Last Updated December 2025
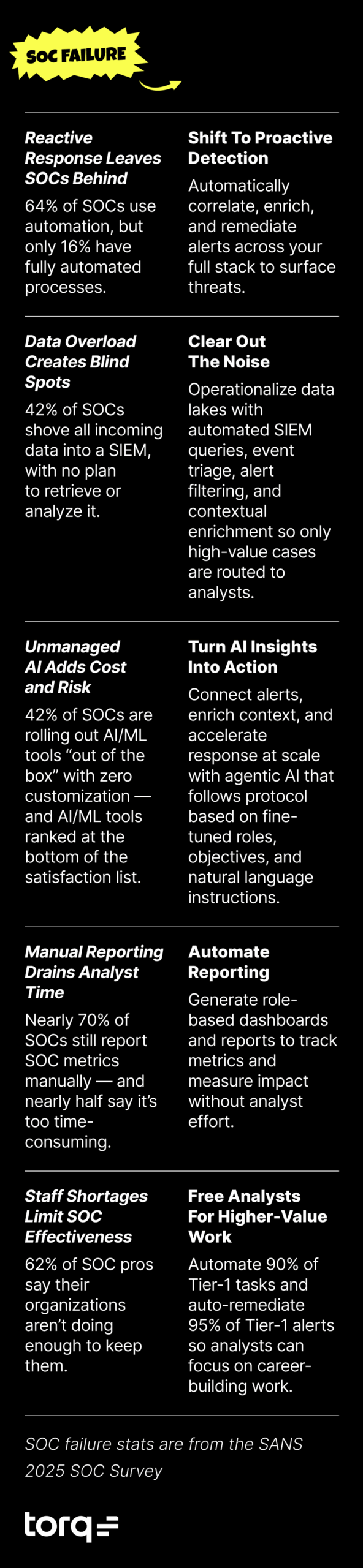
Security operations aren’t failing due to a lack of effort; they’re breaking under pressure. As hybrid cloud environments, SaaS tools, and identity-first architectures scale, they produce more telemetry and alerts than manual workflows can realistically handle. That’s why the benefits of security automation are more than convenience.
Security automation — and increasingly Hyperautomation — is transforming modern SOC operations. By converting repetitive, manual processes into intelligent, orchestrated workflows, teams can scale incident response, reduce alert fatigue, and dramatically cut mean time to respond (MTTR).
Here’s your guide to the benefits of security automation, how top-performing teams implement it, and how Torq Hyperautomation™ enables more resilient full-lifecycle security operations.
Benefits of Security Automation
Security automation uses technology to streamline and execute repetitive security tasks — alert triage, threat enrichment, and response — without manual intervention. This leads to faster detection and response times, reduced alert fatigue, and improved analyst productivity. Automation also strengthens an organization’s overall security posture and compliance readiness by standardizing actions and ensuring full audit trails.
But the real value of security automation emerges when you look at how it transforms the everyday challenges SOC teams face. Modern SOCs aren’t breaking down because analysts lack skill or effort — they’re overwhelmed by the volume, speed, and fragmentation of today’s threat landscape. That’s where automation steps in: not as a convenience, but as the only scalable path forward.
Faster MTTD/MTTR, Reduced Alert Fatigue
Every SOC leader knows the grind of manual triage: Open an alert, pivot to logs, enrich with asset/identity context, check threat intelligence, decide next steps, document. Repeat hundreds of times per day.
Security automation tools allows for:
- Parallel enrichment: Automatically attaches ownership, geolocation, recent activity, and risk context the moment an alert is generated.
- Deduplication and correlation: Related alerts are collapsed into a single case with ranked observables, reducing noise and saving time.
- Automated decision routing: Events are triaged based on policy and risk — either fully automated, escalated to human-in-the-loop, or closed with evidence.
