Contents
Get a Personalized Demo
See how Torq harnesses AI in your SOC to detect, prioritize, and respond to threats faster.
Every day, analysts are buried under a mountain of low-value and often meaningless alerts. And they’re expected to triage, investigate, prioritize, and respond to all of them — faster, better, and with fewer people. With this comes cybersecurity alert fatigue, which can lead to missed threats, slower response times, and SOC analyst burnout.
The good news is that SOC analysts don’t have to live like this anymore. Not if you have the right kind of AI working for you. This blog explores what security alert fatigue is, the causes, and how agentic AI can kill your SOC alert fatigue.
What is Alert Fatigue?
Cybersecurity Alert Fatigue
Alert fatigue in cybersecurity refers to the desensitization and exhaustion experienced by security analysts when they are overwhelmed by a high volume of security alerts, many of which are false positives or low-priority events. This can lead to missed or ignored true threats, potentially causing significant security incidents and breaches.
More than half of security teams say false positives are a huge problem, and 62.5% are overwhelmed by sheer data volume. Without effective triage or prioritization, it becomes harder to distinguish real threats from background noise. This leads to slower detection and response, missed incidents, and higher stress on already-stretched SOC teams, which in turn increases risk to the business.
What Causes Cybersecurity Alert Fatigue?
Alert fatigue is the result of too many notifications with too little value. And it’s a problem that only gets worse as security environments become more complex. Here’s what’s driving it.
Excessive False Positives
False positives occur when security systems incorrectly flag benign events as threats. SOC teams inundated with false positives quickly become overwhelmed and stop trusting the alerts altogether. A recent study indicated that more than half of security alerts are false positives, making analysts skeptical about their legitimacy.
Poorly Tuned Detection Rules
Security monitoring tools like SIEM and SOAR platforms rely on detection rules to trigger alerts. When these rules are not properly tuned or regularly updated, they generate an overwhelming volume of irrelevant alerts, contributing significantly to SIEM alert fatigue and SOAR alert fatigue.
Lack of Context in Alerts
Without context, analysts spend valuable time manually investigating alerts to determine their relevance and severity. Contextual information, such as user details, historical activity, and threat intelligence, is essential for quick decision-making — yet many systems fail to provide it.
Manual Triage Processes
Manually sorting through thousands of daily alerts to decide which ones require attention is tedious and error-prone. Human analysts have limits on processing speed and focus, leading to mistakes, missed threats, and inevitable burnout.
Human Limits in Processing Volume and Urgency
Human cognition has inherent limitations. When faced with a high volume of urgent tasks, analysts inevitably experience exhaustion, become less effective, and experience reduced productivity, exacerbating overall security team burnout.
Legacy SOAR
Legacy SOAR is the #1 driver of SOC alert fatigue. It’s a rigid model that treats every alert like a five-alarm fire. It floods analysts with noise, drowns them in contextless data, and racks up costs with every added integration. And because most legacy SOAR platforms are stuck on-prem, they can’t scale or flex with today’s modern security environments.
The Cost of Alert Fatigue in Cybersecurity
Missed vulnerabilities, delayed incident response: When analysts become numb to the constant flood of alerts, critical incidents can slip through unnoticed. Missed threats or delayed responses increase the likelihood of successful cyberattacks, leading to data breaches or significant operational disruptions.
Burned-out analysts and high turnover: Continuous exposure to high stress and repetitive tasks results in analyst burnout. Studies indicate that more than 70% of SOC analysts report burnout, driving skilled talent away and compounding the cybersecurity skills shortage.
Diminished trust in security systems: When false alarms dominate, analysts lose faith in their tools and processes. This lack of trust can lead to negligence or poor decision-making, ultimately undermining your entire cybersecurity posture.
Increased exposure to threats: Ignoring genuine alerts due to fatigue directly translates to higher vulnerability to cyber threats. Attackers exploit this weakness, capitalizing on diminished responsiveness to launch successful attacks.
Wasted resources: Teams overwhelmed by junk alerts often require more headcount. That’s expensive and inefficient.
