Contents
Get a Personalized Demo
See how Torq harnesses AI in your SOC to detect, prioritize, and respond to threats faster.
Modern enterprises face an increasingly complex and dynamic digital environment, making effective attack surface management (ASM) more critical than ever. The sprawling nature of digital assets, rapid cloud adoption, and evolving threat landscape mean new vulnerabilities and exposures continually emerge. Manual processes and legacy tools can’t keep pace, leaving security teams struggling to track and address threats proactively.
Torq Hyperautomation™ transforms attack surface management by continuously detecting, contextualizing, and remediating threats, ensuring your organization remains ahead of adversaries.
What is Attack Surface Management (ASM)?
An attack surface refers to all the potential entry points (physical, digital, and human) an attacker can exploit to gain access to an organization’s system or data. The larger the attack surface, the higher the exposure to threats.
Attack Surface Management (ASM) is a proactive cybersecurity strategy designed to continuously discover, monitor, assess, and reduce potential exposure across an organization’s entire digital footprint. It focuses on identifying all entry points an attacker could exploit — known and unknown — and mitigating risks before they can be leveraged.
An effective ASM program includes:
- Continuous discovery of exposed assets: ASM tools scan all environments for internet-facing and internal assets — cloud services, domains, APIs, SaaS platforms, shadow IT, and forgotten infrastructure — and make persistent discoveries to account for dynamic infrastructure changes, workloads, and rapid application development cycles.
- Monitoring for vulnerabilities and misconfigurations: Vulnerability management is fundamental to attack surface management. Once assets are discovered, ASM monitors them for known vulnerabilities, insecure configurations, unpatched systems, open ports, and any anomalies that could be exploited. It acts as an early warning system that catches issues before attackers do.
- Prioritization of risks: Not all exposures carry equal weight. ASM contextualizes alerts with business relevance, threat intelligence, and asset sensitivity to help security teams focus on what matters most. This triage process ensures critical issues are addressed quickly, while noise is minimized.
- Streamlined response: Effective ASM initiates action. By integrating with ticketing systems, IAM tools, cloud consoles, and security automation platforms like Torq, ASM can automatically remediate issues or trigger workflows for immediate response, improving speed and efficiency.
Challenges of Traditional Attack Surface Management
Several challenges complicate traditional ASM approaches:
- Shadow IT and SaaS sprawl: Rapid SaaS adoption and shadow IT create blind spots, leaving assets untracked and unmanaged.
- Ephemeral cloud infrastructure: Cloud environments constantly evolve, creating fleeting assets that legacy ASM tools struggle to monitor effectively.
- Legacy tools miss context: Traditional tools lack the context to prioritize threats effectively, causing delays and inefficiencies.
- Alert overload stalls response: High volumes of security alerts overwhelm analysts, leading to alert fatigue and slower incident responses.
3 Keys to Effective ASM
Attack surfaces are dynamic, growing, and constantly shifting. Manual methods can’t keep up. That’s why modern ASM must be:
- Automated: Detect and respond without relying on human intervention.
- Continuous: Monitor in real time, not just during scheduled audits.
- Integrated: Feed into your broader security operations stack for full context and control.
This is exactly where security Hyperautomation can help. Torq Hyperautomation transforms ASM from a slow, manual, and reactive task into a real-time, intelligent, and scalable security practice by automating every step, from asset discovery to remediation. With Torq, security teams gain continuous visibility, instant context, and automated action across the entire attack surface — external, internal, and everything in between.
