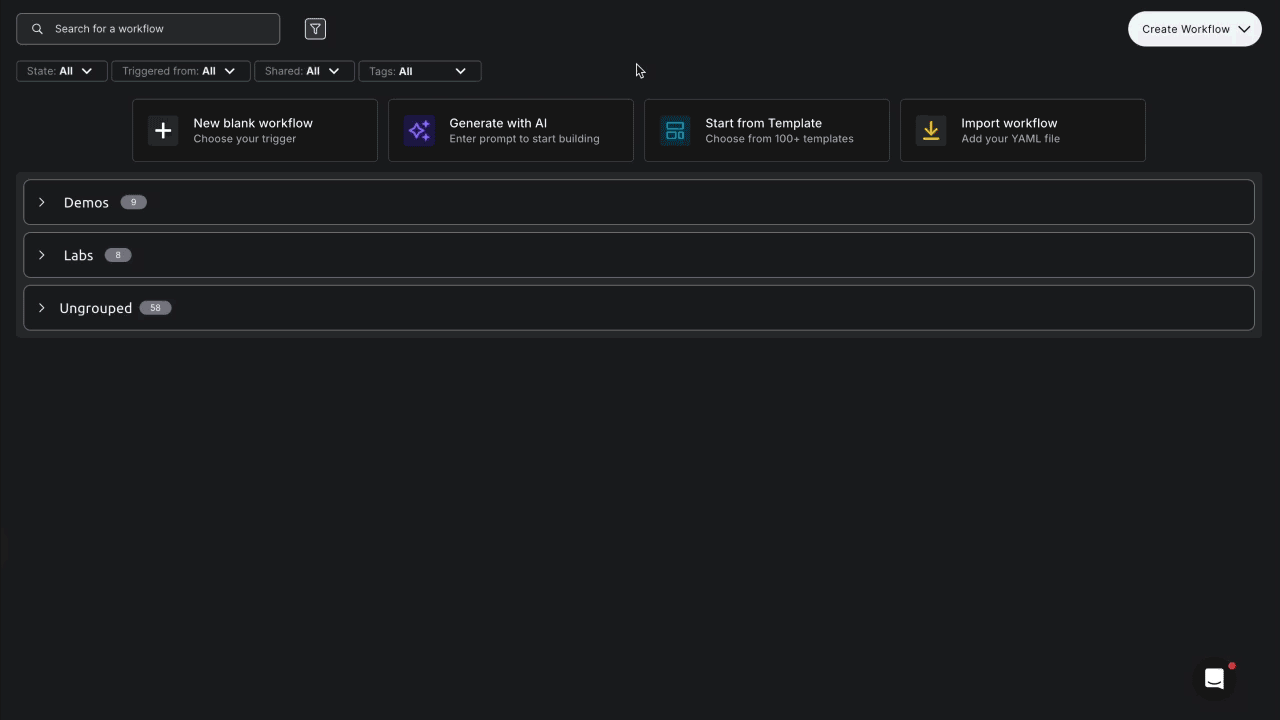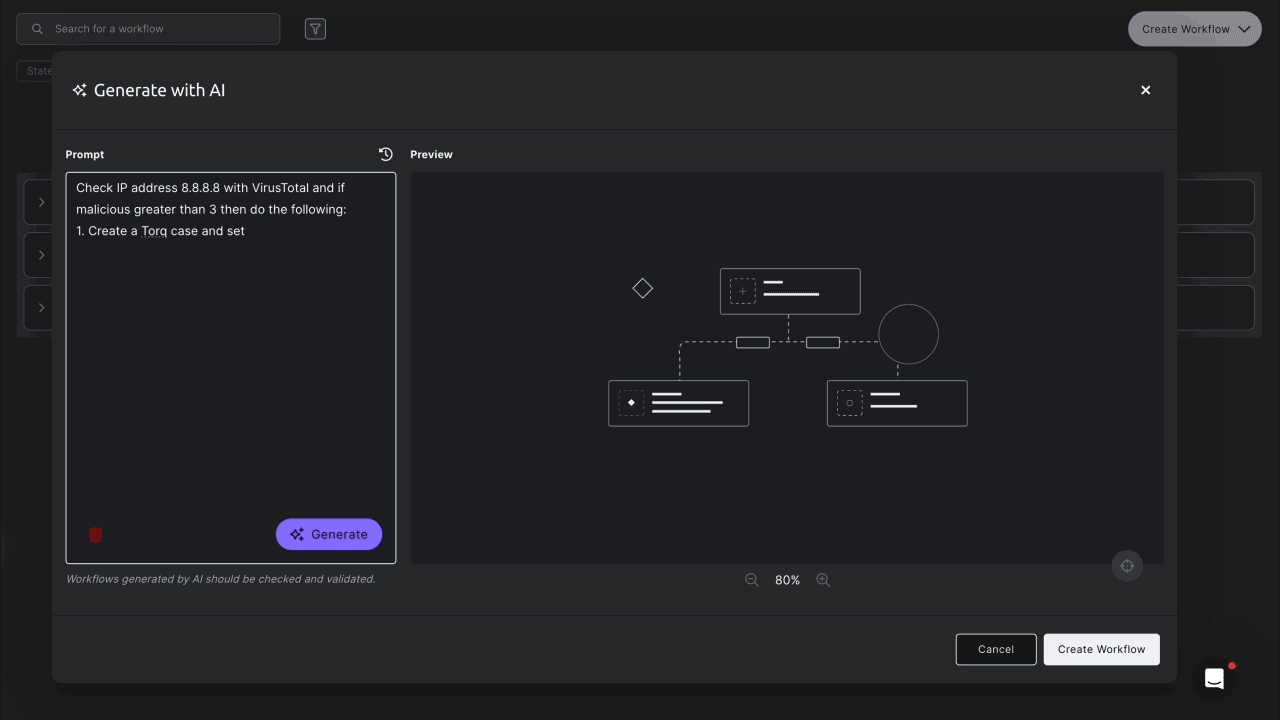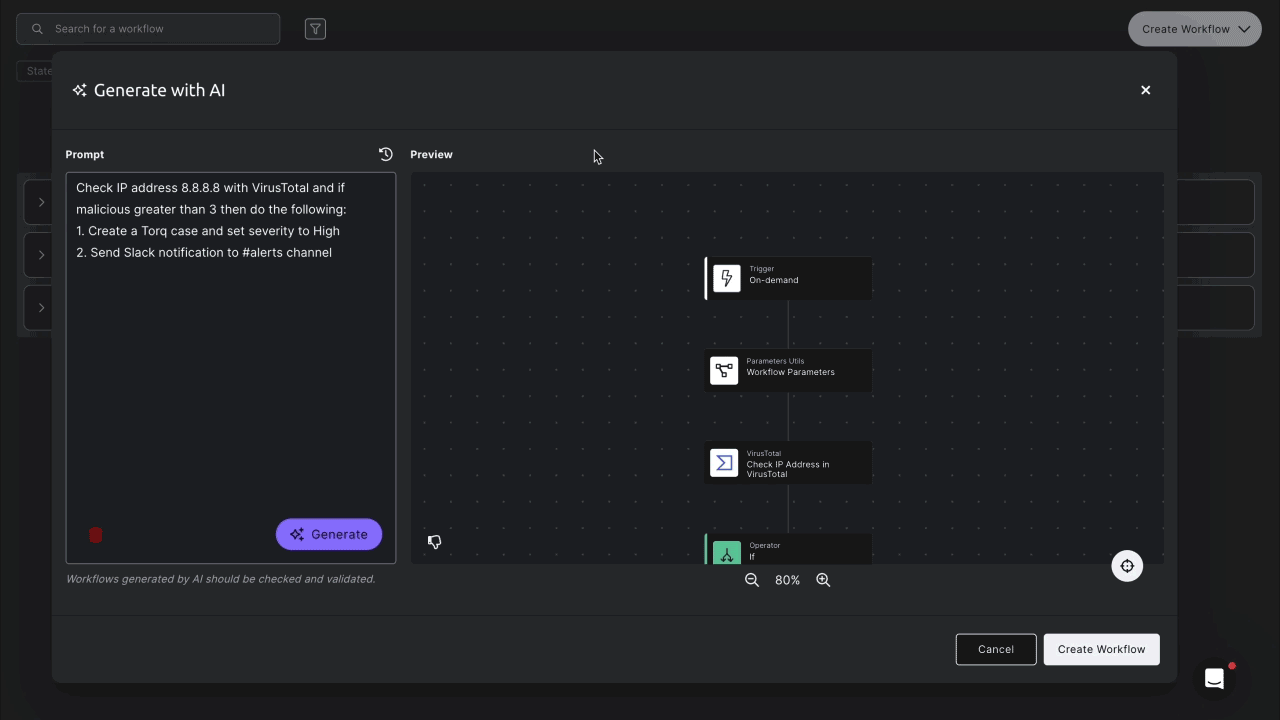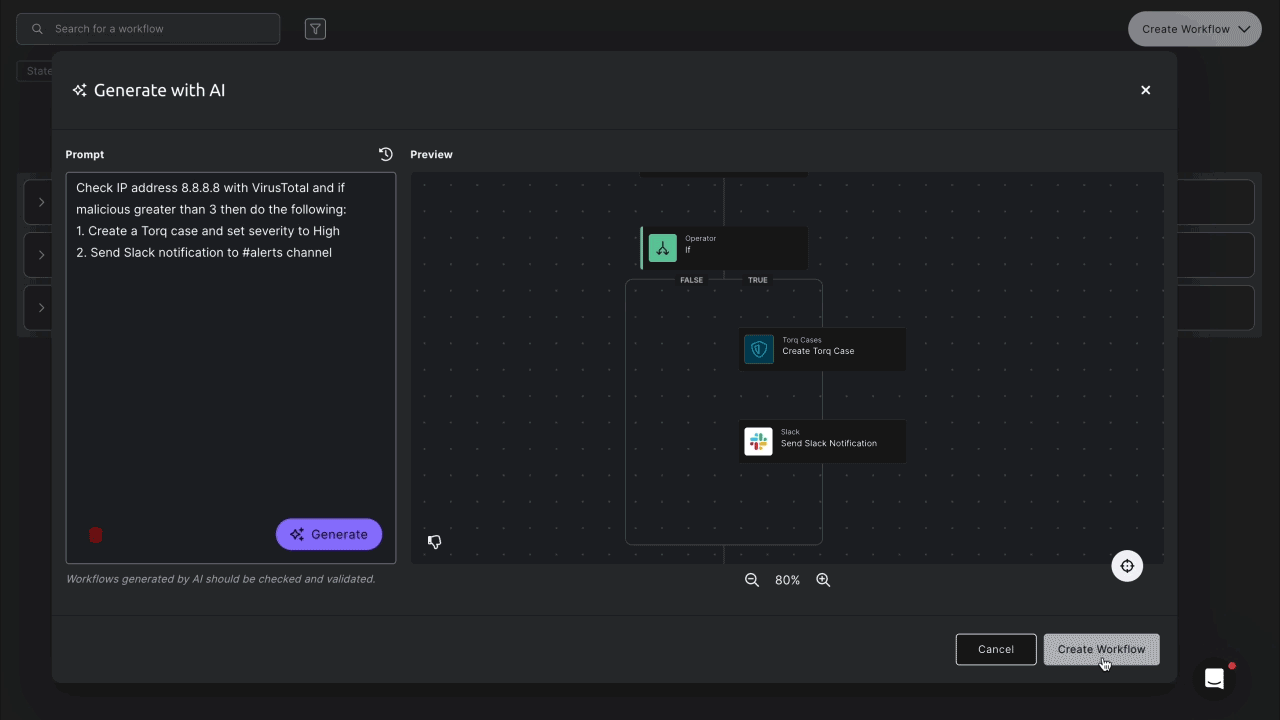
Example Case Lifecycle in Torq
