Contents
Get a Personalized Demo
See how Torq harnesses AI in your SOC to detect, prioritize, and respond to threats faster.
Cyberattacks are becoming more frequent and sophisticated as threat actors continually sharpen their tactics and upgrade their tools. Defending against these evolving threats is increasingly complex, especially in a landscape where cybersecurity ROI is measured in loss prevention rather than revenue generation.
Cyber threat hunting offers a proactive way to secure your environment by actively seeking out threats that evade traditional defenses. However, manual threat hunting is time-consuming, resource-intensive, and complicated by a growing shortage of skilled professionals.
In this blog, we’ll unpack everything you need to know about cyber threat hunting and show how Hyperautomation can help your team stay ahead of attackers by streamlining detection, investigation, and response without requiring massive overhead.
What is Threat Hunting in Cybersecurity?
Cyber Threat Hunting
Cyber threat hunting is a proactive cybersecurity process where trained individuals, called threat hunters, actively search for malicious cyber activities and potential threats that might have evaded traditional security measures. It involves going beyond automated security tools and alerts to investigate and identify hidden threats within a network or system.
The value of cyber threat hunting lies in these key properties:
- Proactive approach: Unlike traditional security measures that react to alerts, threat hunting is a proactive process. Threat hunters actively seek out potential threats rather than waiting for them to be detected or, worse, erupt into a critical incident.
- Augmenting automated systems: Threat hunting complements automated security tools by identifying threats that may have slipped past those systems.
- Human expertise: It relies on the knowledge and skills of threat hunters who use their expertise, tools, and methodologies to identify malicious activities.
- Targeted searches: Threat hunters develop hypotheses about potential threats based on threat intelligence, known attack techniques, and other factors, then they search for evidence to validate those hypotheses.
- Focus on advanced threats: Threat hunting is beneficial for identifying advanced persistent threats (APTs) and other sophisticated attacks that can evade traditional security measures.
Why is Cyber Threat Hunting Important?
Most SOC tools operate reactively — they wait for indicators of compromise (IOCs) or known attack signatures to trigger alerts. However, today’s adversaries are stealthy, often residing in networks undetected for weeks or months. Cyber threat hunting flips the script.
Threat hunting proactively searches for unknown, suspicious behavior and zero-day threats that traditional detection tools miss. The benefits include:
- Early threat detection and response: Threat hunters spot anomalies before damage occurs, enabling rapid, contained responses to reduce breach impact. Early detection and response can significantly reduce the potential damage and costs associated with cyberattacks.
- Identification of persistent and complex threats: Advanced persistent threats (APTs) often evade SIEMs or endpoint detection and response (EDR). Threat hunting reveals long-dwelling attackers using subtle tactics.
- Improved incident response efficiency: Hunting improves context and decision-making for incident response (IR) teams, reducing mean time to investigate (MTTI) and resolve (MTTR). By identifying and mitigating threats proactively, threat hunting strengthens an organization’s overall security posture.
- Enhanced threat intelligence: The insights gained from threat hunting can also improve an organization’s threat intelligence and help them better understand their adversaries.
How Cyber Threat Hunting Works: 6 Methods
Cyber threat hunting isn’t a single technique — it’s a flexible, proactive approach that combines human expertise with data, context, and tooling. Depending on your team’s goals, tools, and maturity level, different methodologies can be used to uncover hidden threats and eliminate adversaries before they cause damage. Here are six of the most effective threat hunting methods in use today.
1. Hypothesis-Driven Hunting
This method begins with a well-formed theory about how an adversary might be operating within your environment. Hunters often base these hypotheses on current threat intelligence, past incidents, or a known threat actor’s tactics.
For example, a threat hunting team may ask, “Is an attacker using PowerShell for lateral movement across endpoints?” They then query logs, examine user activity, and look for anomalies that might validate or disprove that theory. This structured, scientific approach allows analysts to pursue purposeful leads and systematically uncover sophisticated threats.
2. Indicator of Attack (IoA)-Based Hunting
Rather than reacting to alerts, IoA-based threat hunting proactively searches for signs of attacker behavior that signal malicious intent — even if no breach has occurred. Analysts look for behavioral patterns and tactics often used by adversaries, such as a sudden surge in failed login attempts, suspicious registry modifications, or abnormal user behavior during off-hours.
By focusing on indicators of attack (IoAs) instead of indicators of compromise (IoCs), teams can identify active intrusion attempts earlier in the kill chain, often before data exfiltration or lateral movement occurs.
