Contents
Get a Personalized Demo
See how Torq harnesses AI in your SOC to detect, prioritize, and respond to threats faster.
Hyperautomation has become the new standard for modern organizations that want to move faster, work smarter, and operate at scale.
By combining AI, orchestration, and low-code technologies, Hyperautomation enables teams to automate complex business and IT operations end-to-end — including those that previously required human judgment. For security operations, this means faster detection, smarter response, and a foundation for autonomous defense.
Hyperautomation Explained: What It Means for Businesses
So, what is Hyperautomation? It’s a strategic business approach that unifies multiple automation technologies to streamline and speed up complex processes end-to-end. While traditional automation focuses on repetitive, rules-based tasks, Hyperautomation layers in intelligence, adaptability, and orchestration for machine-speed efficiency.
It connects systems, learns from data, and adapts dynamically to changing conditions — allowing businesses and security teams to achieve true operational agility through advanced technologies like artificial intelligence and robotic process automation (RPA).
Learn more about security Hyperautomation >
Automation vs. Hyperautomation: Key Differences
At a glance, automation and Hyperautomation sound similar, but they solve very different problems in cybersecurity. Traditional automation handles simple, repetitive tasks. Hyperautomation spans systems, layers in AI-driven decision-making, and coordinates human-machine collaboration at scale. It’s about full lifecycle automation — detection, triage, enrichment, response, and resolution — across multiple domains.
In cybersecurity, this means moving beyond automating password resets or phishing reports. Hyperautomation empowers your security operations center (SOC) to autonomously detect threats, prioritize alerts, trigger tailored responses, and continuously optimize based on results.
| Automation | Hyperautomation |
|---|---|
| Automates individual, repetitive tasks | Automates entire processes end-to-end |
| Script-based, static workflows | Dynamic, adaptive, and AI-driven workflows |
| Limited to known rules | Learns and evolves from data and context |
| Requires human oversight | Enables human-on-the-loop operation |
| Improves efficiency | Transforms scale, speed, and intelligence |
How Hyperautomation Tools and Platforms Work: A Step-by-Step Guide
Hyperautomation isn’t one tool — it’s a coordinated ecosystem. It connects multiple Hyperautomation technologies into a single framework, typically combining:
- GenAI and agentic AI for decision-making and contextual awareness
- Low-code/no-code platforms for fast workflow building without extensive coding
- Business process management for orchestrating complex workflows
- Integration platforms for connecting apps, tools, and systems
- Analytics and reporting tools for measuring performance and optimizing automations over time
Hyperautomation can adapt — systems can dynamically adjust workflows, update rules based on new data, and seamlessly coordinate human and machine collaboration.
Here’s how a typical Hyperautomation platform functions:
- Data capture and integration: The system collects data from multiple sources, including SIEM, cloud infrastructure, and endpoint telemetry, to create a unified data foundation.
- Orchestration: Hyperautomation maps workflows and identifies opportunities for intelligent orchestration.
- AI: AI models analyze data, make predictions, and recommend actions.
- Automation and execution: Low-code/no-code tools and bots execute complex tasks instantly — from case management to threat containment.
- Monitoring and optimization: Real-time analytics and feedback loops allow continuous process refinement and performance tracking.
The Advantages of Hyperautomation
Hyperautomation technology transforms SecOps by delivering faster, smarter, and more scalable operations. Here’s a quick look at the biggest Hyperautomation benefits:
- Ease of use: With drag-and-drop interfaces and no coding required, anyone on the security team can create powerful automations in minutes. Complex threat responses become easy to build, deploy, and scale across teams without relying on the complexity of legacy SOAR solutions or waiting for custom coding.
- Lower costs: Dedicated expert support with no surprise consulting fees.
- Secure on-prem connectivity: Zero-trust agents connect hybrid environments securely.
- Flexible, full-stack automation: Integrate and automate anything across cloud, infrastructure, and on-prem systems.
Hyperautomation tools transform static operations into adaptive systems that learn, automate, and evolve — creating measurable efficiency across every layer of the enterprise.