Reputation damage: When a preventable breach hits the headlines, the fallout can be massive.
Legal and compliance issues: Missed threats can turn into breaches. Breaches mean SEC reporting, fines, investigations, and answering a whole lot of questions.
The average cost of a data breach was $4.9M in 2024, a 10% increase year over year. On the flip side, organizations that fully embraced security AI and automation saved an average of $2.2M compared to those that didn’t, according to IBM.
How Automation Helps You Beat Alert Fatigue
Security automation has become an essential solution for SOC teams to significantly reduce cybersecurity alert fatigue. Here’s how automation addresses the core issues.
Alert enrichment at scale: Automation enriches alerts with relevant context automatically, including threat intelligence data, historical user behavior, and asset criticality, enabling rapid and informed decisions.
Correlation and deduplication: Automation tools correlate related alerts and remove duplicates, drastically reducing noise. Analysts receive fewer but more comprehensive and meaningful incidents, improving efficiency and accuracy.
Routing to the right responder: Automated systems ensure alerts reach the appropriate analyst based on expertise, urgency, or resource availability. This eliminates delays in assignment, balances resource utilization, and improves team responsiveness.
Automated remediation of low-risk threats: Remediating low-risk incidents autonomously significantly reduces repetitive tasks. This allows analysts to prioritize their time and attention on high-severity threats.
Feedback loops for smarter alerting: AI-driven automated systems can learn from past incidents, continuously refining detection rules and processes to reduce false positives and enhance accuracy, minimizing future alert fatigue.
How To Combat Alert Fatigue
While automation is the key solution, here are other best practices your SOC team can implement to reduce alert fatigue further:
- Regular optimization: Routinely updating detection rules can somewhat reduce irrelevant alerts.
- Prioritization strategies: Clearly define which alerts matter most based on business risk and prioritize accordingly.
- Enhanced alert context: Invest in tools providing contextual intelligence so analysts quickly understand the nature of each alert.
- Regular training and support: Ensure your team has access to continuous education and training, reinforcing resilience and reducing burnout.
- Centralized management: Consolidate alerts into a single case management platform to streamline workflows and reduce duplication.
5 Benefits of Automating Cybersecurity Alert Triage
Automating alert triage doesn’t just address fatigue; it transforms your entire security operation.
- 80% fewer alerts reaching human analysts: Automation filters out irrelevant alerts, dramatically decreasing the number of notifications analysts need to review, significantly reducing cybersecurity fatigue.
- Faster time to detect and respond (MTTD/MTTR): Automation reduces both mean time to detect (MTTD) and mean time to respond (MTTR), allowing analysts to act swiftly and decisively when genuine threats appear.
- Reduced analyst burnout and turnover: By offloading repetitive tasks, automation allows analysts to focus on more engaging, complex issues that require critical thinking, significantly reducing burnout and improving job satisfaction.
- Higher confidence in escalated alerts: With fewer false positives and enriched context, analysts have more trust in alerts escalated to them, ensuring quick and effective response.
- Measurable reduction in false positives: Automated feedback loops continuously improve detection logic, resulting in fewer unnecessary alerts over time, further reducing security alert overload.
