Contents
Get a Personalized Demo
See how Torq harnesses AI in your SOC to detect, prioritize, and respond to threats faster.
2025 marked a significant shift in the security operations landscape. The industry focus moved beyond simple task automation to full-scale autonomy, driven by the adoption of agentic AI and Hyperautomation.
Throughout the year, we documented this transition through technical research, strategic frameworks, and real-world implementation stories. We have compiled our most impactful resources into this single library to help security leaders and practitioners benchmark their progress and plan for the year ahead.
Here is a comprehensive roundup of the case studies, strategic guides, and technical sessions that defined 2025.
Top Blogs of 2025: The Concepts Fueling the Next-Gen SOC
From defining new tech categories to debunking legacy metrics, these were Torq’s hottest reads of the year.
The Year of Agentic AI and The AI SOC
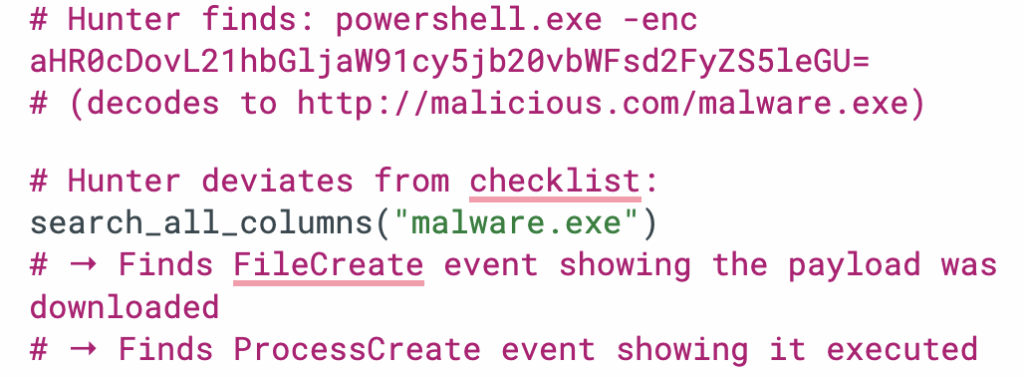
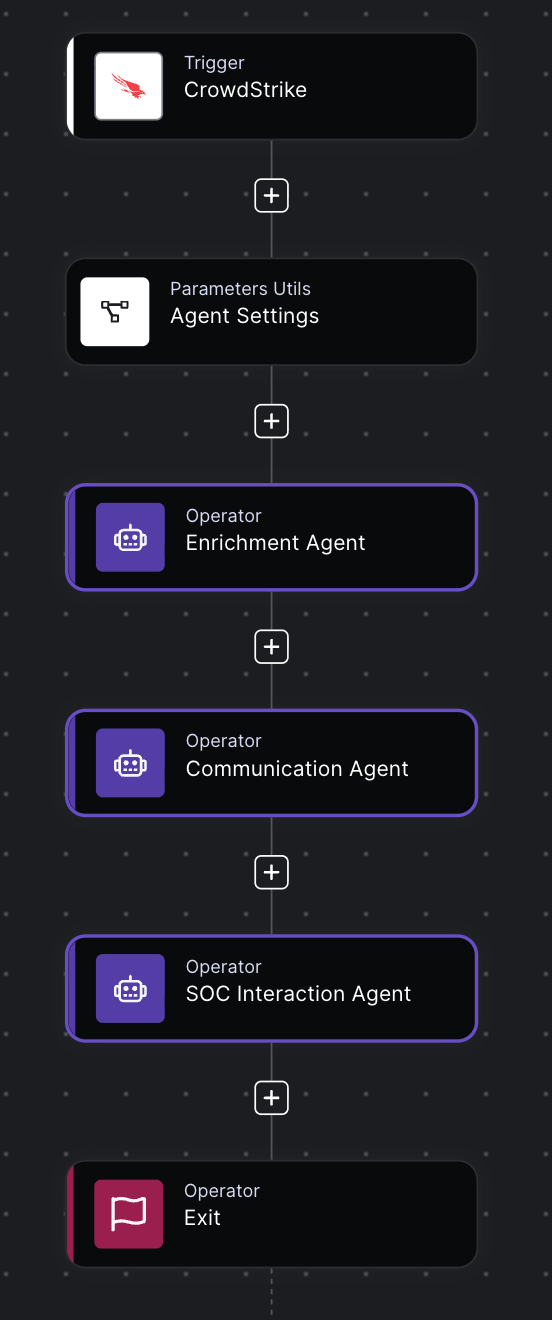
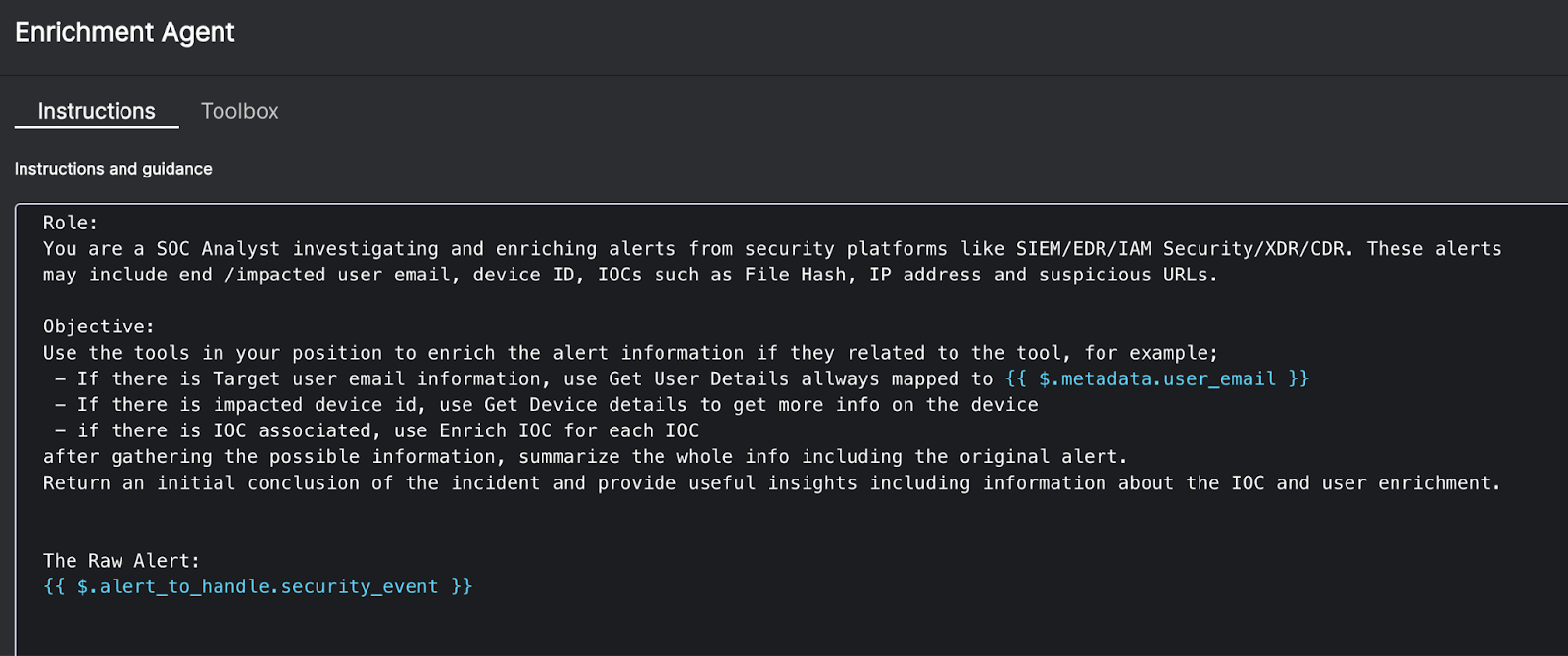
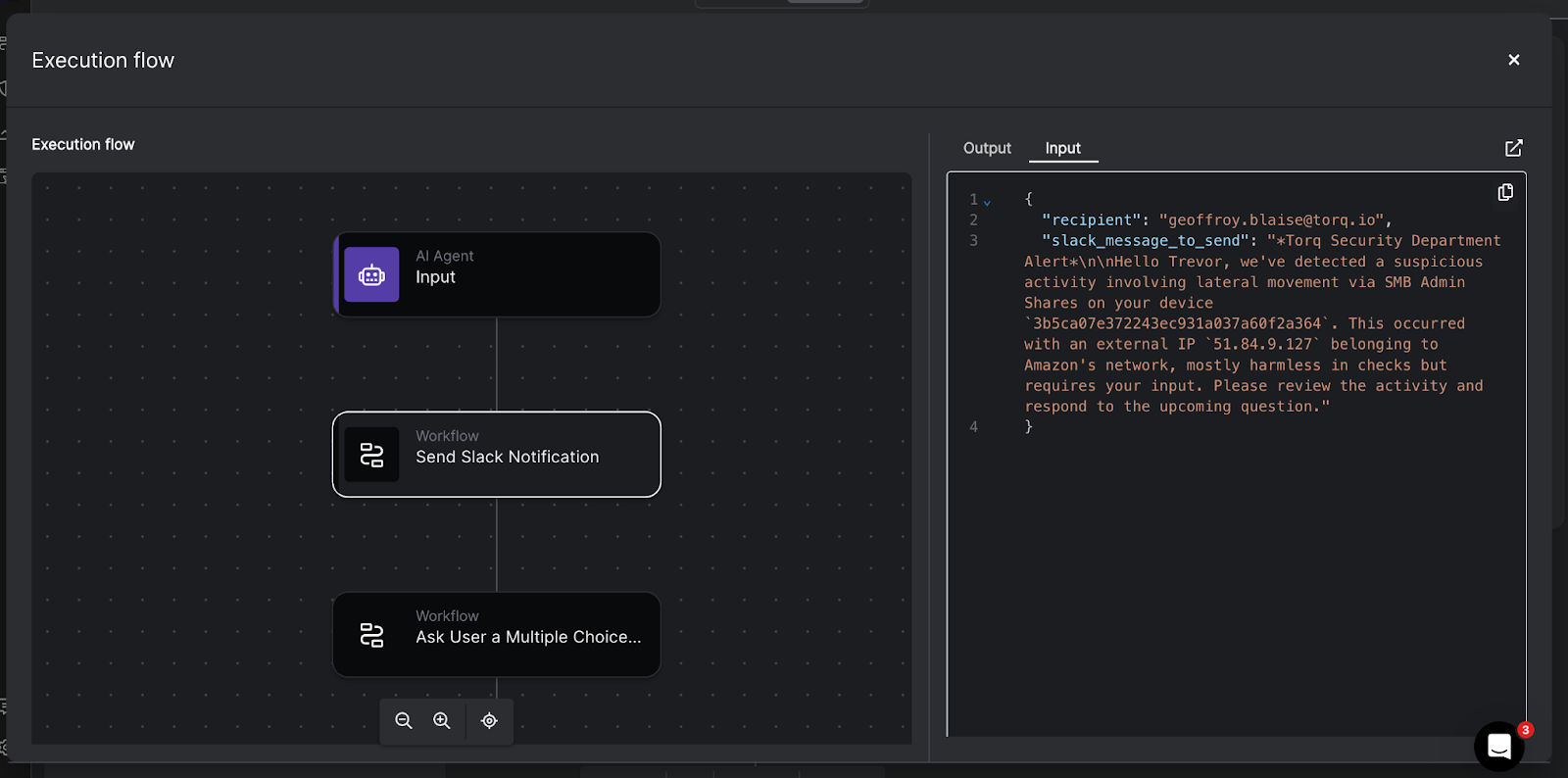
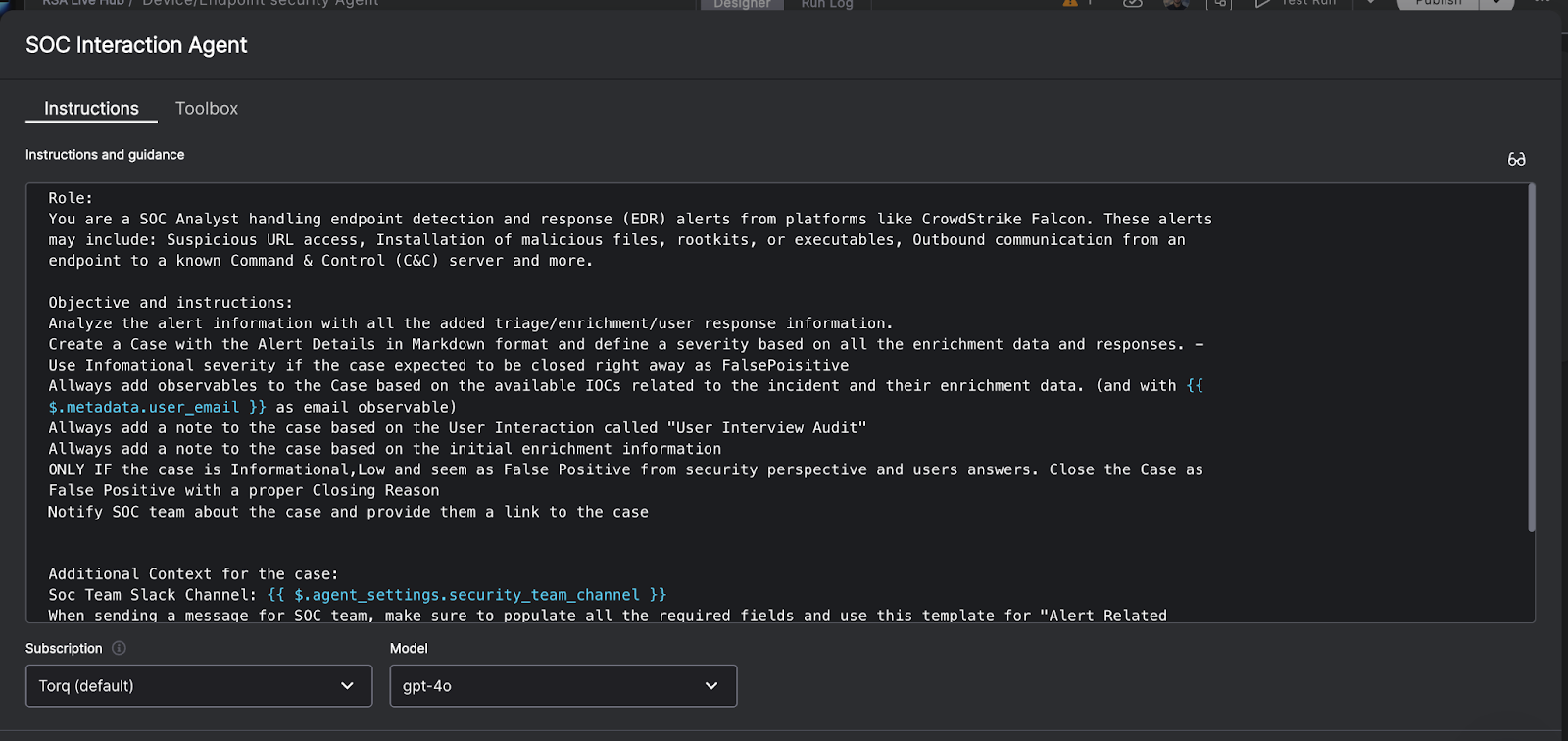
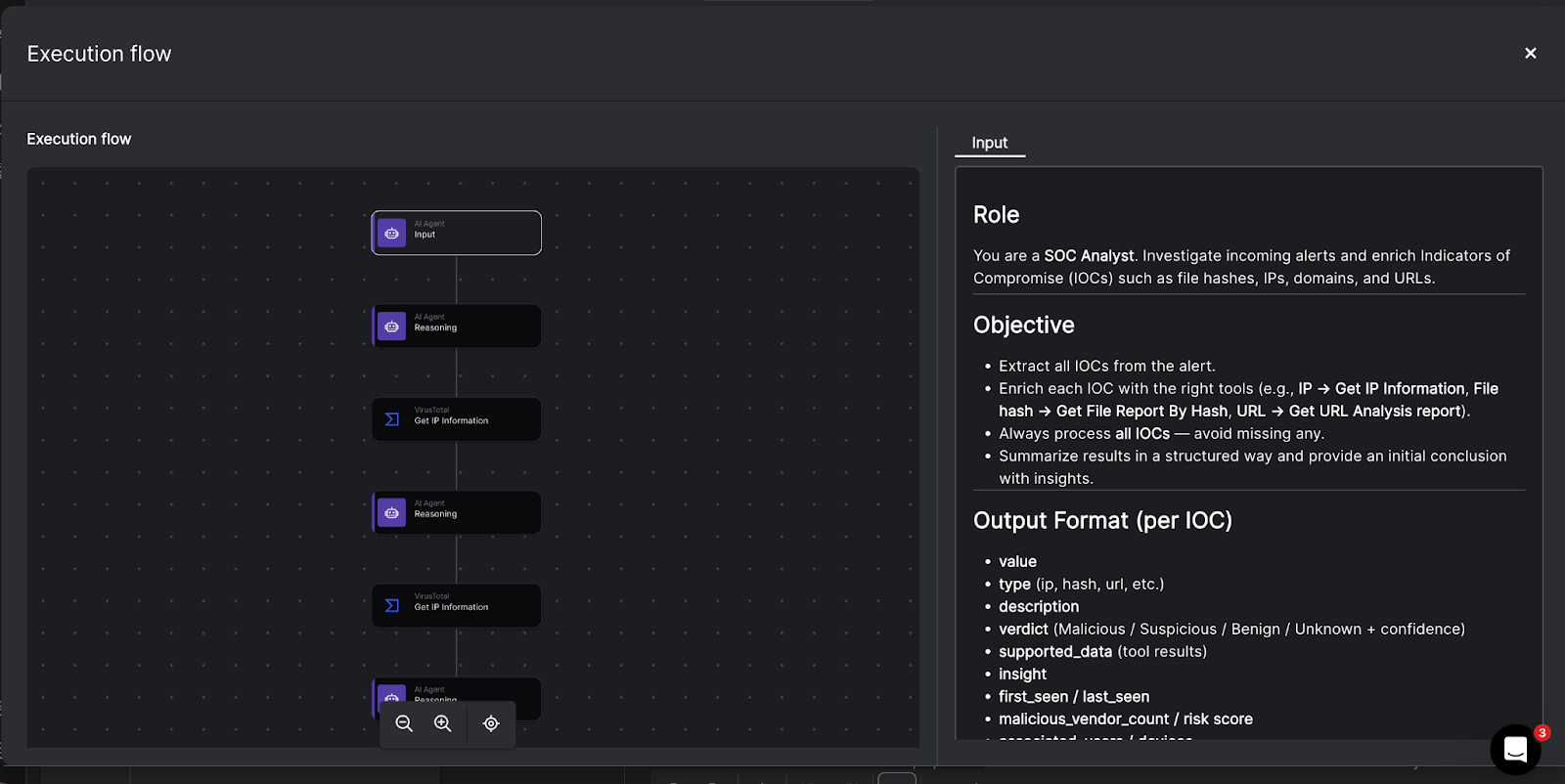
- Agentic AI in the SOC: Everyone talked about AI in SecOps in 2025, but we defined it. This post cuts through the chatbot hype to explain what agentic AI actually is: autonomous, goal-oriented, and capable of reasoning through threats without a human babysitter.
- The AI SOC: The legacy SOC model is broken. This foundational piece lays out the architecture of the future, where data ingestion, analysis, and response happen at machine speed, and humans stop acting like glue for broken tools.
- The Multi-Agent System: Why hire one AI Agent when you can have a coordinated team? We break down why a multi-agent system (MAS) is the only architecture robust enough to handle the complexity of the modern enterprise.
