Contents
Get a Personalized Demo
See how Torq harnesses AI in your SOC to detect, prioritize, and respond to threats faster.
Security teams love Expel for its transparent Managed Detection and Response (MDR) and powerful investigative platform that brings clarity to alerts and incidents. Expel’s Workbench API gives you deep access into alerts, investigations, findings, comments, remediation actions, and much more — making it ideal for automation and orchestration.
But what if you could go beyond reporting and dashboards? What if your security operations platform could investigate, triage, and respond autonomously, driven by deterministic logic and AI?
That’s where Torq and Expel come together.
What Torq Adds to Your Expel MDR Workflows
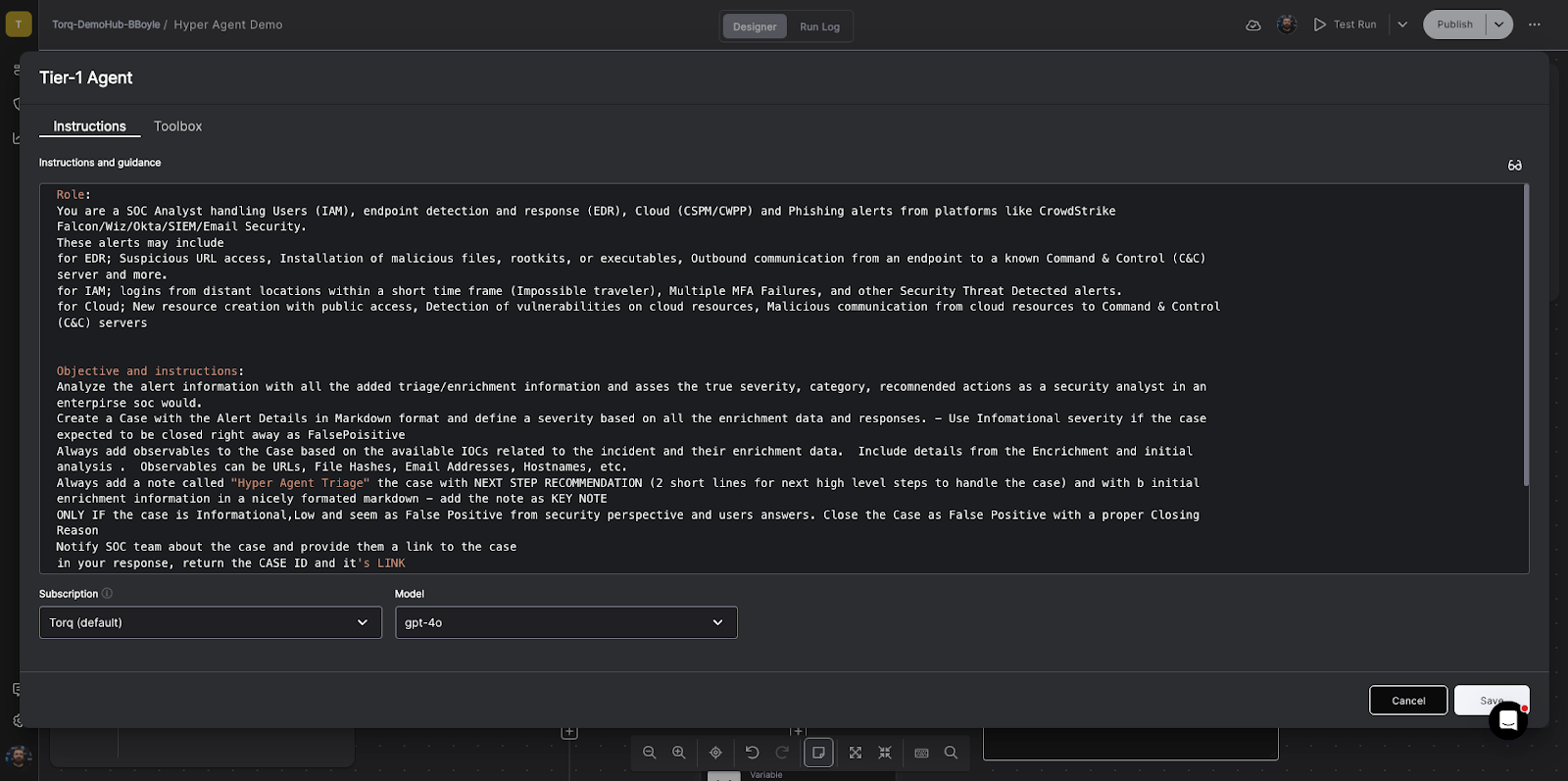
Traditional workflow builders help teams automate tasks. Torq goes further — enabling AI workflows that can reason, decide, and act without waiting on human input. With deterministic guardrails and agentic AI, Torq doesn’t just move data between tools; it investigates alerts, prioritizes risk, and executes response actions at machine speed. This is the difference between connecting tools and running security operations.
Torq gives you a powerful way to automate Expel’s API-accessible capabilities using:
- Deterministic playbooks: Clearly defined steps that follow your SOC processes.
- Copy-paste curl integrations: Every action can be triggered via REST with ready-to-use curl commands.
