Contents
Get a Personalized Demo
See how Torq harnesses AI in your SOC to detect, prioritize, and respond to threats faster.
SOC teams have been on the hunt for ages for a way to automate manual, repetitive tasks and workflows. SOAR was intended to streamline security workflows — however, legacy SOAR tools have long since been called “obsolete” by Gartner due to their reliance on excessive customization and scripting.
That’s why SecOps teams are abandoning legacy SOAR in favor of no-code security automation solutions, particularly the new gold standard for today’s modern SOC operations: AI-driven Hyperautomation and the autonomous SOC.
Let’s break down how these security automation software solutions compare.
What are SOAR Tools?
Legacy Security Orchestration, Automation, and Response (SOAR) tools were designed to help security teams centralize and automate security operations through playbooks. SOARs were developed to solve many of the problems associated with security incident and event management (SIEM) platforms, the old standby tool for security engineers.
However, SOAR tools suffer from limitations such as rigid architecture and a heavy reliance on custom scripting and coding, hindering their ability to integrate with the modern security stack and adapt to evolving security needs.
What is No-Code Security Automation?
No-code security automation refers to tools that anyone — not just security engineers with coding expertise — can use to build and deploy automated security workflows that define risks, enforce security rules, and remediate threats automatically.
By using a codeless approach to security (think drag-and-drop visual interfaces and pre-built templates), no-code security automation tools enable SOC teams to manage risks without depending on specialized, expensive scripting skillsets. This approach empowers security analysts to move quickly: they can launch automated workflows and enforce policy at scale with simple toggles and low-code overrides for edge cases.
SOAR Tools vs. No-Code Security Automation
SOAR tools and no-code security automation platforms overlap in many of their objectives, including:
- Automation: Both solutions enable automated risk identification and management.
- Efficiency: SOAR and no-code security tools are designed to help organizations manage risks more effectively.
- Going beyond threat detection: Unlike SIEMs, SOARs and no-code security frameworks don’t just detect risks and send alerts, they can also be used to manage risk response.
- Threat intelligence: Both categories of tools draw on threat intelligence data to help identify and assess the newest types of security risks.
But the similarities stop there. In general, no-code security automation delivers additional features and benefits that SOAR tools lack, including:
- Accessibility: No-code security automation frameworks are easy enough for anyone to use, regardless of coding experience. They allow all stakeholders, not just cybersecurity experts, to define and enforce security requirements within the systems they manage.
- Automated response: In addition to making it easy to configure security rules, no-code security automation frameworks can automate incident response based on those rules. Traditional SOARs provide some automated response features, but they focus more on orchestrating threat response actions by cybersecurity professionals than on actually remediating the threat themselves.
- Configuration security posture management: Traditional SOAR tools usually identify active risks within environments, rather than assessing configurations to find flaws that could enable a breach. No-code security automation tools do both, which means they can address domains like cloud security posture management (CSPM) in addition to runtime security — and these automation workflows span both prevention and response.
- Simple integrations: While deploying a SOAR in various environments and with many types of systems is possible, doing so usually requires extensive configuration and customizations. In contrast, no-code security automation platforms are designed to start working out of the box, across any mainstream environment, with minimal configuration tweaks.
What Sets No-Code Security Automation Apart
No-code security automation allows anyone — regardless of coding skill — to build, deploy, and manage automated security workflows. Using drag-and-drop visual editors, pre-built templates, and plug-and-play integrations, these platforms make it possible to:
- Detect and respond to threats automatically
- Enforce security policies across the environment
- Remediate incidents in real time
- Manage risk without relying on hard-to-hire scripting experts
Compared to SOAR and even low-code automation, no-code security automation is:
- Faster to deploy: No months-long setup or custom scripting backlog.
- More accessible: Usable by security analysts, IT admins, and even DevOps teams.
- Broader in scope: Covers threat detection, configuration hardening, and policy enforcement.
- Easier to integrate: Connects to your existing stack with minimal configuration.
- End-to-end: Designed for true, end-to-end automation across detection, response, and recovery.
Traditional SOAR still delivers value in orchestration, but no-code platforms remove the barriers that made SOAR slow, rigid, and costly.