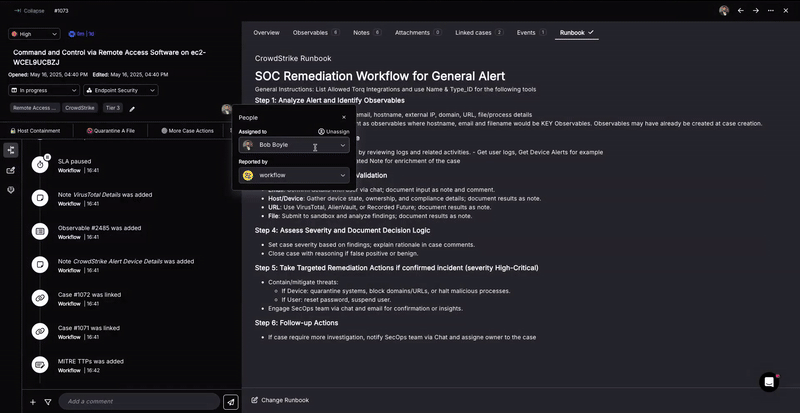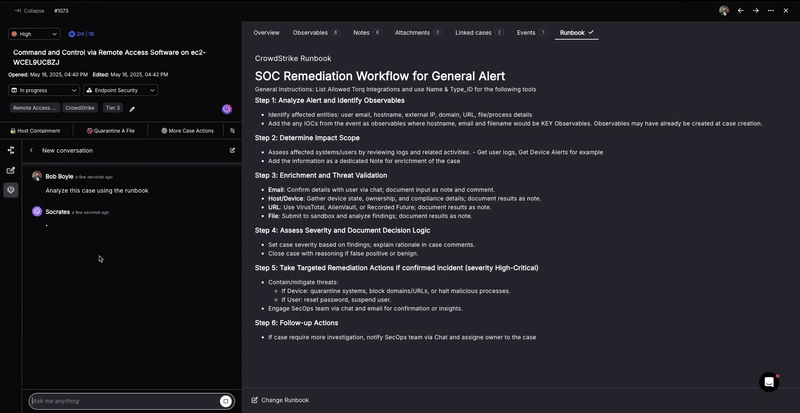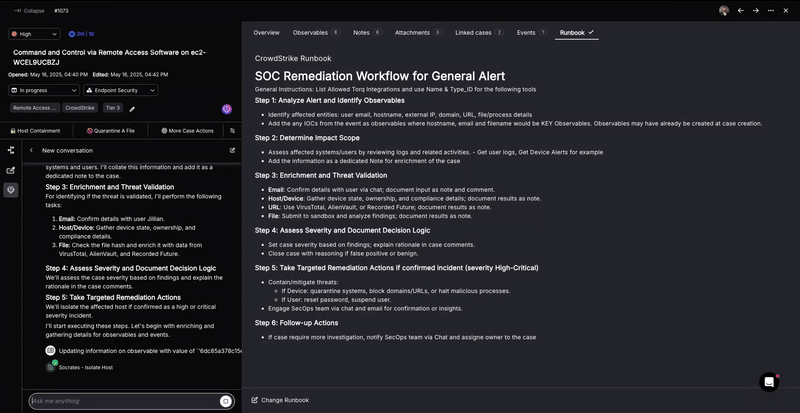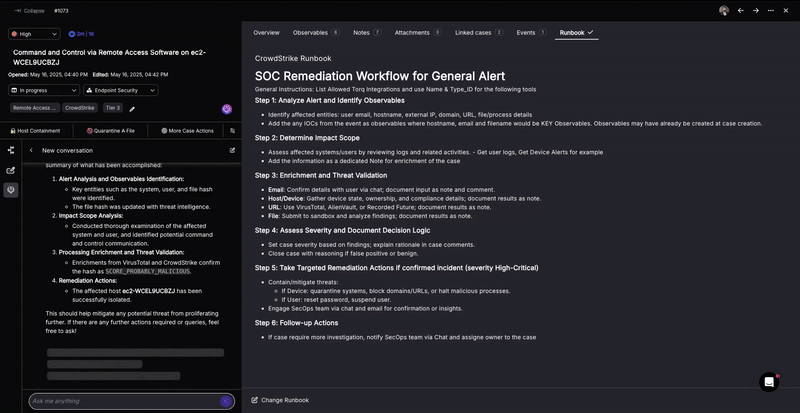
How Automated Attack Surface Management Works
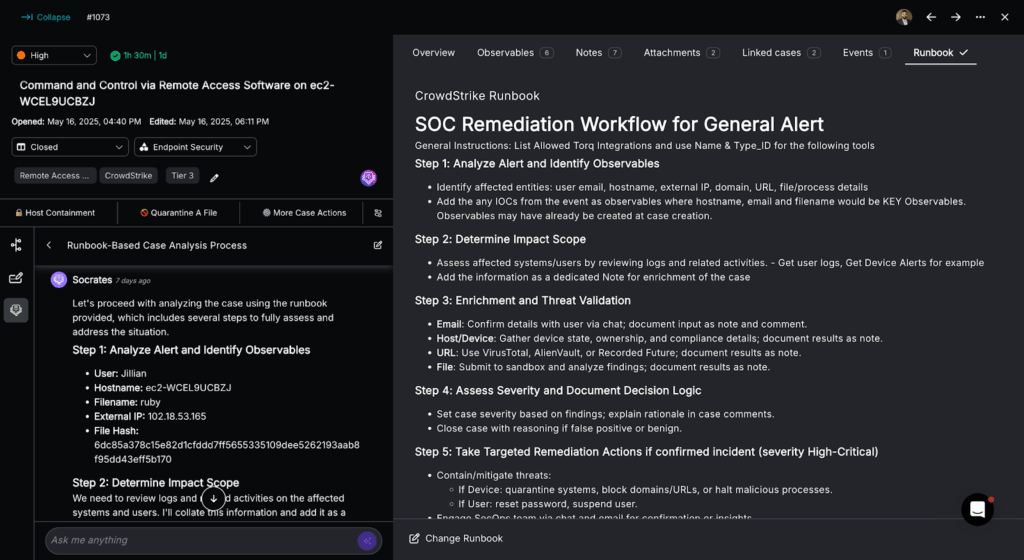
Traditional attack surface management tools often stop at discovery. Torq’s Hyperautomation platform goes several steps further, turning visibility into action and action into measurable impact. It’s not just about knowing your risks; it’s about resolving them automatically, intelligently, and at scale. Here’s how it works.