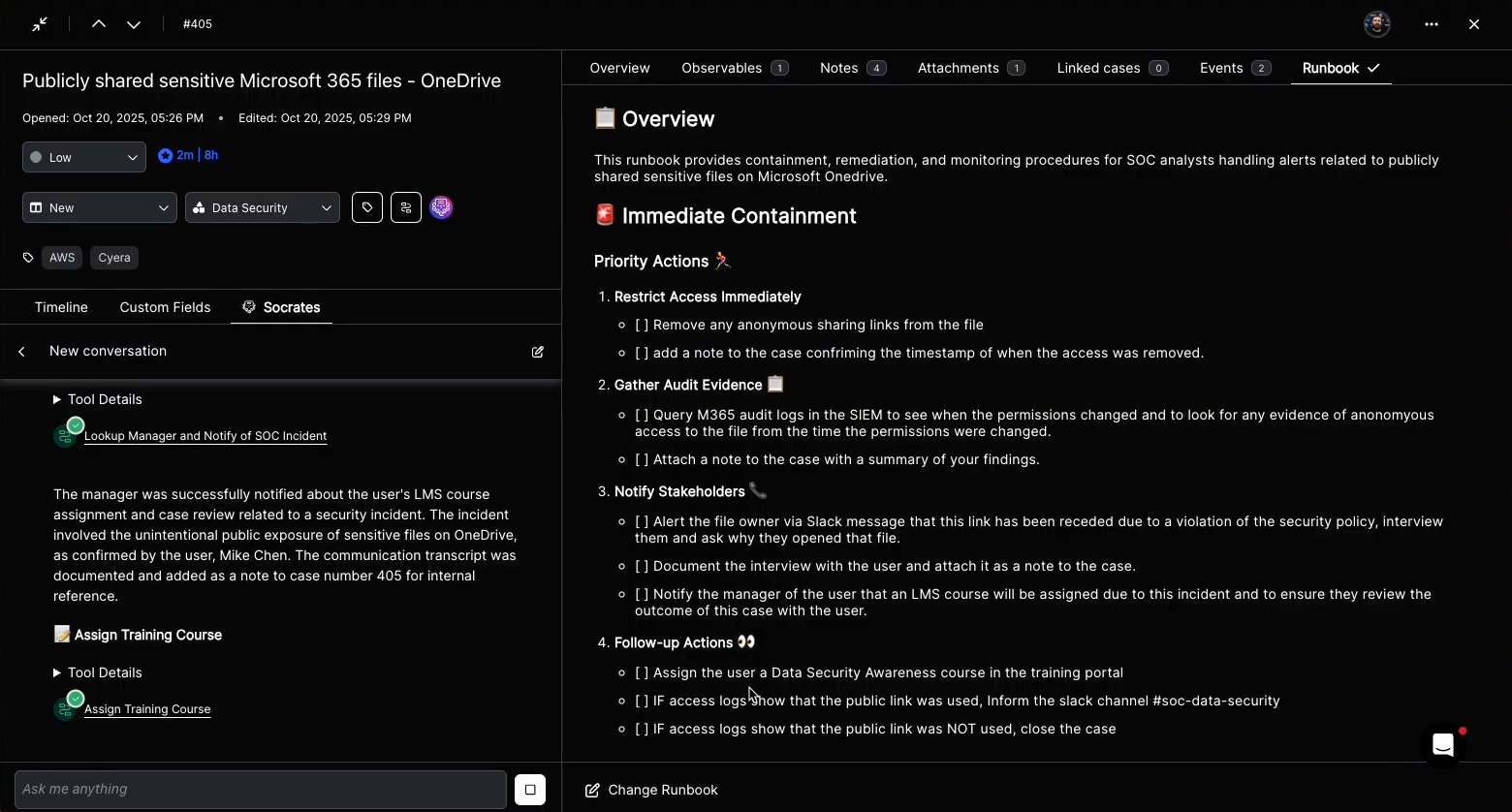
- AI Agents that act on your behalf: Triage, investigate, and update Expel data with natural language guidance and context.
- Bidirectional sync: Change Expel investigations, comments, findings, and more from Torq and reflect changes back in Expel automatically.
Core Expel Actions You Can Automate with Torq
Instead of starting from a blank canvas, Torq delivers production-ready playbooks. These playbooks include: built-in escalation logic and SLAs, AI governance and guardrails for approvals, and safety checks.
Below are the key Expel resources and interactions that Torq can orchestrate, pulling from both the Workbench API documentation and your existing set of Torq actions.
Investigation Lifecycle
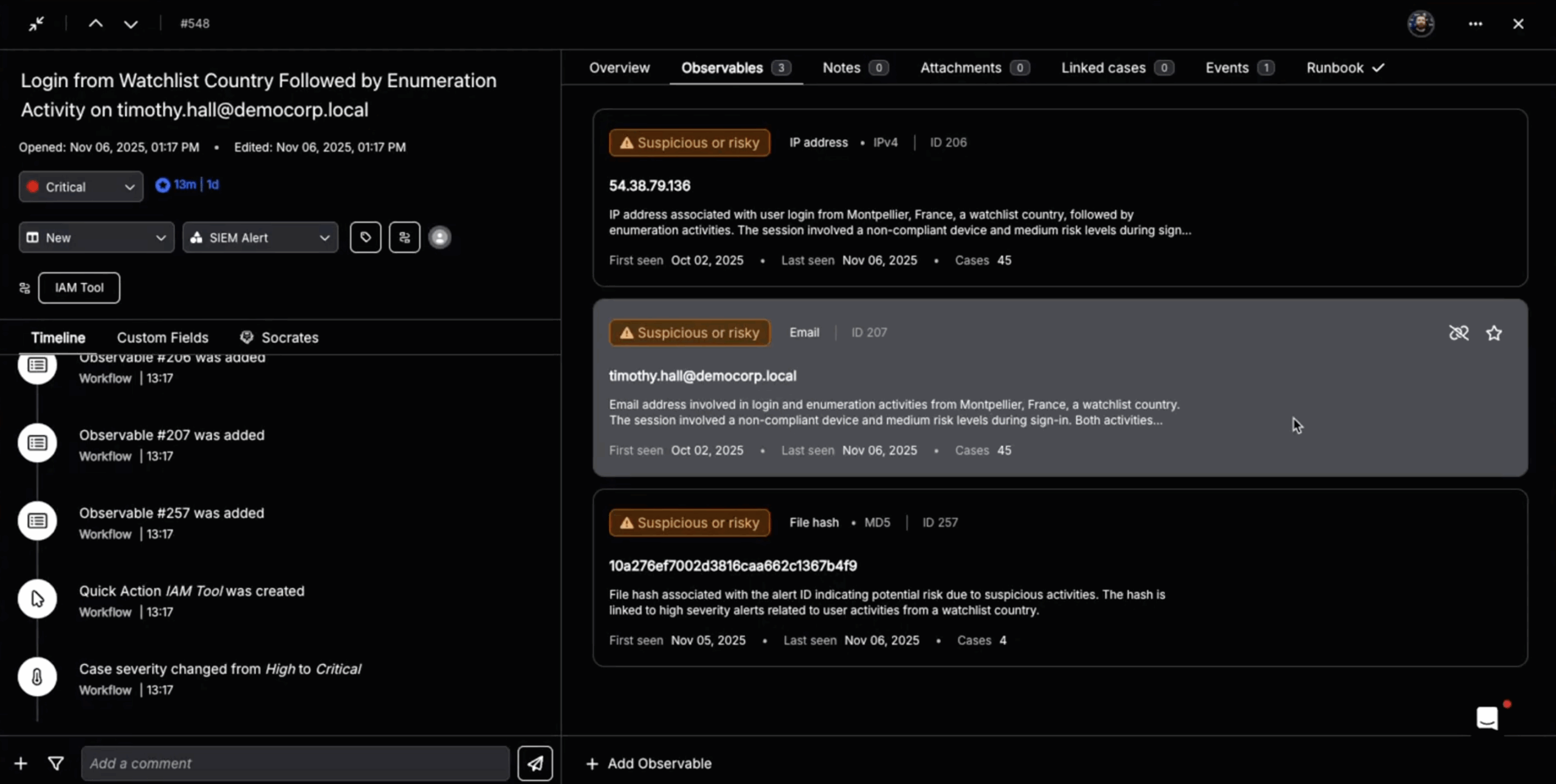
- Retrieve investigations for analysis and routing.