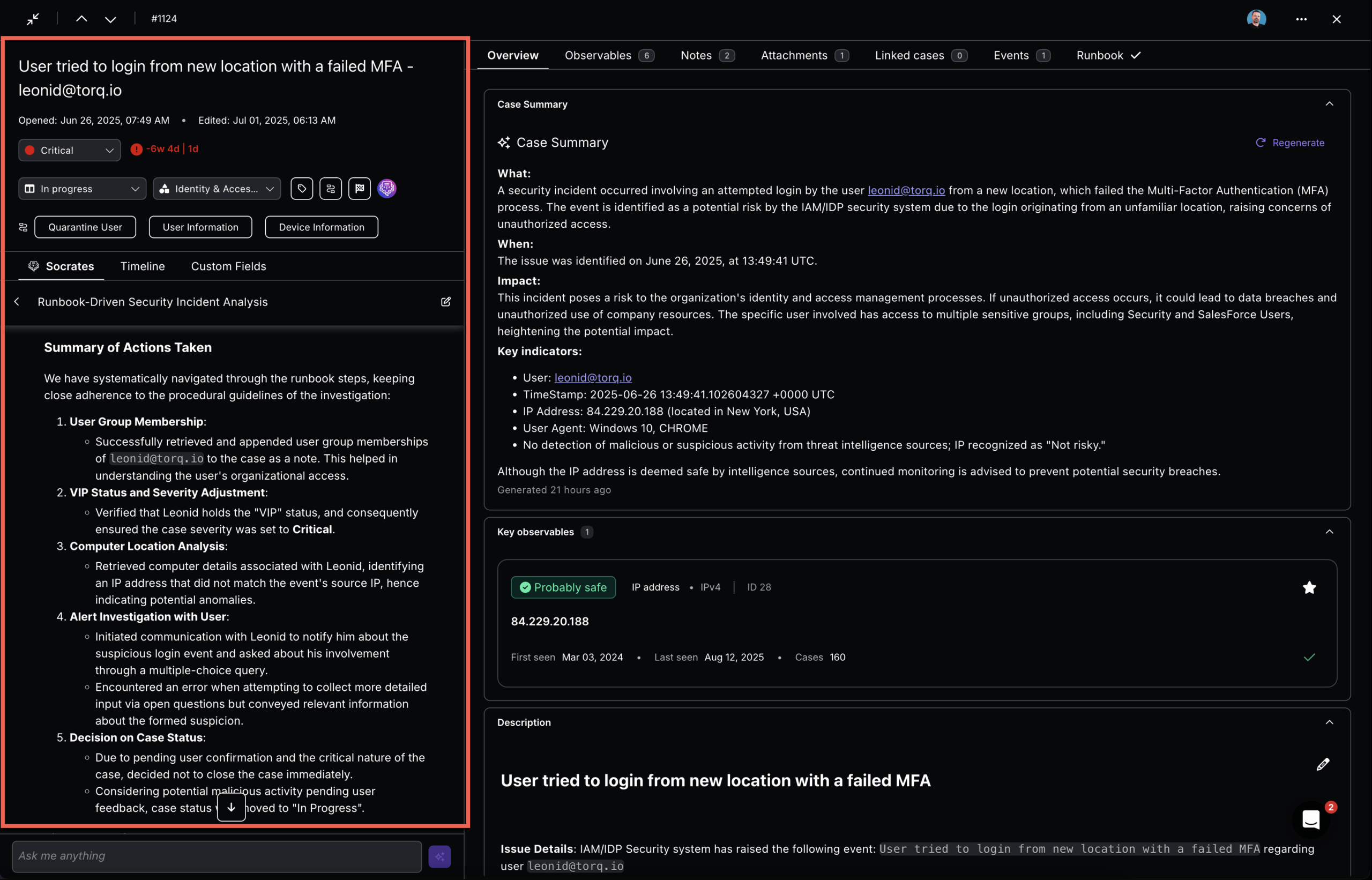
In Torq, this is modeled with workflows, triggers, and steps that enrich, correlate, and act, then persist everything to cases. Features like the Query Cases step help deduplicate or bulk-operate on related cases, cutting repetitive review to near zero.
Autonomous Case Management
Ticket-based systems fragment incident response. Automated security replaces this with a case-centric approach — a single narrative that unifies alert data, context, actions, and documentation.
Torq’s case model supports:
- Auto-generated cases triggered by any tool
- Attached indicators of compromise (IOCs), logs, verdicts, screenshots, and analyst notes
- Dynamic updates to status and assignees (via Slack or Teams)
- Case querying for deduplication and threat hunting
Analysts start with a coherent, enriched narrative, not a blank page — shortening MTTI and MTTR.