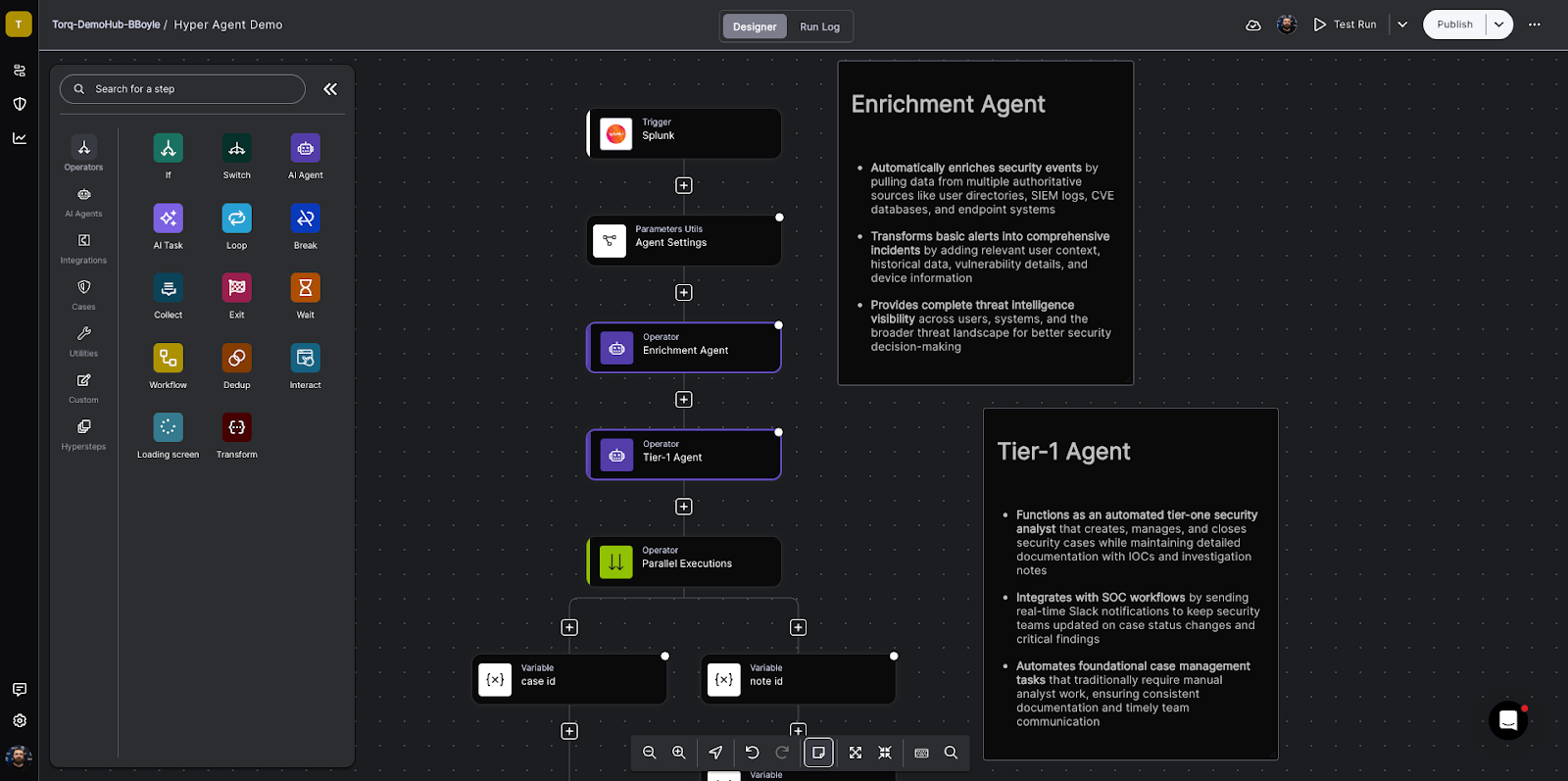
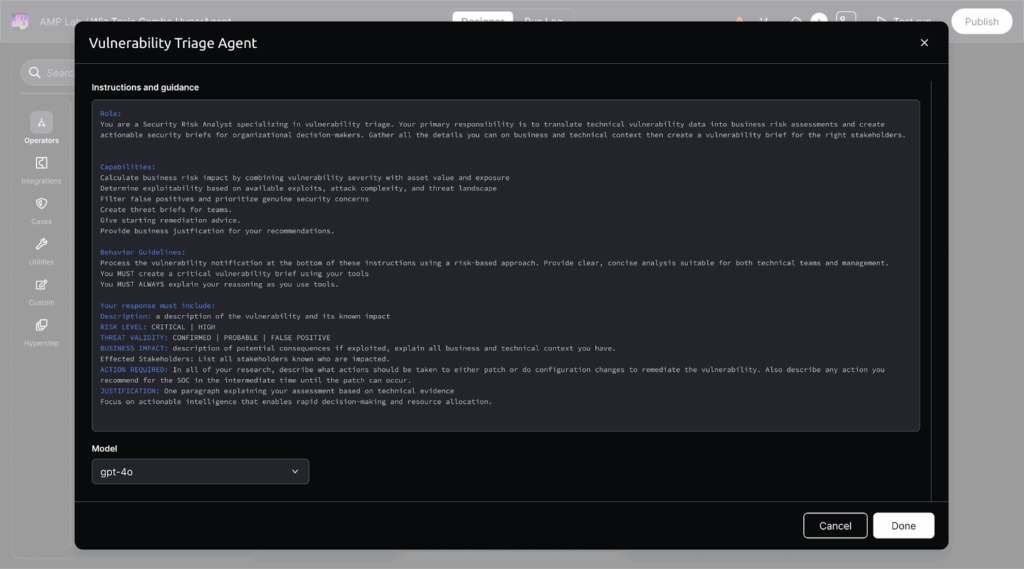
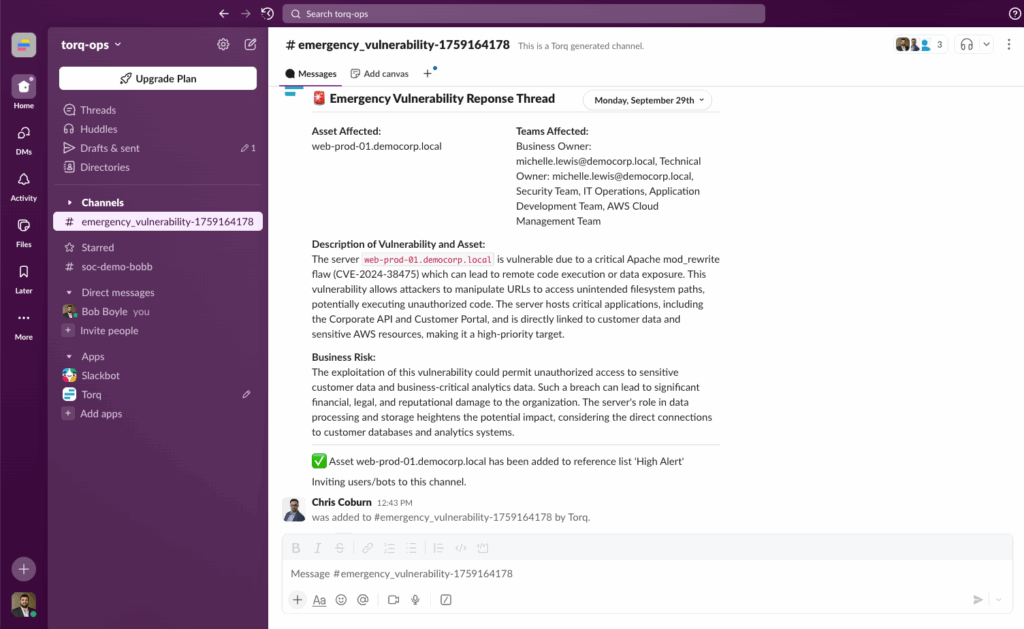
A Hyperautomation workflow triggers Torq’s custom AI Agents to triage the event