- Pull findings to understand what Expel SOC has determined.
- Review actions tied to investigations.
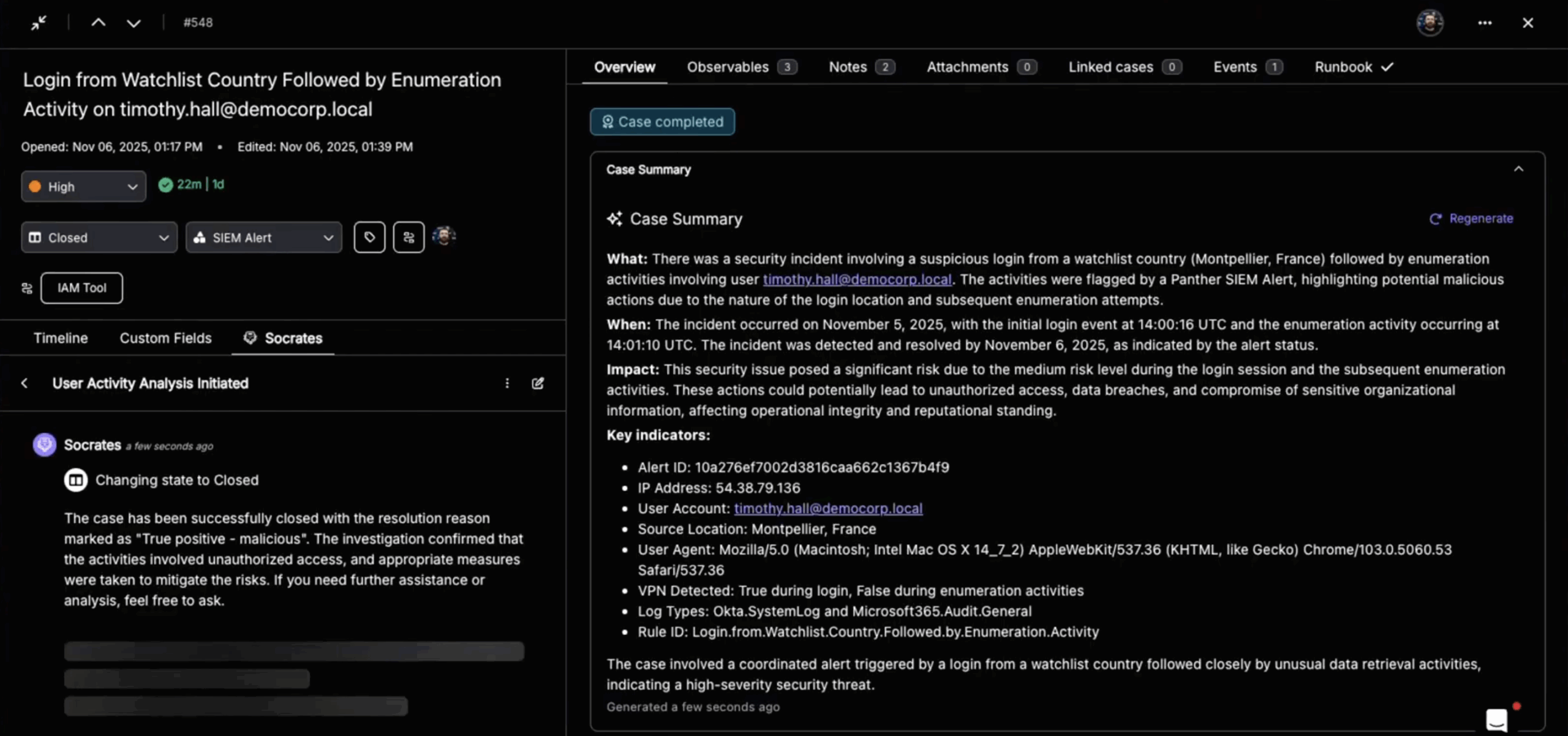
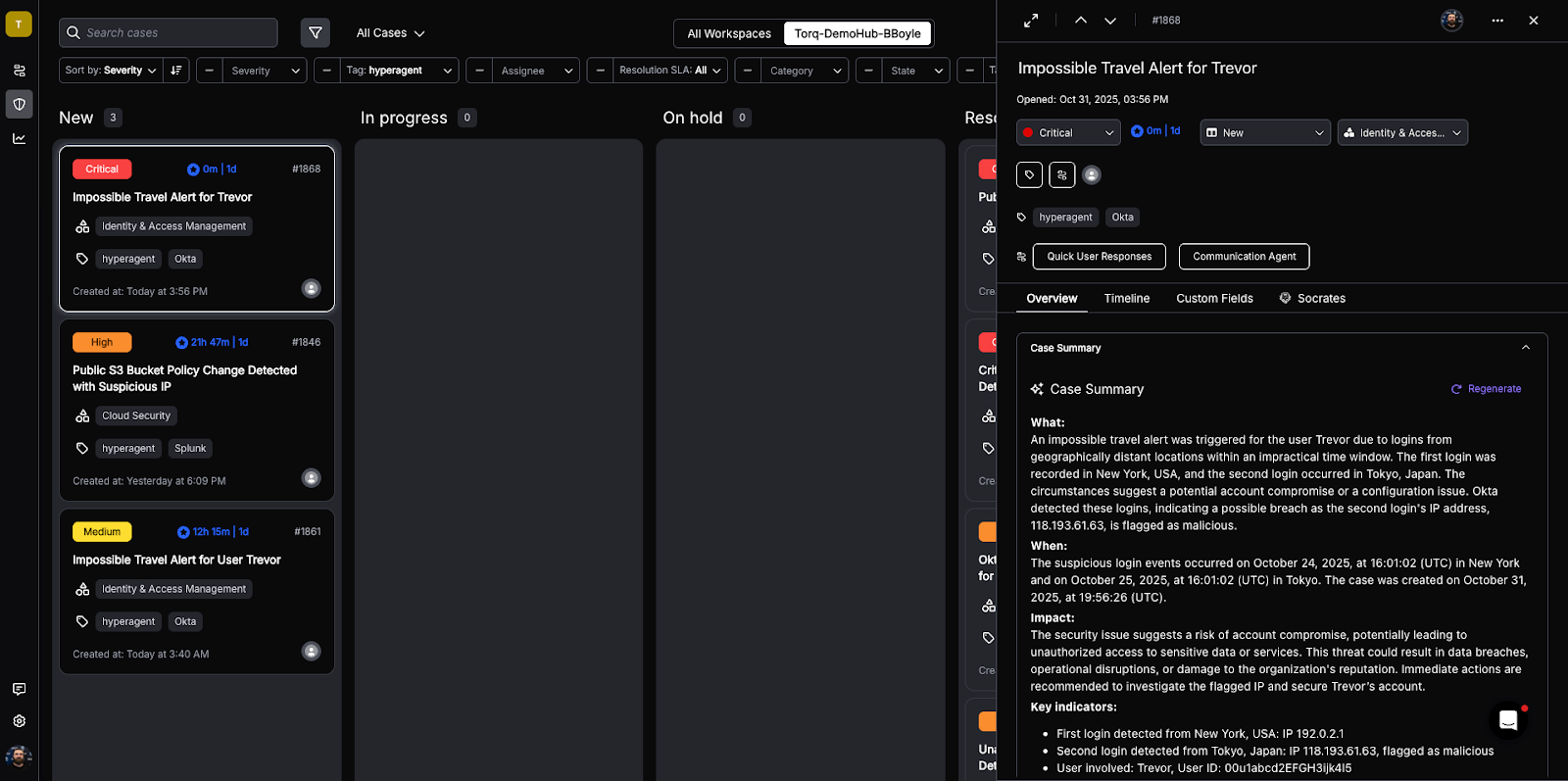
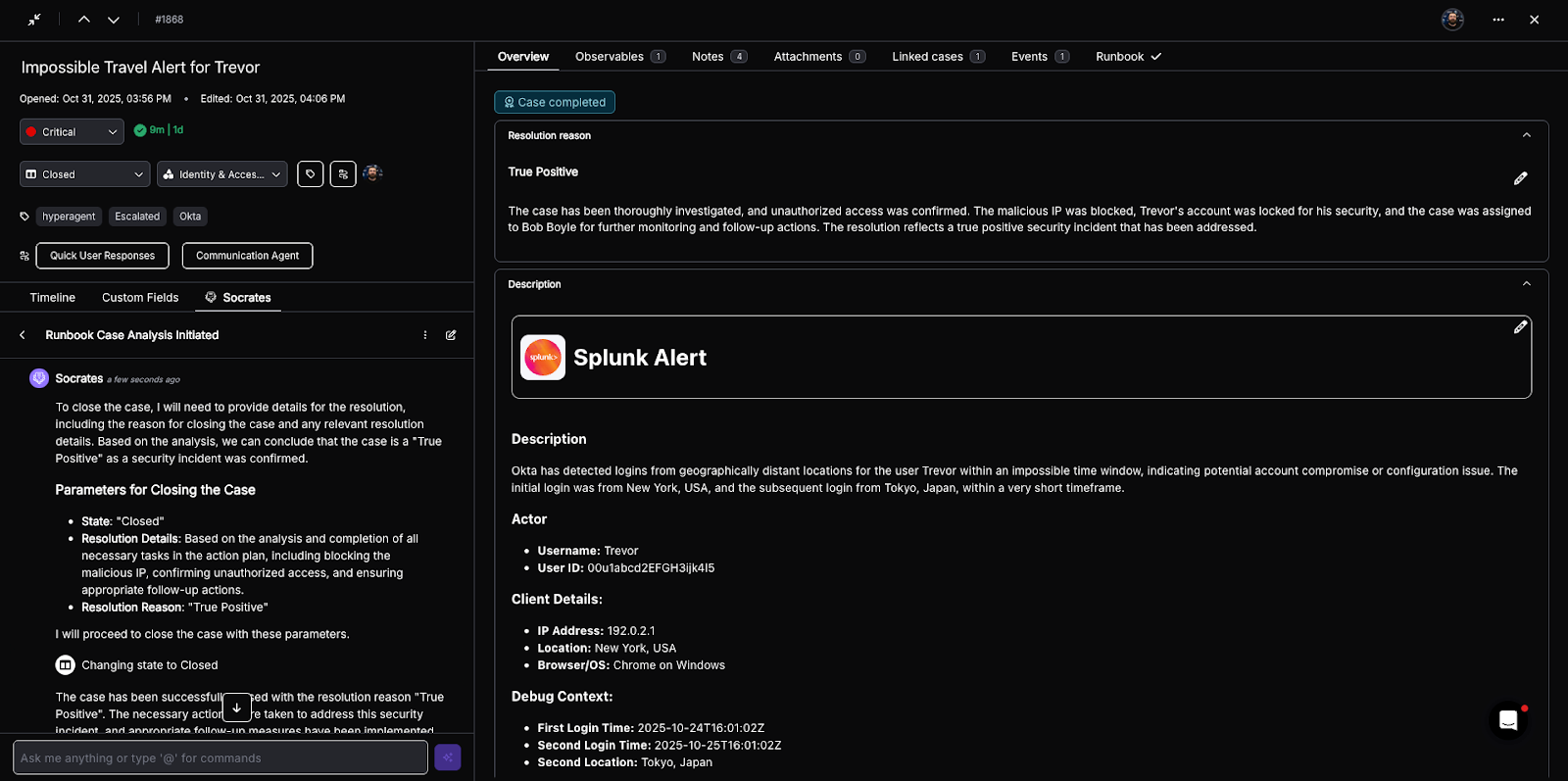
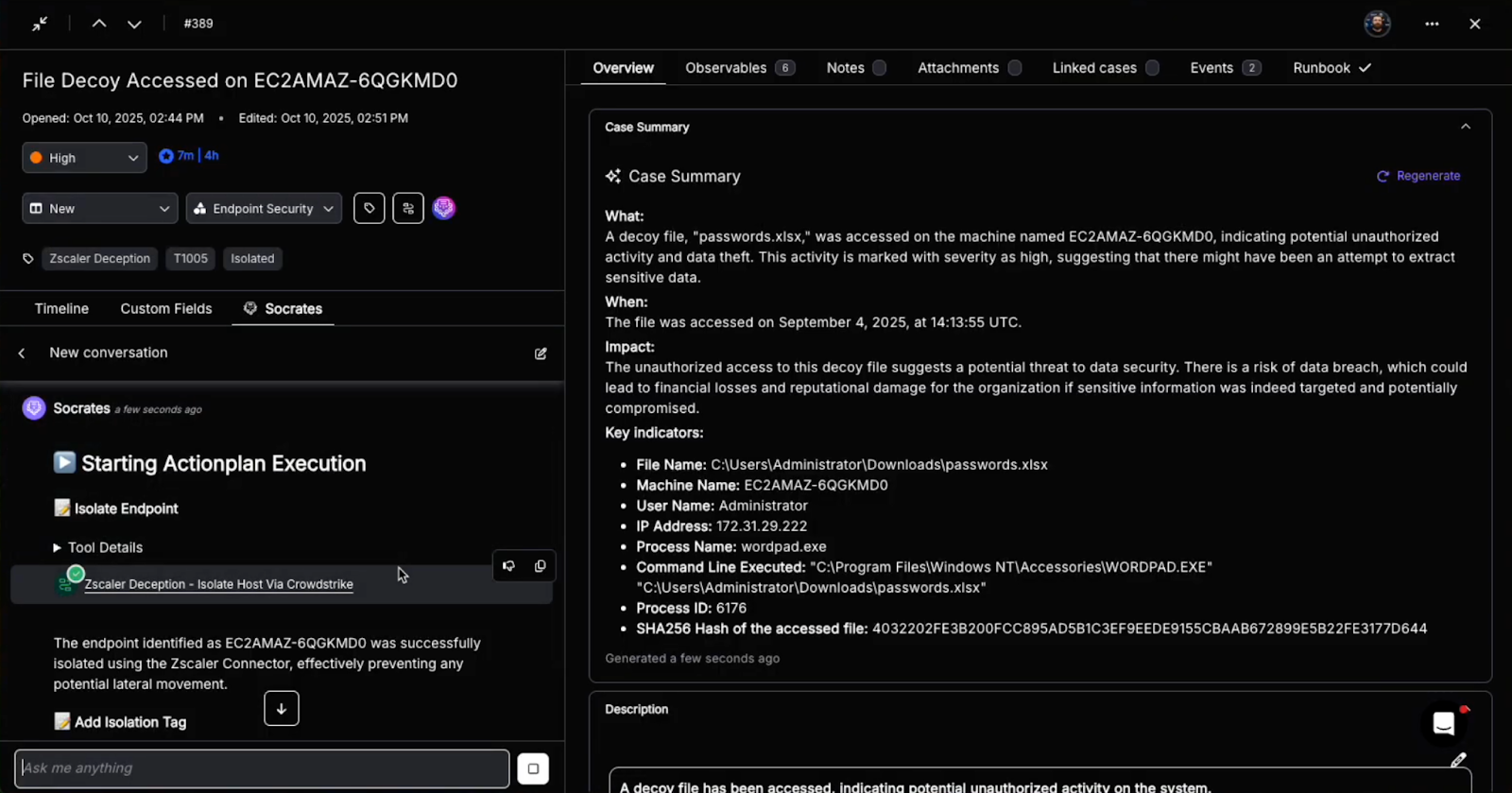
Torq playbooks can create new findings or update investigation fields using POST/PATCH