Contents
Get a Personalized Demo
See how Torq harnesses AI in your SOC to detect, prioritize, and respond to threats faster.
Managed security service providers (MSSPs), desperate to automate repetitive tasks, initially turned to SOAR to reduce their workload and improve threat response times.
But legacy SOAR still stalls at scale, struggles with multitenancy, and breaks on fast-moving APIs — so teams end up babysitting playbooks instead of stopping threats. That’s why leading MSSPs are switching to Torq Hyperautomation: event-driven and massively scalable, with agentless integrations,and no/low-code and AI-generated workflows that turn Tier-1 tasks into hands-off outcomes.
Where Legacy SOAR Breaks for MSSPs
Scalability issues: Legacy SOAR platforms don’t handle alert spikes well. When volumes surge, their schedulers queue work serially, pipelines back up, and response times slip. The result is delayed containment, missed SLAs, and a SOC that’s waiting on tooling instead of stopping threats.
Lack of true multitenancy: Most SOAR tools weren’t built to isolate tenants. A burst of noisy events for one customer can starve resources and slow playbooks for everyone else. For MSSPs running dozens of environments, that bleed-through turns one client incident into a cross-tenant performance hit.
Integration complexity: Connecting customer tools should be routine, but with legacy SOAR, it’s a big project. Custom connectors take weeks to build, break when APIs change, and demand ongoing care and feeding. Teams end up maintaining glue code or paying for professional services, burning time and margin that should go to defending customers.
