Contents
Get a Personalized Demo
See how Torq harnesses AI in your SOC to detect, prioritize, and respond to threats faster.
Phishing attacks have evolved significantly in recent years, rendering traditional, rule-based defenses ineffective against sophisticated threats. Organizations now require dynamic, context-aware defenses that understand and adapt to complex threats in real time.
Torq has delivered a production-grade anti-phishing solution leveraging a multi-agent system built on NVIDIA’s advanced AI infrastructure and the NVIDIA NeMo Agent Toolkit open source library. This initiative provides enterprises with adaptive, scalable security designed to handle evolving cyber threats.
Why Torq Built on NVIDIA AI
Today’s phishing threats are engineered to bypass even the most sophisticated rule-based detection systems. They exploit context, urgency, and behavioral nuance in ways that traditional security architectures were never designed to handle.
Torq set out to solve this problem not with another static filter, but with a dynamic, production-grade product built on a multi-agent system that works like a modern SOC: distributed, specialized, and collaborative. To do that, we needed a framework built for a modular, efficient AI platform that could scale, adapt, and be trusted in real-time enterprise environments.
That’s why we’re collaborating with NVIDIA and built this system using their NeMo Agent Toolkit and NVIDIA NIM microservices.
The NeMo Agent Toolkit enables rapid development of complex, multi-agent workflows using intuitive YAML-based configuration, plug-and-play tool integration, and support for custom large language models. Through built-in profiling and telemetry, developers gain complete visibility into agent performance, latency, and cost, making it ideal for both development and production deployments.
The NeMo Agent Toolkit works side-by-side and around existing agentic frameworks, customer enterprise frameworks, and simple Python agents. It complements any existing agentic framework or memory tool you already use, allowing you to easily integrate your existing code base into the framework.
With NVIDIA NIM, we get high-performance, containerized inference endpoints for the latest AI models from NVIDIA and the community. It’s what lets us serve different LLMs for different tasks, optimize for latency and throughput, and swap in newer models as threats evolve.
Together, these technologies let us build an autonomous decision-making engine that’s explainable and built for production from day one.
Inside the Torq Phishing Defense Architecture with NVIDIA
The multi-agent phishing defense architecture comprises specialized AI agents working collaboratively. Each agent addresses specific aspects of email analysis, mirroring the workflows used by human security operations teams for comprehensive threat assessment.
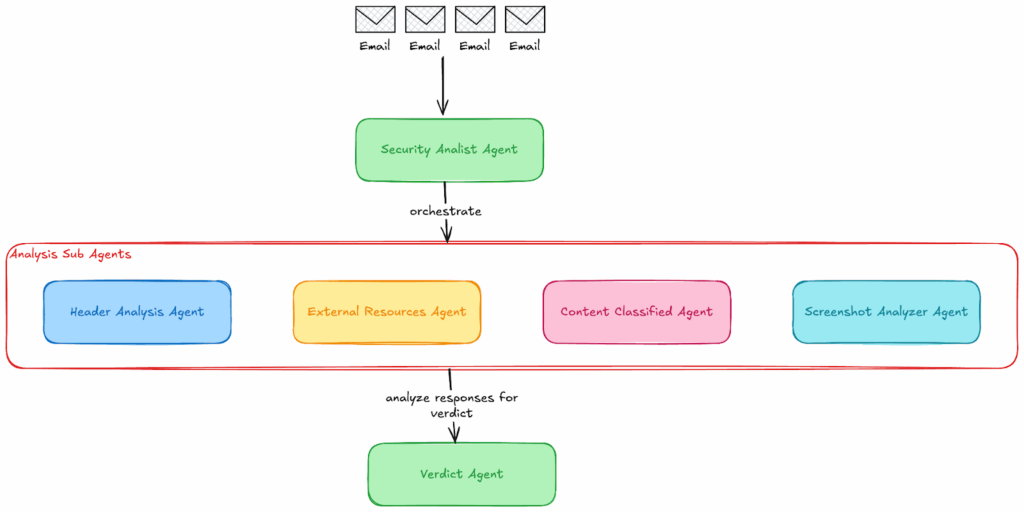
The Torq Phishing Defense architecture with NVIDIA includes:
- SecurityAnalystAgent: Acts as the system’s first touchpoint, ingesting raw email data and parsing it into headers, body content, and attachments. Based on the email’s contents, each element is routed to the appropriate specialist agent for deeper analysis, effectively kicking off the investigation workflow.