From Automation to Hyperautomation
Security automation started with promise — but hit its limits fast. Legacy SOAR tools were designed to orchestrate basic security actions but broke down under the weight of modern security demands. Static playbooks, brittle integrations, and clunky interfaces turned what was supposed to be “automation” into yet another bottleneck.
Security teams needed a new way forward as threats grew faster, more dynamic, and more complex. Unlike SOAR, Hyperautomation doesn’t just automate a few steps; it transforms the entire SOC workflow.
It connects tools across your technology stack, enables context-aware decisions, and executes actions quickly. And because it’s built with low-code/no-code at its core, it empowers any analyst, not just engineers, to build, test, and deploy workflows in minutes.
Where SOAR failed to scale, Hyperautomation moves 10x faster with infinite extensibility, seamless integrations, and case management to reduce noise and prioritize what matters. It enables SOCs to go from “human-in-the-loop” to “human-on-the-loop,” directing strategy while AI and automation handle the grind.
When paired with agentic AI, Hyperautomation becomes the foundation of the autonomous SOC, which is a SOC where alerts are triaged, threats are hunted, incidents are remediated, and analysts stay focused on the big picture.
Hyperautomation Use Cases in Cybersecurity and IT Operations
Hyperautomation doesn’t just make your SOC more efficient — it can transform how your team works. Here are some ways where Hyperautomation delivers major impact for cybersecurity teams.
1. Incident Response
Hyperautomation enables end-to-end incident response without human bottlenecks. From initial detection and triage to investigation, enrichment, and remediation, intelligent SOC automation accelerates every phase of the process — reducing mean time to respond (MTTR) from hours to minutes.
2. Phishing
Phishing is a top entry point for attackers. Hyperautomation instantly identifies suspicious messages, quarantines affected inboxes, revokes compromised credentials, and notifies users — all without requiring analyst intervention.
3. Just-in-Time (JIT) Access Provisioning
Managing administrative privileges across a hybrid infrastructure can be a nightmare. Hyperautomation grants and revokes access dynamically based on workflows and business rules, reducing privilege creep and improving security posture.
4. Threat Hunting
With Hyperautomation, SOCs can continuously search for threats using AI Agents across SIEMs, EDRs, and identity platforms. It’s proactive defense — and it’s fast.
5. Identity and Access Management (IAM)
From self-service access validation to automatic account cleanup, Hyperautomation brings control and consistency to identity workflows, ensuring alignment without added complexity.
Hyperautomation with Torq: How to Get Started
Torq Hyperautomation™ combines agentic AI, low-code/no-code workflow building, and multi-system security orchestration into one unified experience. Whether you’re deploying across cloud, on-prem, or hybrid environments, Torq makes it easy to automate your entire SOC — without needing a single line of code.
Key benefits of Hyperautomating your security operations with the Torq platform include:
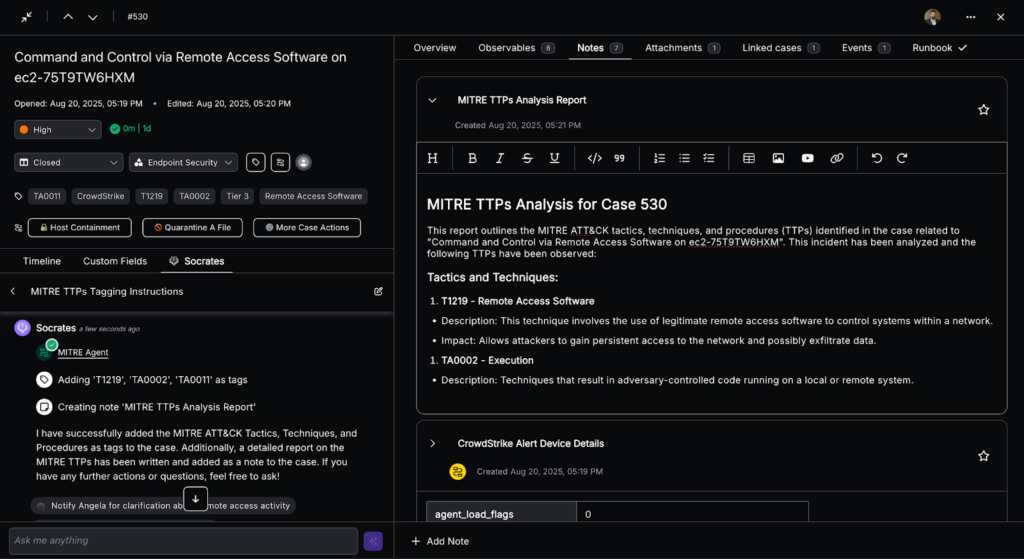
- AI-native: Orchestrate AI Agents that triage, investigate, and remediate alerts.
