Contents
Get a Personalized Demo
See how Torq harnesses AI in your SOC to detect, prioritize, and respond to threats faster.
Despite being around for over 30 years, phishing is a bigger problem than ever for today’s SOCs. Phishing attacks have surged by 4,151% since the emergence of ChatGPT in 2022, leaving security teams drowning in phishing alert noise.
And rather than getting better at recognizing phishing emails, humans are seemingly getting worse, in part due to the increasing phishing sophistication and customization at scale that GenAI offers. According to Verizon’s 2024 Data Breach Investigations Report, people are falling for phishing attacks at an alarming rate, taking a median of just 21 seconds to click a malicious link and another 28 seconds to enter their personal data.
Of course, part of the solution lies in educating users to recognize and report phishing. But user education only goes so far — on average, only 3% of users report phishing emails. Strong anti-phishing education may increase that number, but you’re still fighting an uphill battle if you rely on end users as your primary means of defense against phishing.
Instead, modern security teams are turning to automated phishing response. By using security automation to detect and respond to phishing attempts, security teams can stop the majority of phishing messages before they ever reach end users.
Manual Phishing Triage: A Losing Battle for SOC Teams
Manual phishing investigation and response is a relentless, high-volume drain on SOCs. When a potentially malicious email is flagged — either by a security tool or a user — the clock starts ticking.
- The analyst must first deconstruct the suspicious email: digging into email headers, verifying sender addresses, analyzing the message body for suspicious language, and identifying any potential Indicators of Compromise (IOCs), such as embedded links or file attachments.
- Each potential IOC must then be manually validated. This initiates a tedious cycle of “swivel-chair” analysis, where the analyst copies and pastes information — IP addresses, domains, file hashes, etc. — out of the email and into various threat intelligence platforms and security tools. Juggling these multiple browser tabs and windows is essential to determine if an artifact is truly malicious, but each copy-paste and window hop wastes time while the risk of human error increases.
- And this is all before remediation even starts. Once the threat is confirmed, the analyst must then take action to block the sender, initiate a search to delete the email from all other inboxes, and respond to the user who reported it.
This monotonous, repetitive process is not just slow — it’s dangerously error-prone. A single missed detail or misinterpretation can be the difference between a blocked threat and a full-blown incident.
Manual phishing triage and response workflows can take tens of minutes to over an hour for a single case. Multiply that by hundreds of daily alerts, and the challenge of keeping up becomes too big to ignore. However, with anti-phishing automation, all of the grind of phishing triage, investigation, and remediation disappears.
What is Automated Phishing Response?
Anti-phishing automation refers to technology that autonomously investigates, triages, and neutralizes suspected phishing emails. It is designed to replace the slow, repetitive, error-prone grind of manual phishing defense with a consistent machine-speed response that immediately isolates compromised inboxes, revokes access to malicious emails, blocks phishing URLs, and notifies users.
6 Hyperautomated Phishing Response Strategies and Tactics
Torq Hyperautomation™ integrates with several key partners to help organizations prevent and mitigate phishing attacks and avoid costly data breaches — which cost organizations an estimated $4.88 million in 2024. Below are six strategies for leveraging Hyperautomation to fight phishing across your entire security environment.
1. Perimeter Defense: Hardening the Email Gateway
Your first line of automated defense is securing the primary phishing entry point: the email inbox. The goal is to identify and block as many malicious emails as possible before they ever reach a user.
Torq partners with Secure Email Gateway (SEG) providers to enhance their detection accuracy and response by correlating data across leading SEG solutions like Abnormal Security, Microsoft, Proofpoint, Mimecast, and more. Torq then autonomously initiates remediation actions, such as removing malicious emails or adjusting email security controls.
Key tactics:
- Filter messages based on multiple attributes: The days are long gone when simply scanning email for strings like “Nigerian prince” guaranteed that you’d catch the phishers. Simple keyword or domain name scanning won’t cut it. Effective anti-phishing automation evaluates every email based on multiple attributes — its content, the domain from which it originated, whether it contains an attachment, the type of attachment, and so on — to build a far more informed assessment than content analysis alone can provide.