3. Advanced Analytics and Machine Learning
Threat hunting at scale benefits significantly from security automation, particularly through advanced analytics and machine learning (ML). These AI models are trained on historical attack data and behavioral baselines, helping analysts identify statistical anomalies and outliers across massive datasets.
For example, suppose a user suddenly begins downloading gigabytes of data from an unfamiliar endpoint. ML-driven tools can flag the deviation from normal behavior in that case, even if no specific IoA has been defined. This method increases speed and coverage, especially in cloud or hybrid environments.
4. Structured Hunting
Structured threat hunting leverages formal models and frameworks like MITRE ATT&CK to organize and guide investigations. By using well-defined tactics, techniques, and procedures (TTPs), analysts can systematically scan for known threat behaviors across endpoints, identities, and networks.
This method is beneficial for standardizing team processes, ensuring knowledge sharing, and aligning with compliance or threat modeling requirements. It also enables better documentation and repeatability of hunts, making it a valuable tool for maturing a cybersecurity program.
5. Unstructured Hunting
Unstructured hunting relies more on analyst intuition and real-world experience than on formal rules or frameworks. In this method, seasoned hunters follow their instincts, identifying suspicious patterns, log entries, or correlations that don’t match any known indicators — but still “feel off.”
This open-ended approach can surface novel attacks, zero-day behaviors, or insider threats that evade automated detection. While more time-consuming, unstructured hunting is crucial in developing hypotheses for future structured hunts and refining detection rules.
6. Situational or Entity-Driven Hunting