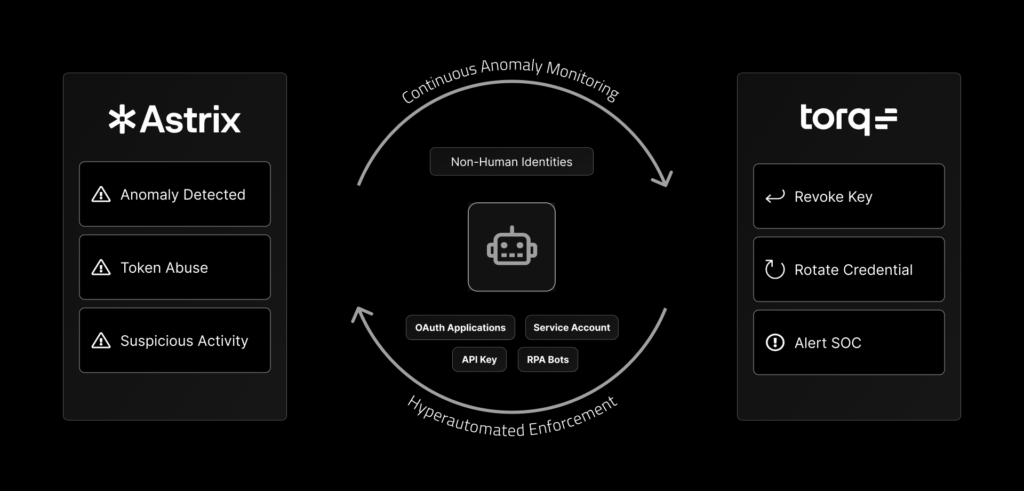
How Torq’s AI-Powered Hyperautomation Replaces Legacy SOAR
Building upon the accessibility and flexibility of no-code automation, the modern SOC now demands a more intelligent and scalable approach: AI-driven Hyperautomation. Torq’s autonomous SecOps platform represents a fundamental leap in the evolution of security automation for modern SOC capabilities.
With security Hyperautomation, SOCs can:
- Eliminate alert fatigue with autonomous triage and Tier-1 auto-remediation
- Enrich alerts in real time with threat intelligence, asset context, and business impact scoring
- Automate investigation and containment across EDR, SIEM, email, identity, and cloud tools
- Scale without friction using agentless architecture and 300+ pre-built integrations
- Empower every skill level with no-code, low-code, and full-code workflow building
Security Hyperautomation delivers significant advancements over SOAR and basic no-code automation. In addition to limitless integrations and cloud-based scalability, Torq Hyperautomation™ offers powerful case management capabilities that eliminate alert fatigue by automating Tier-1 threat remediation and intelligently prioritizing complex cases. And now, Torq’s agentic AI and Multi-Agent System is revolutionizing SOC efficiency through autonomous triage, investigation, and response.
Thanks to no-code, low-code, and AI-generated workflow building, Torq empowers your SOC team to build and manage automations without extensive coding knowledge — while also offering full-code capabilities for those on your team who want granular control.
By automating complex workflows in minutes and leveraging intelligent decision-making, the AI-powered SOC can help organizations move beyond reactive security to become more efficient and resilient in the face of talent shortages and ever-evolving threats.
Choosing the Right Path: What Today’s SOCs Prefer
Market momentum is clear:
- Gartner, IDC, and buyers alike have signaled the decline of SOAR in favor of flexible, cloud-native security automation platforms.
- SOC leaders prefer lower cost, faster onboarding, and the ability to scale automation without adding headcount.
- Modern platforms like Torq let security, IT, and DevOps work from a single automation layer, removing silos and speeding MTTR.
Legacy SOAR simply can’t match the speed, scalability, and adaptability required for today’s high-volume, multi-tool security environments.

No-Code Security Automation in Action: Real-World Use Cases
The advantages of no-code security automation become clear when you see how organizations have transformed their operations. Here’s how leading companies replaced rigid, code-heavy approaches with accessible, scalable automation.
Use Case 1: Scaling a Lean Team Through Automation
Online travel platform Agoda faced a pivotal challenge: modernizing security operations while operating with a small, geographically distributed team. Their existing automation solution required extensive manual connector development and lacked native integrations with their growing security toolset. The CISO’s vision was to build a lean, highly technical team that could scale through automation rather than headcount — but manual processes consumed analyst time across multiple time zones.
Agoda selected Torq Hyperautomation after a proof of concept showcasing the platform’s ease of use, breadth of integrations, and hands-on support. The no-code/low-code interface made automation accessible to security engineers without advanced programming skills, while still allowing power users to push the platform’s capabilities further. Torq’s out-of-the-box integrations eliminated the need for custom connectors.
The Results:
- End-to-end phishing automation: Employees receive verdicts in minutes with zero analyst intervention on a 24×7 basis
- Password resets reduced from hours to minutes with full automation of monthly requests
- App deployment requests cut from one day to 10 minutes—half now handled entirely through Torq workflows
- Cloud security SLOs improved by 47% through orchestrated Wiz findings and automated remediation
- Incident reports generated in 30–40 minutes instead of 6–7 hours using Torq + ChatGPT
- Critical findings reach engineering teams in near real-time instead of two weeks
Use Case 2: Rapid Workflow Deployment in Financial Services
A top-30 U.S. bank faced an urgent, compliance-driven requirement: automate detection and response to fraud alerts in Zelle, their customer-facing payment service, which had been suspended by the SEC due to a surge in fraudulent activity. Like many SOCs dealing with a cybersecurity talent shortage, they had too few skilled analysts and too many alerts, leading to inconsistent, reactive incident response. Their phishing response process was especially time-consuming, requiring analysts to jump between windows to track down information from URLScan, Recorded Future, VirusTotal, and other tools.