- Detonate attachments in sandboxes: For suspicious but unconfirmed email threats, automation can instantly “detonate” (i.e. download and open) attachments or links in a secure, isolated sandbox. By evaluating the content’s behavior in a safe environment, the system can detect anomalies or attack signatures that confirm the content is indeed malicious. At the same time, the original email remains quarantined from the user. Pending the results, the workflow can either safely release the back content to the user or block it definitively.
- Block sender names and domains automatically: When a phishing attempt is confirmed, automation can instantly block the sender’s name and entire domain across the organization. This prevents subsequent waves of the attack from different accounts on the same infrastructure, disrupting the phisher’s campaign.
2. Identity and Access Control: Protecting Your People
Since credentials are the primary target of most phishing attacks, proactively protecting user identities is paramount. Torq does this by analyzing cloud-based user and entity behaviors to detect anomalies that could be indicative of phishing. And if a phishing attack does occur, Torq integrates with solutions, including Okta, Active Directory, JumpCloud, OneLogin, Ping, and Wiz, to prevent account takeover and limit an attacker’s access.
Key tactic:
- Reset credentials automatically: Upon detecting a potential phishing compromise, automation should immediately trigger a security workflow to reset login credentials for impacted users. This includes logging the user out of all active sessions and forcing a password reset to instantly invalidate any stolen credentials.
3. Endpoint Security: Containing the Impact
If a malicious email makes it through and a user clicks a link or opens an attachment, the battle shifts to the endpoint (e.g. the user’s laptop or phone). Working with EDR providers like Crowdstrike, SentinelOne, Microsoft, and others, Torq can correlate endpoint data for a holistic view of a phishing attack’s scope and impact, then rapidly take action to contain and remediate any compromise on the device itself.
Key tactic:
- Scan and quarantine affected endpoints automatically: The moment a user is linked to a confirmed phishing attack, automation should trigger the EDR solution to perform an immediate scan of their devices. If malware is found, the endpoint can be automatically quarantined from the network to prevent lateral movement while the threat is removed.
4. The Human Element: Empowering Users as a Line of Defense
Your employees are both a target and a potential ally. Torq’s chatbot integrations with communication tools like Slack, Microsoft Teams, Discord, and email make it quick and easy for users to report threats, providing them with instant feedback and education, and turning users into an active part of your security posture.
Key tactics:
- Use chatbots for phishing reporting: Integrating chatbots into communication tools like Slack or Microsoft Teams gives users a simple, immediate way to report suspicious emails. These bots can then kick off automated security workflows based on the report, such as resetting passwords, revoking access, or initiating scans for malware. Chatbots can also provide educational resources and coaching to users on how to avoid phishing and improve their cybersecurity awareness.
- Triage user-reported emails automatically: When a user reports a suspected phishing email, automation takes over. It can instantly extract key indicators (URLs, file hashes, headers), analyze them against threat intelligence, and provide the user with immediate feedback, confirming if the email was malicious and has been handled, or if it was safe.
5. Data Protection & Incident Response: Minimizing the Damage
When a breach occurs from a phishing email, the strategy shifts to understanding and minimizing the damage. Automation is critical for rapidly assessing the scope and scale of data loss and ensuring compliance with regulatory requirements for notifications and reporting. Torq partners with providers like Microsoft, Crowdstrike, Varonis, and Symantec to automate these two important pieces of the phishing puzzle.
6. Continuous Improvement: Learning from Every Attack
A strong defense is one that constantly learns and adapts. Understanding the metrics after the fact can help prevent a phishing attack in the future. Torq partners with SIEM, SEG, and EDR providers to use data from past incidents to refine and improve your automated workflows and overall security posture.
Key tactic:
- Quantify improvements with automated metrics: Use automation to analyze response times, workflow effectiveness, and incident severity. By leveraging AI in the SOC to automatically categorize incidents and create cases, you can ensure critical threats receive priority and gather insights to continually harden your defenses against future attacks.
