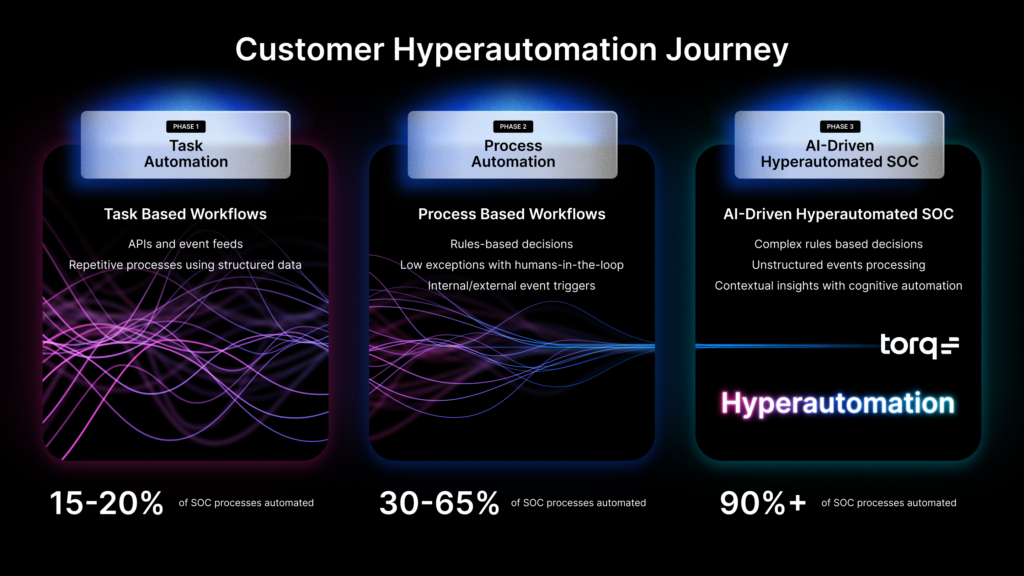
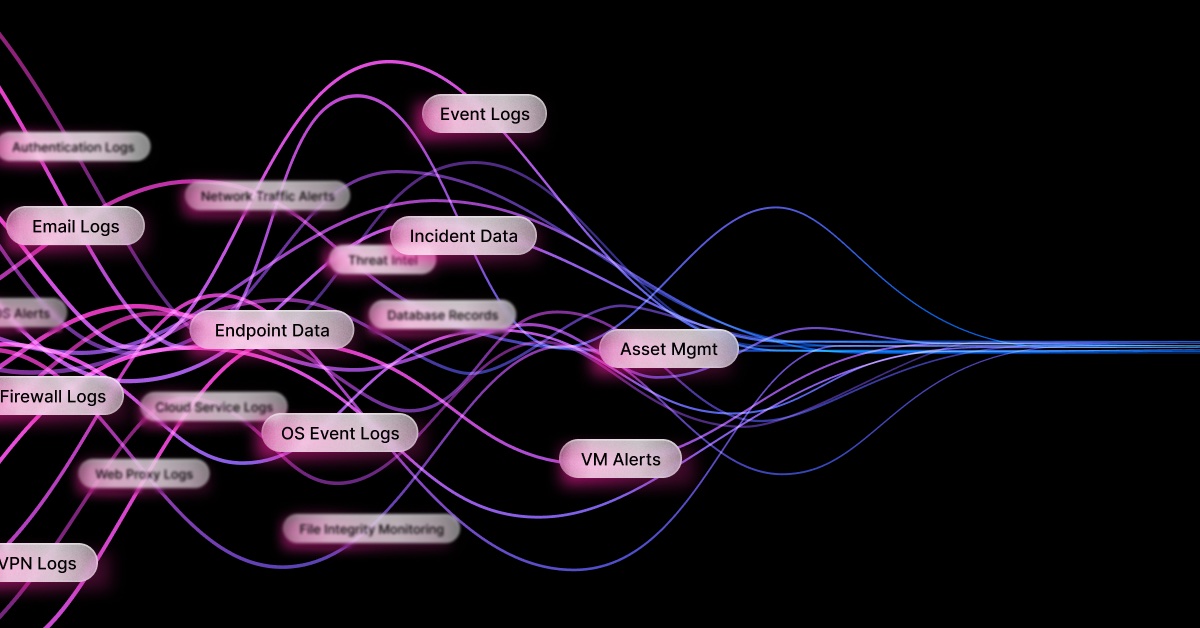
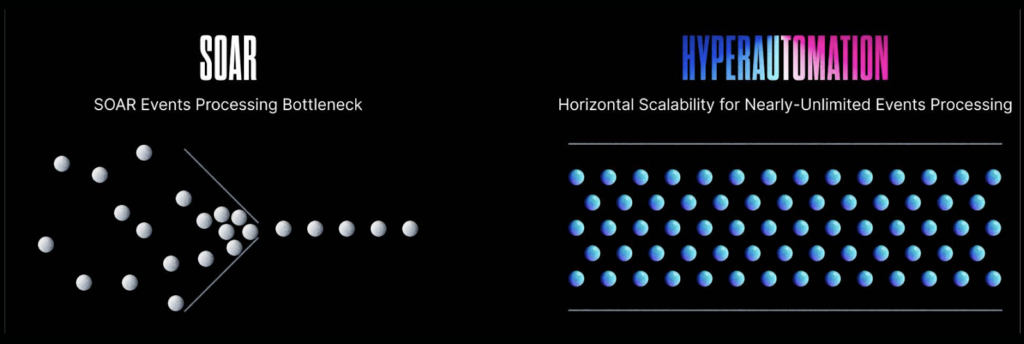
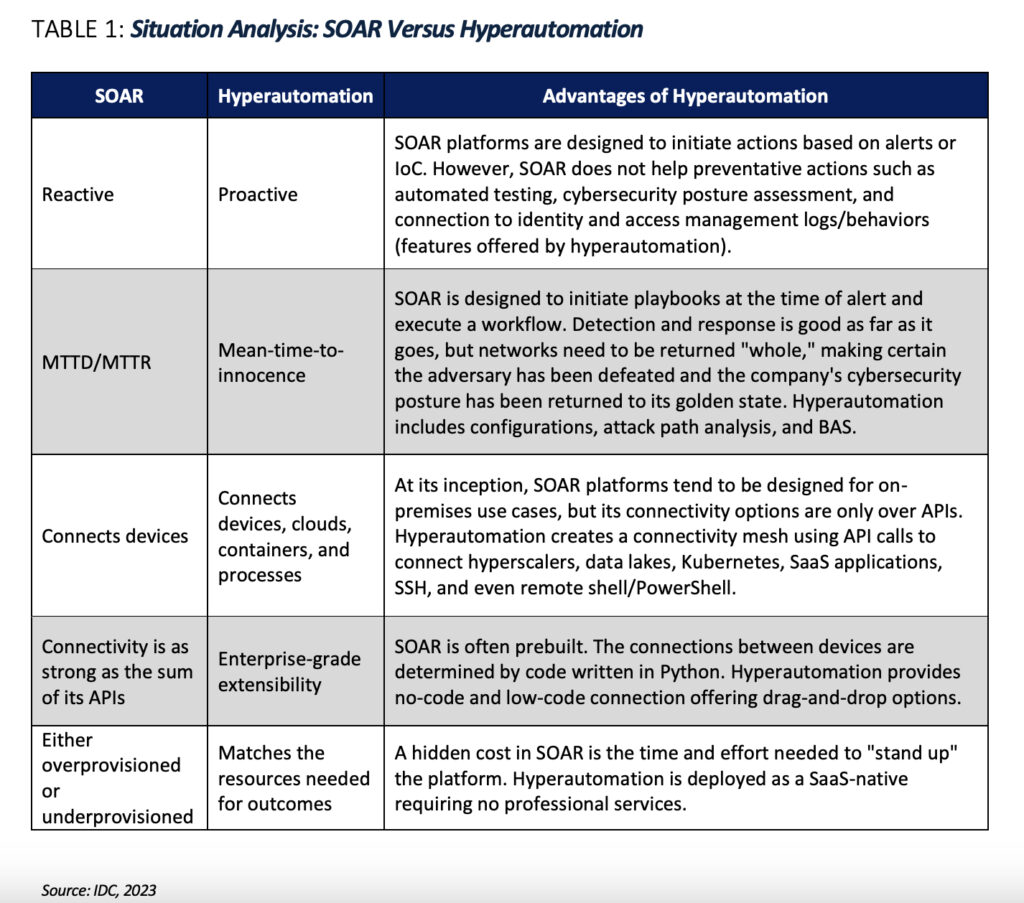
No-code support should be just that – the ability to build automations without coding.
At Torq, we continually work to extend the out-of-the-box no-code automation features available in our platform. That’s just what we’re doing with Step Builder, a new no-code feature that is now in GA.
