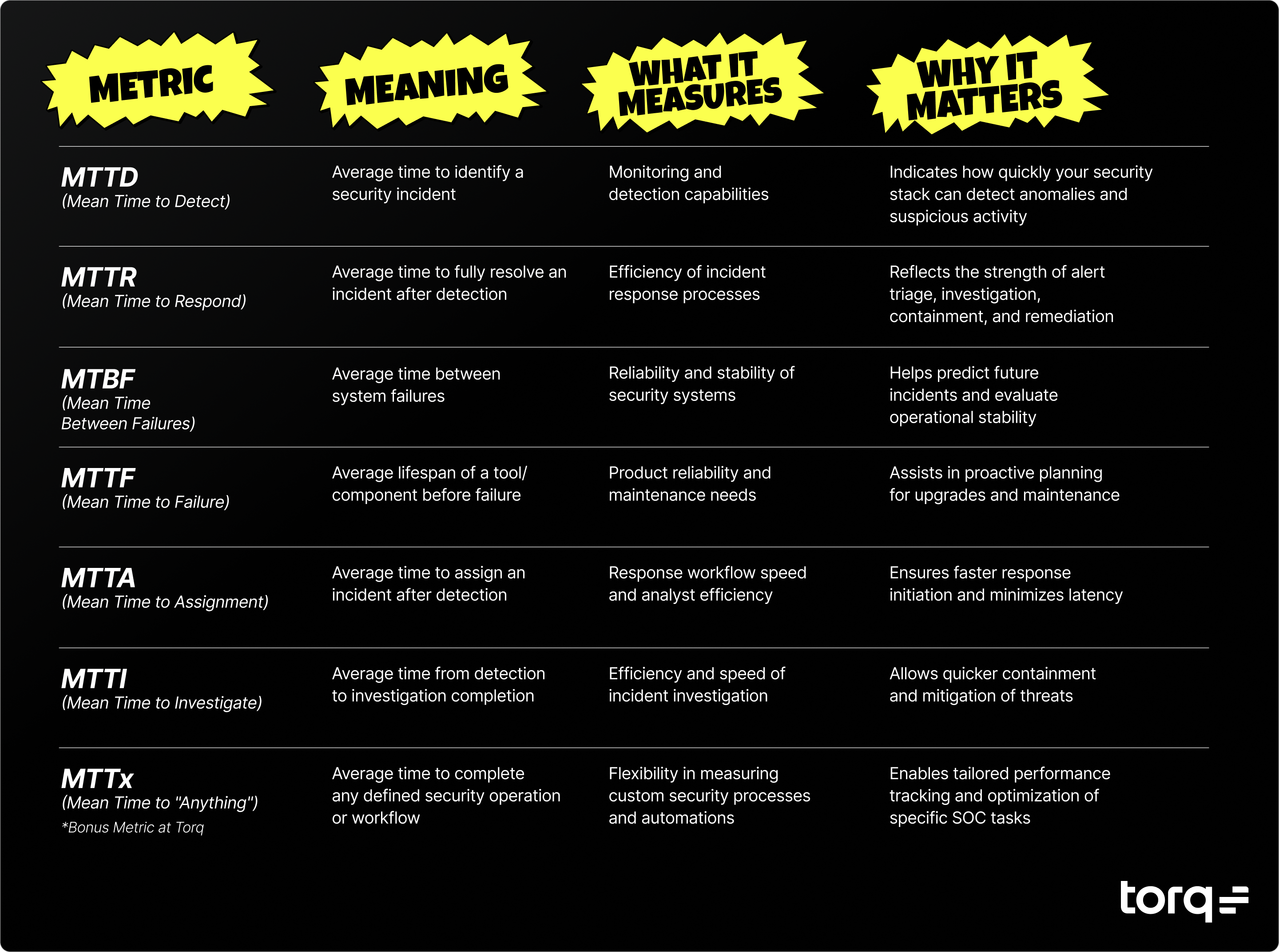
Contents
Get a Personalized Demo
See how Torq harnesses AI in your SOC to detect, prioritize, and respond to threats faster.
The biggest cybersecurity threats often arrive quietly, disguised as something users trust — and they go straight for the top. Whaling phishing attacks are precision strikes crafted to target senior executives, exploiting their authority to steal money or critical data.
Below, we share strategies to recognize and prevent whaling phishing attacks before they reach your leadership team.