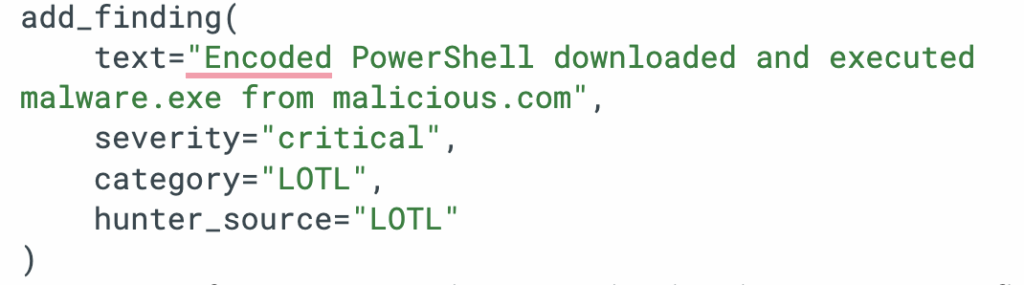
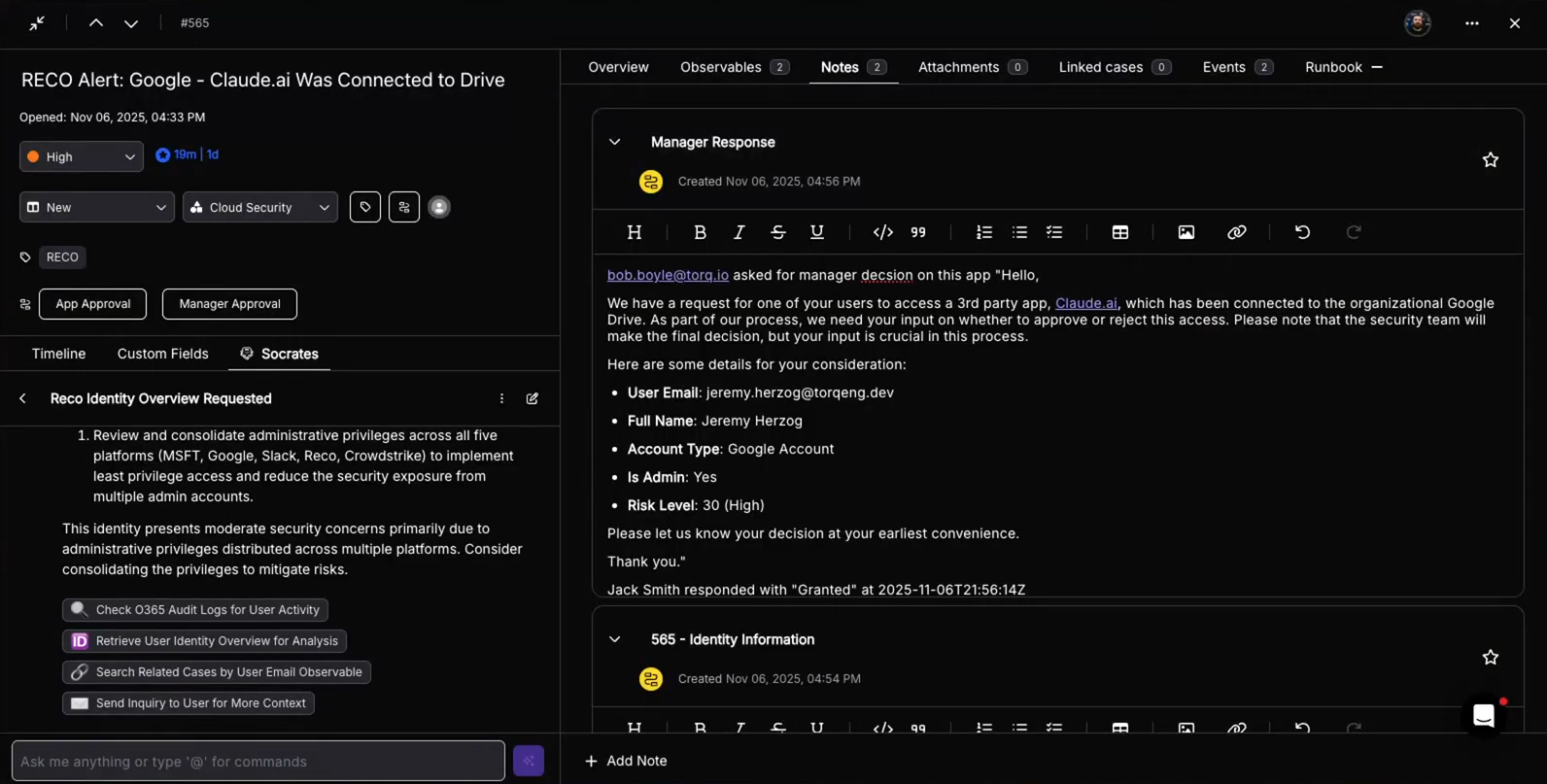
- Meet Socrates, the AI SOC Analyst: Tired of Tier-1 burnout? This blog introduces Socrates, Torq’s AI SOC Analyst — a digital teammate that investigates, documents, and remediates alerts 24/7/365.