Asset Discovery
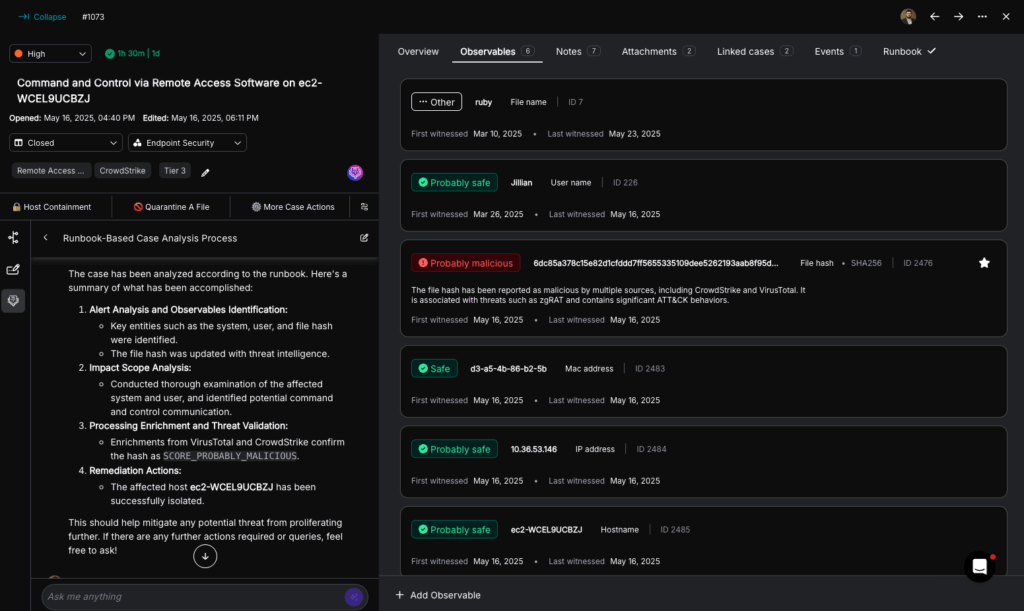
Torq continuously ingests data from across your infrastructure: cloud environments (AWS, Azure, GCP), SaaS platforms (Okta, GitHub), asset inventories, and external ASM tools like SentinelOne, Rapid7, or Qualys. Whether it’s a cloud workload, a shadow IT application, or an unmanaged endpoint, Torq ensures it’s identified and accounted for. The platform dynamically updates its asset map as your environment evolves, providing complete, real-time visibility across internal and external attack surfaces.