High maintenance costs: Legacy SOAR products often come with high maintenance costs in terms of time and resources. An organization might use around 25 different playbooks for different services and integrations, each requiring regular updates and optimization. Before long you’re maintaining dozens of near-duplicates, versioning them, testing them, and fixing scripts after every platform update. The operational overhead snowballs and erodes profitability.
Limited customization and flexibility: SOAR stacks lock down scripting and libraries, which cap what you can actually build. If you can’t use common SDKs or craft custom logic, you’re stuck with canned steps that don’t match real-world workflows. Analysts spend more time working around the platform than improving outcomes.
Hyperautomation: Built for MSSP Scale
Legacy SOAR tools weren’t designed for the scale, complexity, and economics that MSSPs face today. They’re monolithic, brittle, and reliant on endless scripting to keep up with changing APIs and customer environments. As MSSPs grow, those limitations compound — onboarding slows down, SLA penalties mount, and gross margins erode. At Torq, we deemed SOAR dead, and industry analysts followed suit.
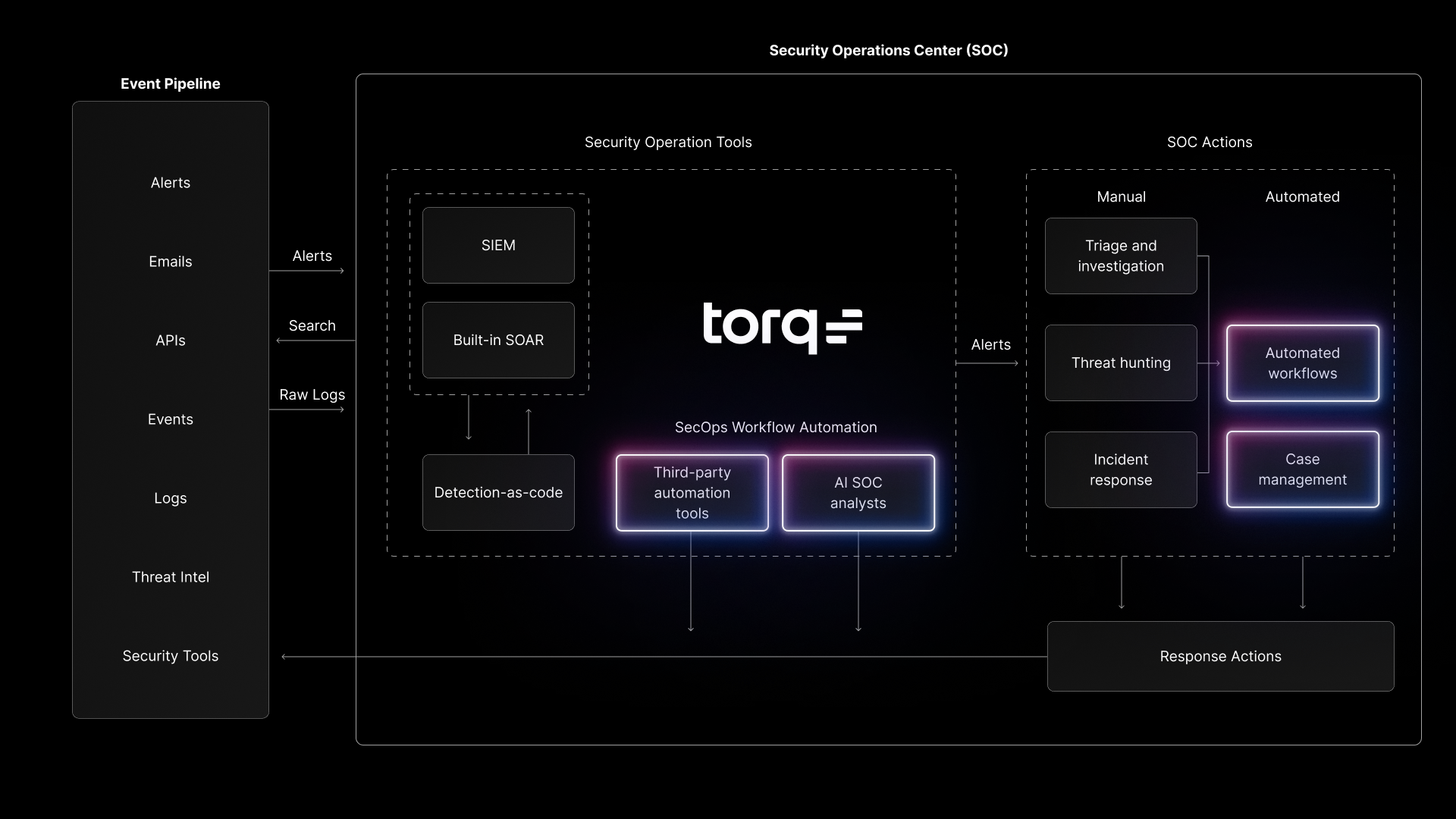
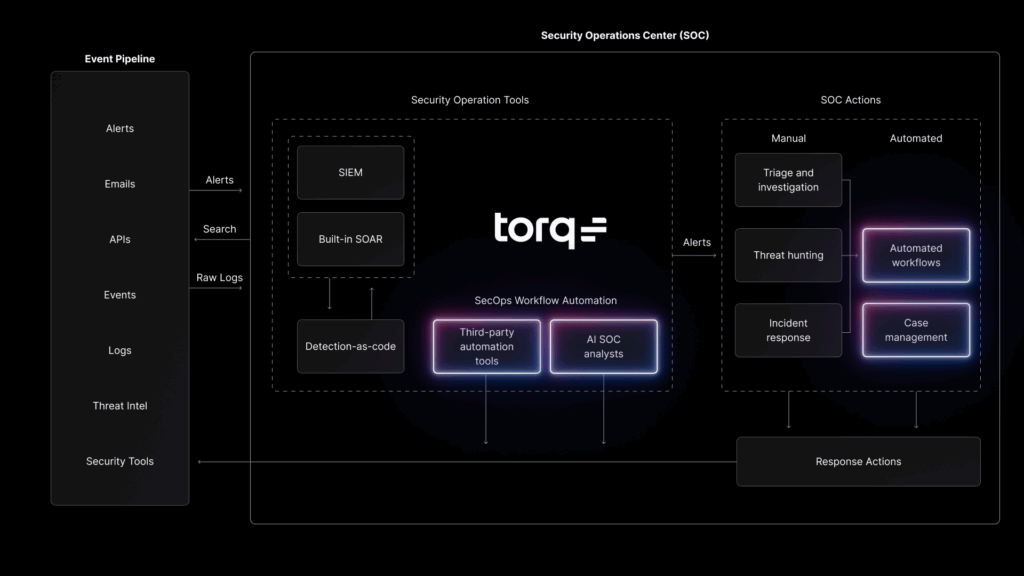
Security Hyperautomation is different. It’s event-driven, horizontally scalable, and built for multi-tenant operations from the ground up. Torq enables MSSPs to orchestrate real-time alerts and responses across dozens or hundreds of unique customer stacks.
Key advantages of Torq for MSSPs include:
- Parallel execution: Torq runs thousands of workflows simultaneously, ensuring tenants never compete for capacity.