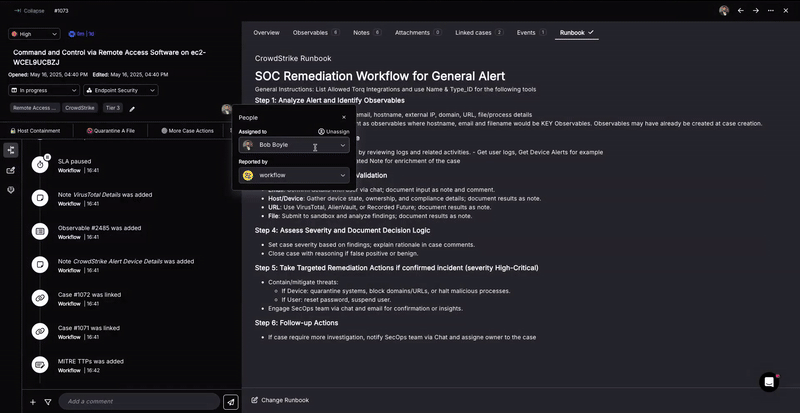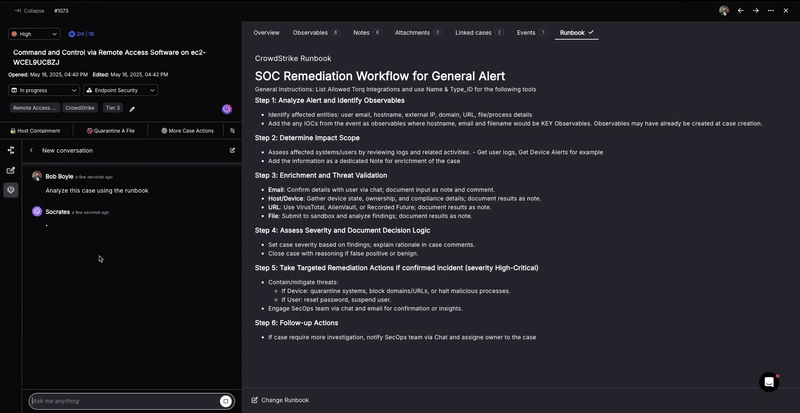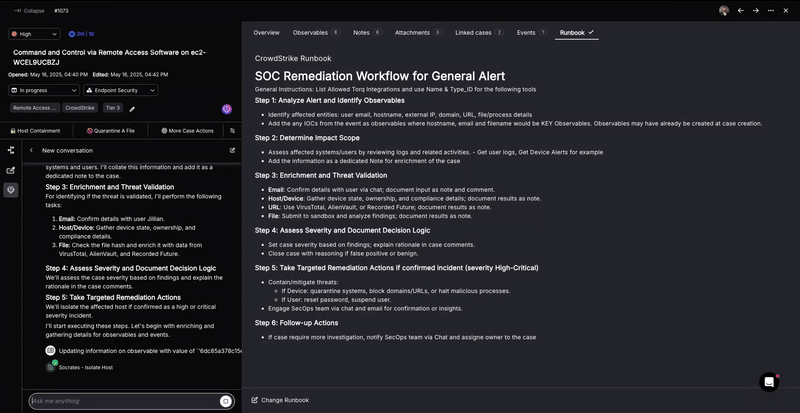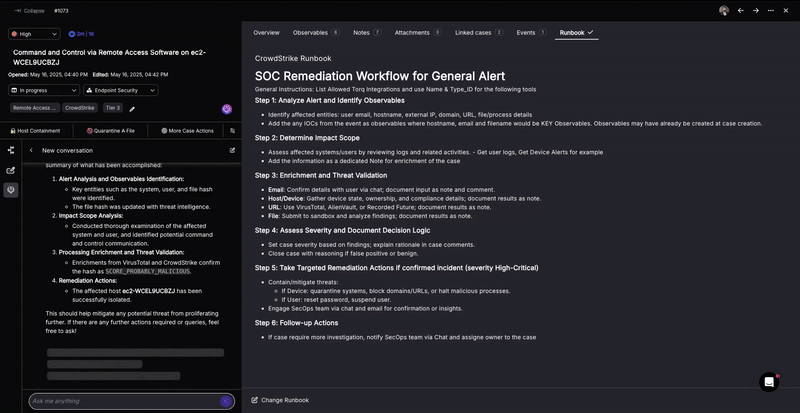
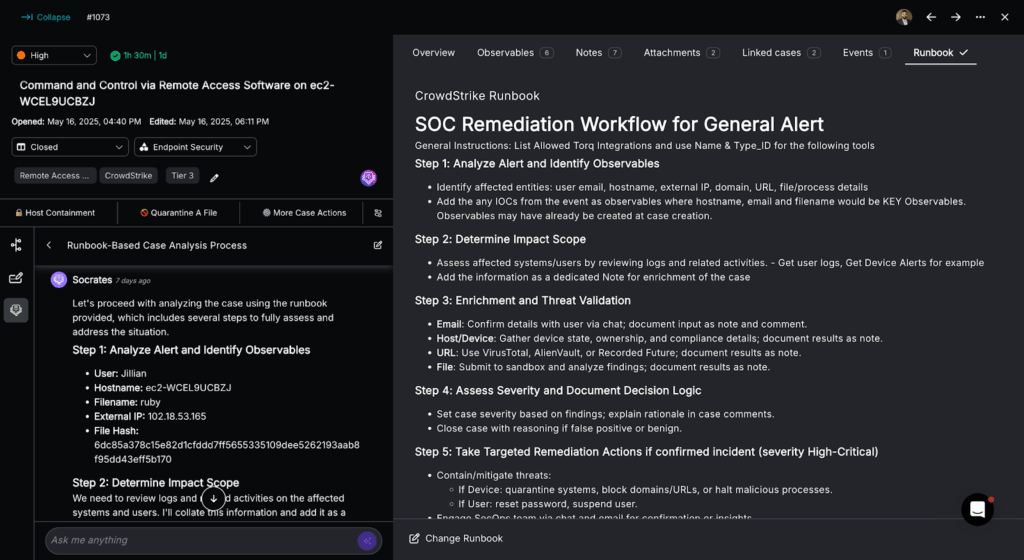
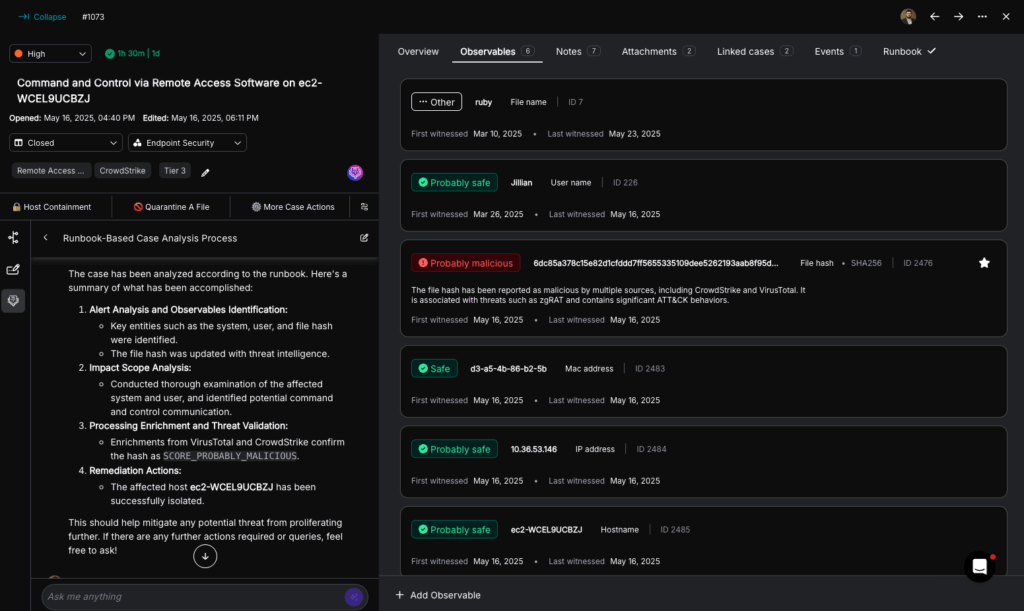
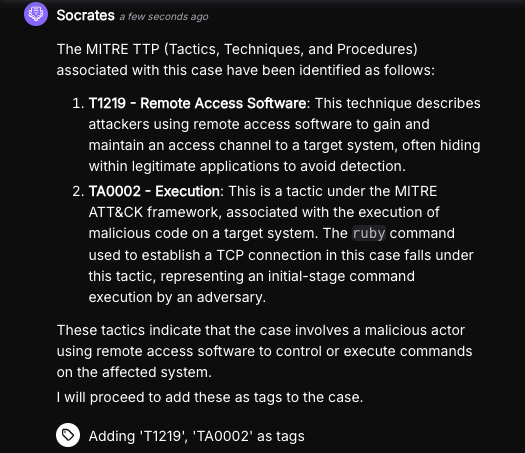
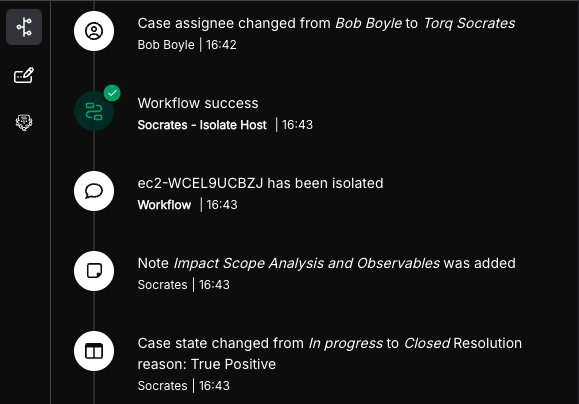
Example Automated Phishing Alert Analysis Workflow in Torq
This Torq Hyperautomation workflow automates the initial triage of a reported phishing email. It instantly extracts and aggregates key artifacts like URLs, file hashes, and headers from Outlook messages and attaches to create a structured data set for deeper analysis, following these steps:
- Alert trigger: The process begins the moment a potential phishing alert is received from a source like Microsoft 365.
- Parallel data extraction: Torq immediately executes multiple tasks in parallel to deconstruct the email:
- URLs: It extracts all unique URLs from the email’s body and within any attachments.
- Attachments: It processes all file attachments to retrieve their details and corresponding file hashes.
- Headers: It retrieves the full message headers using the Microsoft Graph API.