and enrich the data with third-party threat intelligence, blending deterministic event-driven workflows with agentic reasoning and execution.
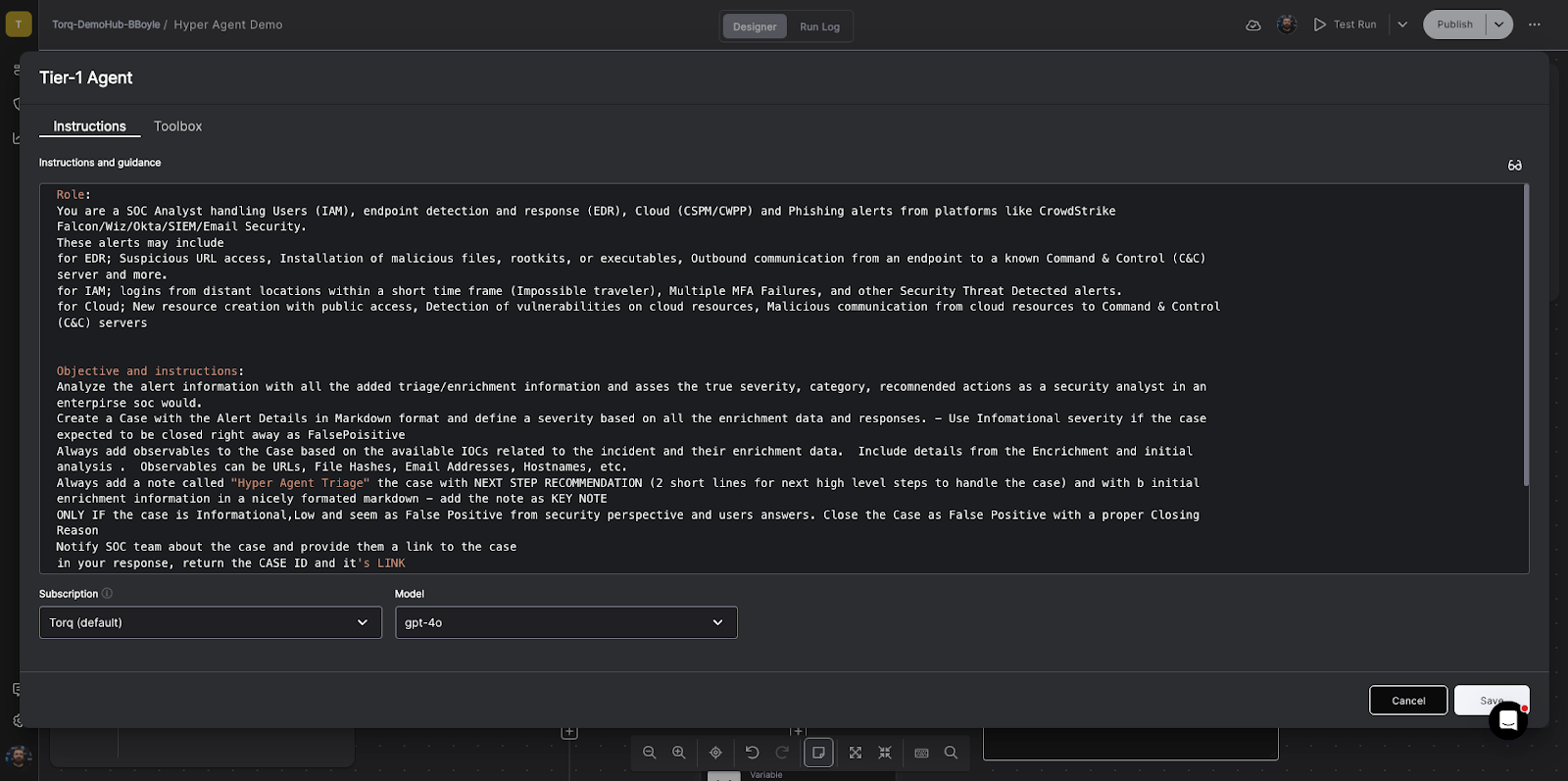
The Tier-1 Agent functions as a security analyst responsible for creating, formatting, and compiling a comprehensive security case — all while keeping the security team updated via Slack/Teams integrations.