This method prioritizes hunting based on specific contexts — such as critical assets, high-risk users, or sensitive business functions. For example, threat hunters may target systems housing personally identifiable information (PII) or monitor executive accounts likely to be targeted in phishing or business email compromise (BEC) attacks.
Situational or entity-driven hunting ensures security teams protect what matters most by focusing on high-value targets and contextual threat intelligence. It can also quickly act on suspicious activity that might otherwise get lost in the noise.
Cyber Threat Hunting Process
Effective threat hunting follows a straightforward process. Here’s how top-performing teams approach it.
- Trigger: A hunt often starts with a clue — a suspicious login, a new TTP from a threat intel feed, or a hunch. Triggers inform what to investigate.
- Investigation: Hunters use SIEM, EDR, network traffic, and log data to dig deeper. Enrichment, correlation, and historical context help determine risk.
- Resolution: If a threat is confirmed, it’s escalated for response, and hunting insights are used to improve detection rules and workflows in the future.
Cyber Threat Hunting Tools & Technologies
- SIEM (Security Information and Event Management): Aggregates logs across systems to provide a centralized view and real-time alerts.
- EDR (Endpoint Detection and Response): Monitors and records activity on endpoints to uncover suspicious behavior.
- MDR (Managed Detection and Response): Outsources threat detection and response to external experts, ideal for resource-limited teams.
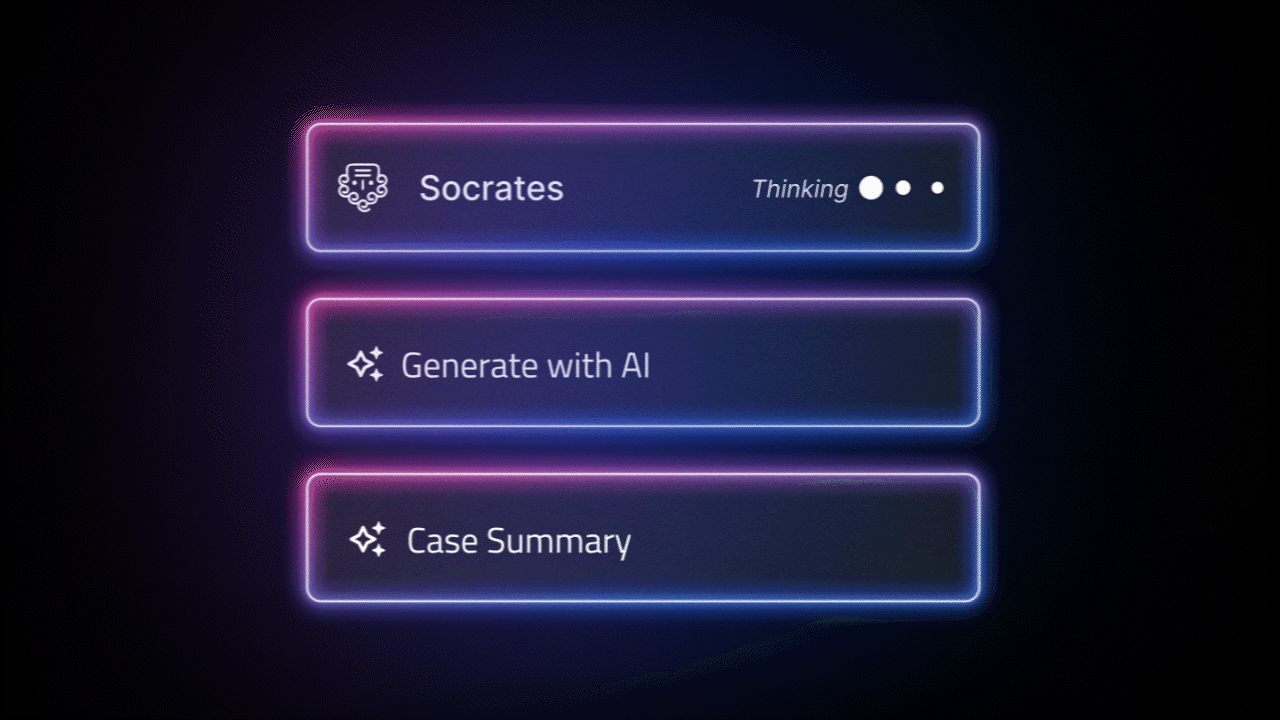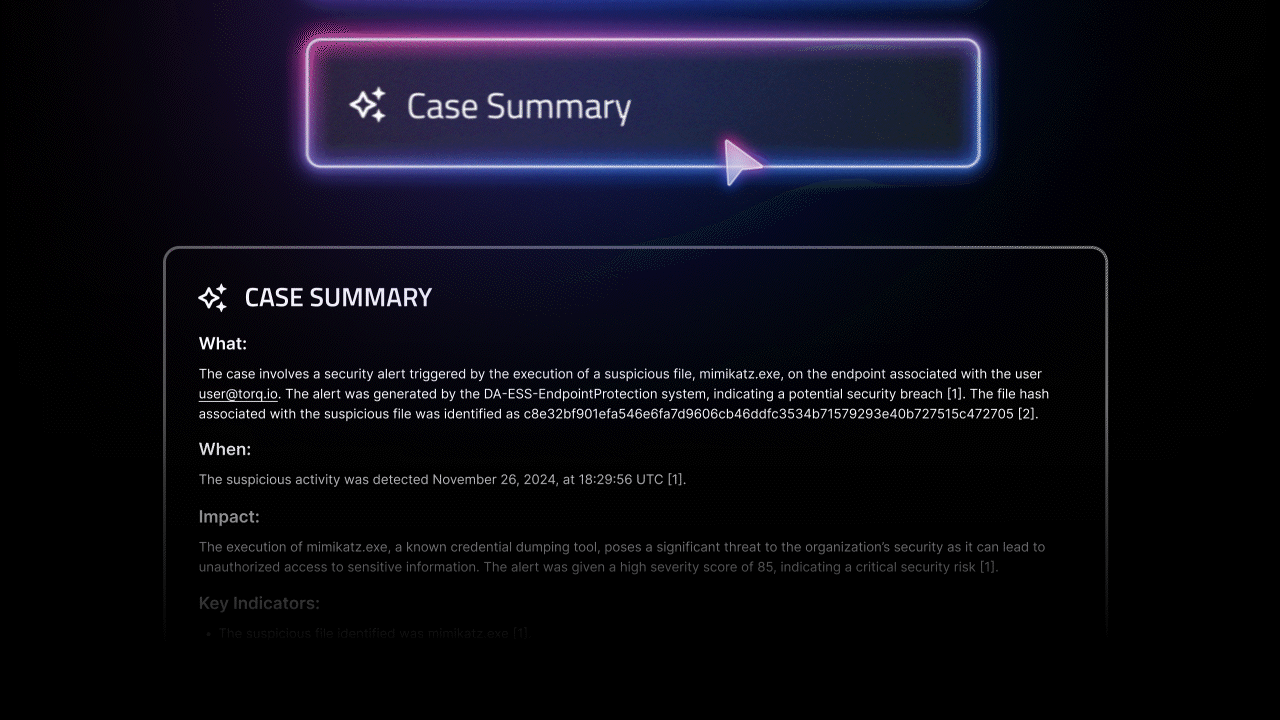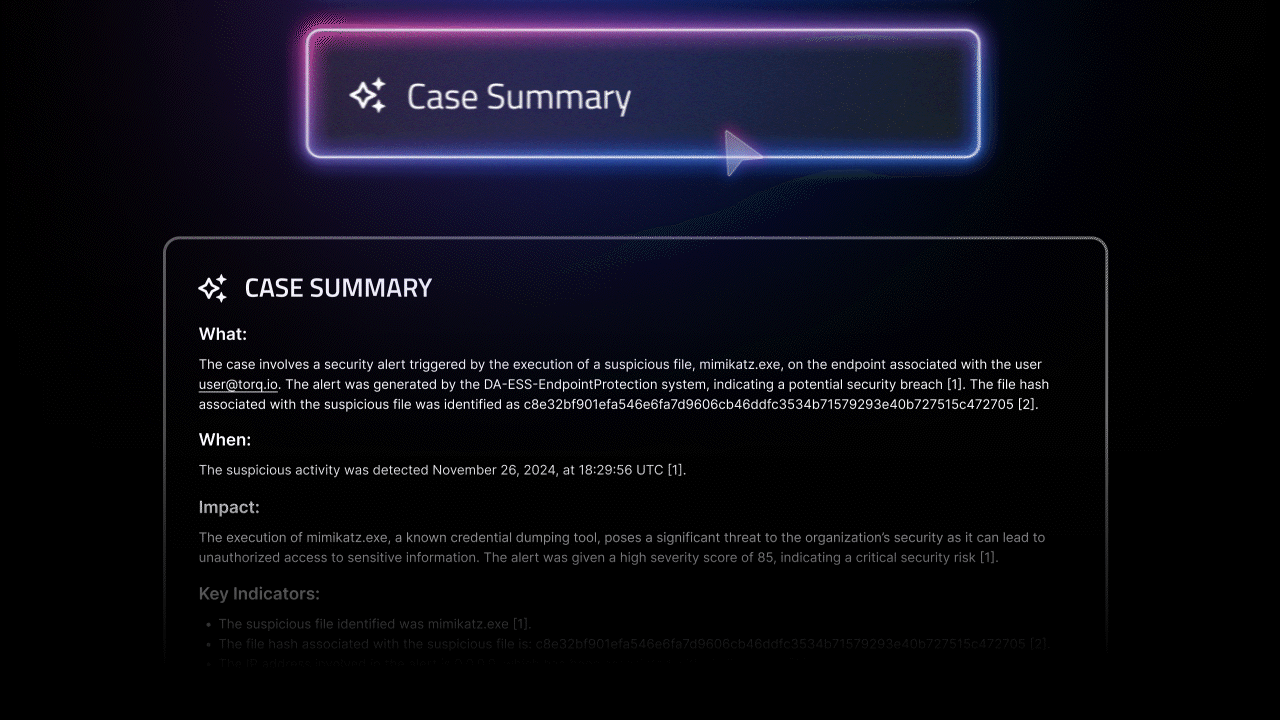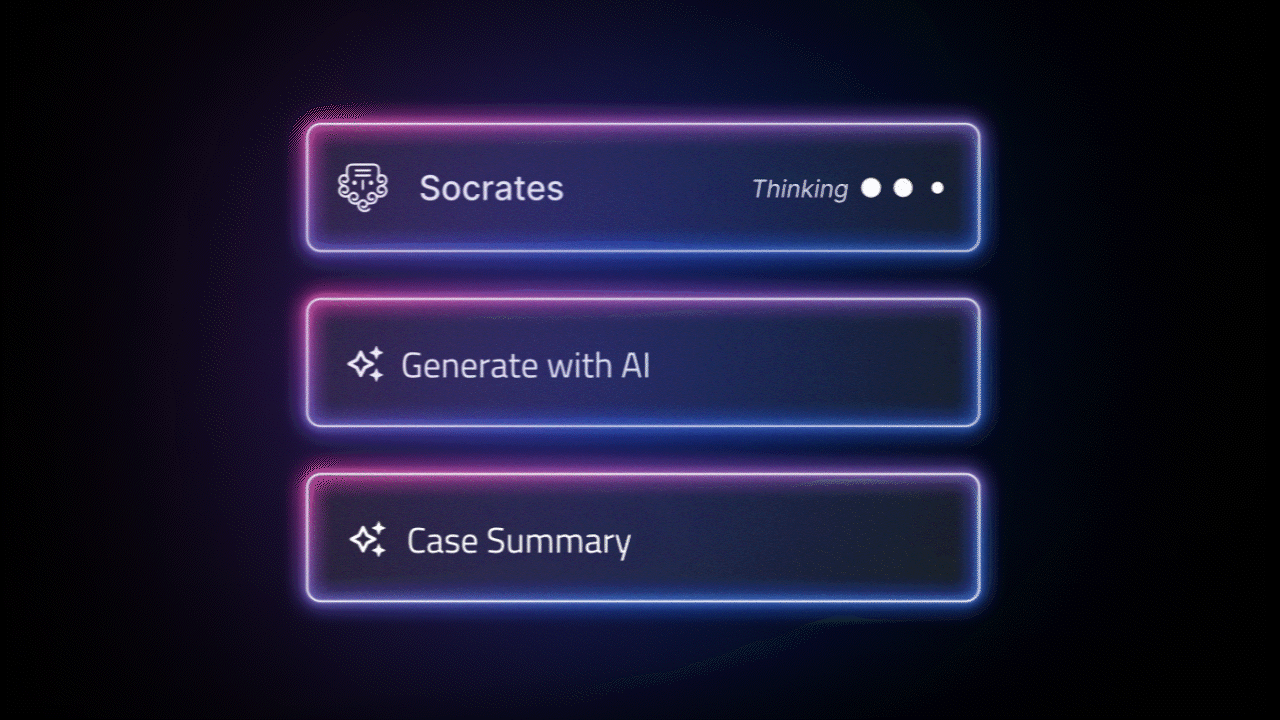
- Hyperautomation: Goes beyond basic automation. Combines AI, orchestration, and no-code/low-code tools to scale SOC threat detection and response with minimal manual effort. Hyperautomation platforms like Torq can enrich alerts, orchestrate threat investigations, and even automate entire cyber threat hunting workflows.