calls via Expel’s API. These investigation-related resources give Torq the ability to see what’s happening in Expel and take action.
Alert Data and Comments
- Fetch alerts from Expel’s Workbench, filter by severity or source.
- Retrieve discussion threads on investigations.
- Log analyst notes programmatically or via AI Agent decisions.
Remediation Actions
- Understand the available actions for a given investigation or alert.
- Get detailed context around specific actions.
- Kick off remediation directly from Torq using curl-based API calls.
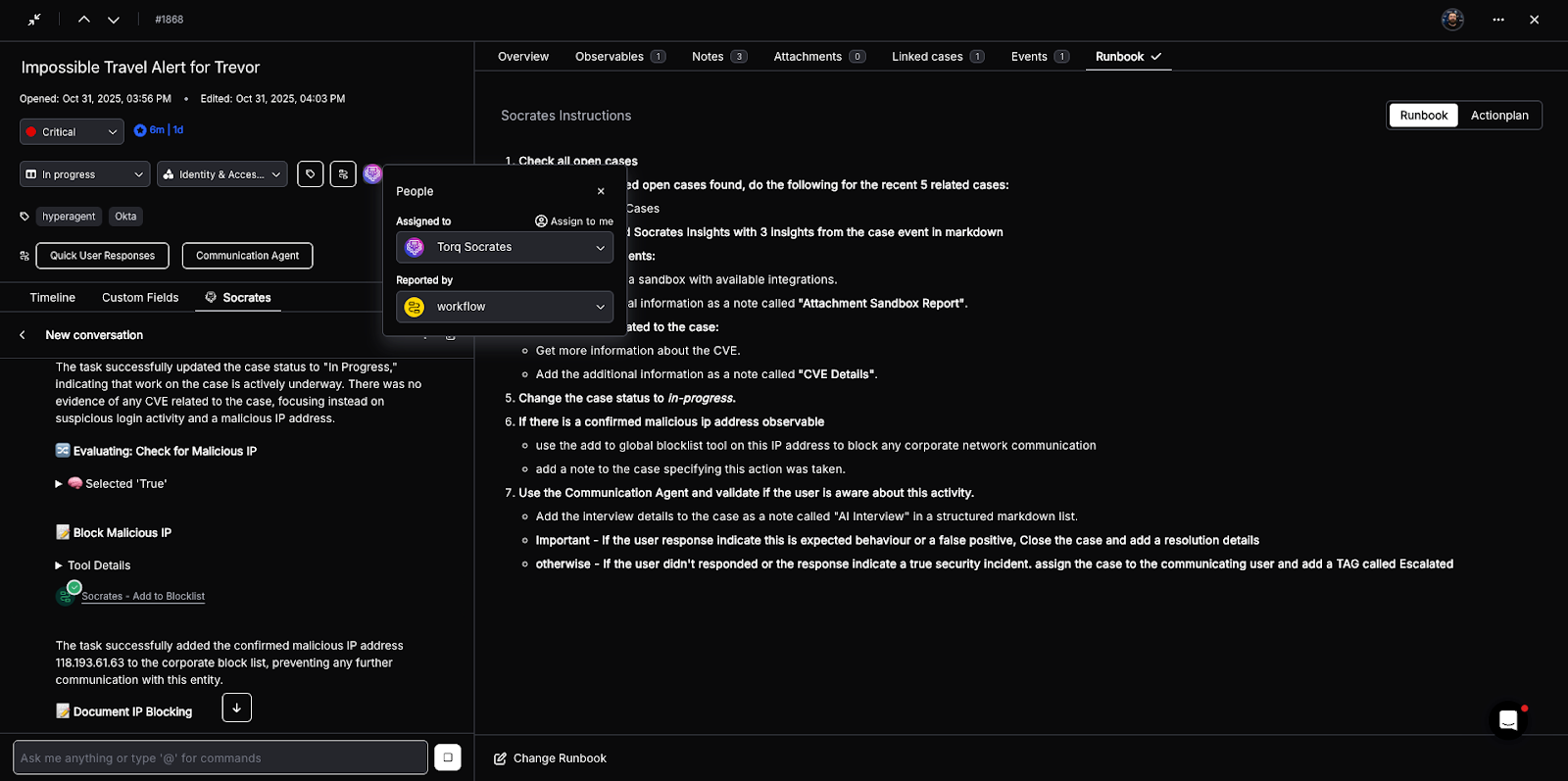
These actions let Torq trigger containment, cleanup, or other security responses in sync with Expel’s recommended workflows.