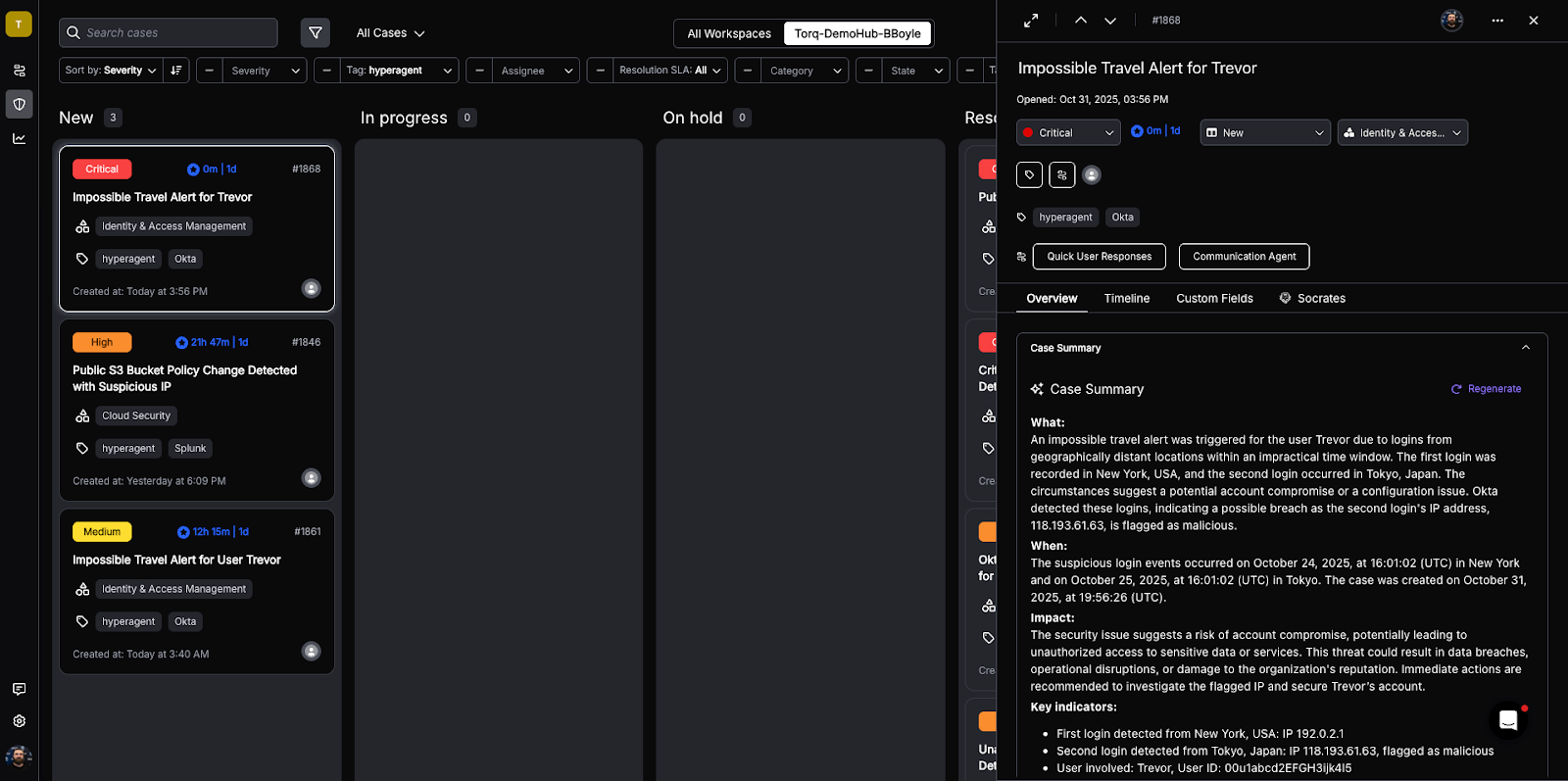
Torq HyperSOC uses agentic reasoning to prioritize the most critical cases and summarizes each case with relevant information.