Exposure Monitoring
Once assets are discovered, Torq automatically monitors them for known vulnerabilities, insecure configurations, open ports, identity exposures, and other signs of risk. These checks run continuously — not periodically — ensuring that risks are detected as soon as they appear. Torq’s integration with leading vulnerability scanners, CSPM tools, and threat intelligence feeds enables rich, multidimensional analysis of exposures from both inside and outside the perimeter.
Contextual Alerting
Torq enhances every alert with contextual data that matters, like asset ownership, criticality, geographic location, user identity, and recent activity. This enrichment turns raw alerts into actionable intelligence. Instead of treating all alerts equally, Torq prioritizes them based on business risk, reducing alert fatigue and surfacing what truly needs attention. Analysts don’t just receive more information; they get the right information at the right time.
Automated Remediation
Once a threat is confirmed, Torq automatically executes response playbooks tailored to the incident type, asset profile, and organizational policy. These playbooks can:
- Disable vulnerable cloud resources
- Revoke compromised credentials
- Trigger ticketing workflows in Jira or ServiceNow
- Notify the responsible owners or escalate to human analysts
- Re-run validation checks to confirm resolution
Every action is logged, auditable, and fully customizable, enabling high-assurance, closed-loop remediation with minimal manual intervention.
6 Benefits of Hyperautomated Attack Surface Management
Real-Time Visibility Across All Environments
Modern attack surfaces span hybrid clouds, SaaS tools, endpoints, and shadow infrastructure. Torq’s continuously scans your internal and external environment, providing a live, unified view of all known and unknown assets. This real-time visibility eliminates blind spots and ensures security teams can track changes the moment they occur, not days or weeks later. Enhanced visibility supports ongoing risk assessment efforts, allowing teams to prioritize vulnerabilities effectively.
Reduced Risk from Shadow IT and Misconfigurations
Unmanaged SaaS applications, orphaned cloud resources, and misconfigured systems are some of the riskiest parts of any attack surface. Torq’s ASM automations immediately flag these issues, correlate them with business context (e.g., owner, function, sensitivity), and kick off appropriate remediation workflows.
Fewer False Positives Thanks to Contextual Intelligence
False positives waste time, drain resources, and increase the likelihood of real threats slipping through. Torq solves this by enriching alerts with contextual data, such as asset criticality, historical behavior, identity attributes, and network topology. Analysts are presented with actionable intelligence instead of raw signals, reducing noise and sharpening focus on what matters most.
Dramatically Shorter Time to Detect and Respond
Automated ASM eliminates the latency of human-driven detection and triage. As soon as a vulnerability or suspicious exposure is detected, Torq initiates real-time enrichment and response. Whether isolating a misconfigured asset or revoking exposed credentials, remediation begins instantly, cutting Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR) by orders of magnitude.
Always-On Security Posture, Not Periodic Snapshots
Traditional ASM approaches rely on point-in-time scans that become outdated almost immediately. Torq replaces these snapshots with always-on automation, constantly monitoring your infrastructure, scanning for exposure, and triggering responses as needed. This 24/7 posture ensures your security surface evolves at the speed of your business.