Full-Lifecycle Response
Many tools advertise “automation” that ends with a ping or a basic API call. True automated security must handle the entire detection-to-resolution lifecycle:
- Detect/Ingest: Collect and correlate from SIEM, EDR, cloud, identity, or email
- Enrich/Correlate: Layer in asset, identity, threat intelligence, drift, and activity context
- Decide: Apply policy and risk posture
- Respond: Block, quarantine, reset, rollback
- Verify: Recheck controls, confirm success
- Document: Auto-generate case timelines with all actions and evidence
Torq orchestrates that end-to-end flow with workflows and integrations, writing outcomes back to the case and ITSM, and generating an audit-ready trail by default.
Scalable, No-Code Deployment Across Cloud/Hybrid Environments
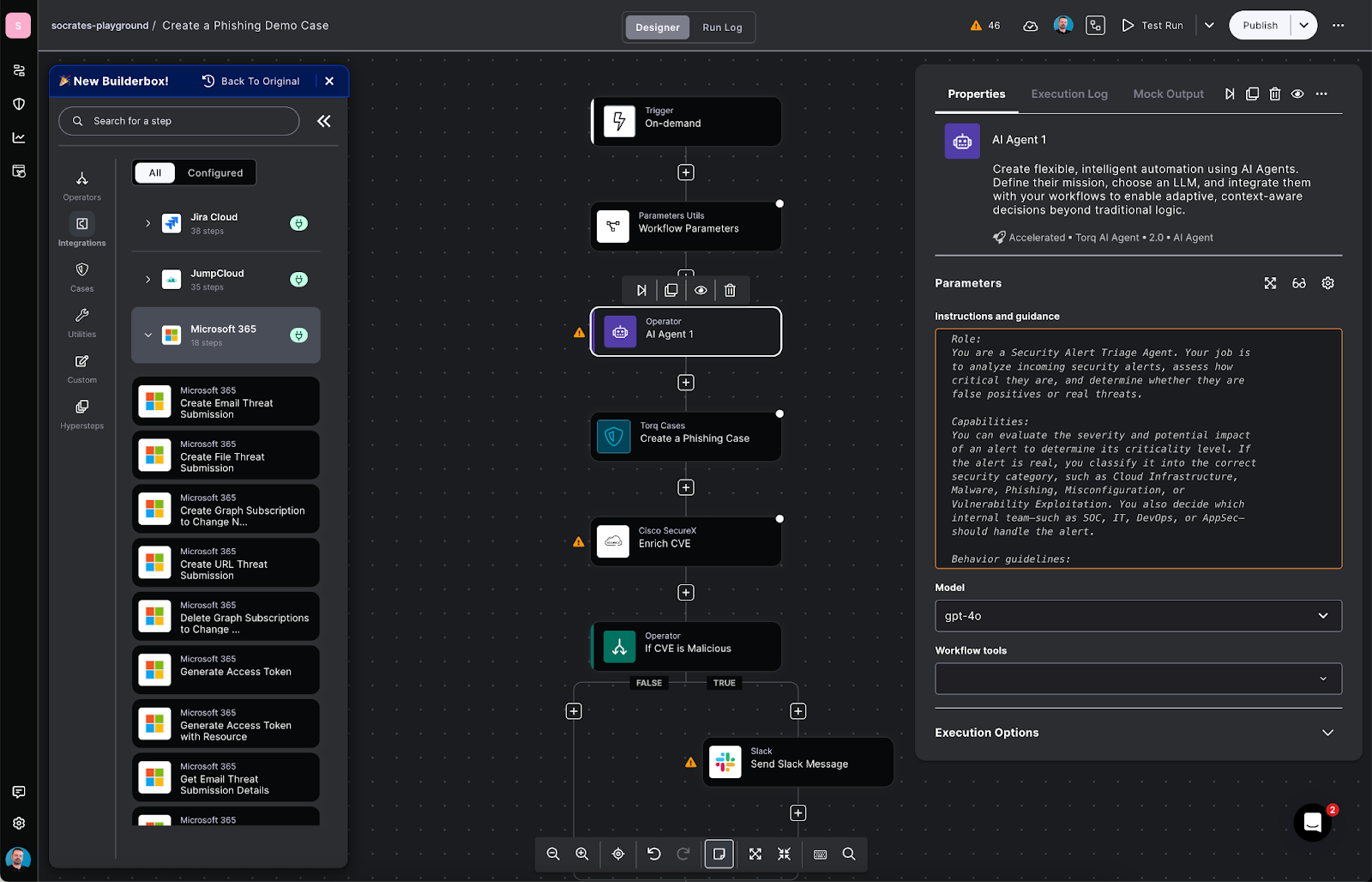
Even the best automation strategy fails if only a handful of developers can maintain it. Security automation has to be accessible. That’s why Torq makes orchestration no-code and low-code, enabling analysts, threat hunters, and responders to build and adapt workflows without specialized programming skills.