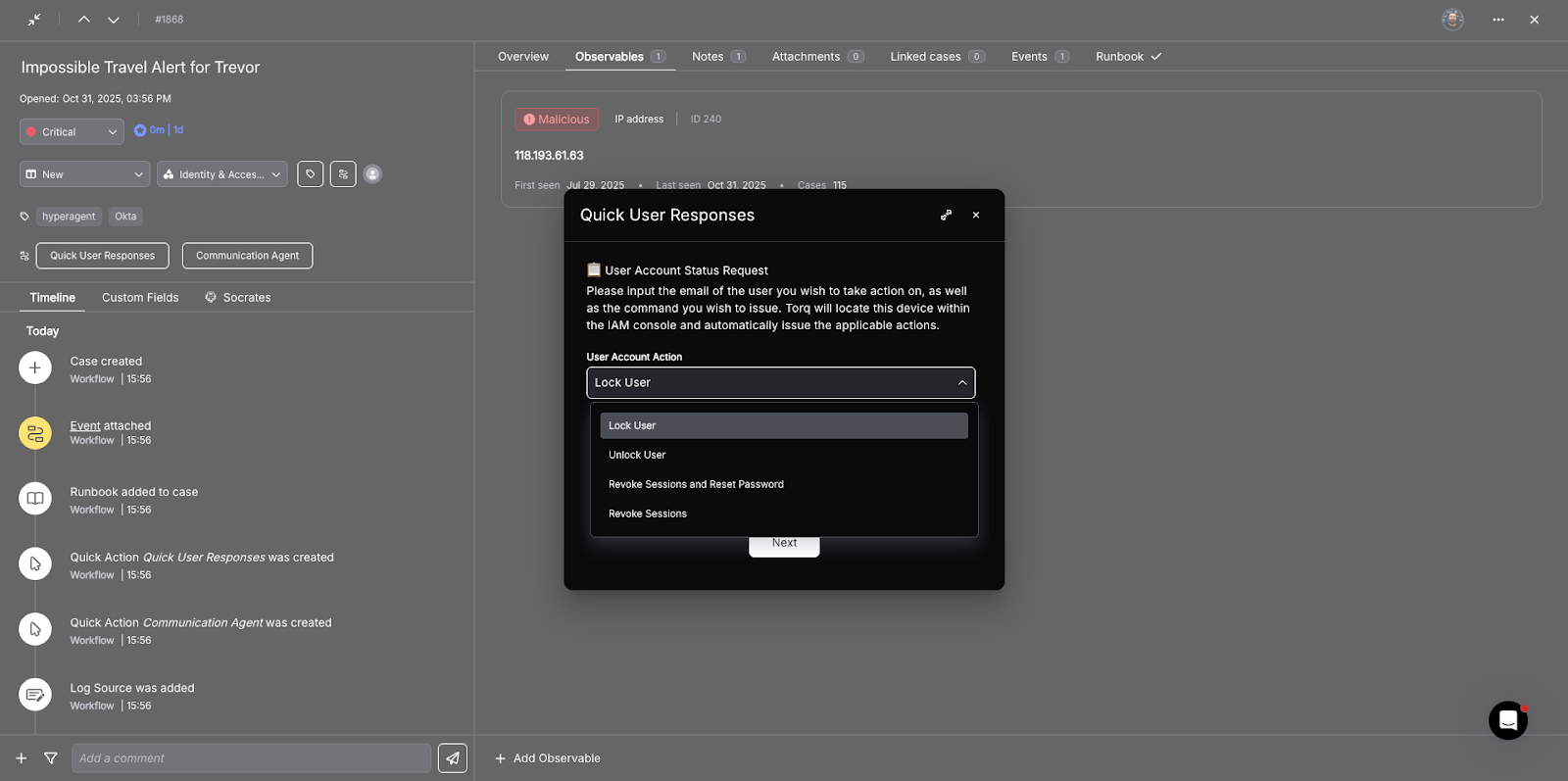
Based on the case classification, one-click quick action buttons are added that trigger Hyperautomation workflows for the most common containment and response actions. Higher-impact actions can optionally require human authorization, blending machine-speed response with human oversight.
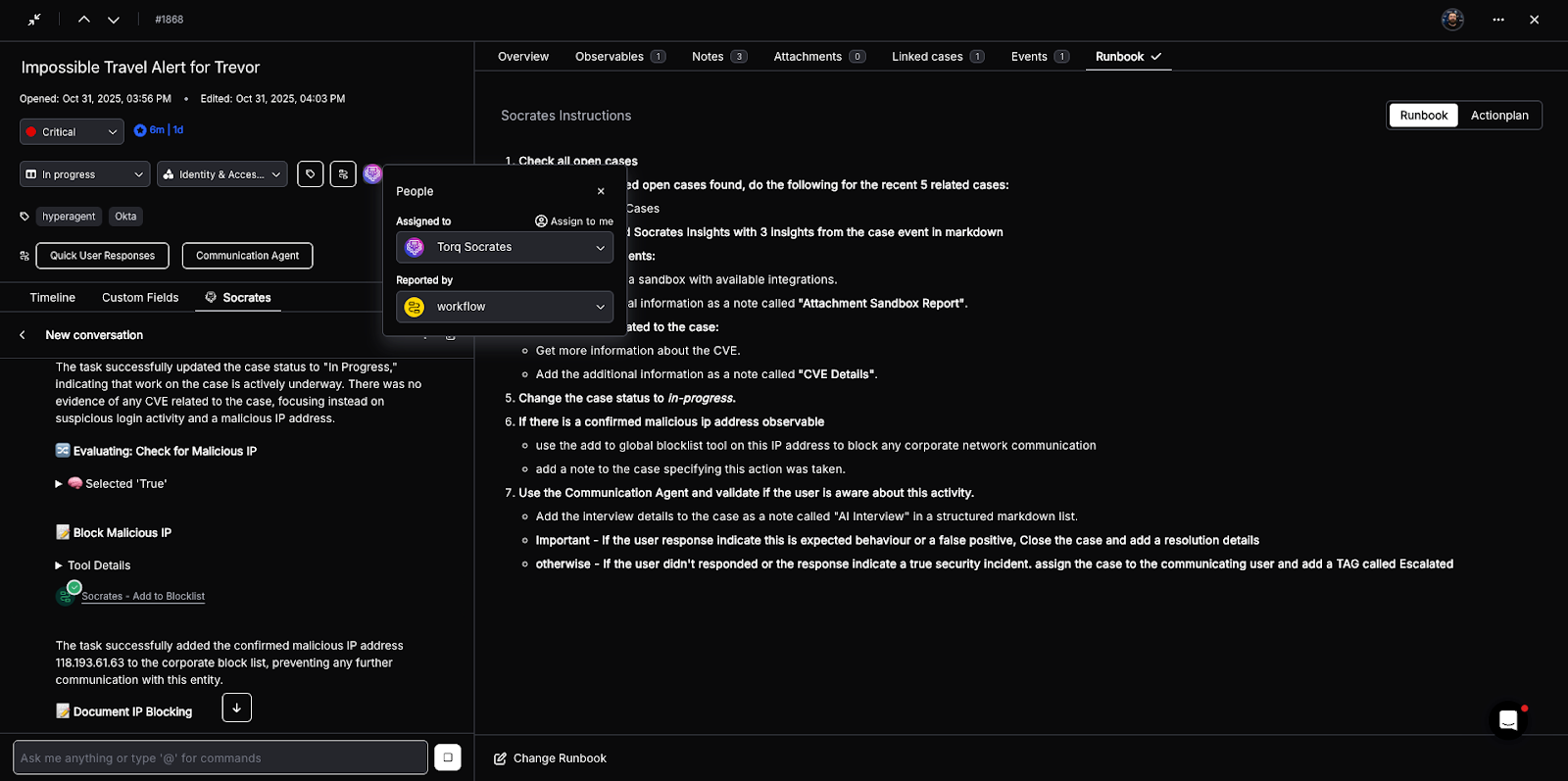
In over 90% of cases, Socrates — the AI SOC Analyst — has the tools necessary to remediate the case autonomously, following the steps laid out in the appropriate remediation runbook. Every AI action is thoroughly documented, with immutable execution logs and transparent decision-making processes.