- No-code/low-code simplicity: Use drag-and-drop or natural language prompts to build advanced workflows in minutes.
- Massive integration library: Connect with any tool in your security stack and beyond.
- Case management: Prioritize and enrich alerts automatically, route decisions to the right people, and track everything.
As threats grow faster, more complex, and more automated, your response strategy has to evolve just as quickly. Whether you’re replacing legacy SOAR, reducing alert fatigue, or scaling your SOC, Torq’s Hyperautomation platform gives you the speed, intelligence, and flexibility to stay ahead.
Feeling the pressure to get more done faster across your security operations?
FAQs
Hyperautomation is an advanced business strategy that uses AI (artificial intelligence)and robotic process automation (RPA) to automate complex business processes end-to-end. Unlike standard automation tools that focus on repetitive, manual tasks, Hyperautomation orchestrates entire workflows across multiple systems — from data analysis and decision-making to execution.
It combines advanced technologies like natural language processing (NLP), process mining, and business process management (BPM) to help organizations improve efficiency, reduce human error, and accelerate digital transformation.
While RPA (robotic process automation) automates simple, rule-based tasks, Hyperautomation expands that capability with AI to handle more complex, dynamic, and unstructured scenarios.
- RPA: Executes fixed, repetitive workflows (like copying data between systems).
- Hyperautomation: Uses AI, BPM, and intelligent automation to analyze, decide, and automate processes that evolve over time.
Hyperautomation relies on an ecosystem of automation technologies that work together to create intelligent, self-improving systems. These include:
- Artificial intelligence (AI) for contextual understanding and decision-making
- Robotic process automation (RPA) for executing repetitive, rule-based actions
- Business process management (BPM) for orchestrating and optimizing workflows
- Process mining to discover and map inefficiencies in existing processes
- Natural language processing (NLP) to interpret and process unstructured data such as emails or documents
- Automation platforms that unify bots, analytics, and human oversight in one environment
Together, these tools turn fragmented automation into cohesive, intelligent, and automated processes.
Hyperautomation enhances efficiency by automating manual, repetitive tasks and enabling systems to learn, adapt, and optimize over time.
Through AIL, it can analyze vast amounts of operational data, identify bottlenecks, and continuously refine processes for better outcomes. By orchestrating business processes end-to-end, organizations reduce errors, cut costs, and speed up execution — freeing humans to focus on innovation instead of routine work.
The benefits of Hyperautomation extend across efficiency, intelligence, and scalability:
- Higher efficiency: Automates thousands of repetitive tasks with precision
- Improved accuracy: Reduces human errors in manual processes
- Faster decisions: Uses AI to analyze and respond instantly
- End-to-end automation: Unifies business process management with orchestration
- Scalability: Easily expands across business units and data systems
Smarter operations: Turns unstructured data into insights that drive outcomes
Hyperautomation is a cornerstone of digital transformation because it enables continuous innovation across every layer of the business. By integrating AI, RPA, BPM, and process mining, it transforms static operations into agile, intelligent automation ecosystems.
Organizations can scale processes faster, reduce costs, and empower employees with tools that amplify human capability — all while achieving measurable improvements in efficiency, compliance, and customer experience.