- Threat Validation: Torq then leverages integrations with various threat intelligence feeds, such as VirusTotal, to determine if the URLs, attachments, or information pulled from the email headers are flagged as malicious or benign. This helps quickly weed out false positives, or confirms the alert as a true malicious threat before a security case is even created.
- Data consolidation and output: All extracted artifacts (URLs, file hashes, and headers) are automatically collected, combined, and formatted into a single, structured output, ensuring all necessary data is ready for the next step.
- Initiate case management: If the alert is confirmed as malicious through third-party validation (or reaches a designated suspicious threshold), the structured output is then used to automatically create a new security case or escalate an existing incident with similar IOCs, often triggering a nested workflow for full case management and remediation.
Case Study: Lennar Cuts Phishing Resolution from Hours to Minutes
The security team at Lennar, one of the nation’s leading homebuilders, was swamped by phishing. They spent “hours and hours” remediating phishing attacks due to manual processes and the lack of flexibility and integrations in their existing XSOAR solution.
After switching to Torq Hyperautomation, the time it took Lennar to resolve a phishing attack dropped from hours to just minutes. This freed up their security experts to focus on more important work, like hunting for major threats.
Before we had Torq, we would do a lot of manual phishing remediation, which was a big time-taker. We would spend hours and hours. With Torq, we’ve significantly reduced the amount of time spent on phishing, which allowed us to further refine our other tools and alerts.
Daniel Gross, Senior Operations Analyst, Lennar
Win the Phishing War with Automated Phishing Response
Phishers are only going to get better at what they do, especially as they become more sophisticated in their use of AI. The only way for today’s stretched-thin security teams to keep up is with automated phishing response.
Anti-phishing automation eliminates the noise from low-level phishing alerts and frees up analysts to focus on more critical threats. It also enables immediate, consistent, and accurate phishing incident response, reducing human error and minimizing the potential impact of a breach.
A truly effective automated phishing defense relies on the ability to connect and orchestrate every tool in your security stack. With Torq’s limitless integrations, you can automate any phishing tool and process, creating a unified and automated response to neutralize phishing threats across your entire environment.
Want to make your SOC more efficient across the board? Get Torq’s Field CISO’s guide covering practical advice to overcome rising threats, lean teams, and budget scrutiny.