- No-code/low-code and AI-built automation: Analysts can build, customize, and deploy workflows in hours — accelerating onboarding and reducing the need for engineering resources.
- Limitless integrations: With 300+ native connectors and containerized options, Torq adapts to any toolset, no matter how fragmented or fast-changing.
- AI-assisted efficiency: Torq’s AI SOC Analyst, Socrates, enriches, correlates, and classifies cases automatically, while analysts approve high-risk actions through Slack, Teams, or ITSM.
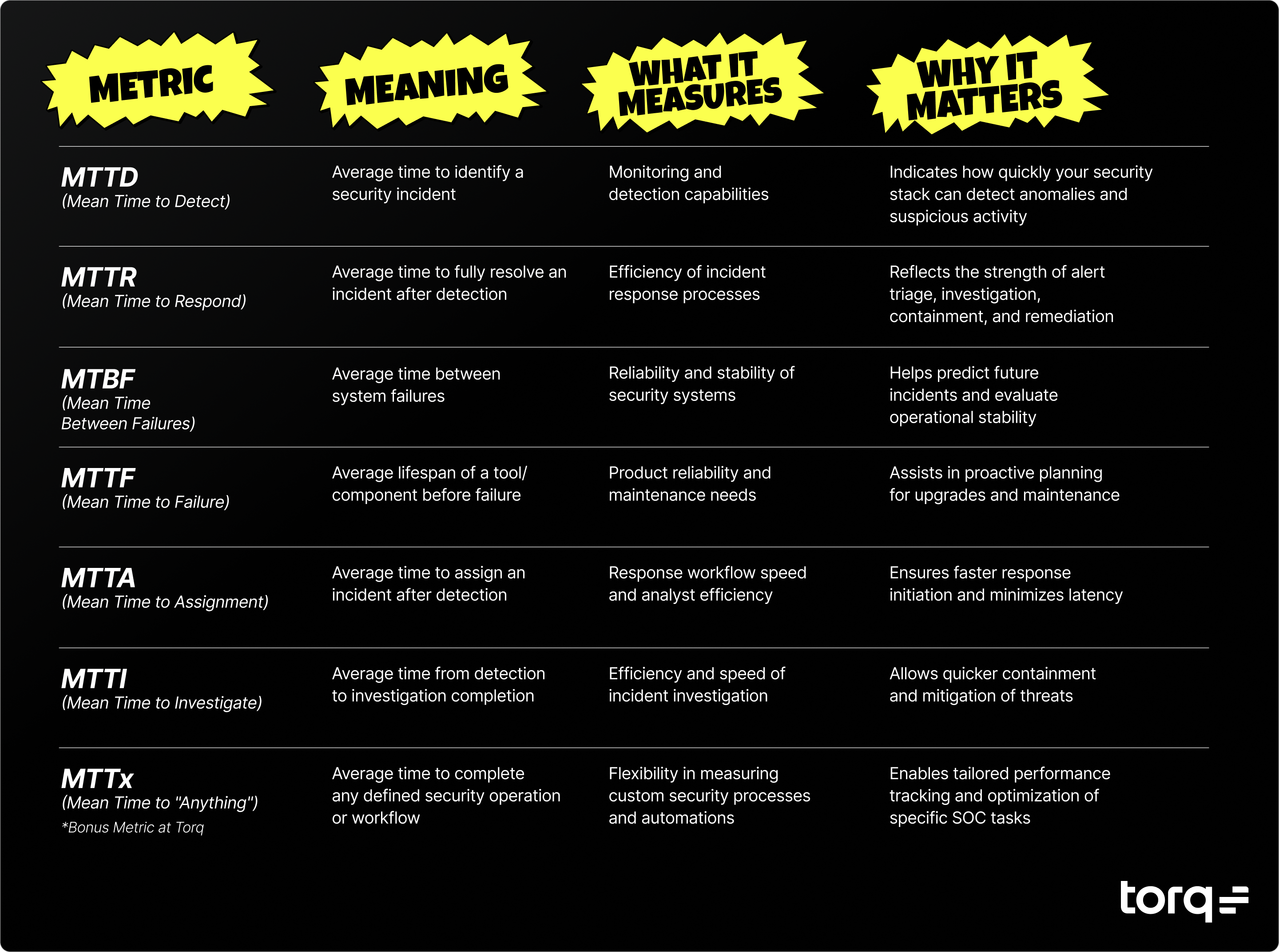
For MSSPs, this means Tier-1 cases can be fully automated, Tier-2 streamlined with supervised approvals, and Tier-3 supported with rich AI-driven context. The result: reduced MTTR, happier customers, and healthier margins — even as alert volumes and customer counts grow.