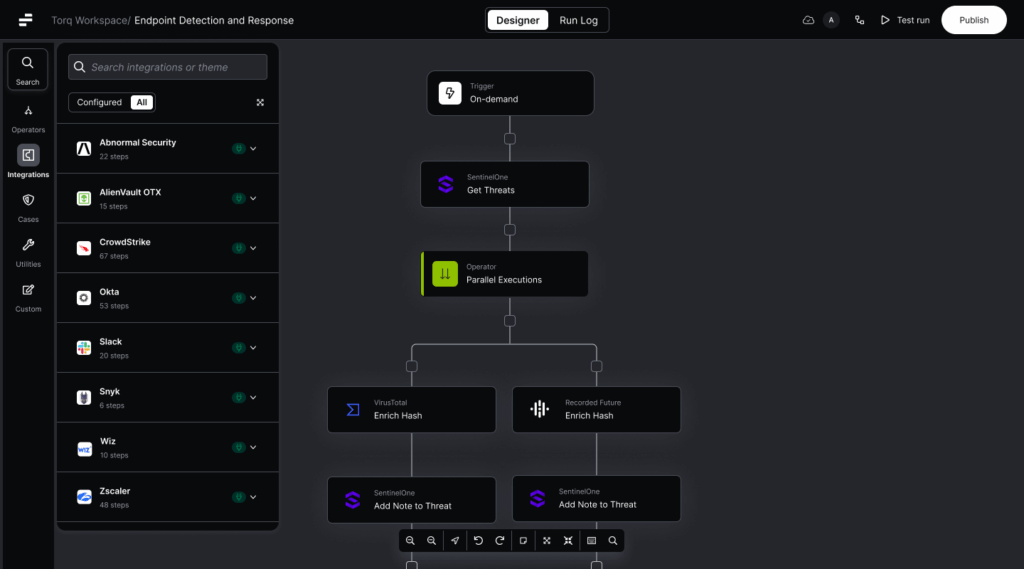
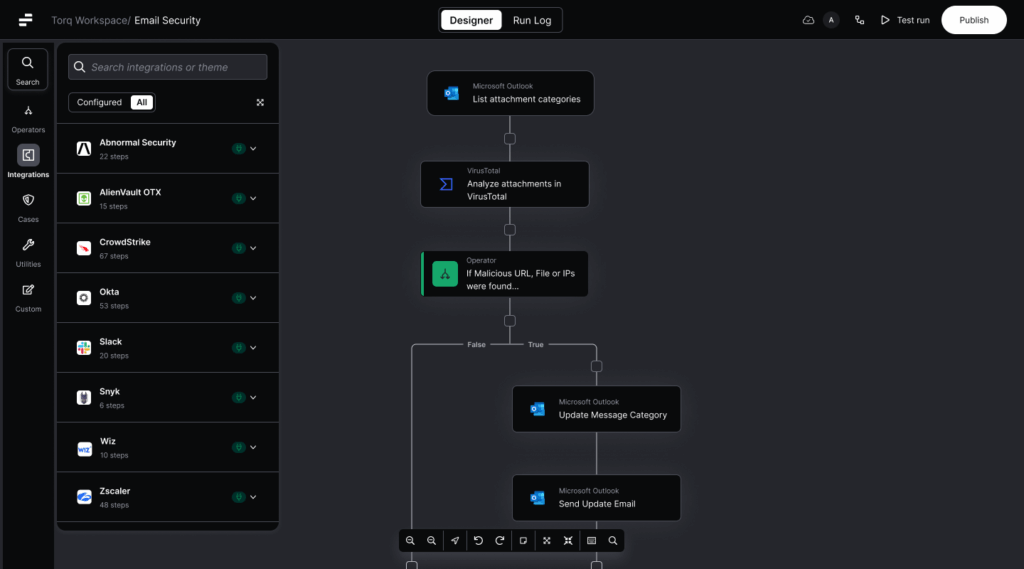
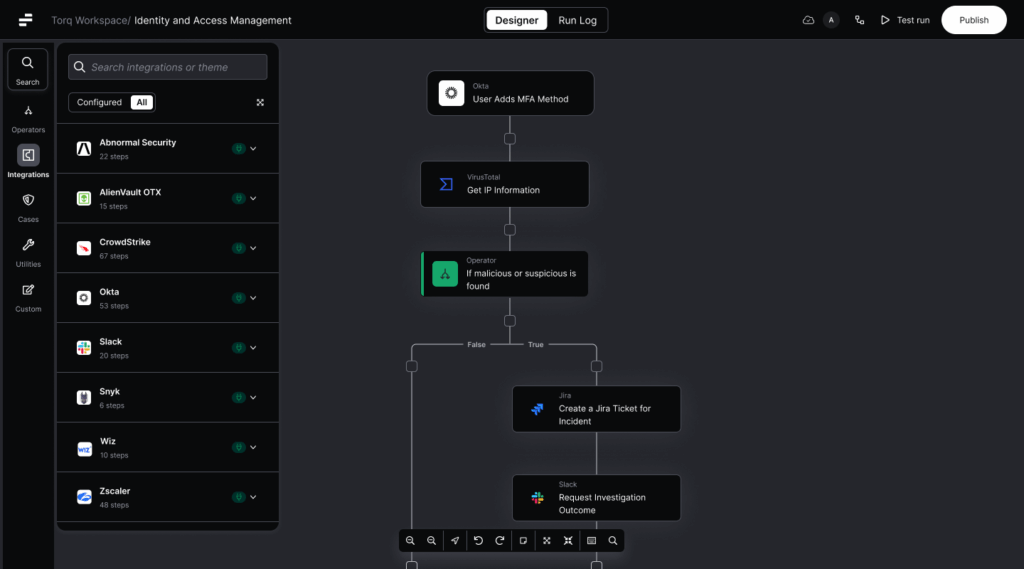
How Torq Can Prevent Cybersecurity Alert Fatigue with Automation
Security teams have always relied on automation to streamline repetitive tasks, but traditional automation still requires substantial human oversight and manual intervention. Hyperautomation, however, elevates security operations to an entirely new level by combining advanced deterministic automations with AI-driven non-deterministic automations for real-time adaptive decision-making capabilities.