The bank bypassed legacy SOAR solutions, finding Torq’s no-code/low-code capabilities and minimal learning curve enabled their internal security team to quickly become proficient in building complex workflows. Torq’s onboarding program led to a pivotal “aha” moment when developers realized how quickly and effectively they could build workflows, empowering the internal team to take full control without incurring costly professional services.
The Results:
- 100+ workflows launched in just 3 months by the internal team
- Zelle services reinstated after Torq automated end-to-end fraud detection and account lockdown
- MTTI reduced from hours to minutes across the security stack
- Phishing response fully automated: scanning, enrichment, threat intelligence correlation, and user classification
- Malware/ransomware recovery accelerated through automated quarantine, hash blocking, and endpoint reimaging
- Expansion beyond security into IT, fraud, and GRC teams within months of deployment
See Torq in Action
The SOC has changed — your automation should too. Torq Hyperautomation combines no-code accessibility, low-code flexibility, and AI-powered autonomy to modernize security operations from the ground up.
Whether you’re replacing SOAR, extending your existing stack, or building an autonomous SOC, Torq delivers:
- Autonomous triage, enrichment, and remediation driven by automated decisioning
- Seamless integrations with your current tools and pre-built connectors
- Faster MTTR and higher productivity for your security analysts, powered by automated workflows
See how Torq Hyperautomation stacks up.
FAQs
No-code security automation refers to platforms that allow anyone — regardless of coding expertise — to build, deploy, and manage automated security workflows using visual interfaces, drag-and-drop editors, and pre-built templates. Unlike traditional SOAR tools that require custom scripting and developer involvement, no-code platforms enable security analysts, IT admins, and SOC teams to create automations for threat detection, policy enforcement, and incident response without specialized programming skills.
While both solutions automate security workflows, they differ significantly in accessibility, deployment speed, and maintenance burden. SOAR tools require extensive custom scripting, developer expertise, and months-long implementations. No-code security automation platforms offer drag-and-drop interfaces, pre-built integrations, and out-of-the-box functionality that enables deployment in days. Valvoline‘s experience illustrates this: a Rapid7 integration their legacy SOAR couldn’t complete after hundreds of developer hours was running in under a week with Torq’s no-code approach.
Organizations are abandoning legacy SOAR because it failed to deliver on its automation promises. Key issues include: rigid architectures that can’t adapt to evolving threats, heavy reliance on custom scripting that creates developer bottlenecks, expensive maintenance and configuration requirements, limited accessibility (only specialists can build workflows), and slow deployment timelines. Gartner has labeled legacy SOAR “obsolete,” and organizations like Bloomreach spent three years trying to push SOAR adoption before finding success with no-code alternatives.
Yes, this is the core advantage of no-code platforms. Security analysts, IT administrators, and even DevOps teams can build and maintain automated workflows without coding expertise. Bloomreach specifically chose Torq because they “wanted everybody on the team, including junior analysts, to be able to build automations — not just developers.” Their team members became productive through hands-on experience alone, without completing formal training.
No-code security automation platforms can be deployed in days rather than the weeks or months required by legacy SOAR. Valvoline saw operational ROI within 48 hours of deploying Torq. HWG Sababa replaced years of hand-coded automations in just weeks. This speed comes from pre-built integrations, visual workflow builders, and agentless architectures that eliminate complex configuration requirements.
No-code security automation can handle the full detection-to-response lifecycle: alert triage and enrichment, threat intelligence correlation, phishing response and email security, endpoint detection and response actions, identity and access management workflows, cloud security posture management, incident containment and remediation, case management and documentation, compliance reporting, and fraud detection.
Based on real customer outcomes:
- 100+ workflows launched in 3 months (Major Regional Bank)
- End-to-end phishing automation with zero analyst intervention (Agoda)
- Incident reports reduced from hours to 30–40 minutes (Agoda)
- 6–7 analyst hours saved daily (Valvoline)
- MTTI reduced from hours to minutes (Major Regional Bank)
- Operational ROI within 48 hours (Valvoline)
- Enterprise-wide automation adoption including IT, fraud, and GRC teams (Major Regional Bank, Bloomreach)
- Most organizations see measurable time savings within the first week of deployment.
Yes, no-code platforms like Torq are well-suited for regulated industries including financial services and healthcare. A major regional bank chose Torq specifically for compliance-driven requirements: when the SEC mandated automated fraud detection before reinstating their Zelle payment service, Torq automated the end-to-end process of detecting fraud alerts and locking down accounts.
The platform also automates CRM updates so customer service representatives have immediate context when speaking with affected customers. Torq’s audit trails, case management, and documentation capabilities support compliance frameworks including SOC 2, ISO 27001, NIST, HIPAA, and SEC requirements.