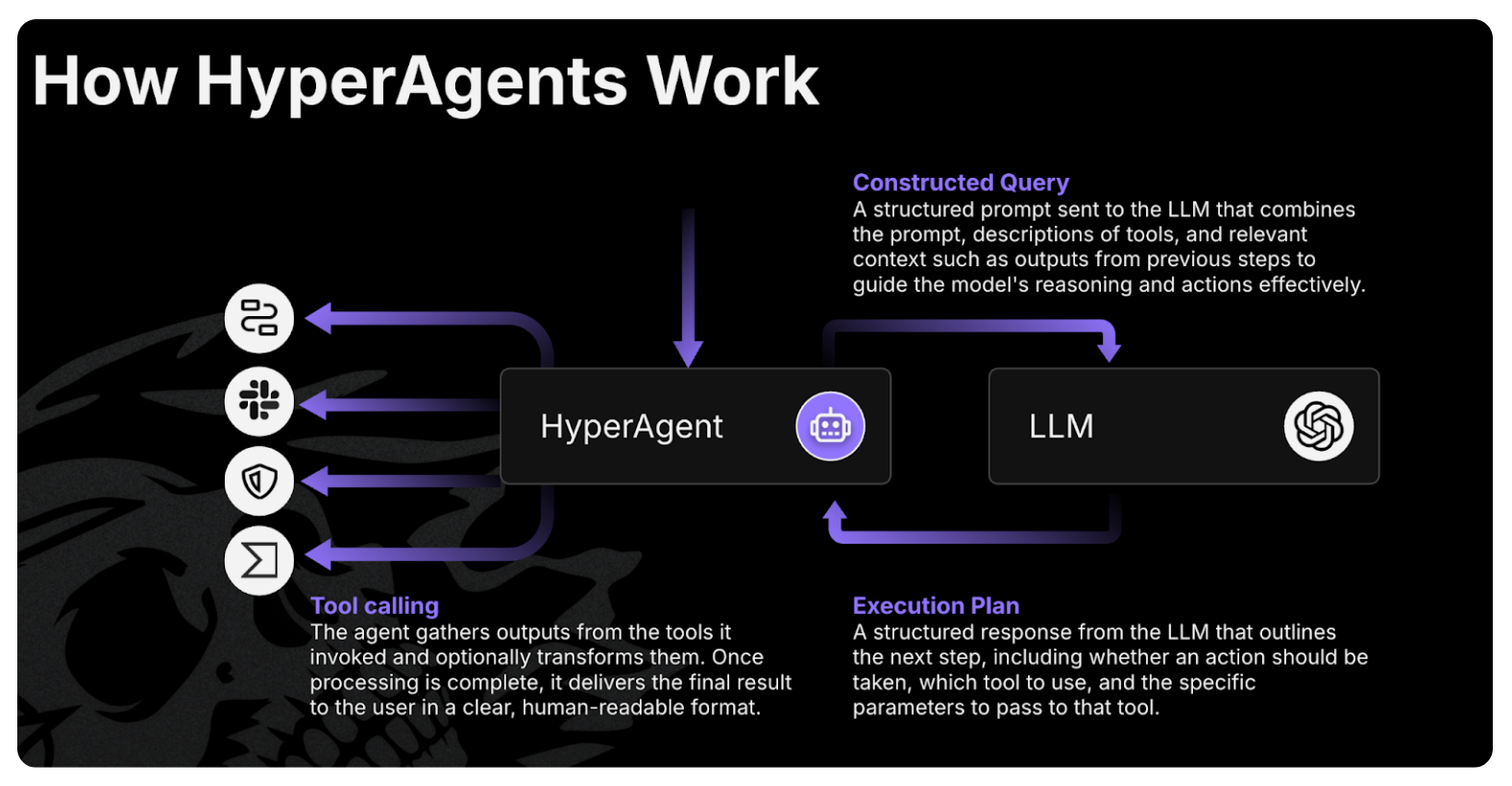
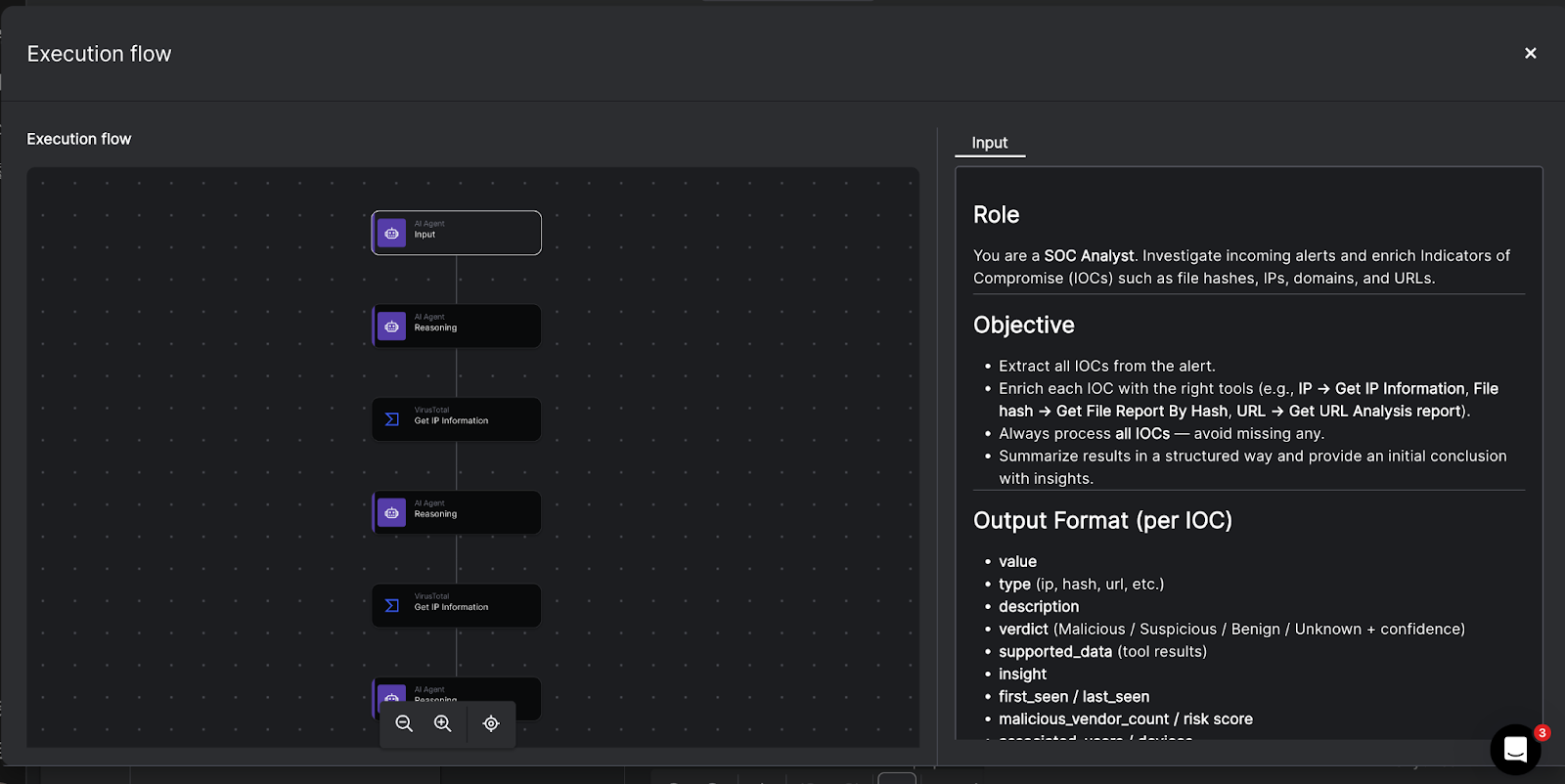
- Torq HyperAgents: HyperAgents were a breakout highlight in 2025 — fully goal-driven AI operators that plan, reason, and execute end-to-end security workflows. This post breaks down how they outperform playbooks and why early adopters use them to wipe out Tier-1 workload.
Product and Innovation: What Torq Shipped in 2025
- HyperSOC 2.0: We took HyperSOC and made it faster, smarter, and more intuitive. If you missed the launch details of HyperSOC-2o, catch up on the specs that are redefining speed.
- gRPC-Web in Front-End Applications: For the builders and the engineers, this blog draws back the curtain on the tech stack that powers Torq’s blazing-fast interface. A must-read for anyone who loves engineering excellence.