Closed Loop from Detection to Resolution
Most ASM tools identify problems but leave resolution to manual processes. Torq completes the loop with intelligent, automated workflows that take action on validated exposures, revoking access, shutting down vulnerable services, notifying asset owners, and logging everything for audit and compliance. This full-cycle automation ensures exposures are resolved, verified, and documented.
Attack Surface Management Implementation: 4 Best Practices
1. Maintain continuous asset inventories: A complete, real-time view of your digital environment is foundational to effective ASM. Conduct continuous asset discovery and inventory updates to track new devices, applications, APIs, cloud resources, and shadow IT. This ensures your security team has an accurate understanding of all external-facing assets and can quickly spot unmanaged or vulnerable components before attackers do.
2. Integrate ASM with security stack: ASM should not operate in isolation. Connect it with your SIEM, vulnerability management, endpoint detection, and identity platforms to enable correlation and enriched context. This integration eliminates blind spots, improves visibility across environments, and empowers security teams to act on threats with unified intelligence.
3. Establish a strong vulnerability management process: Define formal, documented policies for identifying, prioritizing, and remediating vulnerabilities uncovered by ASM. Ensure roles, SLAs, and escalation paths are clearly defined. Integrate vulnerability data with your incident response workflows to speed up resolution and ensure no exposure goes unaddressed.
4. Automate notifications and remediation workflows: Reduce time-to-response and human error by implementing automated alerting and response playbooks. Use workflow automation to route findings to the right teams, trigger patching or access revocation, and track resolution status. Automation accelerates containment, improves coordination, and transforms ASM into a proactive defense layer.
How Torq Hyperautomation Powers End-to-End Attack Surface Management
Torq Hyperautomation integrates seamlessly into your security workflows:
- Connects with external ASM tools (like Palo Alto, Crowdstrike, Microsoft) and internal asset inventories
- Ingests and enriches alerts with detailed contextual data (identity, geography, asset ownership)l
- Triggers automated playbooks for immediate remediation, revocation, alerting, or escalation
- Reduces MTTR by integrating seamlessly with ticketing systems (Jira, ServiceNow), IAM solutions, and cloud providers
- Continuously monitors post-remediation to confirm full resolution
Case Study: How Deepwatch Scaled Global Attack Surface Coverage with Torq Hyperautomation
For managed detection and response (MDR) providers like Deepwatch, delivering high-fidelity protection across a sprawling customer base means managing hundreds (if not thousands) of constantly shifting attack surfaces. But legacy SOAR platforms simply couldn’t scale with the speed, precision, or flexibility needed to keep up.
By adopting Torq Hyperautomation, Deepwatch transformed its security operations and delivered real-time visibility and response capabilities across global customer environments. The result: Over 90% automation of Tier 1 and Tier 2 alerts, faster onboarding for new clients, and dramatic reductions in both mean time to respond (MTTR) and operational overhead. “We’ve come from legacy SOAR to Hyperautomation, and what we’ve been able to build — the environment we now give to our analysts — I don’t think would have ever been achievable with legacy SOAR,” says Micah Donald, Sr. Director of Solutions Engineering, Deepwatch.
With Torq, Deepwatch automated the detection and remediation of exposed assets and vulnerabilities across internal and external attack surfaces without relying on slow manual scripting or disconnected tools. Torq’s low-code/no-code platform enabled Deepwatch analysts to build powerful workflows on the fly, integrate seamlessly with cloud infrastructure, and deliver precision response at scale.
From cloud complexity to shadow IT to ever-evolving customer demands, Deepwatch’s attack surface challenges mirror those of most enterprises today. Their success proves what’s possible when attack surface management is not just monitored but Hyperautomated.
“Torq helps customers get the biggest bang for their security buck, maximizing the value of their existing security investments.”.
– Micah Donald, Sr. Director of Solutions Engineering, Deepwatch
Real Security Use Cases Powered by ASM Automation
Attack surface management isn’t a standalone task — it’s the foundation that powers broader security operations. With Torq Hyperautomation, ASM becomes the connective tissue for dozens of high-impact use cases across your SOC.