How MSSPs Use Torq Hyperautomation
Accelerating onboarding: Every new customer brings a unique stack of firewalls, EDRs, SaaS apps, and cloud platforms. Instead of writing one-off automation scripts, MSSPs use Torq’s template-first playbooks with tenant-specific variables and policy toggles. This lets them onboard new clients in hours or days — not weeks — while maintaining consistency across tenants.
Meeting SLAs: SLA exposure through missed MTTA or MTTR is a top MSSP pain point. With Torq, Tier-1 alerts are fully automated — phishing, commodity malware, suspicious logins, impossible travel — and higher-risk actions are gated for analyst approval in Slack or Teams. Every case is logged with timestamps and actions, making SLA reporting defensible and reducing penalties.
Handling integration complexity: Customers bring dozens of different tools, many with fast-changing APIs. Torq’s 300+ native integrations, containerized connectors, and no-code customization allow MSSPs to connect “anything to anything” without custom code. This flexibility reduces the integration maintenance tax that eats into MSSP margins.
Reducing analyst burnout: MSSPs often deal with massive alert queues across tenants. Torq automates over 90% of Tier-1 triage and enrichment, suppresses false positives, and prioritizes high-risk cases. Analysts spend less time on swivel-chair tasks and more on threat hunting and customer strategy.
Delivering continuous optimization: Clients expect not just coverage but ongoing improvement. Torq enables MSSPs to measure MTTR, suppression rate, and analyst touches per case across all tenants. Workflows can be tuned continuously, and reports are compliance-ready for SOC 2, NIST, HIPAA, or industry-specific audits.
The business impact for MSSPs: Faster onboarding (up to 18×), faster workflow creation (10×), automated handling of up to 95% of Tier-1 alerts, and more substantial gross margins per customer.
The MSSP Hyperautomation Playbook: How HWG Sababa Doubled SOC Output
A few years ago, Italy-based MSSP HWG Sababa faced a tipping point in its growth. Instead of trying to squeeze more efficiency out of scripts and manual processes, it rebuilt its SOC around Torq Hyperautomation™. The result was a complete step-change in scale and efficiency.
Within weeks of adopting Torq, HWG Sababa:
- Automated 55% of monthly alerts by targeting repetitive Tier-1 cases first
- Cut MTTI and MTTR by up to 95% for routine alerts and 85% for high-priority threats
- Nearly doubled SOC productivity and capacity without adding headcount
- Boosted analyst morale and retention by eliminating repetitive, burnout-inducing tasks
- Reduced customer-side effort by automating remediation actions directly in client environments
Marco Fattorelli, Head of Innovation at HWG Sababa, said Torq enabled them to deliver automated threat detection, containment, and remediation inside customer environments, saving clients hours of manual effort while strengthening trust and satisfaction.
The takeaway is this: Hyperautomation isn’t just a technical upgrade for MSSPs — it’s a competitive differentiator. By combining no-code workflows, vendor-agnostic integrations, and AI-driven case management, MSSPs like HWG Sababa prove ROI instantly while building more scalable and sustainable SOCs.
“Based on customer feedback when we showcase our services, Torq is the ideal solution for adding value to our managed SOC, particularly with its seamless integrations. By accelerating our automations and responses, Torq Hyperautomation helps us stay ahead of the curve and the competition.”
Join the World’s Top MSSPs in Ditching Legacy SOAR
Legacy SOAR can’t keep pace with the multi-tenant scale, SLA pressure, and tooling diversity MSSPs face every day. Hyperautomation fixes the foundation: elastic execution that never stalls during spikes, true tenant isolation, plug-anything integrations, and AI-assisted workflows that turn the Tier-1 grind into hands-off outcomes. That’s how managed security service providers protect margins while delivering faster MTTR, stronger SLAs, and happier analysts.
MSSPs worldwide use Torq Hyperautomation to stamp reusable playbooks across tenants, orchestrate any stack, capture audit-ready evidence by default, and gate high-risk actions through Slack/Teams.
Ready to trade scripting and an endless backlog for scalable, multi-tenant automation? Get the Managed Services Manifesto.