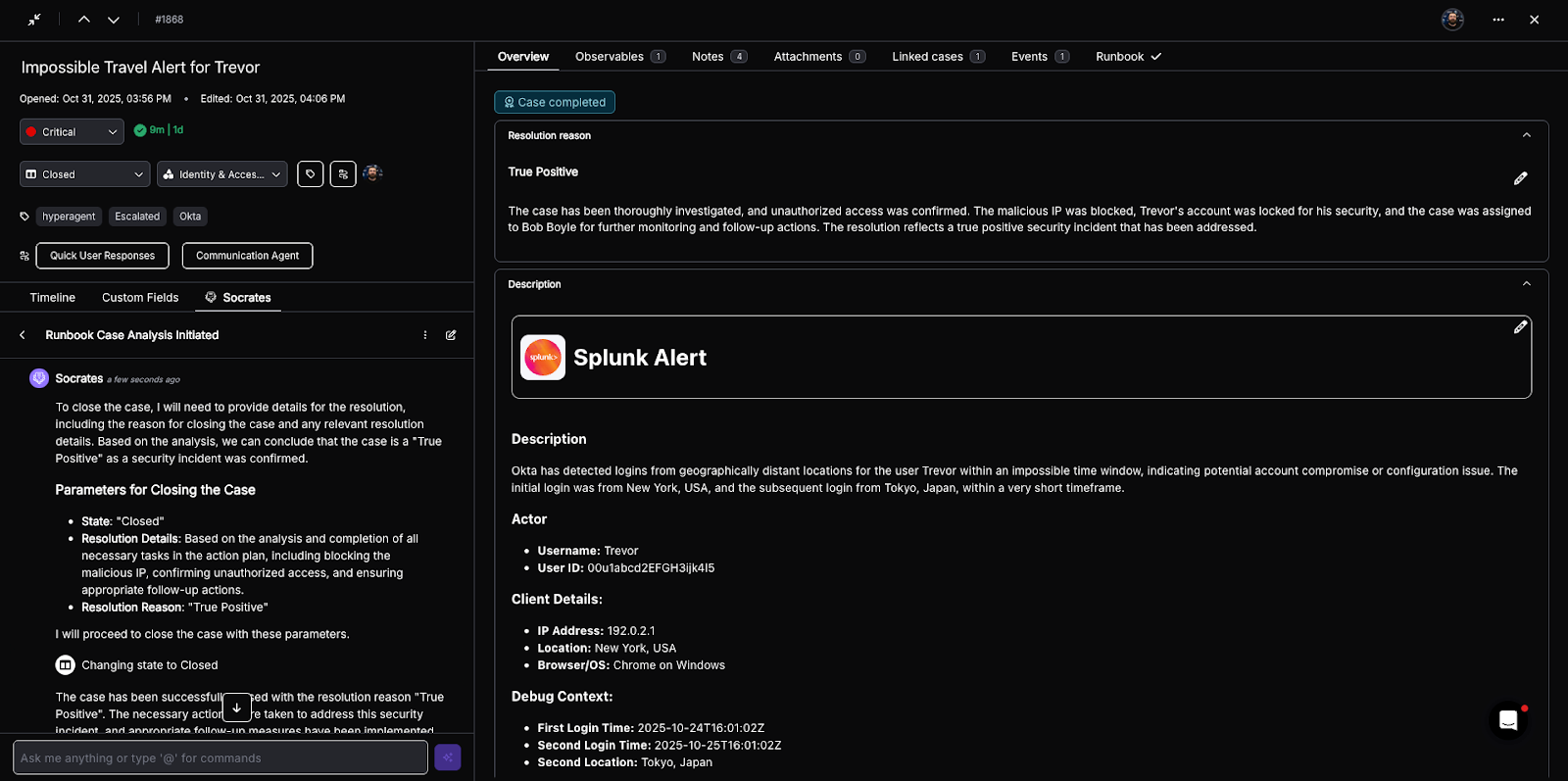
Once the incident is contained and the risk is remediated, the case is closed, and an AI-generated resolution note is added. If necessary, the case will be assigned to a human analyst for any further action — such as following up with a user whose account was locked, or assigning additional security awareness training.