- HeaderAnalysisAgent: Focused on the metadata and dissects email headers to detect spoofing or forgery. It verifies SPF, DKIM, and DMARC records, tracks anomalies in the mail relay path, and identifies mismatches between sender fields and the authentication records.
- ExternalResourcesAgent: Hunts for malicious links, cross-referencing URLs against both external threat intelligence sources (like VirusTotal) and internal threat databases. Each URL is scanned and ranked by risk score. File attachments, both unprotected and password-protected, are also scanned using 3rd party vendors to detect malware. Often, phishing emails contain password-protected files with the password casually embedded in the email’s body. This is easily detected by a human, but requires a lot of engineering effort to extract and detect. Nowadays, thanks to LLMs, we can easily identify passwords and perform proper scanning on password-protected assets.
- ScreenshotAnalyzerAgent: The email is rendered in a sandboxed environment, and then a screenshot is taken. We then use VLMs with image analysis support to identify any potential signs of a phishing email, such as broken logos, mixed font colors, and other indicators that a trained expert could only identify in the past. Nowadays, we can achieve that using out-of-the-box foundational models or models fine-tuned for phishing email data.
- ContentClassifierAgent: Uses a LLM to analyze the email’s tone, urgency, and intent. It flags psychological manipulation cues (like fake deadlines or impersonation), often hidden from traditional filters.
Example prompt snippet:
# Social Engineering Tactics:
– Urgency and time pressure (“Act now!”, “Limited time!”, “Expires today!”)
– Authority impersonation (pretending to be from banks, government, IT support, executives)
– Fear-based manipulation (account suspension, security breach, legal action threats)
– Emotional appeals (charity scams, personal emergencies, romantic deception)
– Curiosity exploitation (mysterious packages, secret information, exclusive offers)
– Trust exploitation (fake testimonials, false credentials, friendship pretense)
# Content Analysis:
– Requests for sensitive information (passwords, SSN, account details, verification codes)
– Suspicious links or attachments mentioned in the text
– Generic greetings vs. personalized communication
– Grammar, spelling, and language inconsistencies
– Mismatched branding or logos mentioned
– Unusual payment methods (gift cards, cryptocurrency, wire transfers)
# Behavioral Indicators:
– Instructions to bypass security measures
– Requests to keep communication secret
– Pressure to act without verification
– Unusual communication channels suggested
– Requests to download software or click links
– Inconsistent sender identity or story
# Technical Red Flags:
– Shortened URLs or suspicious domain names mentioned
– Requests to disable security software
– Instructions to enable macros or run executables
– Phishing kit indicators (template text, placeholder content)
– URL analysis for typosquatting or suspicious domains
# Language Pattern Analysis:
– Inconsistent tone or writing style
– Translation artifacts suggesting non-native speakers
– Copy-paste indicators from legitimate sources
– Formatting anomalies or HTML artifacts
– Mixed font styles or encoding issues
- VerdictAgent (The SOC Lead): Compiles all findings, weighs conflicting signals, and delivers a contextual risk score with a clear explanation. Acting as the decision-making layer, it mimics a senior analyst’s judgment to determine whether the email poses a threat. In addition to a verdict, it also provides the reasoning behind the decision and the investigation.
This sophisticated logic requires a powerful, reliable execution engine. The NVIDIA NeMo Agent Toolkit provides:
- Framework-agnostic orchestration: Integrates existing Python libraries and agents seamlessly. Using it allows us to build multi-agent flows with ease.
- YAML-driven workflows: Uses declarative YAML files for defining agent behaviors, workflows, and model configurations and prompts, simplifying deployments.
- Built-in profiling and evaluation: Offers detailed telemetry to optimize latency, performance, and resource usage. This is extremely handy during the development phase. Using the profiling and evaluation data helps to select the right model for the job, either a cloud-hosted one provided by one of the vendors or a locally running one powered by the NVIDIA NIM containers.