Unlike basic automation, which crumbles under the pressure of too many complex alerts, Hyperautomation handles volumes that SOAR and other legacy platforms can’t even come close to. It dynamically filters, enriches, correlates, and aggregates alerts at machine speed, ensuring analysts see what actually matters.
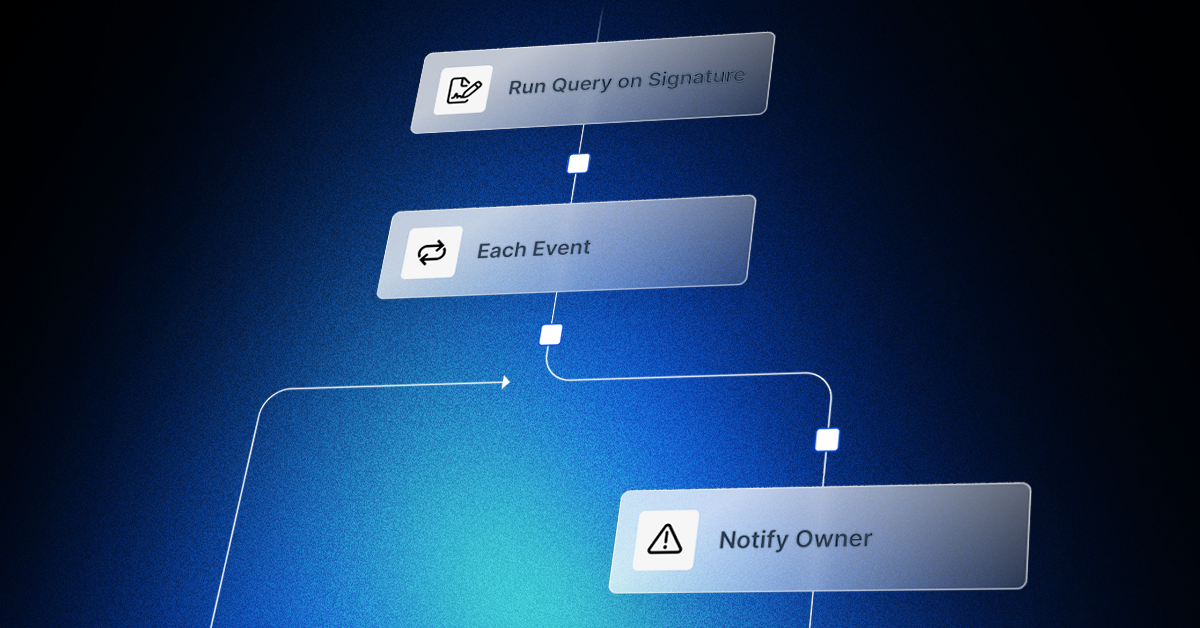
Torq HyperSOC™ takes Hyperautomation a step further by integrating agentic AI — an intelligent system capable of autonomous reasoning, decision-making, and iterative planning — to manage security operations at unprecedented speed and scale. Torq HyperSOC dynamically adapts, picking the most appropriate Hyperautomation workflows based on live data and context, enabling autonomous resolution of complex security issues.