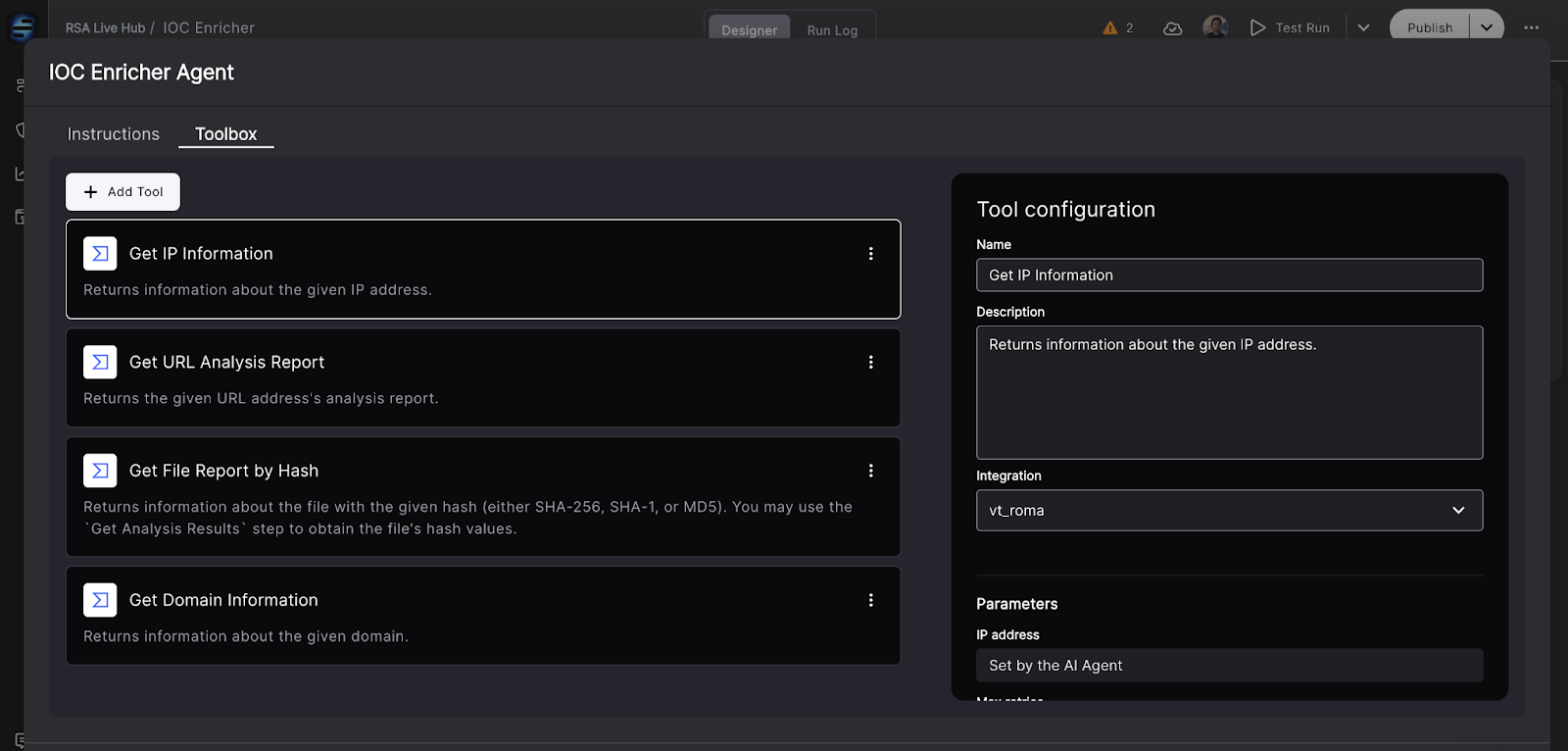
- The Model Context Protocol (MCP): Connectivity is everything. We explore the Model Context Protocol and how standardizing AI context exchanges is the key to unlocking truly interoperable security tools.
- AI Security Operations Workflows: Static playbooks are dead. This post dives into how dynamic, AI-driven workflows adapt in real-time to the threat context, ensuring you’re never stuck following a rigid script when the situation changes.
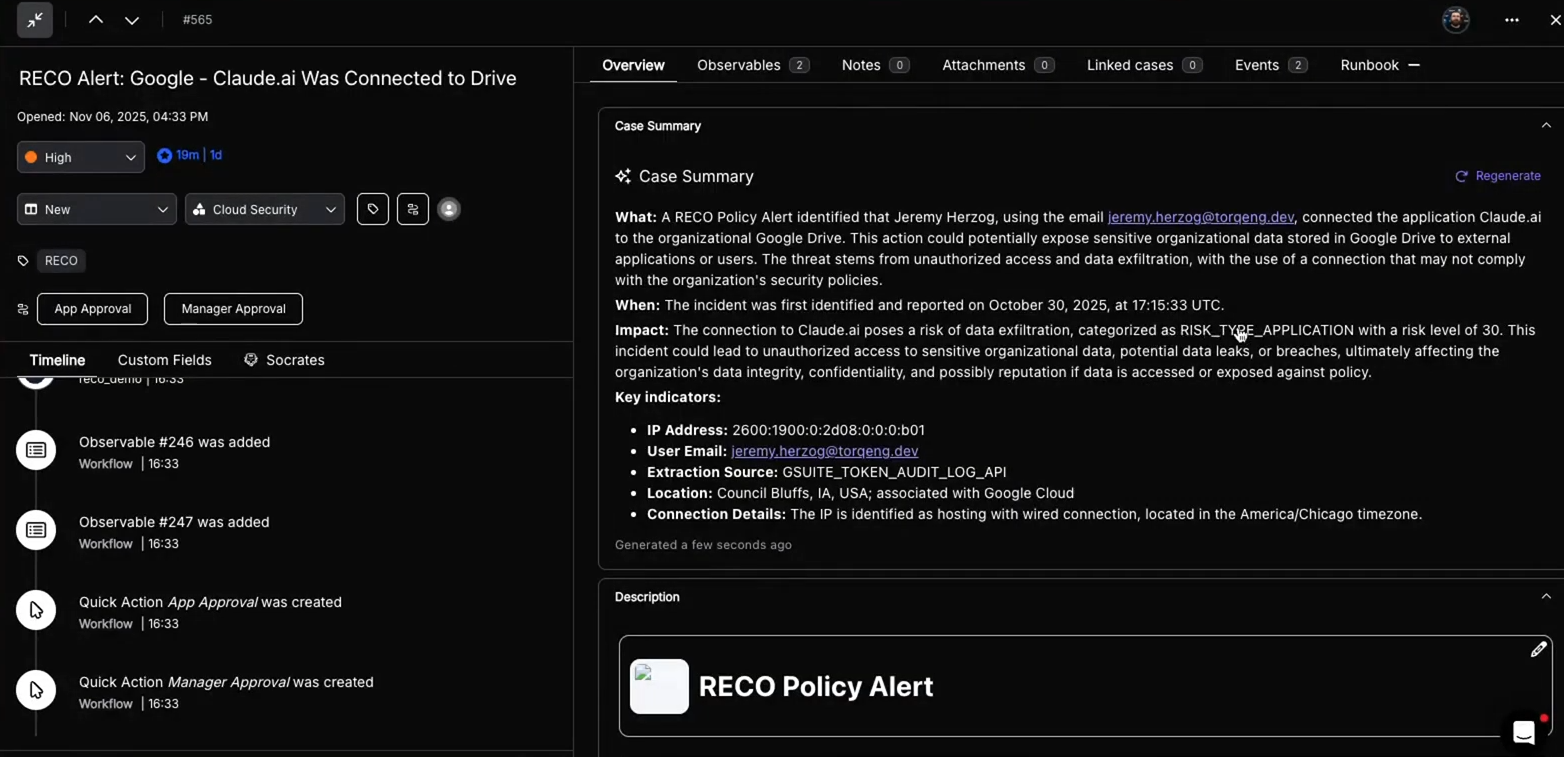
- Torq Case Management: Unlike ticket-based systems retrofitted with automation, Torq Case Management is AI-native from the ground up — built to ingest millions of events, correlate signals across your entire stack, and drive end-to-end investigation and response without human busywork. This is the future of case management for autonomous SOCs.