Torq’s workflow builder includes:
- Drag-and-drop steps for branching logic, loops, retries, and error handling
- Integration steps and webhook triggers for event-driven execution
- Workspace and SSO controls for governed access, with credentials centrally managed
- Reusable subflows and templates for fast rollout across teams/tenants
With Torq, teams kick off SSO, add integrations, and start building in hours — then reuse those patterns across use cases and environments.
Continuous Compliance and Audit Readiness
Instead of scrambling at the end of a quarter or audit cycle, Torq automatically documents every action taken — from detection through remediation — in real time. This ensures a defensible, evidence-backed trail that satisfies cybersecurity frameworks like SOC 2, ISO 27001, NIST, HIPAA, and SEC requirements.
By embedding compliance into daily workflows, teams reduce audit prep time from weeks to hours while proving consistent security effectiveness to executives, customers, and regulators.
All of these benefits lay the foundation for something bigger: the evolution from basic automation to full Hyperautomation and the rise of the autonomous SOC.
The Future of Security Automation: Torq Hyperautomation and the Autonomous SOC
The future of cybersecurity automation is being written in real time, and the direction is unmistakable. Macro trends are converging: data volumes double every few years, hybrid work pushes identity management to its limits, SaaS adoption fragments IT environments, and adversaries are turning to cloud-native tactics that move at machine speed. Traditional tools and linear workflows simply can’t keep up.
What’s next isn’t just automating individual tasks — it’s security Hyperautomation: Chaining automations together across the entire security lifecycle, guided by context, risk scoring, and organizational policy. Instead of responding to one alert at a time, Hyperautomation lets SOCs orchestrate enrichment, triage, containment, and compliance in a seamless, end-to-end flow.
Layered on top is the rise of agentic AI, which doesn’t just execute instructions but actively helps coordinate, summarize, and adapt workflows. AI agents will triage thousands of events simultaneously, escalate only what truly matters, and produce instant, audit-ready case narratives. The analyst’s role shifts from being “in the loop” for every click to being “on the loop,” supervising and validating higher-risk or novel incidents.
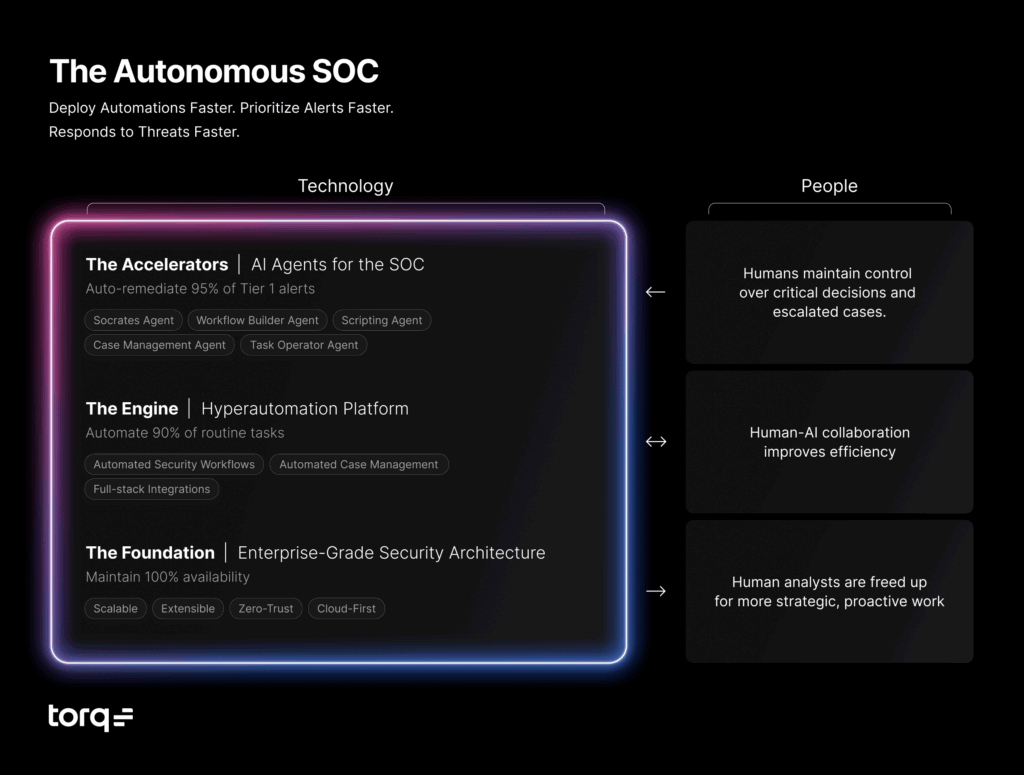
This is the foundation of the autonomous SOC, a model in which Tier-1 is handled end-to-end by automation, Tier-2 is pre-enriched and guided by AI, and Tier-3 analysts focus on strategic hunts, detection engineering, and adversary simulation. The SOC becomes not just reactive but proactive, anticipating risks, learning from every case, and continuously improving.