Whaling Phishing Attacks Explained
Whaling Phishing Attacks
Whaling is a highly sophisticated and targeted form of phishing that zeroes in on high-profile executives, like the CEO, CFO, or other senior leaders. While a standard phishing attack might try to trick an unsuspecting employee into clicking a malicious link, a whaling attack uses carefully crafted emails that are made to look like they’re from a trusted source, such as a colleague or a vendor.
What makes whaling unique is the level of detail and personalization used to deceive recipients. Attackers research company structure, executive behavior, and industry-specific language to make their fraudulent messages convincing. Their goal is to request sensitive data transfers or financial transactions, or steal confidential information — all under the authority of the executive they’re impersonating.
The impact of a single successful whaling attack can be catastrophic. The FBI’s Internet Crime Complaint Center (IC3) reported that business email compromise (BEC) and email account compromise (EAC) scams, which include whaling, resulted in over $2.7 billion in losses in 2022 alone. In one infamous case, a company lost over $46 million to a whaling scam over a period of several years. This isn’t a small-time email scam — it’s a high-stakes, high-reward scheme that can sink a company.
How to Identify Whaling Phishing Attacks: 4 Warning Signs
Whaling emails are often subtle, but there are clear red flags that security teams and employees can watch for. Recognizing these warning signs is the first step in neutralizing an attack before it succeeds.
Social Engineering
Attackers carefully research the organization’s hierarchy, ongoing projects, and executive routines to craft messages that feel authentic. These emails may reference real initiatives, use company jargon, or mimic internal communication styles to build trust and lower suspicion.
Impersonating Company Executives
Attackers pose as senior leaders like CEOs, CFOs, or board members. By spoofing or using lookalike email addresses, attackers exploit authority and urgency, making employees more likely to comply without question.
Fake “Urgent” Messages from Fake Email Addresses
Many whaling attempts use urgency to pressure quick decisions. Subject lines such as “Immediate Action Required” or “Confidential Transaction Approval Needed” create stress and encourage recipients to move quickly without verifying the request, increasing the chance of a costly mistake.
Sending Strange or Unidentified URLs
Links included in these emails may look legitimate at first glance, but redirect to malicious sites or credential-harvesting pages. Subtle misspellings in domain names (e.g., micros0ft.com instead of microsoft.com) and unfamiliar file attachments are clear indicators of a potential attack.
6 Ways to Prevent Whaling Phishing Attacks
1. Employee Training and Awareness
Executives and their support staff must undergo specialized phishing awareness training, including signs of whaling phishing attacks. Teach them to spot common tactics, validate requests, and report suspicious activity.
2. Multi-Factor Authentication (MFA)
Enforce MFA across all accounts, particularly executive-level accounts. Even if credentials are stolen, MFA makes it much harder for attackers to gain access.
3. Advanced Email Filtering
Use email security tools that scan for domain spoofing, suspicious metadata, and malicious attachments before they reach inboxes.
4. Anti-Phishing Software
Deploy software that uses behavioral analytics to detect anomalies in communication patterns — especially important for high-risk roles like finance and legal.
5. Real-Time Threat Intelligence
Staying ahead of attackers requires live intelligence. By integrating global threat feeds, organizations can block known malicious domains and adapt to emerging attack patterns instantly.
6. Security Automation
Manual detection and response are too slow for modern whaling threats. Security automation ensures that suspicious emails are quarantined, alerts are prioritized, and responses are orchestrated without human delay.
Why Threat Intelligence and Automation Are Critical
Manual phishing response is a losing battle. Analysts burn hours pivoting between tools, validating IOCs, and remediating inboxes — time attackers exploit. Torq Hyperautomation eliminates that grind by automatically enriching alerts with threat intelligence integrations such as VirtusTotal to determine if URLs, attachments, and other indicators are malicious. This provides the context for faster, more informed decisions and helps quickly weed out false positives before a security case is even created.
With prebuilt workflows, phishing alerts can be automatically triaged, validated, and remediated in minutes instead of hours, slashing noise and reducing human error.
At Lennar, one of the largest U.S. homebuilders, Torq cut phishing resolution time from hours to minutes by automating investigation and remediation, freeing analysts to focus on more complex investigations.