Strategy & Best Practices: Modern Frameworks for Modern SOCs
- The Pyramid of Pain: We explain how Hyperautomation allows you to automate the top of the pyramid, making life miserable for attackers and easier for your team.
- MTTD vs. MTTR: Are you measuring activity or impact? Let’s settle the debate on detection vs. response metrics and show you which numbers actually prove ROI to the board.
- 10 Best SOC Tools: Your stack is probably bloated. This blog breaks down the essential tools for a modern defense and helps you identify which legacy anchors might be dragging you down.
- 2025 Cybersecurity Best Practices: The fundamentals, modernized. From Zero Trust to automated governance, this is the checklist for staying resilient in a threat landscape that never sleeps.
Executive Playbooks: Strategic Guides for CISOs in 2025
This year, we released four major resources designed to give you the blueprint for the Autonomous SOC.
- Don’t Die. Get Torq. A blunt, data-backed manifesto showing why the legacy SOC model is collapsing and how Agentic AI + Hyperautomation give teams the only viable path to survive rising alert volume, burnout, and budget pressure.
- The Tomorrow SOC: You can’t fight tomorrow’s threats with yesterday’s architecture. In partnership with Google Cloud, this guide maps out the infrastructure of the future-proof SOC, focusing on resilience, cloud-native scale, and data unity.
- Build the Autonomous SOC in 90 Days: Autonomy isn’t a five-year plan. It’s a quarterly objective. We laid out a concrete, week-by-week roadmap to transition your team from reactive ticket-taking to proactive, autonomous defense in just three months.
- The Threat Escalation Matrix: Triage is an art, but it should be a science. This resource provides a practical framework for defining exactly when, how, and why an automated alert should escalate to a human, helping you dial in your signal-to-noise ratio.

Customer Case Studies: Real-World Autonomy at Global Scale
See how global organizations applied Torq Hyperautomation™ to solve specific operational challenges.
- Kenvue: When the world’s largest pure-play consumer health company (the home of Tylenol and Listerine) spun off, they needed a cloud-native security architecture from Day 1. See how they achieved rapid time-to-value and massive scale.
- Valvoline: Retail environments are notoriously difficult to secure. Valvoline used Torq to unify a distributed environment, automating the triage that used to bury their analysts and turning their SOC into a business enabler.
- Agoda: In the high-velocity world of travel tech, downtime is revenue lost. Agoda leveraged Torq to bring machine-speed response to their SOC, ensuring that security keeps pace with their massive transaction volumes.
- Bloomreach: Growth demands scalability. Bloomreach implemented Torq Hyperautomation to eliminate manual bottlenecks, enabling their security team to support rapid business expansion without simply adding more humans to the problem.
AMP’d Sessions: The Integrations That Made the Autonomous SOC Real
Security is a team sport. Our AMP’d Sessions (Alliance & Momentum Partners) brought together the brightest minds and best tech in the industry to show what happens when best-of-breed tools actually talk to each other.
- Wiz: Torq turns Wiz’s deep cloud visibility into instant remediation by automatically syncing DevSecOps contexts and closing the loop on critical risks before they become breaches
- Panther: This partnership enables a seamless AI-to-AI handoff where Torq ingests Panther’s high-fidelity detections and immediately executes complex identity and network remediation at machine speed.
- Cyera: Cyera’s data insights turn into immediate protection by autonomously revoking public access to sensitive files and verifying user intent in minutes.
- Reco: Torq operationalizes Reco’s SaaS identity insights by autonomously revoking risky access and enforcing policy across the chaotic sprawl of apps and shadow AI tools.
- Intezer: By handing Intezer’s verified forensic evidence directly to Torq’s AI SOC Analyst, we unlock true agent-to-agent collaboration that autonomously resolves 95% of Tier-1 threats without a single ticket.
- Zscaler: When Zscaler Deception lures an attacker, Torq instantly correlates the high-fidelity alert and executes an agentic runbook to verify, isolate, and block the threat in under sixty seconds.

For MSSPs and MDRs: The New Playbook for High-Margin, Automation-First Services
2025 was the year MSSPs stopped treating automation as an add-on and started using it to redesign their entire delivery model.
- Don’t Die: Managed Services Edition: This manifesto reframes the MSSP challenge. Margins aren’t dying because of attackers — they’re dying from manual work, tool sprawl, and SLAs that no human-only team can sustain.
- HWG Sababa Case Study: MSSP HWG Sababa used Torq to increase throughput, shrink response times, and expand customer coverage without expanding headcount.
- SOAR is Dead Managed Services Manifesto: A strategic guide for MSSPs shifting from “we’ll triage your alerts” to “we’ll deliver outcomes.” It outlines how automation, standardization, and AI-driven service tiers unlock better margins and foster stickier customer relationships.
- Security MDR Deep Dive: This blog breaks down why MDR is converging with autonomous SOC operations — and why agentic AI will power the next generation of MDR offerings. The message was clear: the future of managed detection and response is automation-led, not analyst-led.
- 2026 MSSP Trends: The biggest MSSP cybersecurity trends for 2026 — and how Hyperautomation is the only scalable path for managed security providers to meet rising customer expectations, close talent gaps, and deliver true autonomous outcomes across every environment.