Identity and access management (IAM): Torq cross-references exposed assets with identity data from Okta, Azure AD, or HRIS systems. When orphaned accounts or overprivileged identities are discovered on exposed systems, Torq can automatically revoke access, enforce MFA, or trigger re-verification workflows without analyst intervention.
Cloud security posture management (CSPM): Combine CSPM tools like Wiz or Prisma Cloud with Torq’s Hyperautomation to turn misconfiguration alerts into real-time action. Whether it’s shutting down an open S3 bucket, quarantining an untagged instance, or enforcing encryption standards, Torq ensures posture risks are remediated, not just reported.
Threat intelligence operationalization: Torq integrates with threat intel platforms to correlate known IOCs (e.g., IPs, domains, malware hashes) with your asset inventory. If a match is found, Torq can isolate the asset, create a high-priority case, and initiate a full threat hunting workflow.
Email and endpoint security: Attack surface blind spots often include email systems and endpoints. Torq bridges the gap by integrating with email security tools (like Proofpoint and Microsoft Defender) and EDRs (like CrowdStrike and SentinelOne). ASM alerts tied to phishing or endpoint anomalies can trigger dynamic playbooks for containment, notification, and root cause analysis.
Compliance and audit automation: Torq’s action across your ASM program is fully logged and auditable. You can automatically generate compliance artifacts showing asset inventory, exposure history, response timelines, and post-remediation validation, streamlining audits for security frameworks like NIST, ISO, or SOC 2.
Hyperautomate Your Attack Surface Management with Torq
Your organization’s attack surface evolves continuously. ASM tools help you discover new vulnerabilities, but Torq empowers you to automatically respond and remediate, significantly shrinking your risk. With Torq, your ASM strategy is always-on, automated, and agile.
Don’t wait to react. Don’t accept blind spots.
FAQs
Torq Hyperautomation™ transforms attack surface management from a static, manual process into a dynamic, automated capability. Traditional ASM often involves periodic scans and manual triage, which leave gaps in visibility and delay remediation. Torq eliminates these blind spots by continuously orchestrating real-time asset discovery, risk prioritization, and automated response across your existing security stack.
This allows security teams to instantly detect new exposures and take immediate action without human intervention. By replacing fragmented processes with intelligent, automated workflows, Torq significantly reduces response time, operational overhead, and risk of oversight.
Yes — effective ASM is an enabler of compliance. Regulatory frameworks like HIPAA, PCI-DSS, and ISO 27001 require organizations to maintain visibility into their digital environments and actively manage vulnerabilities. Torq supports this by automatically inventorying assets, tracking configuration changes, and documenting remediation efforts.
Compliance reporting becomes faster and more accurate, with up-to-date telemetry across hybrid and multi-cloud environments. Torq also automates audit preparation through prebuilt workflows that map findings to compliance controls, helping security and GRC teams demonstrate ongoing adherence.
Industries with high-value data and strict regulatory requirements stand to gain the most from comprehensive ASM, including finance, healthcare, retail, manufacturing, and technology. These sectors often face sprawling digital footprints, complex supply chains, and increasing attack surface due to remote work and cloud adoption.
Torq tailors its Hyperautomation workflows to meet the unique operational and compliance demands of each industry, whether it’s protecting financial APIs, securing electronic health records (EHRs), or enforcing zero trust policies in distributed cloud environments.
Torq breaks down silos between SecOps, IT, and cloud teams by providing a centralized automation platform that unifies threat detection, incident response, and asset visibility. Teams can collaborate on shared playbooks, receive alerts through integrated channels like Slack or ServiceNow, and maintain role-based access to workflows and data.
Torq’s automated workflows ensure consistent execution while allowing human oversight when needed, improving alignment and accelerating decision-making across teams. The result is faster response, reduced miscommunication, and a unified approach to attack surface defense.