4 Cyber Threat Hunting Challenges & How to Navigate Them with Torq
Cyber threat hunting is an essential pillar of modern cybersecurity strategy, but it’s not without its obstacles. Today’s SOC teams face increasing complexity, resource constraints, and alert overload, which can hinder their ability to detect and respond to threats proactively.
Below are four of the most common challenges security teams encounter in threat hunting, along with how Torq’s Hyperautomation platform directly addresses them with AI-driven precision and scale.
1. Integrating Disparate Data Sources
The Challenge: Threat hunters rely on data from SIEM, EDR, firewalls, and cloud environments, which are often siloed.
How Torq Helps: Torq Hyperautomation breaks down these silos by integrating your entire security stack into a unified, low-code automation engine. With hundreds of pre-built integrations, Torq enables real-time data normalization, enrichment, and orchestration across all sources. Threat intel from platforms like VirusTotal or Recorded Future can be automatically enriched into alert streams, providing analysts with actionable context — fast. This consolidated view eliminates blind spots and empowers threat hunters to act confidently and quickly.
2. Alert Fatigue
The Challenge: Analysts drown in noisy, low-value alerts, making it difficult to spot real threats.
How Torq Helps: Torq uses agentic AI to combat alert fatigue. Torq ensures that only high-confidence, context-rich alerts reach analysts by filtering out noise, deduplicating alerts, and applying real-time prioritization logic. Low-risk or redundant alerts are automatically suppressed, and high-severity incidents are escalated to the right person or team through customized workflows. This triage process reduces alert volume by up to 95%, allowing teams to focus on what truly matters — critical threats that require human judgment.