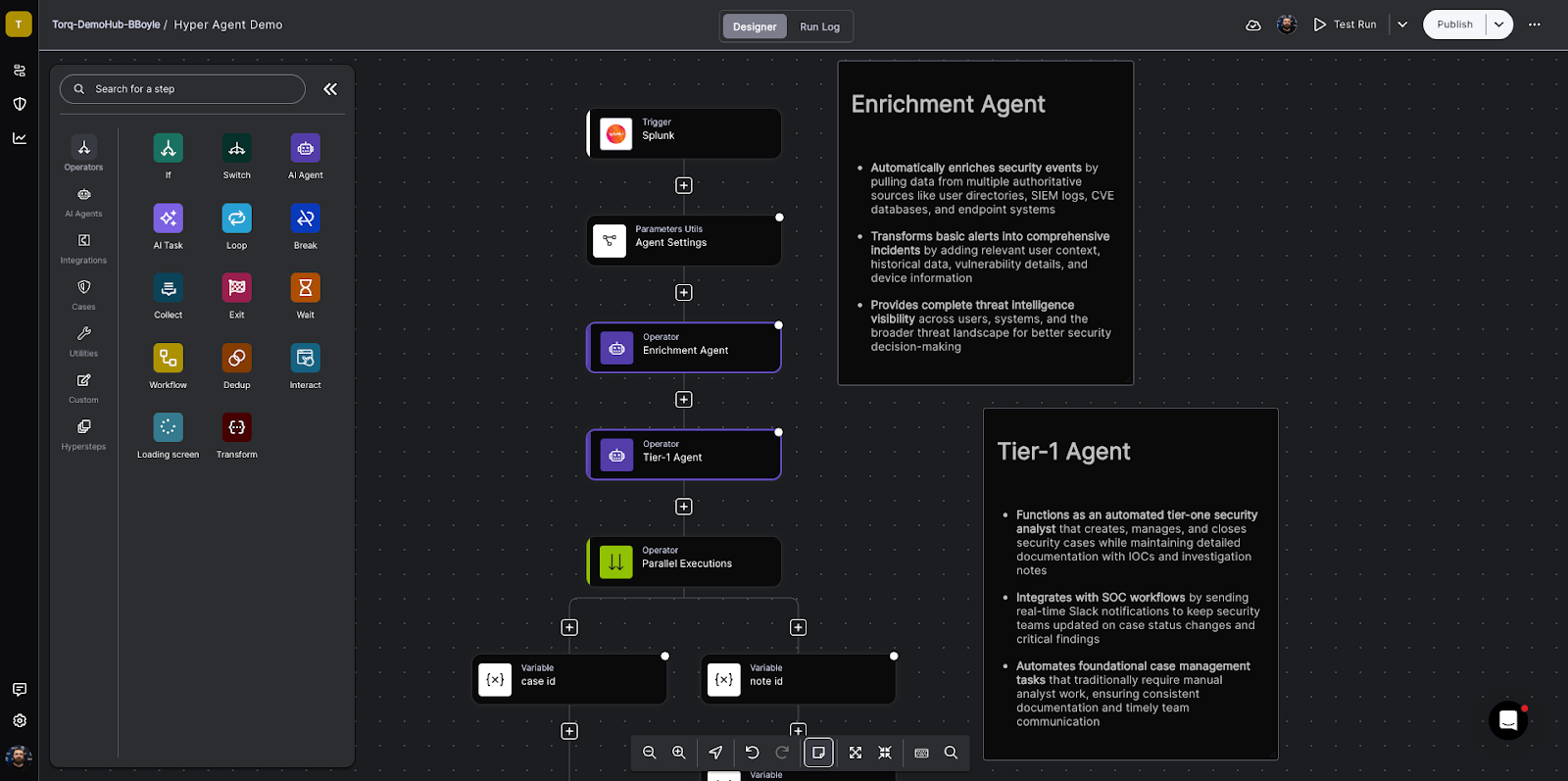
How We Implement This in Torq
1. Deterministic Steps You Control
Torq playbooks execute step-by-step logic that maps to how your SOC works.