Unlike traditional automation, agentic AI iteratively plans and reasons, adjusting actions based on real-time context. It automatically filters noise, enriches data, correlates related alerts, and resolves low-risk incidents without human intervention.
With agentic AI, Torq has replaced repetition with relevance. Our multi-agent system takes on the tasks that drain analysts most — triage, enrichment, correlation, case summaries, even full remediation—and executes them autonomously. Analysts no longer have to sift through countless meaningless alerts because HyperSOC escalates only those that truly require human attention. That means fewer panicked 2 a.m. Slacks and “Why am I still doing this manually?” moments.
“Torq HyperSOC is the first solution we’ve seen that effectively enables SOC professionals to mitigate issues including alert fatigue, false positives, staff burnout, and attrition.”
IDC: Achieving Machine Speed Detection and Response
Torq HyperSOC achieves:
- Up to 95% reduction in alert volume: HyperSOC automatically filters, correlates, and prioritizes alerts, drastically reducing noise for analysts.
- Real-time incident remediation: Automates end-to-end response, resolving low-risk threats autonomously without human intervention.
- Accelerated mean time to detect and respond (MTTD/MTTR): Identifies and addresses critical security incidents in seconds, minimizing potential damage.
- Reduced analyst burnout and improved rroductivity: Offloads repetitive tasks, freeing SOC analysts to focus on high-value activities that require human expertise.
With HyperSOC, SOC analysts can finally shift from constantly firefighting false positives to focusing their expertise on high-impact threats that demand human ingenuity.
Legacy SOAR vs. Torq HyperSOC™: Solving Alert Fatigue
Here’s how Torq HyperSOC™ stacks up compared to legacy SOAR systems when it comes to solving cybersecurity alert fatigue.
| Legacy SOAR | Torq HyperSOC |
| SOC alerts are treated like a five-alarm fire, with no intelligent prioritization | Agentic AI triages and prioritizes alerts with semantic, episodic, and procedural memory |
| Inflexible, SIEM-dependent pipelines for noise reduction and enrichment | Hyperautomation eliminates SIEM dependency and enriches data on the fly |
| Manual alert triage leads to SOC burnout and delays | AI-driven triage, investigation, and remediation reduce analyst burden |
| Rigid, on-prem architecture limits scalability and flexibility | Cloud-native architecture scales effortlessly with your environment |
| Siloed tools and alerts lack unified context | Multi-agent system correlates alerts into unified incidents with full context |
| Slower response times due to disconnected systems and workflows | End-to-end automation delivers sub-minute response times |
| High analyst turnover from alert overload and frustration | AI offloads repetitive work, reducing burnout and improving retention |
By taking over the repetitive, time-consuming tasks that drive SOC burnout, agentic AI lets analysts do the work that actually matters. You know, the reason they got into security in the first place.
Hyperautomation is the Answer to Cybersecurity Alert Fatigue
The constant flood of alerts compromises response times, erodes analyst trust, causes burnout, and directly increases your organization’s cyber risk. Without addressing cybersecurity alert fatigue, your security strategy is fundamentally flawed.
Hyperautomation, driven by advanced AI, provides a decisive answer to alert fatigue. By automating routine, repetitive tasks and prioritizing real threats, it drastically enhances SOC efficiency and resilience. Torq’s HyperSOC, with its innovative agentic AI, stands at the forefront of this solution, empowering teams to work smarter, not harder.
Ready to take control of your alerts and eliminate SOC burnout once and for all? Learn how to kill your SOAR.