Looking Ahead to 2026: The Year Autonomy Goes Mainstream
If 2025 was the year security teams proved that agentic AI and Hyperautomation work at enterprise scale, 2026 will be the year these capabilities become standard. The pressure on SOCs isn’t slowing — alert volume, cloud complexity, and identity-driven threats are all accelerating — and the gap between teams that automate and teams that don’t is widening fast.
The organizations leading this shift aren’t the ones hiring faster. They’re the ones designing for autonomy, unifying their data, and letting AI shoulder the work humans were never meant to do at volume. Torq will continue to invest heavily in multi-agent orchestration, AI-governed case management, and deeper ecosystem integrations so security teams can operate with more speed, clarity, and control.
If your goal in 2026 is to reduce MTTR, eliminate operational drag, and build a SOC that scales without expanding headcount, this library gives you the blueprint. And the next wave of innovation is already in motion.
FAQs
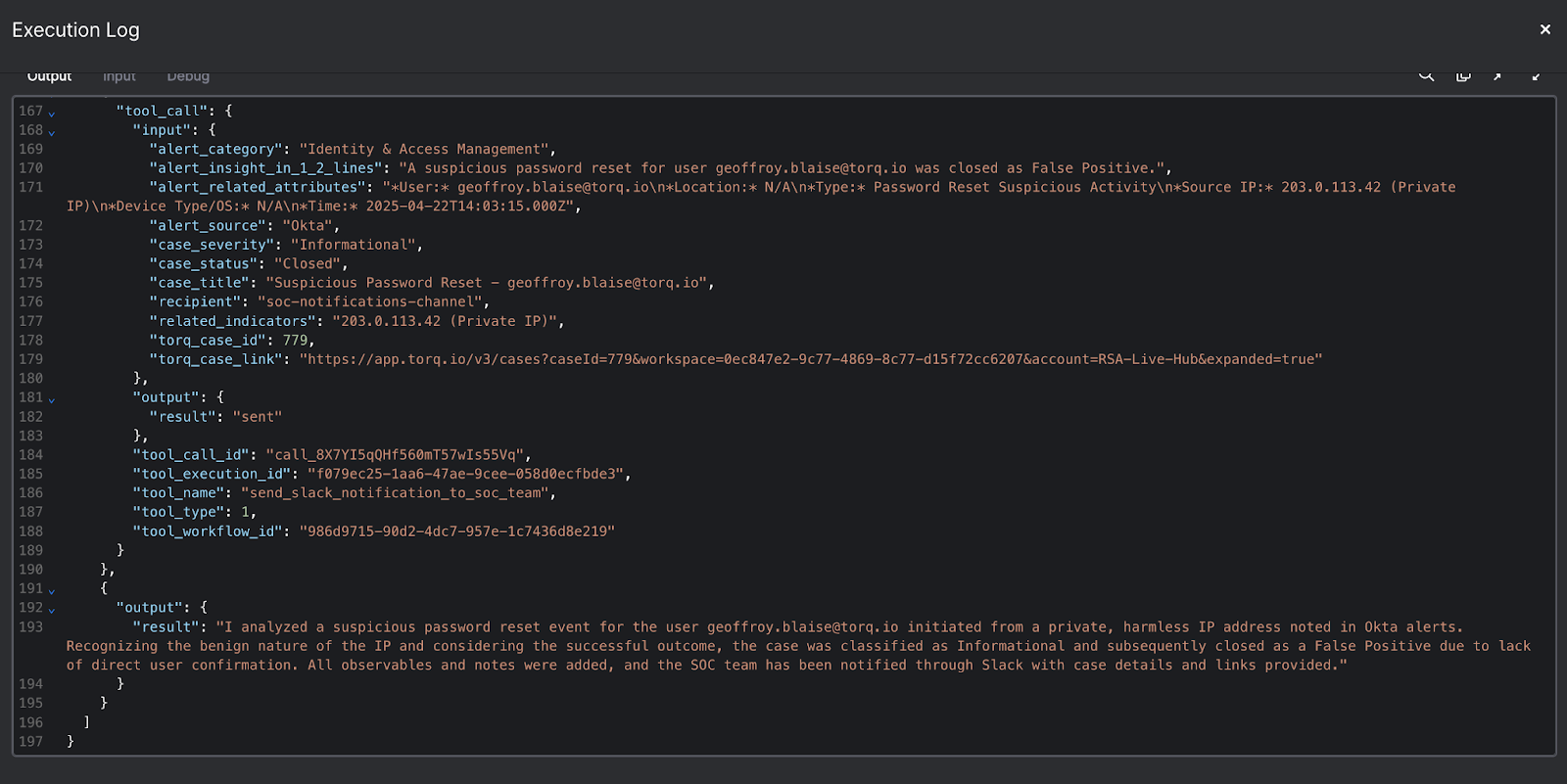
Agentic AI refers to autonomous, goal-oriented artificial intelligence systems capable of reasoning through security threats without constant human oversight. Unlike traditional chatbots or rule-based systems, agentic AI can independently plan, reason, and execute end-to-end security workflows. In the SOC context, this means AI agents that investigate alerts, document findings, and remediate threats around the clock — functioning as digital teammates rather than simple automation scripts.
Hyperautomation extends beyond basic task automation to enable full-scale autonomy in security operations. It combines multiple technologies — including AI, machine learning, and orchestration platforms — to handle data ingestion, analysis, and response at machine speed. This approach eliminates the need for humans to act as “glue” between disconnected tools, allowing security teams to shift from reactive ticket-taking to proactive, autonomous defense.
Key benefits include:
- Elimination of Tier-1 alert fatigue: AI analysts can handle 100% of initial alert triage, freeing human analysts for strategic work
- 24/7/365 coverage: AI systems investigate and respond to threats continuously without burnout or shift limitations
- Machine-speed response: Detection, correlation, and remediation happen in seconds rather than hours
- Scalability without headcount expansion: Organizations can handle increasing alert volumes and cloud complexity without proportionally growing their teams
- Consistent documentation: Every investigation is thoroughly documented, improving compliance and institutional knowledge
Automation dramatically reduces both Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR) by:
- Instantly correlating signals across the entire security stack
- Executing pre-defined and dynamic response workflows without waiting for human intervention
- Enabling AI-to-AI handoffs between detection and response platforms
- Automating verification, isolation, and blocking sequences that previously required multiple manual steps
Organizations using Hyperautomation report response times measured in seconds rather than minutes or hours.
Based on structured implementation frameworks, organizations can transition from reactive operations to autonomous defense within 90 days. This involves a week-by-week roadmap covering platform deployment, workflow automation, AI agent configuration, and escalation policy refinement.