Complementing the toolkit, NVIDIA NIM delivers high-performance, containerized inference endpoints for model flexibility. Using NIM containers allows easy, single-click model swaps without infrastructure complications.
Orchestration in Practice with config.yaml
At the center of this phishing defense system is a declarative NeMo Agent Toolkit configuration file that defines every component of the multi-agent architecture within a single YAML file. This makes the system highly extensible, developer-friendly, and production-ready.
The NVIDIA NeMo Agent Toolkit enables this orchestration by configuring each tool, model, prompt, and agent as composable, callable components. Here’s a conceptual breakdown of how it all comes together.
1. Tools and Agents Defined as Functions
The YAML configuration begins by defining individual tools: custom Python functions, API lookups, and Retrieval-Augmented Generation (RAG) pipelines. These are then mapped to specialized AI agents like HeaderAnalysisAgent and URLScannerAgent. Each agent uses a specific LLM and toolset to complete its role within the overall phishing analysis.
2. LLMs Powered by NVIDIA NIM
Two distinct LLMs are served via NVIDIA NIM containers: one for general reasoning and ReAct-style logic, and another fine-tuned for phishing content classification. With just a few lines of config, you can swap out or upgrade models.
3. VerdictAgent as the Final Judge
The workflow culminates in the VerdictAgent, implemented as an agent that reviews the results of the investigator agents to complete the analysis. It generates a verdict based on the assessment results generated by the investigative agents, summarizing their conclusions and calculating a risk score based on their findings.
Here’s what makes this approach powerful:
- Modularity: Each agent is an independent component, making updates and testing seamless.
- Flexibility: Swapping models, tuning prompts, and adding or removing tool logic are a matter of changing the agent’s configuration in the configuration YAML.
- Explainability: The VerdictAgent aggregates signals from diverse sources, enabling human-readable reports and confidence scoring.
Spear-Phishing Detection in Action
By utilizing NVIDIA’s rich LLM ecosystem, Torq delivered a system uniquely capable of identifying high-risk spear-phishing campaigns targeting executives. These attacks typically include password-protected malware attachments with credentials shared in the email body. While traditional tools overlook this context, the AI agents in the system understand intent and behavior.
The results speak for themselves: LLM-based security systems dramatically outperform traditional rule-based engines, reducing incident response times from hours to under ten minutes for critical threats. These systems also demonstrate superior resilience against AI-generated phishing attacks, maintaining accuracy even when sophisticated rephrasing techniques are employed — showing only a 3-4 percentage point decline compared to 5-9 points for traditional models.
Perhaps most importantly, intelligent event correlation tackles alert fatigue head-on, reducing alert volume by up to 87% while ensuring security teams can focus on genuine threats rather than managing false positives.
Real-World Impact
Leveraging Python as a unifying language, the NeMo Agent Toolkit for rapid development, Torq was able to build an agentic AI-based phishing email detection feature quickly. This effectively addresses advanced phishing tactics, including password-protected malware attachments. It understands the nuanced context within phishing emails, resulting in:
- Accelerated incident response: Agents collaboratively analyze threats, drastically reducing the mean time to respond (MTTR) up to 92% faster compared to manual investigation.
- Fewer false positives: Context-aware agents ensure precise detection, minimizing alert fatigue.
- Stronger threat correlation: Agents correlate seemingly unrelated phishing attempts, uncovering hidden threat patterns and bolstering overall security posture.
- 7-15x More Effective at Catching Missed Phishing Emails: Our initial testing shows that our product is able to detect a significant number of malicious emails that have already been scanned and deemed “safe” by traditional gateways like those in Microsoft 365 or Google Workspace.
Building AI Security That Learns and Scales
Phishing threats continue to evolve, demanding smarter, adaptive solutions. The collaboration between NVIDIA and Torq shows how multi-agent AI systems can redefine phishing defense.
Customers can plug our advanced phishing detection feature directly into their Torq workflows; it is available as a Step in their Builder’s Toolbox. This feature enables real-time analysis of emails, attachments, URLs, and headers using multiple specialized AI agents, delivering highly accurate threat detection without manual tuning. By embedding this capability into automated workflows, security teams can rapidly identify and mitigate phishing attempts while continuously adapting to new threat patterns.
See how AI-driven security operations transform detection, response, and scale across your entire environment.