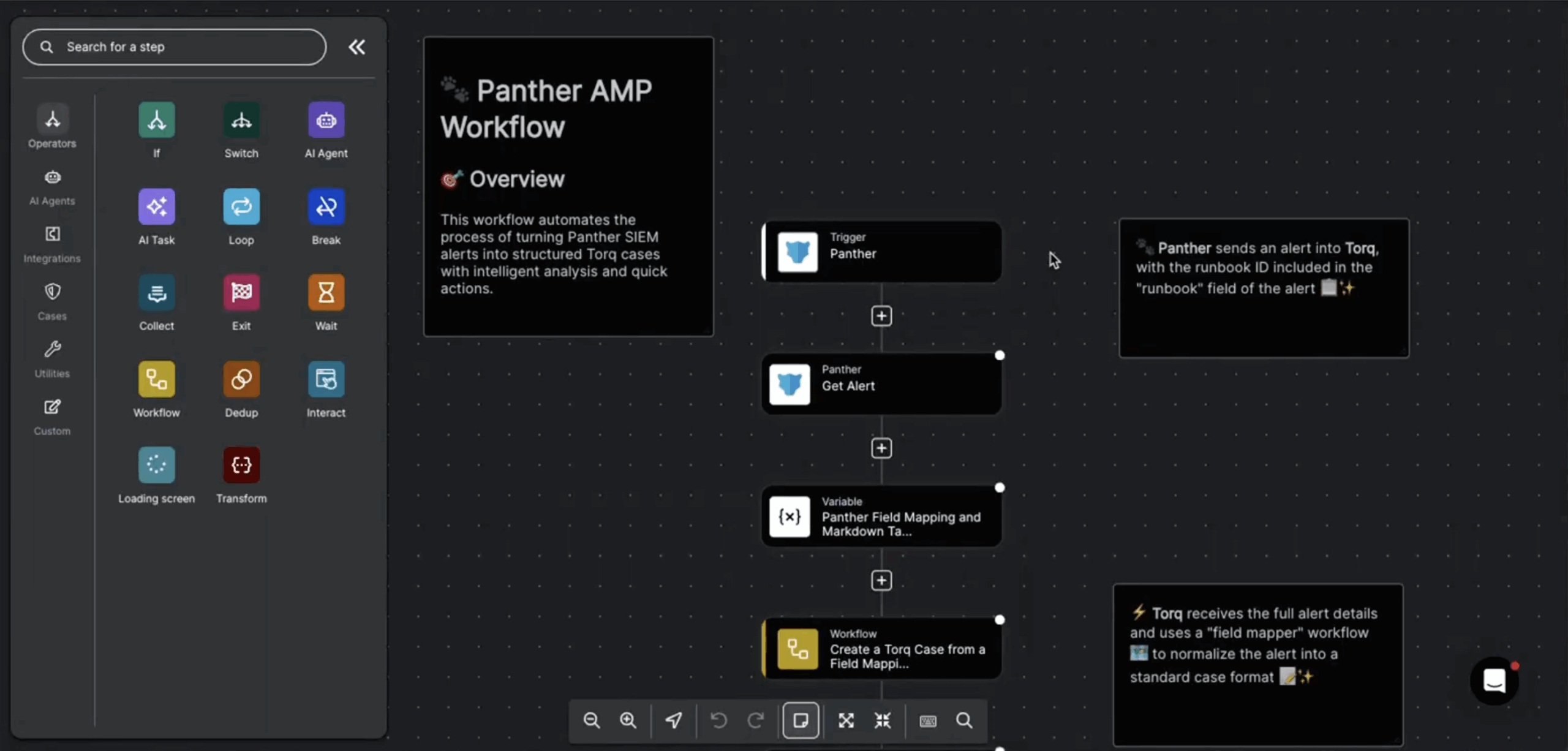
Step 1: Retrieve new Expel alerts
Step 2: Enrich context (SIEM, Endpoint, Threat Intel)
Step 3: Evaluate alert severity + indicators
Step 4: If criteria met → create investigation or escalate
Step 5: Write back comments, findings, remediation actions
2. Curl-Ready Integrations
Every API call Torq performs can be surfaced as a simple curl command for reuse or embedding.
curl 'https://workbench.expel.io/api/v2/expel_alerts?filter[status]=OPEN' \
-H "Authorization: Bearer $EXP_KEY"
3. AI Agents That Investigate Like Analysts
Torq’s AI Agents can:
- Query Expel for alert details
- Enrich with context from other systems
- Triage and suggest next steps
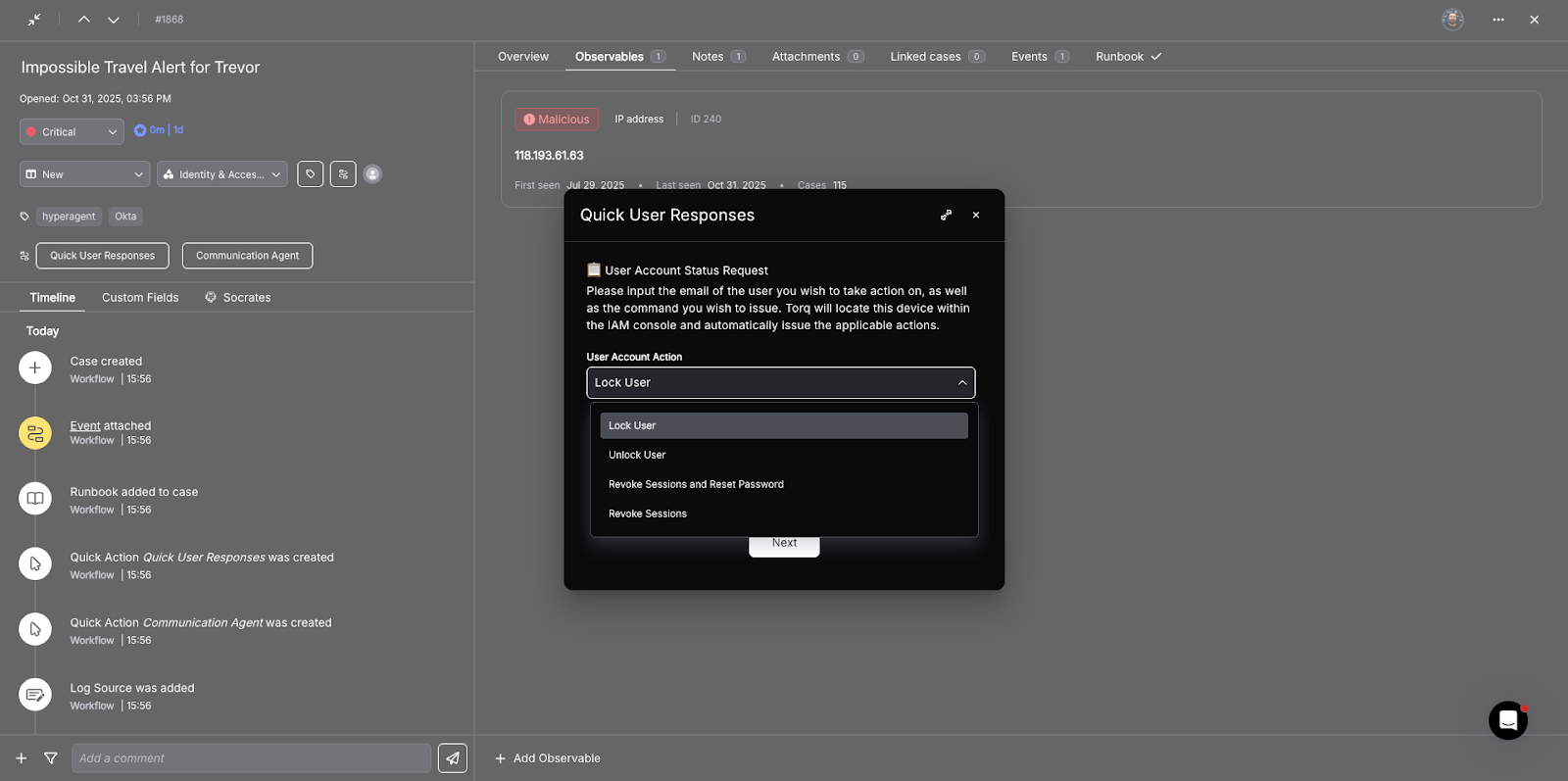
- Write back decisions as comments, tags, or remediation tasks
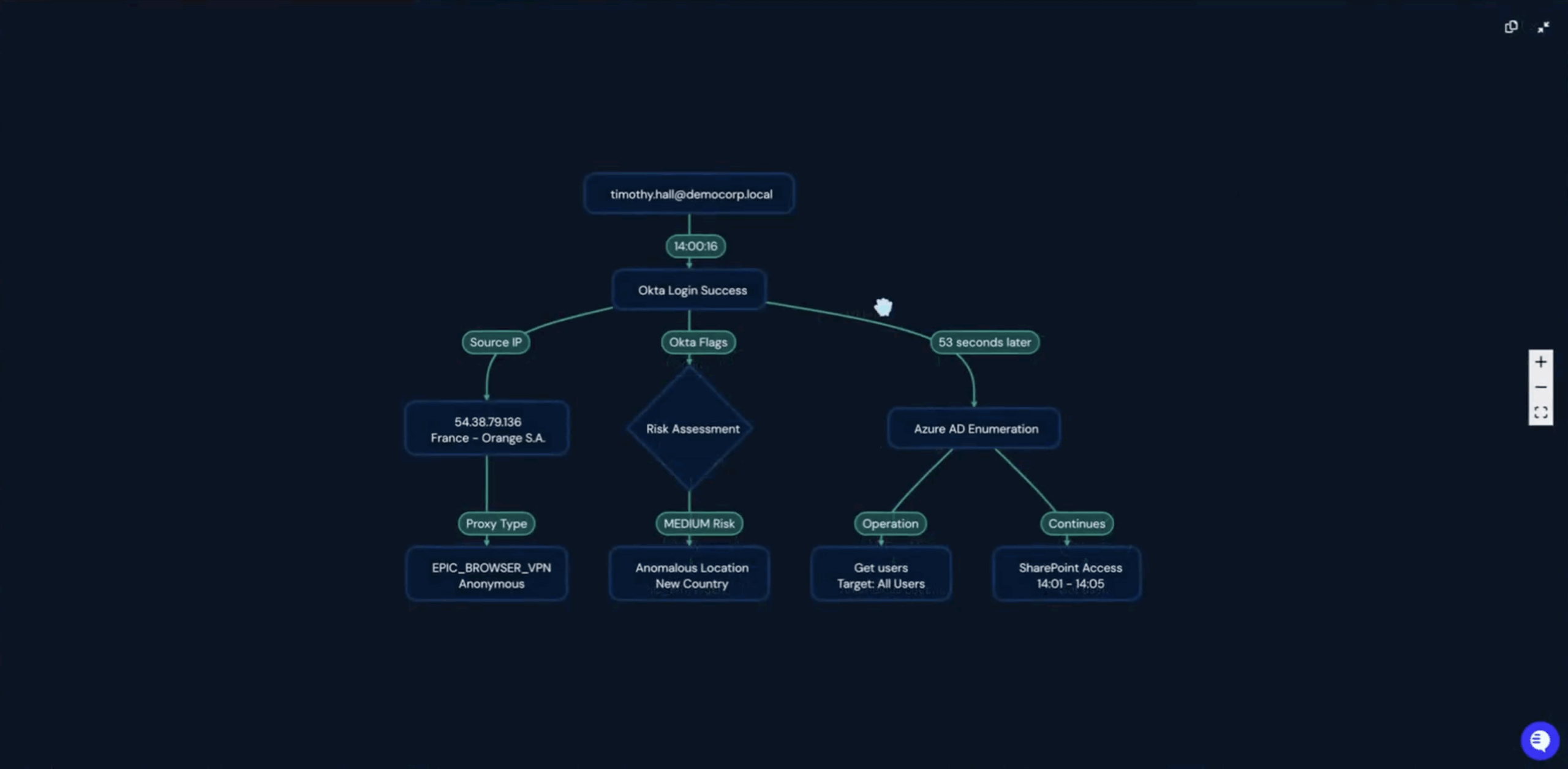
For example, an AI Agent can analyze five related Expel investigations, identify shared indicators, determine likely root cause, and update every case automatically — saving hours of analyst time.
4. Bidirectional Sync
Changes in Expel MDR — like an updated investigation status or new remediation details — can be reflected back to Torq playbooks, dashboards, and downstream tools automatically.
Real-World Use Cases: Torq + Expel
Automated Triage Pipeline
When a new alert arrives from Expel, Torq triggers a workflow. The workflow automatically enriches the alert by querying additional systems such as SIEMs, endpoint tools, or identity providers using predefined steps.
How Torq handles it:
- Enrichment steps gather context (related alerts, user attributes, or asset details).
- Conditional logic evaluates alert fields and enrichment results to determine the next action.
- Based on these conditions, the workflow can create or update a Torq case, add findings or comments, and route the case to the appropriate queue or team.