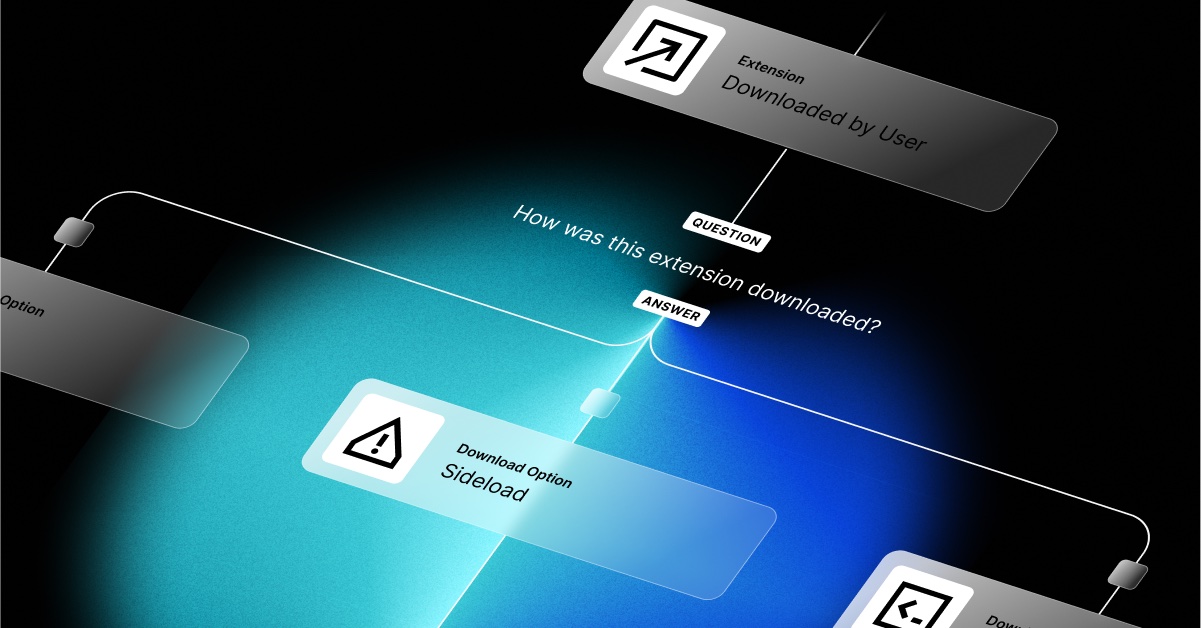
Step Builder gives Torq users the ability to quickly and easily create custom content without the need to code, making your options for integration limitless. We already offer several thousand pre-built steps from more than 250 vendors, and Step Builder infinitely expands your options with a way to create a new, custom step with no code required. When we say “limitless integrations” we mean it – you can use automation for whatever you want.
And Step Builder features a dynamic preview of the step you’re creating – so you can see how it will look as you build it. You can also do a test run directly from Step Builder without having to return to the workflow.
Step Builder introduces new simplicity and efficiency to Torq’s already expansive no-code user experience, going well beyond what’s offered through legacy SOAR. There’s no need to code at all to extend the system and you can virtually create new steps or modify existing ones.
It’s also functionality not offered by other no-code automation solutions. With Step Builder, you can create high-level no-code steps that you can use without the need to understand the underlying REST APIs or care about technicalities, while other no-code systems allow for the creation of custom REST API/Webhook call steps, but you still have to take care of the additional details.
Step Builder is available to use now in the Torq Hyperautomation Platform.
AI Completions for Advanced Steps
Along with Step Builder, we’ve also released a new feature that gives automators of all skill levels the ability to bring scripting, querying, and coding capabilities into a no-code workflow by using Generative AI completion.
AI Completions for Advanced Steps is now available in the Workflow Designer. It simplifies and streamlines extensibility and the creation of advanced scenarios in Torq workflows. Specifically for cloud administrators using Torq in AWS, Azure, Google Cloud, and other platforms, this brings in a familiar language of capabilities available in the often very advanced CLI interfaces these platforms offer.
It’s simple to use: when you’re in the Workflow Designer, you can use the step name (description) as an input for Generative AI to generate that step’s advanced configuration and complete the step, whether that’s command arguments, scripts, queries, etc. Now in GA, the feature supports Python, Bash, PowerShell, JQ, RegEx, AWS CLI, Azure CLI, and GCP CLI.
This eliminates the need to bounce between tools and windows to build scripts – you can do it all from within Torq.
AI Completions for Advanced Steps is a win-win – giving less technical users in-context automation options, while giving more technical users who know what they want to achieve a more streamlined experience.
To see how Torq can improve your efficiency and productivity, request a demo.