3. False Positives
The Challenge: Traditional tools generate too many “maybe” threats — wasting time and delaying response. In fact, more than half of security teams say that false positives are a huge problem.
How Torq Helps: Torq uses intelligent case automation and prioritization to differentiate between real threats and false alarms intelligently. By analyzing historical resolution data, Torq can fine-tune playbooks to automatically suppress known false positives while continuously learning and adapting to your unique environment. This self-optimizing capability reduces alert fatigue and improves detection, cutting through the noise to surface high-priority incidents faster.
4. Limited Resources
The Challenge: Skilled threat hunters are in short supply — and expensive.
How Torq Helps: Torq HyperSOC empowers teams of all skill levels to participate in advanced threat hunting. Its intuitive low-code interface allows junior analysts to build and execute workflows without needing deep coding experience. Meanwhile, Torq’s AI agents led by Socrates, automatically handle routine triage, enrichment, and correlation, freeing up senior analysts to focus on deep-dive threat analysis and strategic improvements. The result is an autonomous SOC that can scale without scaling headcount.
The Bottom Line
Cyber threat hunting is too important to be slowed down by fragmented tools, noisy alerts, or stretched resources. Torq Hyperautomation modernizes the threat hunting process by combining unified data integration, real-time alert intelligence, and agentic AI, enabling any SOC team to hunt smarter, faster, and more efficiently.
Ready to eliminate your threat hunting roadblocks? See Torq Hyperautomation in action and learn how to evolve from reactive to proactive security today.