All actions occur immediately as part of the workflow execution, without requiring an analyst to collect or enter data manually.
Remediation Acceleration
When alert severity or defined conditions meet response criteria, Torq workflows can initiate containment or remediation actions through supported integrations.
How Torq handles it:
- Workflow steps invoke remediation actions via REST API calls or native integration actions.
- Actions include isolating a host, disabling an account, blocking an IP address, or triggering response actions exposed by Expel or other security platforms.
- These steps are executed automatically based on workflow logic, not manual intervention.
Because predefined workflow conditions drive remediation, response actions occur consistently and quickly, while still remaining fully visible in execution logs and case records.
Investigation Orchestration
Torq workflows can be triggered by events or on a scheduled basis to coordinate investigation activity across multiple alerts, cases, or teams.
How Torq handles it:
- Scheduled workflows can query systems for open cases, active alerts, or unresolved findings.
- Aggregated results can be summarized into case updates, notifications, or reports.
- Additional workflows can be triggered to collect deeper context, request analyst review, or assign follow-up tasks.
This approach allows teams to standardize investigation processes, maintain visibility across concurrent incidents, and ensure no cases are missed.
Why Torq + Expel Is a Game-Changer for Security Operations
Combining Expel MDR and Torq turns great investigations into fast, repeatable outcomes. With the Expel + Torq integration, you can automate the full lifecycle — from alert intake and enrichment to investigation updates and remediation — using deterministic playbooks, AI-driven SOC workflows, and bidirectional sync.
Ready to operationalize it? Get started with our Don’t Die, Get Torq manifesto.