How Hyperautomation Powers Your Defense and “Squishes” Phishers
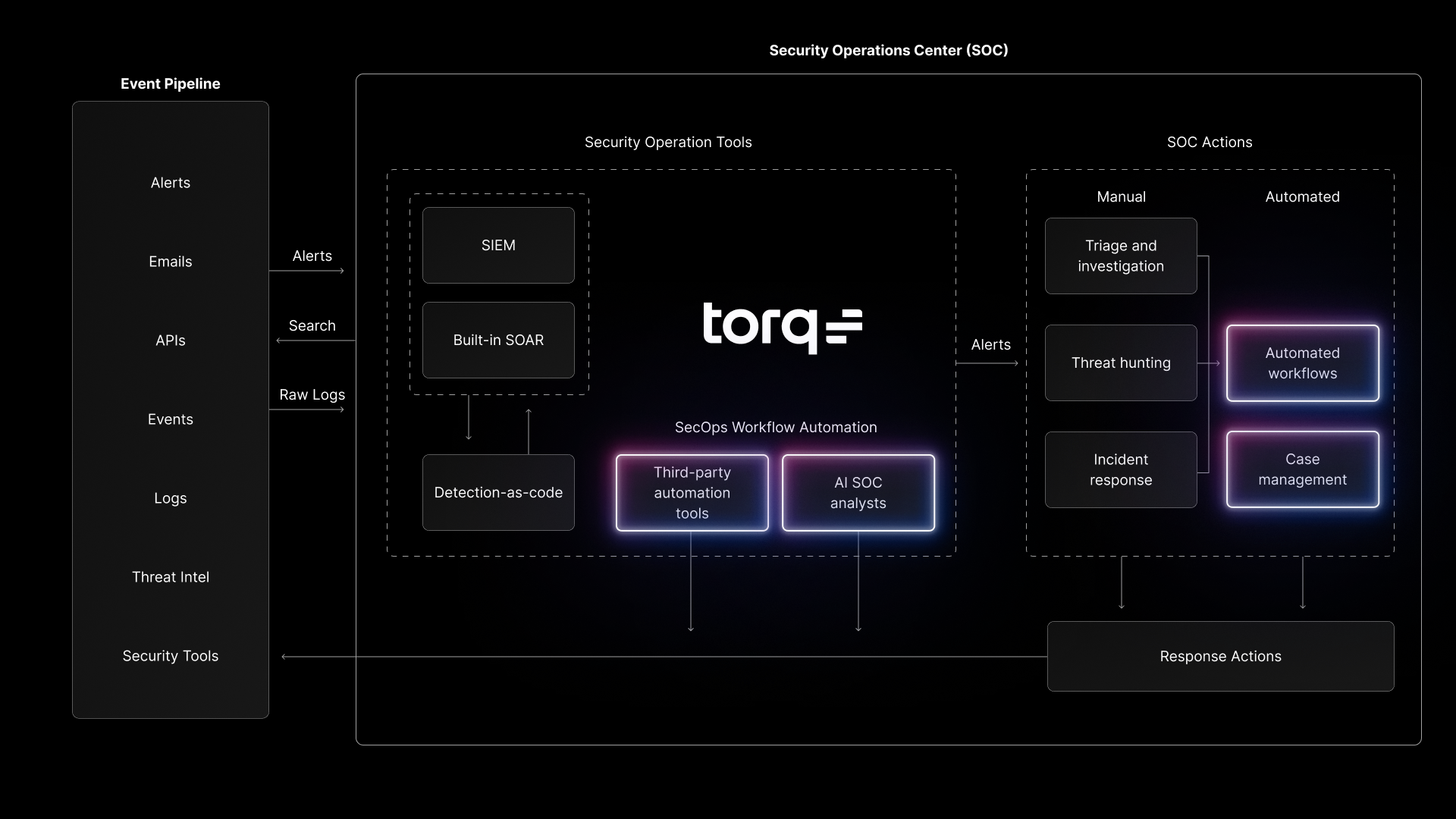
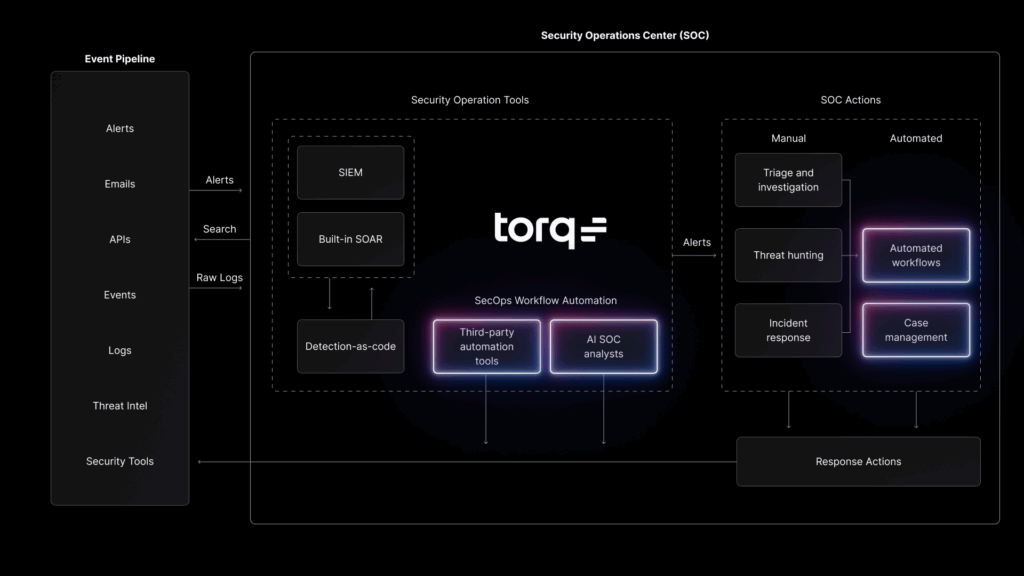
Torq’s Hyperautomation platform empowers security teams to build end-to-end phishing defenses without adding complexity. It integrates across your entire security stack — email gateways, identity platforms, EDRs, SIEMs, and more — to detect, investigate, and neutralize phishing attempts at machine speed.
When a phishing alert is triggered — say, from Microsoft 365 — Torq instantly takes over the triage process. It automatically extracts URLs, attachments, and headers in parallel, then validates them against multiple threat intelligence feeds like VirusTotal. This weeds out false positives and confirms true threats within seconds. All artifacts are consolidated into a structured dataset, which Torq uses to automatically create or escalate a case. From there, auto-remediation workflows — such as blocking senders, quarantining endpoints, or resetting credentials — can be launched without analyst intervention.
Torq Hyperautomation™ changes the game by:
- Automating phishing and whaling triage. Torq instantly extracts IOCs (URLs, hashes, headers), checks them against threat intel, and validates alerts without analyst intervention.
- Orchestrating remediation. Auto-remediation workflows block senders, reset credentials, quarantine endpoints, and remove malicious emails from inboxes automatically.
- Empowering end users. Chatbot integrations in Slack, Teams, and email give employees a one-click way to self-report phishing, while automation handles the rest.
By automating repetitive workflows and augmenting analysts with agentic AI, Torq helps organizations detect, prioritize, and respond to phishing scams and whaling attacks faster than attackers can act. The result: reduced human error, stronger executive protection, and maximized SOC efficiency.
Winning the Phishing War
Generative AI has made phishing faster, cheaper, and harder to detect — meaning that phishing and whaling attacks will only grow more sophisticated, more frequent, and more damaging. Relying on human vigilance and manual triage won’t be enough.