Torq Hyperautomation is built for this future. Torq bridges today’s security challenges with tomorrow’s fully autonomous operations with our event-driven, multi-tenant architecture, no-/low-code and AI-generated workflow builder, and Socrates, the AI SOC Analyst. It ensures teams don’t just keep pace with cloud-speed adversaries — they set the tempo.
So how do teams put this vision into practice today? The best place to start is with repeatable, high-volume use cases that deliver fast ROI.
Hyperautomation Use Cases that Deliver Fast ROI
Use Case 1: Reducing Manual Triage Work
Problem: SOCs often face high alert volume, requiring analysts to perform repetitive checks across SIEM, identity, and endpoint tools before determining severity or next steps.
How Torq helps: Workflows can automatically enrich alerts using integrations, add context from identity or asset systems, and create or update cases based on defined conditions. Torq’s execution logs ensure each step is auditable, and cases can be routed to the appropriate queue using workflow logic.
Result: Analysts begin their investigation with the necessary context already assembled by automation, reducing manual steps and improving consistency across triage workflows.
Case study: HWG Sababa adopted Torq Hyperautomation to automate the processes that consumed their SOC analysts’ time, specifically alert management and manual TIer-1 processes. After replacing years of hand-coded automations in just weeks, Torq now autonomously processes about 55% of their monthly alert volume — enriching, correlating, and responding before an analyst ever touches the case. Key outcomes include:
- 95% faster MTTI/MTTR for medium- and low-priority events and 85% faster for high-priority alerts.
- Near-doubling of SOC productivity as Torq took over repetitive Tier-1 tasks.
- Improved analyst morale, with teams freed from tedious checks and able to focus on high-value investigations.
- Reduced customer effort, as Torq now performs containment and remediation actions automatically on behalf of HWG Sababa’s clients.
Use Case 2: Speeding Up Incident Response
Problem: Incident response often requires actions across several systems — isolating assets, updating tickets, sending notifications, and validating changes — all of which take time when performed manually.
How Torq helps: Torq workflows can orchestrate actions across SIEM, EDR, IAM, cloud platforms, ITSM, and collaboration tools. A single alert-triggered workflow can perform enrichment, initiate response steps, notify users or teams, and update cases or tickets.
Result: By centralizing and automating these repeatable tasks, SOC teams reduce tool-switching and increase the speed and consistency of incident handling. Analysts receive a pre-enriched case with completed actions, allowing them to focus on decision-making rather than manual execution.
Case study: Agoda adopted Torq to speed up their incident response processes while running a lean, globally distributed team. With Torq, every SIEM alert now fires automated enrichment and containment actions, handing analysts pre-investigated alerts and isolating threats even when the team is offline. Key wins include:
- Phishing fully automated end-to-end: Employees now receive verdicts in minutes, with zero analyst involvement.
- Password resets and app deployment requests automated, dropping resolution time from hours (or a full day) to minutes.
- Cloud risk remediation accelerated: Torq orchestrates Wiz findings and cut missed SLOs by 47%.
- Incident report creation automated: Torq + ChatGPT reduced reporting time from 6–7 hours to under 40 minutes.
Why SOC Teams Choose Torq
If you’re evaluating security automation tools, use this checklist to differentiate true systems from demo-ware:
- Event-driven: Can it respond in real time across tools like SIEM, EDR, cloud, identity, email, and chat?