What Makes Torq Case Management Different
Architecture-Level Advantages
- Event-driven: Built on an asynchronous, distributed event system that handles millions of concurrent actions with zero blocking.
- Schema-agnostic: Accepts unstructured JSON payloads and normalizes them into a consistent internal data model for cross-tool correlation.
- API-first design: Every case, enrichment, and action is addressable via REST and GraphQL APIs for seamless integration with custom tooling.
- Immutable state engine: Every field modification is versioned; every state change is logged — ensuring compliance, auditability, and forensic traceability.
- Elastic scalability: Dynamic worker scaling enables horizontal growth across clusters without downtime, supporting multi-region, multi-tenant SOCs.
AI + Deterministic Reliability
Torq blends agentic AI with deterministic control, ensuring automation remains explainable and compliant.
- LLM-based reasoning for analysis and enrichment
- Deterministic “approval gates” for containment or deletion actions
- Immutable logs of every AI recommendation, human correction, and execution
- Continuous learning from resolved cases to refine triage logic
This combination delivers both speed and trust, balancing AI autonomy with human oversight — a key reason enterprises choose Torq over less mature “workflow emulators.”
Hyperautomation
Torq unifies detection, enrichment, workflow, and audit into a single case lifecycle. Unlike platforms that bolt ticketing onto automations, Torq’s cases are the automation — dynamically updating with every new event, IOC, and workflow execution.
- Auto-populates with threat, asset, and user context
- Logs every enrichment, containment, and analyst action
- Enables one-click actions (isolate, revoke, block) from within the case
- Generates immutable audit trails and timeline visualizations
Real-Time Collaboration
Torq’s enterprise case management syncs context, chat, and action in one workspace — automatically updating as workflows execute.
- Live “war rooms” that connect SOC, IT, and compliance teams
- Real-time updates on findings, analyst notes, and playbook actions
- Integrations with Slack, Teams, and ServiceNow for seamless handoffs
- Cross-functional collaboration for HR, Help Desk, or BI teams — without requiring platform logins
Built for MSSPs and Global Enterprises
Torq’s multi-tenant case management enables managed security service providers and large organizations to scale horizontally, managing hundreds of customers or internal business units through a unified platform.
- Templates and reusable workflows accelerate onboarding
- Shared automations across tenants while keeping data fully isolated
- Unified analyst queue that spans customers, with precise access controls
- Faster SLAs, consistent reporting, and stronger margins for MSSPs
Case Management for the SOC of Tomorrow
Case management is no longer about tracking what happened but orchestrating what happens next. Torq HyperSOC™ transforms every case into a living, automated workflow that connects people, processes, and AI in real time.
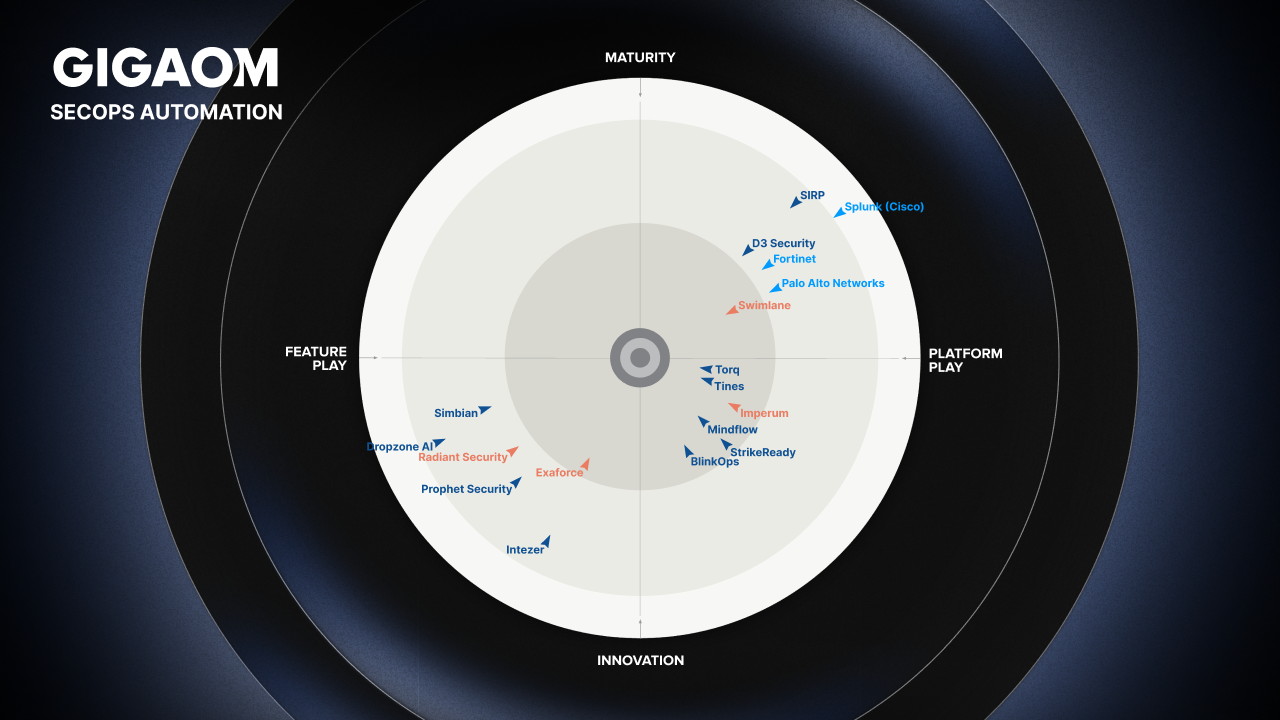
And industry validation backs it up: The 2025 GigaOm SecOps Automation Radar Report named Torq a Leader and Fast Mover for execution-based automation, giving Torq Enterprise Case Management a top score in this area.