The only sustainable path forward is automation: uniting threat intelligence, AI-driven detection, and orchestrated response into one seamless defense layer. By eliminating manual bottlenecks and supercharging SOC efficiency, Torq ensures that phishing — even whaling-level attacks — never has the chance to sink your business.
Learn the keys to building a more efficient SOC, straight from Torq’s Field CISO.
FAQs
A classic example of whaling is when an attacker impersonates a CEO or CFO to trick an employee into authorizing a wire transfer. In one real-world case, attackers posed as executives and convinced employees to transfer $46.7 million to fraudulent overseas accounts. This shows how whaling phishing attacks exploit executive authority to carry out high-value fraud.
The three most common types of phishing attacks are:
- Standard Phishing Attacks – Bulk, generic emails sent to many users in hopes of tricking someone into clicking a malicious link or opening an infected file.
- Spear Phishing Attacks – Highly targeted phishing attacks that use personal or organizational details to tailor the message to a specific individual or small group.
- Whaling Phishing Attacks – A specialized form of spear phishing aimed at high-profile executives, such as CEOs or CFOs, often involving financial fraud or sensitive data theft.
In cybersecurity, “whaling” refers to attackers targeting “the big fish” — senior leaders or executives within an organization. The goal is to exploit their authority and access to approve high-value financial transactions or disclose sensitive company information.
Impersonation is a tactic: attackers pretend to be someone trusted (e.g., a colleague, vendor, or executive) to trick the victim. It can be used in many types of phishing.
Whaling is a strategy: it specifically targets senior executives. Whaling almost always involves impersonation, but with a narrower and higher-value focus than general phishing.