- Case-centric: Can it group observables, context, actions, and notes into one object?
- Integration-first: Does it offer both prebuilt connectors and full API flexibility?
- Governed AI: Can analysts ship flows safely and at scale with retries, approvals, and error handling?
- Audit-ready: Does every run persist with full execution details and outcomes for compliance?
With Torq, the answer is yes — to all of it.
Torq replaces brittle, one-off automations with platform-level resilience thanks to:
- Purpose-built security and IT workflows
- Case-first operations for faster triage and resolution
- 300+ prebuilt integrations and universal API connectivity
- RBAC, SSO, and secure workspace governance
- Reusable templates and subflows that scale across teams and environments
It’s not just automation; it’s scalable, secure, and enterprise-ready Hyperautomation. These benefits show that security automation is no longer just about efficiency, but rather fundamentally rethinking how SOCs operate.
From Automation to SOC Autonomy
The future of the SOC is outcome-driven, not task-driven. An autonomous SOC doesn’t just execute; it thinks, verifies, and improves. Torq makes this future real by combining secure AI, case-based reasoning, and flexible orchestration into one platform that adapts to your environment.
You don’t need to rip and replace what works. You just need to connect it.
See how Torq Hyperautomation can cut MTTR and alert fatigue in under 90 days.
FAQs
What is security automation?
Security automation is the automatic execution of previously manual SOC processes — triage, enrichment, response, and documentation — so humans focus on decisions and edge cases, not tedious, repetitive work.
What are the benefits of security automation with Torq?
Torq security Hyperautomation delivers faster detection and response by automating triage, enrichment, remediation, and documentation, reducing MTTR from hours to minutes. With 300+ integrations and no-/low-code and AI-generated workflows, Torq unifies siloed tools and enables SOCs and MSSPs to scale without adding headcount. By reducing alert fatigue, automating case management, and ensuring audit-ready reporting, Torq improves both security outcomes and operational ROI.
How does Torq handle complex incident scenarios?
Torq enables security teams to manage complex incident scenarios through customizable no-code/low-code, and AI-generated workflows. Torq ensures streamlined handling of vulnerability management cases by allowing teams to define multi-step processes that incorporate different tools and contexts. Analysts can create tailored workflows that adapt to specific incident types, ensuring a thorough and efficient response every time.
How does Torq help with compliance and regulatory requirements?
Torq is designed to simplify compliance by automating documentation and reporting processes. Every action taken during an incident response is logged, creating a full audit trail. This automated documentation ensures you’re always prepared for audits while significantly reducing the manual workload of compiling compliance reports.
How does Torq future-proof security operations?
Torq’s architecture is event-driven, API-first, and designed to adapt to new tools and threats. As organizations evolve cloud, SaaS, and identity-first strategies, Torq ensures workflows scale without rewrites. Combined with Hyperautomation and AI, Torq positions SOCs to shift to autonomous security operations — where Tier-1 is handled entirely by automation.
What role does AI play in Torq’s platform?
Torq embeds agentic AI in the SOC to summarize cases, triage events at scale, and guide analysts through complex investigations. Instead of just automating clicks, AI adds context and decision support — turning thousands of raw alerts into prioritized, narrative-driven cases ready for human review.
Can Torq replace legacy SOAR platforms?
Yes. Torq is built as a modern alternative to traditional SOAR platforms. Torq’s no-/low-code orchestration, 300+ integrations, and agentic AI enable faster deployment, broader use cases, and easier maintenance. Organizations migrating off legacy SOARs cut operational overhead and unlock new automation and orchestration opportunities.
How does Torq support proactive vulnerability management?
Torq automates vulnerability management end-to-end. From ingesting scanner results to correlating with asset inventories, routing risk-based workflows, and triggering remediation or ticketing, Torq accelerates patching cycles and ensures consistent, audit-ready handling of vulnerabilities across environments.
How is Hyperautomation different?
Hyperautomation is automation at system scale: Many coordinated automations, governed by policy, context, and (increasingly) AI. Torq’s platform was built for this model, connecting your entire stack and enabling autonomous security operations.
How fast can we start with Torq?
Torq customers typically light up SSO, add integrations, and publish first workflows within days of onboarding, then expand by cloning patterns across use cases and business units. Torq provides a dedicated team and guidance for SSO, integrations, and workflow triggers to accelerate setup.